by Vry4n_ | Mar 10, 2020 | Labs
This has been writen to explain the steps to set a basic insecure SMTP lab. We are using hMailServer to act as a mail server & Thunderbird as mail client.
https://www.hmailserver.com/
https://www.thunderbird.net/
Mail Server (hMailServer)
1. Start the wizzard
2. Next, Accept the license
3. Select the install folder, next
4. Full installation, next
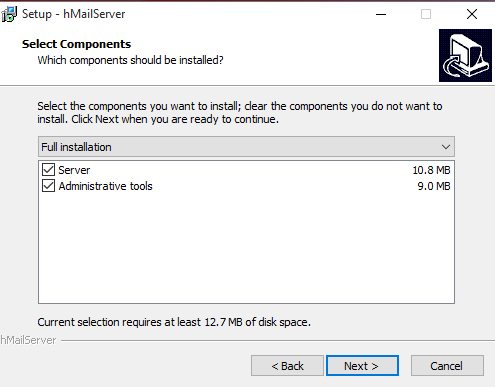
5. Use built in database, next

6. Create a shortcut, next

7. Choose the password for accessing hMailServer
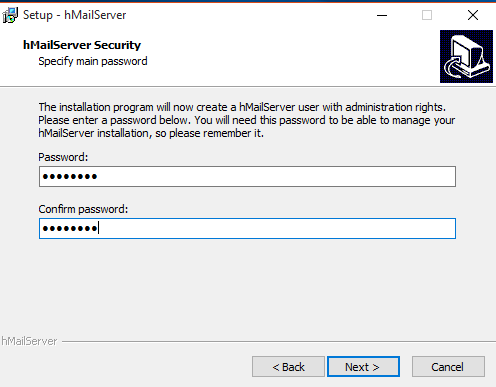
8. Complete the installation
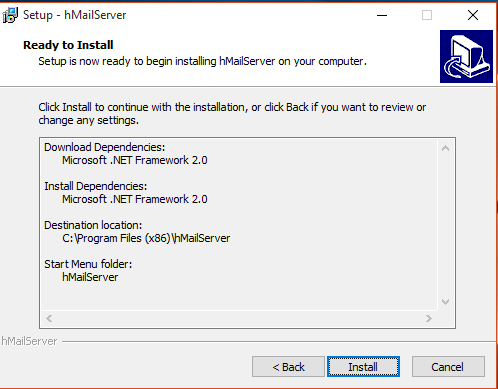
9. This may pop up, click yes, to install some dependencies

10. The installation begins
Configuration
1. Connect as Administrator
2. Enter the password we just created

3. You will enter to the main view
4. First thing start up process
5. We need to create a domain
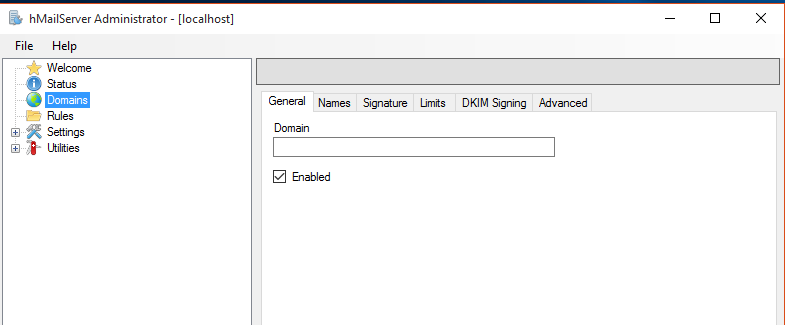
In that we have different tabs
- General: The name of the domain. To be considered valid, a domain name must include a dot. You must set up your DNS servers so that email can be sent to your mail server.
- Names: One domain can have several names. These are also known as domain aliases. For example, your organization might own the domain, company.com, but it might also own company.org
- Signature: you can configure hMailServer to add a signature to all email sent from this domain, If no HTML signature is specified, hMailServer will use the plain text signature as HTML signature as well.
- Limits: If you have specified 500MB, the total size of all messages in the domain will not exceed 500MB
- DKIM Signing (encryption): DKIM, Domain Keys Identified Mail, is a method to sign the content of messages. The recipient can verify that the message is sent from a server authenticated to send from the sender’s domain, and that the message content has not been modified in transit.
- Advanced: This tab contains the advanced settings for the domain. You normally don’t need to modify these settings.
Note
For this lab I will only modify general tab
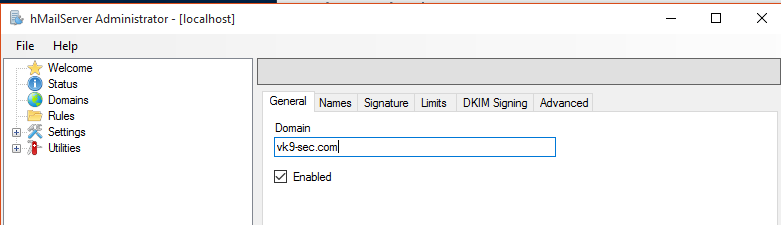
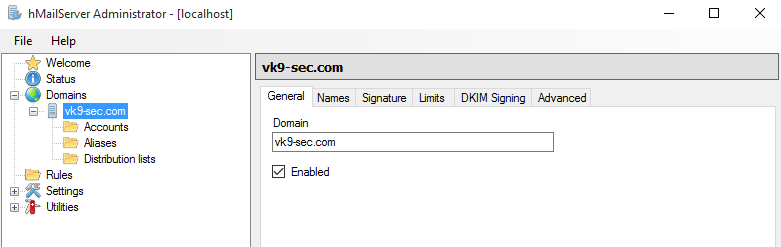
6. After saving the changes, we see the domain added
7. Now, it’s time to add user accounts
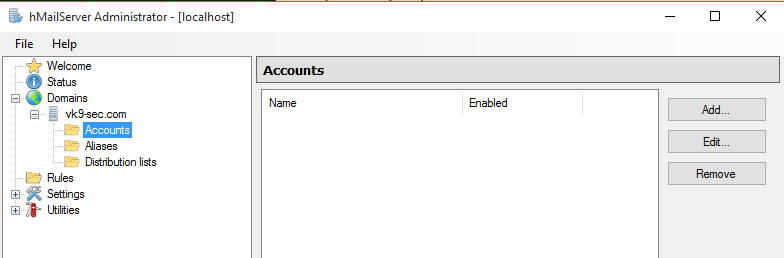
8. Add a user (leave the rest as default), then save
- Address: vry4n
- Password: pass1

