WES-NG is a tool based on the output of Windows’ systeminfo utility which provides the list of vulnerabilities the OS is vulnerable to, including any exploits for these vulnerabilities. Every Windows OS between Windows XP and Windows 10, including their Windows Server counterparts, is supported. (https://github.com/bitsadmin/wesng)
How to use
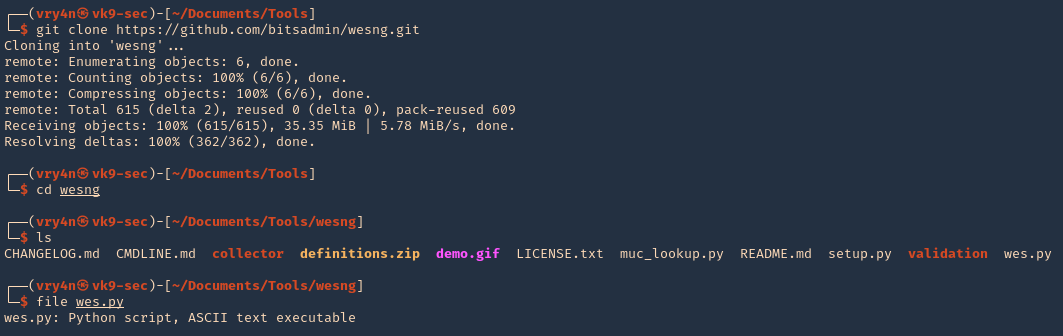
1. Download the tool from the repository, access the downloaded folder and see its contents
- git clone https://github.com/bitsadmin/wesng.git
