WPScan is an open source WordPress security scanner. You can use it to scan your WordPress website for known vulnerabilities within the WordPress core, as well as popular WordPress plugins and themes.
This tool is available at: https://github.com/wpscanteam/wpscan, this comes installed in most security distributions.
How to use
1. Display help
- wpscan –help
- wpscan -h
2. Show tool version
- wpscan –version

3. Don’t display banner
- wpscan –nobanner –version
4. Update the database
- wpscan –update
Scanning
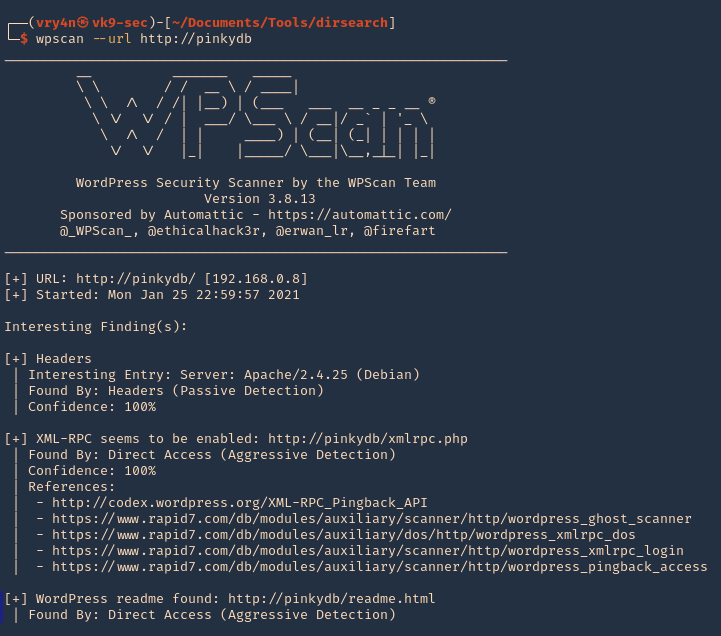
1. Basic scan, you need to set the site that runs WordPress, it will run vulnerability scan
- wpscan –url http://pinkydb
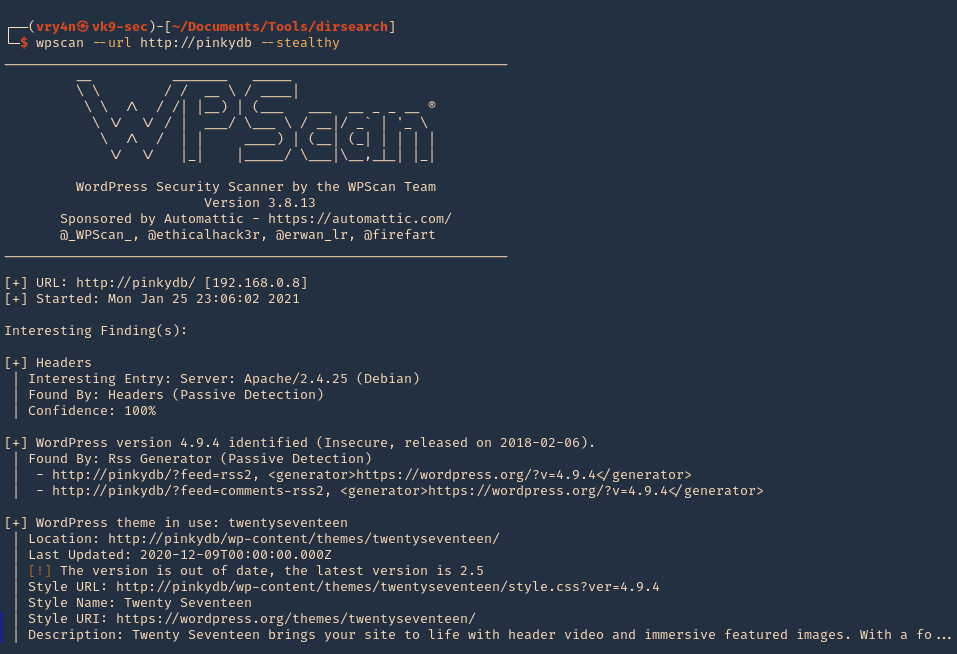
2. You can also run a more stealthy scan
- wpscan –url http://pinkydb –stealthy
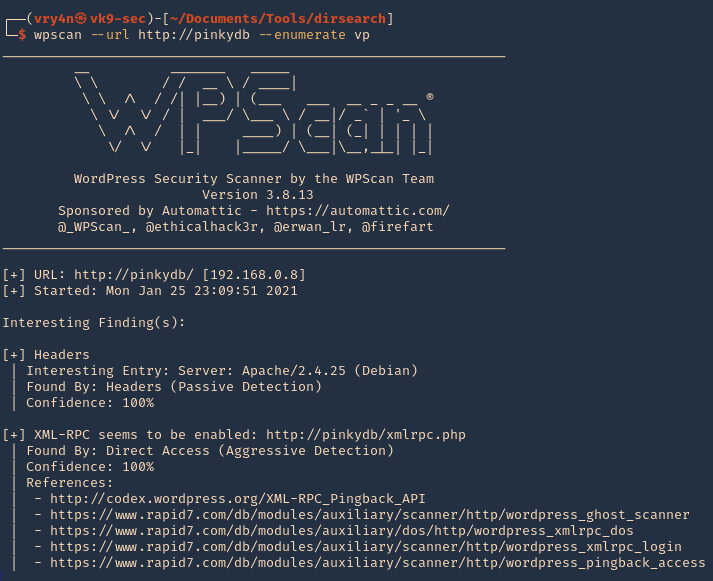
3. Scan for vulnerable plugins using –enumerate
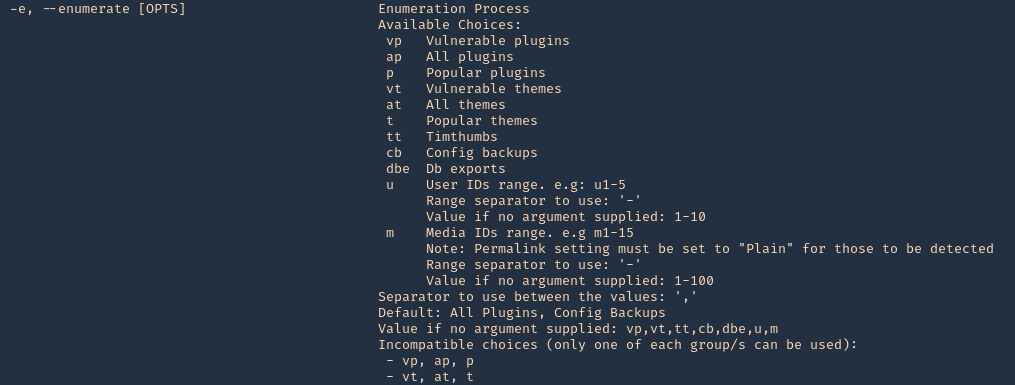
- wpscan –url http://pinkydb –enumerate vp
4. Check for vulnerable theme
- wpscan –url http://pinkydb –enumerate vt
5. Enumerate users
- wpscan –url http://pinkydb –enumerate u
- wpscan –url http://pinkydb–enumerate u1-1000
6. Use a custom user agent
- wpscan –url http://pinkydb –user-agent ‘Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/11.1.2 Safari/605.1.15’
7. Use a random user agent
