This publication is intended to guide you through to create a custom wordlist using hashcat.
1. First create or have already a word list. (I created a 4 words list)
- cat mylist.txt
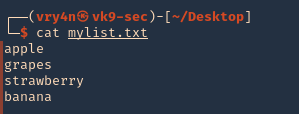
2. if you want to add dates next to the work you cant create a wordlist
- for i in $(cat mylist.txt); do echo $i; echo ${i}2020; echo ${i}2021; done >> mylist2.txt
- cat mylist2.txt
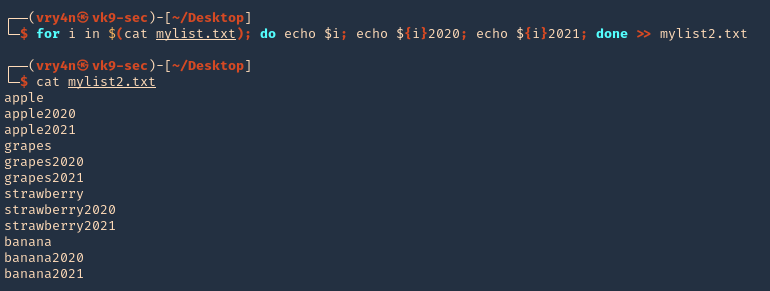
3. Now we will apply hashcat rules to this word list, the rules are located at /usr/share/hashcat/rules
- ls /usr/share/hashcat/rules
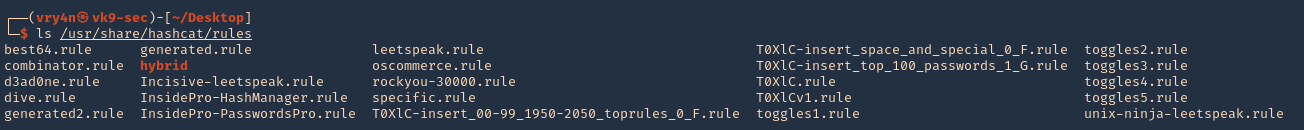
4. I’d use best64 rule
- hashcat –force –stdout mylist2.txt -r /usr/share/hashcat/rules/best64.rule > mylist3.txt
- wc -l mylist3.txt
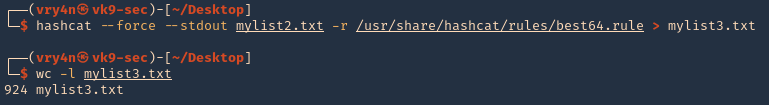
Note: Now we got a 924 lines
5. Read the file & inspect it
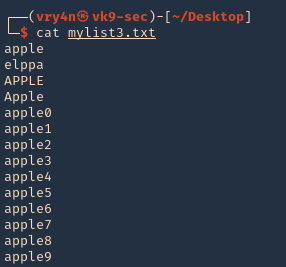
- cat mylist3.txt
Some useful queries
Combinator Attack:
Combinator Attack: Generates combinations of words from multiple wordlists.
- hashcat –stdout -a 1 password1.txt password2.txt > wordlist.txt
Rule-based Attack:
Rule-based Attack: Applies rules to create variations of words based on predefined transformations.
- hashcat –stdout -a 0 -r rules/best64.rule password.txt > wordlist.txt
Hybrid Attack:
Hybrid Attack: Combines known words with characters or numbers to create hybrid variations.
- hashcat –stdout -a 6 -i –increment-min=1 password?d > wordlist.txt
Password Dictionaries:
Password Dictionaries: Utilizes pre-existing password dictionaries for wordlist generation.
- hashcat –stdout -a 0 rockyou.txt > wordlist.txt
Custom Wordlists:
Custom Wordlists: Creates wordlists based on custom input files.
- hashcat –stdout -a 0 custom.txt > wordlist.txt
Personalized Wordlists:
Personalized Wordlists: Generates wordlist variations based on personalized patterns and information.
- hashcat –stdout -a 1 –custom-charset1=?l?d -1 ?l?d ?1?1?1?1?1 > wordlist.txt
Brute-Force Masks:
Brute-Force Masks: Uses masks to systematically generate wordlist entries based on defined patterns.
- hashcat –stdout -a 3 -1 ?l?u ?1?1?1?1?1?1?1 > wordlist.txt
Keyboard Patterns:
Keyboard Patterns: Creates wordlists based on keyboard patterns and common key sequences.
- hashcat –stdout -a 1 -k password.txt > wordlist.txt
Language-Based Wordlists:
Language-Based Wordlists: Generates wordlists specific to a particular language or region.
- hashcat –stdout -a 0 -j lang/english.dict > wordlist.txt
Leet Speak Variations:
Leet Speak Variations: Applies leet speak substitutions to words to create alphanumeric variations.
- hashcat –stdout -a 1 –custom-charset1=?l -1 ?l 1337?1 > wordlist.txt
Markov Chain Generation:
Markov Chain Generation: Uses Markov chains to generate wordlists based on an analysis of input wordlists.
- hashcat –stdout -a 0 –markov-hcstat=markov/hashcat.hcstat markov/wordlist.txt > wordlist.txt
Permutation Attack:
Permutation Attack: Generates permutations of words by rearranging their characters.
- hashcat –stdout -a 2 password.txt > wordlist.txt
Date and Year Variations:
Date and Year Variations: Incorporates date and year variations into wordlist generation.
- hashcat –stdout -a 1 –custom-charset1=?d -1 ?d date?1 > wordlist.txt
Targeted Wordlists:
Targeted Wordlists: Creates wordlists targeting specific character sets or patterns.
- hashcat –stdout -a 1 –hex-charset -1 303132333435363738394142434445464748494A4B4C4D4E4F505152535455565758595A word1?1?1?1 > wordlist.txt
Wordlist Combination:
Wordlist Combination: Combines wordlists using different character sets to create variations.
- hashcat –stdout -a 1 password.txt -1 ?l?u ?1?l?l > wordlist.txt
Recommendations
- Use Strong Passwords: Encourage users to create strong passwords that are long, complex, and unique. Include a mix of uppercase and lowercase letters, numbers, and special characters. Discourage the use of common or easily guessable passwords.
- Implement Password Policies: Enforce password policies that require regular password changes, minimum password length, and complexity requirements. Set limitations on password reuse to prevent users from recycling passwords.
- Multi-Factor Authentication (MFA): Implement MFA wherever possible. This adds an extra layer of security by requiring users to provide additional verification, such as a code sent to their mobile device or a biometric factor.
- Hashing Algorithms and Salting: Implement strong and secure hashing algorithms, such as bcrypt or Argon2, for storing password hashes. Additionally, use random salts for each password to prevent rainbow table attacks and make the cracking process more difficult.
- Password Encryption and Storage: Protect password databases and ensure they are securely encrypted. Implement strict access controls to restrict unauthorized access to password storage systems.
- Education and Awareness: Educate users about the importance of strong passwords, password hygiene, and the risks associated with weak passwords. Promote awareness about password cracking techniques and provide guidance on creating and managing strong passwords.
- Limit Failed Login Attempts: Implement mechanisms to detect and prevent brute-force attacks by limiting the number of failed login attempts. Implement account lockouts or delays between failed login attempts to deter attackers.
- Use Password Managers: Encourage the use of password managers to generate and securely store complex passwords. Password managers simplify the process of using strong, unique passwords without the need for users to remember them.
Need to down load all data from profile