- cd wesng
- ls
- file wes.py
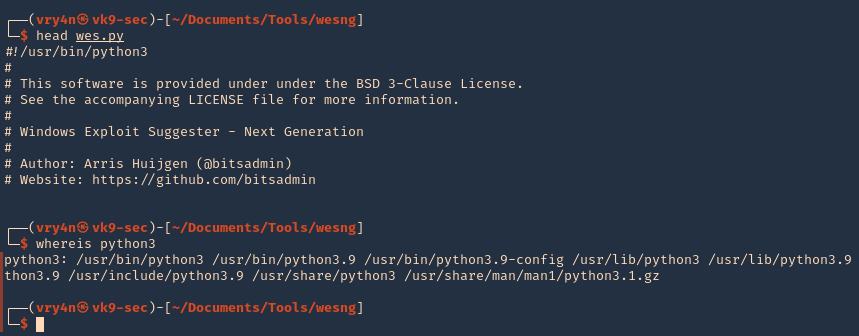
2. This tool is written in Python 3, so make sure it is installed on your computer
- head wes.py
- whereis python3
3. Getting help
- python3 wes.py -h
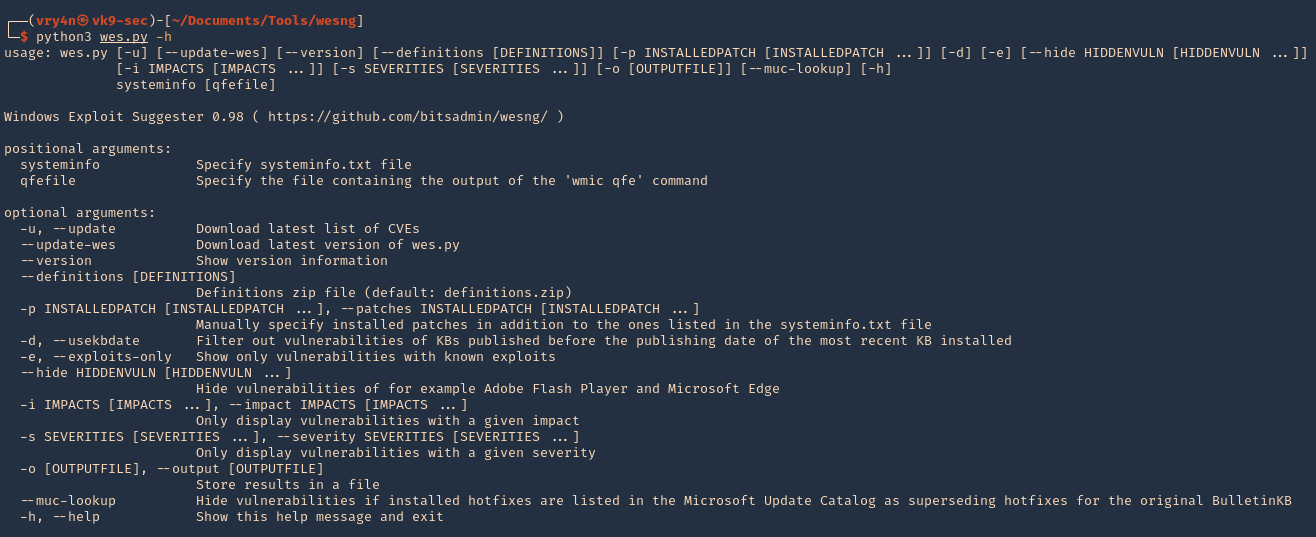
Note:
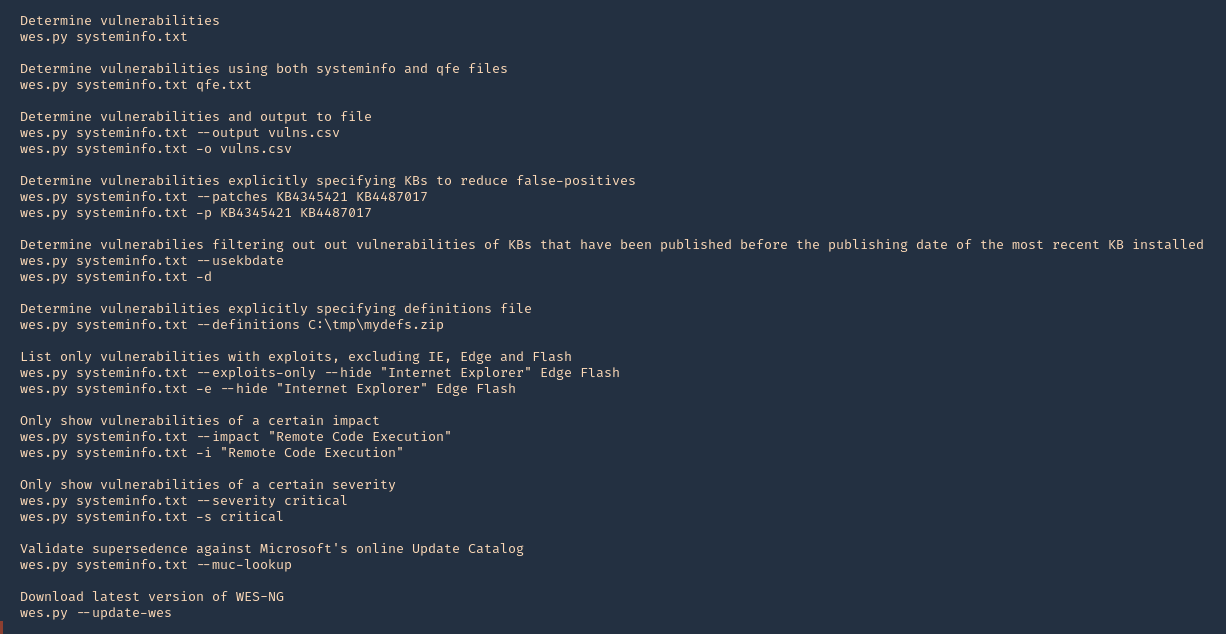
At the bottom we can find examples
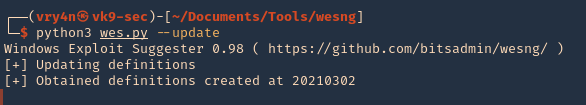
4. Update the database
- python3 wes.py –update
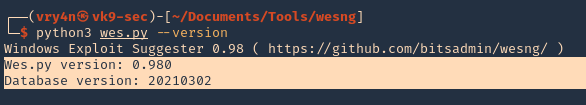
5. See the tool version
