Python is a versatile and powerful programming language known for its simplicity and readability. One of the features that makes Python flexible is the eval() function, which allows the execution of dynamically generated code. While eval() can be a useful tool in certain situations, it also carries inherent security risks if used improperly. In this article, we will delve into the dangers of Python EVAL code injection and how it can be exploited by malicious actors.
Understanding EVAL and Code Injection:
The eval() function in Python evaluates a string as a Python expression and returns the result. It allows developers to dynamically execute code during runtime, providing great flexibility. However, if user-supplied input is directly passed into eval(), it can lead to code injection vulnerabilities.
Code injection occurs when an attacker manages to insert malicious code into a program, exploiting a vulnerability in the system. In the case of Python EVAL code injection, an attacker manipulates input data to execute unintended commands, potentially compromising the security and integrity of the system.
Exploiting EVAL Code Injection:
Exploiting EVAL code injection involves crafting input that can be executed by eval() in an unintended manner. Here’s an example:

In this code snippet, the user is prompted to enter a number, which is then concatenated with a string to form an expression that is passed to eval().
If an attacker enters malicious input like “__import__(‘os’).system(‘rm -rf /’)” instead of a valid number, the eval() function will execute the unintended command, resulting in the deletion of files on the system.
Example
1. So, by running this function normally, the eval() will add 2 + the user provided input.
- python3 eval_test.py
- 4

2. Abusing this eval function we can inject code, in this case
- python3 eval_test.py
- __import__(‘os’).system(‘date’)
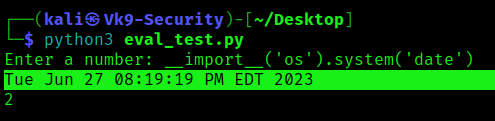
3. You can then exploit further to get a reverse shell, escalate privileges, or read/write important files
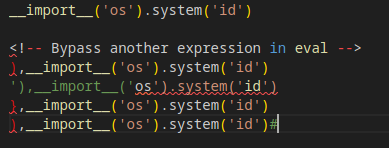
Bypass examples
Most of the time, we need to bypass another expression to execute our desired command.
Mitigating the Risks:
To protect against EVAL code injection, it is crucial to follow best practices for input validation and sanitization. Here are some recommended measures:
- Input Validation: Always validate user input to ensure it conforms to expected formats and ranges. Use appropriate validation techniques like regular expressions or type checking to filter out potentially harmful input.
- Avoid Direct EVAL: Whenever possible, avoid using eval() to evaluate user input. Consider alternative approaches that don’t involve executing arbitrary code, such as using ast.literal_eval() to safely evaluate literals.
- Context-Specific Evaluation: If you must use eval(), restrict the evaluation to a specific context by creating a whitelist of allowed functions, modules, or operations. This approach limits the potential damage an attacker can inflict.
- Use Secure Defaults: Configure your system and applications with secure defaults, such as running with limited privileges or using a restricted execution environment. This reduces the impact of code injection vulnerabilities.
- Regularly Update Dependencies: Keep your Python interpreter and libraries up to date to benefit from security patches and fixes. Many vulnerabilities related to EVAL code injection are often addressed in newer versions.
Sources
https://semgrep.dev/docs/cheat-sheets/python-code-injection/
https://www.stackhawk.com/blog/command-injection-python/
https://exploit-notes.hdks.org/exploit/linux/privilege-escalation/python-eval-code-execution/
https://medium.com/swlh/hacking-python-applications-5d4cd541b3f1
https://sethsec.blogspot.com/2016/11/exploiting-python-code-injection-in-web.html