Port Knocking is a method used to secure your port access from unauthorized users. Port Knocking works by
- Opening ports on a firewall by generating a connection attempt on a set of defined closed/open ports.
- Once a correct sequence of connection attempts is received, the firewall will open the port that was previously closed.
The main purpose of port knocking is to defend yourself against port scanners.
Install and Configure SSH
1. First thing to do is to update the system and then proceed with apt install, run the program by using ‘service’ command
- sudo apt update && dist-upgrade -y
- sudo apt install ssh
- sudp systemctl enable ssh.service
- sudo service ssh start
- sudo service ssh status
2. From our Kali machine we will run nmap against port 80, it should show as ‘open’
- nmap -p 22 -sV 192.168.0.5

Install and Configure Iptables
1. Check if any other Firewall service is running and stop it before initiating/installing IPTables, in this case ‘UFW’ is installed on my machine
- sudo ufw status
- sudo ufw disable

2. Now install ‘iptables’
- sudo apt install iptables iptables-persistent

Note: default dir for rules IPv4: /etc/iptables/rules.v4 & IPv6: /etc/iptables/rules.v6

5. Once iptables is installed, you will need to allow all established connections and on-going sessions through iptables. Which means current sessions won’t be terminated.
| -A, –append chain rule-specification | Append one or more rules to the end of the selected chain. When the source and/or destination names resolve to more than one address, a rule will be added for each possible address combination.
(Note: the chains INPUT and OUTPUT are only traversed for packets coming into the local host and originating from the local host respectively. |
| -m, –match match
-m conntrack |
Specifies a match to use, that is, an extension module that tests for a specific property. The set of matches make up the condition under which a target is invoked. Matches are evaluated first to last as specified on the command line and work in short-circuit fashion, i.e. if one extension yields false, evaluation will stop.
The one called conntrack works with the network connection tracking capabilities of the kernel. |
| -j, –jump target | This specifies the target of the rule; i.e., what to do if the packet matches it. |
| ACCEPT | means to let the packet through. |
| –cstate | ESTABLISHED,RELATED: This specifies the type of connection to which the rule will apply, namely ESTABLISHED and RELATED connections. |
- sudo iptables -A INPUT -m conntrack –ctstate ESTABLISHED,RELATED -j ACCEPT
3. Next step after accepting active traffic traffic through IPTables, block the desired incoming port, in our case port SSH (22)
| -A: Append | the rule to the firewall rules table, i.e., add it to the bottom. |
| INPUT | This rule is about incoming connections. |
| -p tcp | This rule applies to traffic that uses the Transmission Control Protocol. |
| –dport 22 | This rule specifically applies to TCP traffic that targets port 22 (the SSH port). |
| -j REJECT | If the traffic matches the rule, jump to the REJECT target in the firewall. So, if the traffic is rejected, it’s not permitted through the firewall. |
- sudo iptables -A INPUT -p tcp –dport 22 -j REJECT
4. Now, we start the netfilter service, and, save the rule we just created
- sudo systemctl start netfilter-persistent
- sudo systemctl enable netfilter-persistent
- sudo netfilter-persistent save
- sudo netfilter-persistent reload
5. Now running Nmap againg from our Kali machine, the port should show as ‘filtered’ or ‘closed’
- nmap -p 22 -sV 192.168.0.5

Install and Configure Knockd
knockd is a port-knock server. It listens to all traffic on an ethernet (or PPP) interface, looking for special “knock” sequences of port-hits.
- A client makes these port-hits by sending a TCP (or UDP) packet to a port on the server. This port need not be open
- Since knockd listens at the link-layer level, it sees all traffic even if it’s destined for a closed port.
- When the server detects a specific sequence of port-hits, it runs a command defined in its configuration file.
- This can be used to open up holes in a firewall for quick access.
1. Install the tool in the server
- sudo apt install knockd -y
2. Once knockd is installed, you will need to enable knockd service to start on boot. You can do this by editing /etc/default/knockd file (change value from 0 to 1), additionally we need to specify the network interface (change ), in our case “ens33”, this can be revealed with ‘ifconfig’
- sudo vi /etc/default/knockd
- START_KNOCKD=1
- KNOCKD_OPTS=”-i ens33”

3. you will need to configure knockd. You can configure it by editing /etc/knockd.conf file
| sequence | The sequence of ports someone must access to open or close port 22. The default ports are 7000, 8000, and 9000 to open it, and 9000, 8000, and 7000 to close it. You can change these or add more ports to the list. For our purposes, we’ll stick with the defaults. |
| seq_timeout | The time period within which someone has to access the ports to trigger it to open or close. |
| command | The command sent to the iptables firewall when the open or close action is triggered. These commands either add a rule to the firewall (to open the port) or take it out (to close the port). |
| tcpflags | The type of packet each port must receive in the secret sequence. A SYN (synchronize) packet is the first in a TCP connection request, called a three-way handshake. |
- sudo vi /etc/knockd.conf