- wpscan –url http://pinkydb –random-user-agent
8. Set the threats to run the scan faster default 5
- wpscan –url http://pinkydb -t 10
9. Send through a proxy, in BurpSuite we can also confirm our spoofed user agent.
- wpscan –url http://pinkydb –user-agent ‘Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/11.1.2 Safari/605.1.15’ –proxy http://127.0.0.1:8080
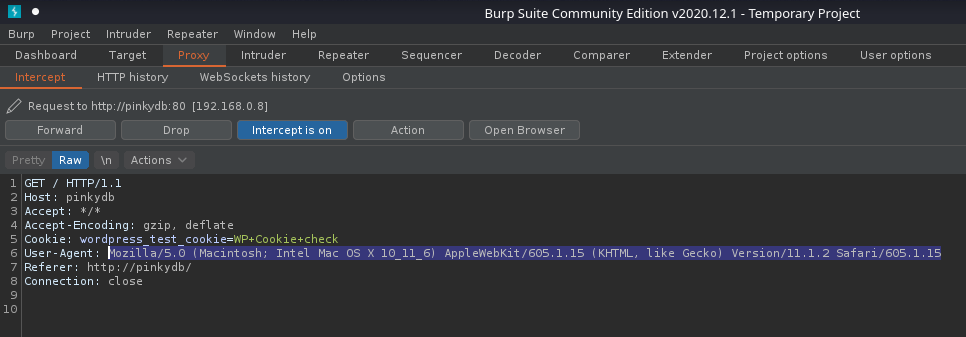
10. You can also set a cookie, if the page requires any
- wpscan –url http://pinkydb –cookie-string <cookie>
11. Scan API
- api-token <token>
12. If WordPress doesn’t locate the page automatically you can set the location, also, plugins have a similar option
- wpscan –url http://pinkydb –wp-content-dir <DIR>
- wpscan –url http://pinkydb –wp-plugin-dir <DIR>
13. Run a more aggressive scan (mixed, passive, aggressive)
- wpscan –url http://pinkydb –detection-mode aggressive
14. Run a more aggressive plugin detection mode (mixed, passive, aggressive)
- wpscan –url http://pinkydb –plugins-detection aggressive
- wpscan –url http://pinkydb –plugins-version-detection aggressive
15. Define a URI if the WordPress login page is different than /wp-login.php
- wpscan –url http://pinkydb –login-uri /wordpress/login.php
16. Supply usernames for enumeration
- wpscan –url http://pinkydb -U user_list.txt –enumerate u