- python3 wes.py –version
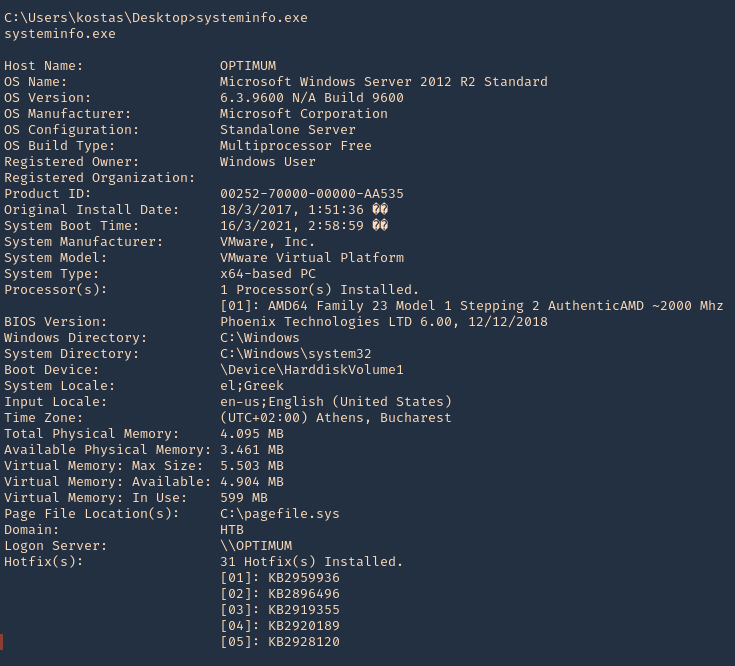
6. Basic analysis. On the remote Windows Workstation or Server, run systeminfo.exe. Copy and paste the info to your kali machine
- systeminfo.exe
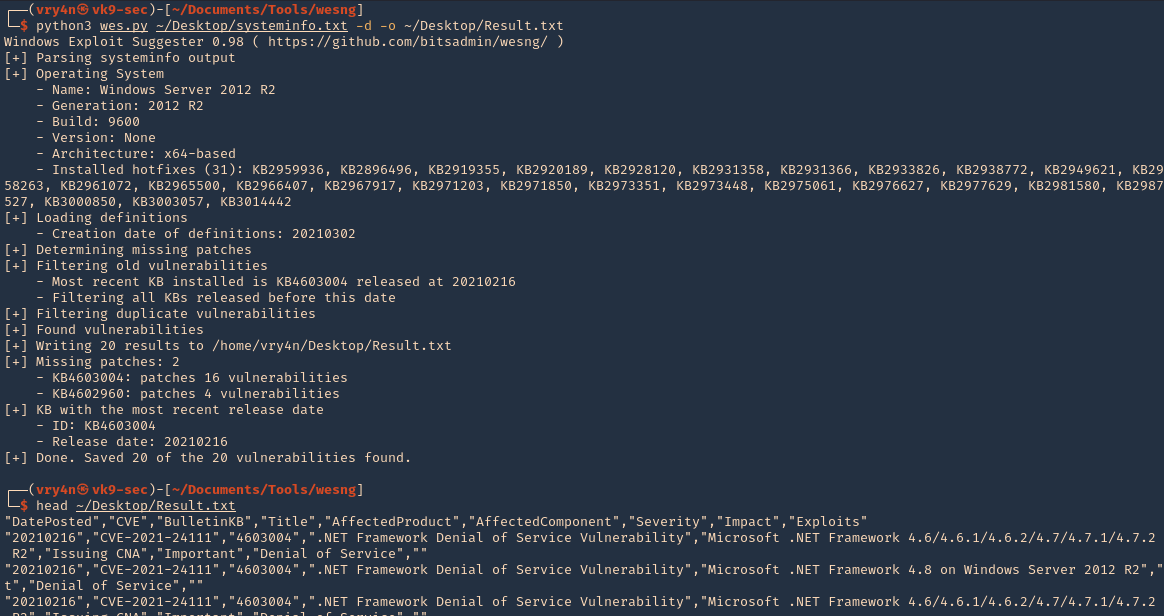
7. Having output in Kali we will run the application against the file
- python3 wes.py ~/Desktop/systeminfo.txt
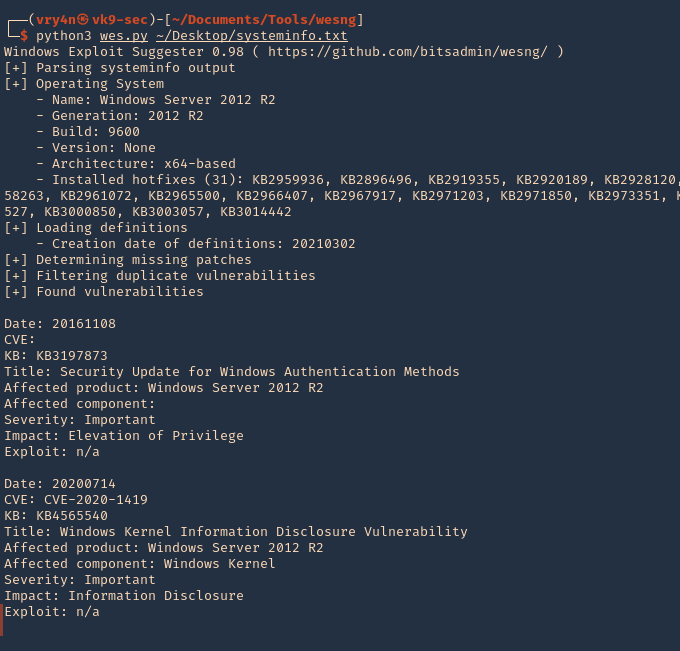
Note. This will give us a general overview of the KBs
8. To filter by KB with known exploit