4. Change the [openSSH] and [closeSSH] section default knock sequence as per your requirements:
[openSSH]
- sequence = 10011, 10001,10111
- seq_timeout = 20
- tcpflags = syn
- command = /sbin/iptables -I INPUT -s %IP% -p tcp –dport 22 -j ACCEPT
[closeSSH]
- sequence = 10111,10011,10001
- seq_timeout = 20
- command = /sbin/iptables -D INPUT -s %IP% -p tcp –dport 22 -j ACCEPT
- tcpflags = syn

5. Save the file when you are finished, then start knock service to apply these changes:
- sudo systemctl start knockd
Note:
- sequence = 10011,10001,10111 : Knock will open the SSH port when the sequence is completed from client machine.
- seq_timeout = 20 : This option defines how long you have time to complete the sequenct for the knock.
- command = /sbin/iptables -I INPUT -s %IP% -p tcp –dport 22 -j ACCEPT : This command will open the port 22.
- sequence = 10111,10011,10001 : Knock will close the SSH port when the sequence is completed from client machine.
- command = /sbin/iptables -D INPUT -s %IP% -p tcp –dport 22 -j ACCEPT : This command will close the port 22.
6. Now activate the knockd service
- sudo systemctl enable knockd.service
- sudo service knockd start
- sudo service knockd status

At this point we are done with the configuration. Now it’s time to test it
Knocking ports to open SSH.
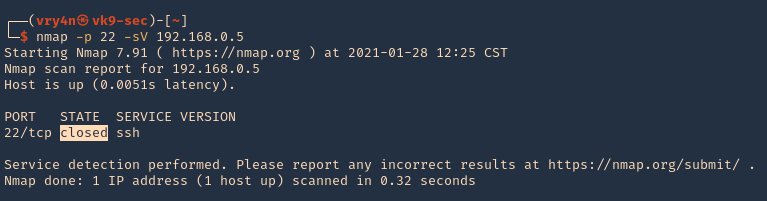
1. Running nmap on the target host, we can see that the port was actually closed.
- nmap -p 22 -sV 192.168.0.5
2. Running the knock command with the specific sequence will open the port.
- knock 192.168.0.5 10011 10001 10111 -d 500
- nmap -p 22 -sV 192.168.0.5
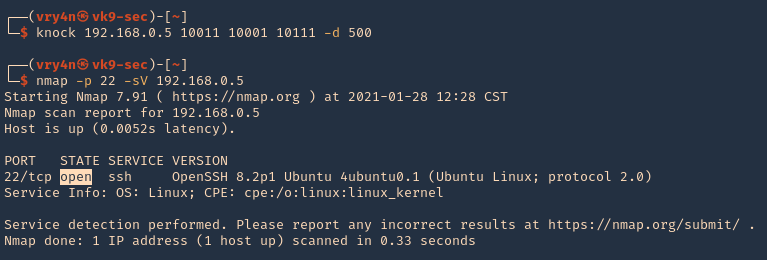
3. Now we are able to ssh to the box
- ssh vry4n@192.168.0.5

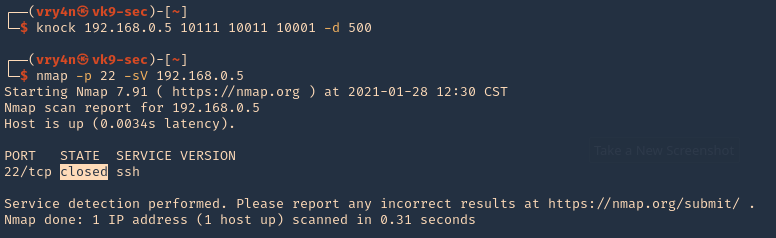
4. To close the port, we can run the sequence specified in /etc/knockd.conf [closeSSH]
- knock 192.168.0.5 10111 10011 10001 -d 500
- nmap -p 22 -sV 192.168.0.5
5. Checking Syslog log file we can find the activity open & close
- tail -f /var/log/syslog

Extra
When we have a port list and don’t know the sequence, we can use a script to automate things
1. I have written the following script to test different sequences
2. Download the script
- git clone https://github.com/vry4n/knock_test.git
3. Run the script
- cd knock_test
- python3.9 knock_test.py

Best view i have ever seen !
Best view i have ever seen !