Windows Remote Management (WinRM) is the Microsoft implementation of WS-Management Protocol, a standard Simple Object Access Protocol (SOAP)-based, firewall-friendly protocol that allows hardware and operating systems, from different vendors, to interoperate.
https://docs.microsoft.com/en-us/windows/win32/winrm/portal
WinRM is a command-line tool that is used for the following tasks:
- Remotely communicate and interface with hosts through readily available channels/ports within your network, including workstations, servers and any operating system that supports it.
- Execute commands remotely on systems that you are not local to you but are network accessible
- Monitor, manage and configure servers, operating systems and client machines from a remote location.
Ports and Compatibility
- WinRM Port is 5985 and 5986 (HTTPS)
- In previous versions of WinRM, though, communications used to be done over port 80/443.
Enable this service
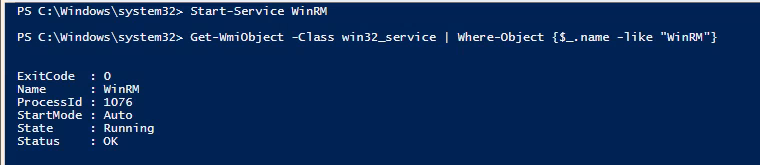
1. Using an admin account you can enable it using powershell
- Start-Service WinRM
- Get-WmiObject -Class win32_service | Where-Object {$_.name -like “WinRM”}
2. If you want the service to start automatic use
- Set-Service WinRM -StartMode Automatic
3. This command modifies the TrustedHosts list for the WinRM client. The computers in the
TrustedHosts list might not be authenticated.
- Get-Item WSMan:\localhost\Client\TrustedHosts
- Set-Item WSMan:localhost\client\trustedhosts -value *
- Get-Item WSMan:\localhost\Client\TrustedHosts

4. If you Scan this host after the service run you will see the ports enabled
- nmap -p 5985,5986 192.168.0.100

Run Evil WinRM
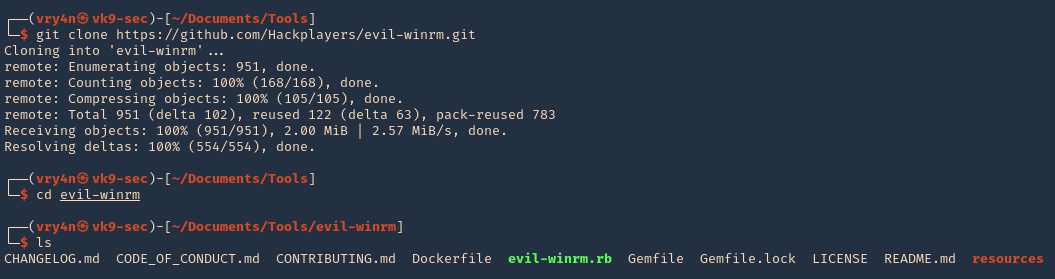
1. Download the program
- git clone https://github.com/Hackplayers/evil-winrm.git
- cd evil-winrm
- ls
2. I had to install dependencies
- sudo gem install winrm
- sudo gem install winrm-fs
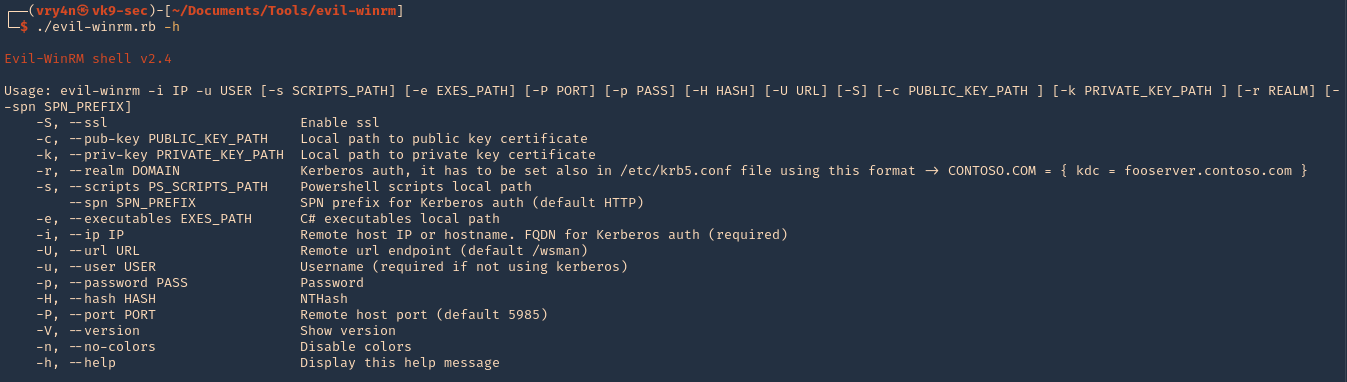
3. Run the script help
- ./evil-winrm.rb -h
4. Knowing a user credential we can log in
- ./evil-winrm.rb -u vry4n -p Admin.1 -i 192.168.0.100
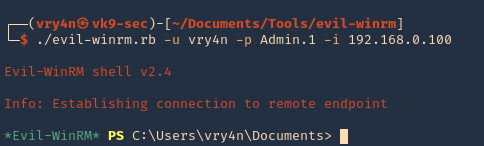
5. Specify a port if this is set to run on another uncommon port
- ./evil-winrm.rb -u vry4n -p Admin.1 -i 192.168.0.100 -P 5985
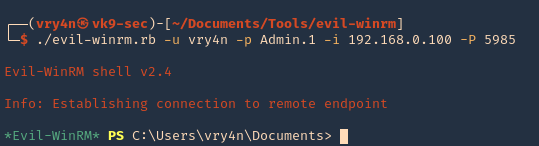
6. Display the version
- ./evil-winrm.rb –version