-e, –exploits-only = Show only vulnerabilities with known exploits
- python3 wes.py ~/Desktop/systeminfo.txt -e
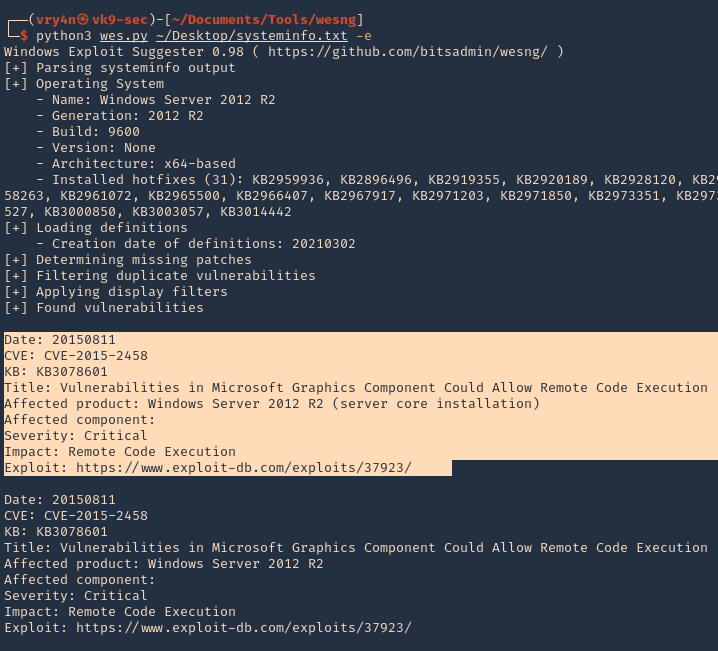
9. Determine vulnerabilities filtering out vulnerabilities of KBs that have been published before the publishing date of the most recent KB installed
- python3 wes.py ~/Desktop/systeminfo.txt -d
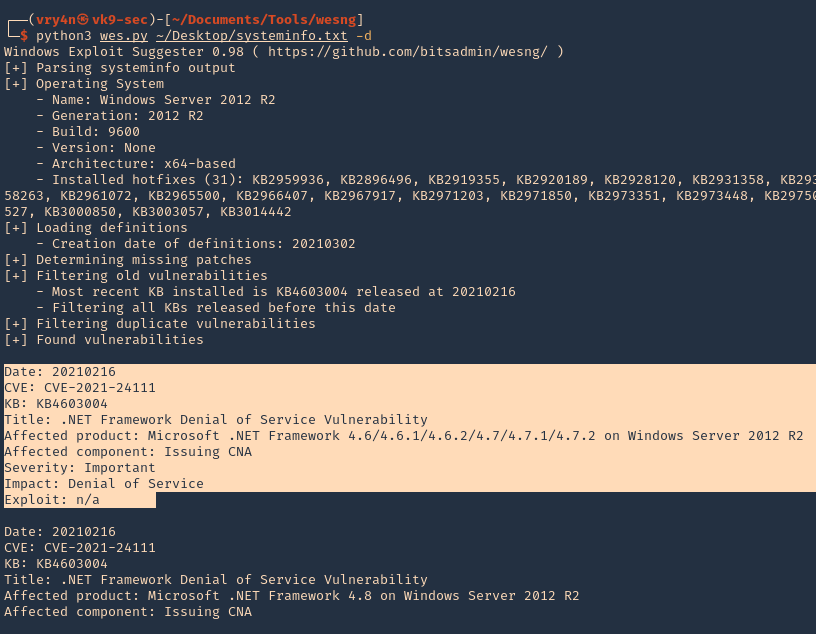
10. Write to output file
- python3 wes.py ~/Desktop/systeminfo.txt -d -o ~/Desktop/Result.txt
- head ~/Desktop/Result.txt