Shellshock is effectively a Remote Command Execution vulnerability in BASH. The vulnerability relies in the fact that BASH incorrectly executes trailing commands when it imports a function definition stored into an environment variable.

A lot of programs like SSH, telnet, CGI scripts allow bash to run in the background allowing the vulnerability to be exploited remotely over the network which makes it more scary. Shellshock can be exploited in
- RCE via Apache with mod_cgi, CGI Scripts, Python, Perl
- RCE on DHCP clients using Hostile DHCP Server
- OpenSSH RCE/Privilege escalation
This vulnerability is exploitable via multiple vectors (DHCP, HTTP, SIP, FTP, and SMTP) and could allow an attacker to inject and execute arbitrary commands on a vulnerable system.
Affected versions
CVE-2014-7169 – GNU Bash through 4.3 bash43-025
CVE-2014-6271, CVE-2014-6277, CVE-2014-6278, CVE-2014-7186, CVE-2014-7187 – GNU Bash through 4.3 bash43-026

Affected systems
The vulnerability affects versions 1.14 through 4.3 of GNU Bash.
- GNU Bash 3.0
- GNU Bash 3.1
- GNU Bash 3.2
- GNU Bash 4.0
- GNU Bash 4.1
- GNU Bash 4.2
- GNU Bash 4.3
Variables
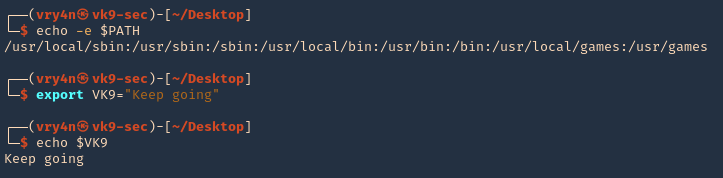
Bash supports environment variables. They contain information about your login session, stored for the system shell to use when executing commands.
- env

Print, and add new variables
- echo $PATH
- export VK9=”Keep going”
- echo $VK9
Bash Functions
1. Bash functions are blocks of code that can be used in .sh scripts to execute an instruction. These can be used as one line piece of code, interpreted by bash
- name() { echo $Path; date; }
- name

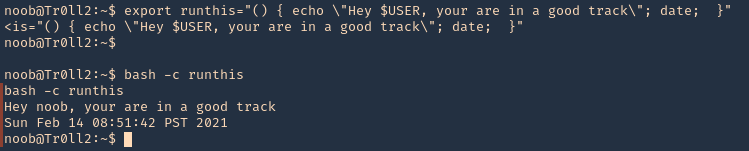
2. These functions can also be set as environment variables
- export runthis=”() { echo \”Hey $USER, your are in a good track\”; date; }”
- bash -c runthis
Test vulnerability
1. Check bash version
- bash –version

2. A simple test to check if your Bash is vulnerable. (local test)
- env var='() { ignore this;}; echo vulnerable’ bash -c /bin/true
- env x='() { :;}; echo shellshocked’ bash -c “echo test”

The way this proof of concept works is that bash functions can be exported to environment variables. When code is added to the end of the function definition inside the variable, it gets executed when the shell is invoked (“bash -c”).
Remediation
Remediation is obviously going to be most successful by applying patches to affected systems. Check with relevant vendors for updated information. This is also an opportunity to review systems for unused services, like FTP, Telnet, and DCHPd, and disable them when they are not required.