9. In accounts we see our first user created
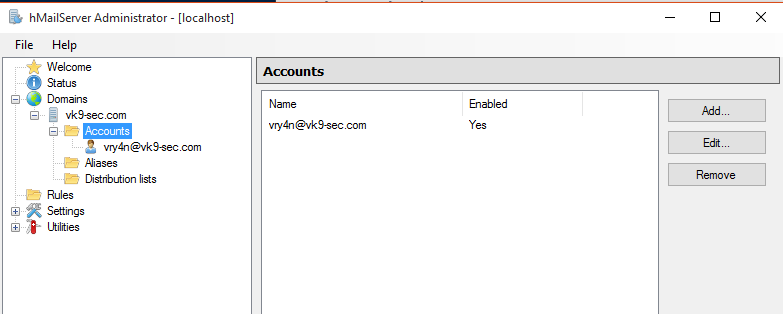
We will add a second user named john

At this point we are done with the mail server set up. Now it is time to run an email client to be able to send/receive emails
Email client (Thunderbird)
For this exercise we will use Thunderbird and a Linux machine to connect.
1. Install Thunderbird
- apt-get install thunderbird
2. Run the application
The application will now show up.

3. Add the SMTP server

4. Select the default account or add a new one

Edit the settings
- Description: VK9 SMTP
- Server Name: vk9-sec.com
- Port: 587
- Connection security: (optional TLS)
- Authentication method: (optional)
- User Name: Administrator
- OK
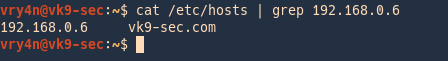
4. Add the domain name and server address to DNS records, we will use /etc/hosts
- vi /etc/hosts
- add -> 192.168.0.6 vk9-sec.com
- cat /etc/hosts | grep 192.168.0.6
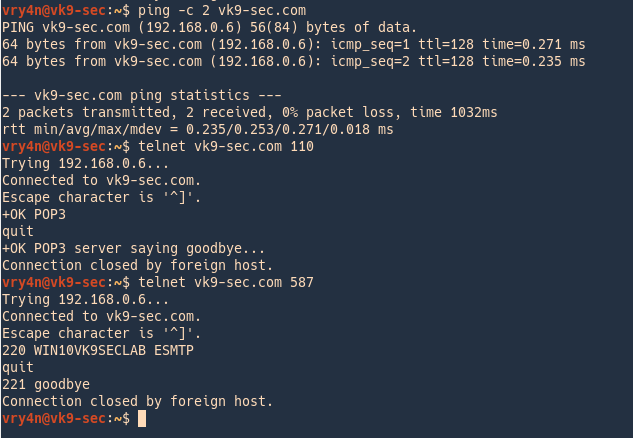
5. Test connectivity
- ping -c 2 vk9-sec.com
- telnet vk9-sec.com 587
- telnet vk9-sec.com 110
5. Now it is time to set up our accounts, when ThunderBird is first opened it requests to add an account.
- File -> New -> Existing mail account

Fill the blank spaces
- name: vry4n
- email address: vry4n@vk9-sec.com
- password: pass1
We have already created the accounts in the previous steps, in hMailServer
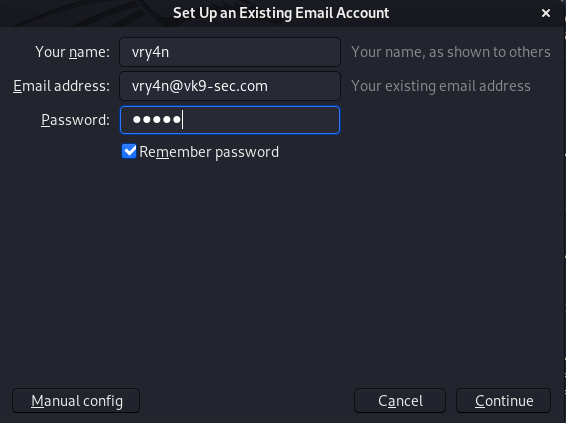
6. Now, click on “Manual config”, correct the server name. and, adjust the settings to match the server’s. I use POP3, I manually changed that
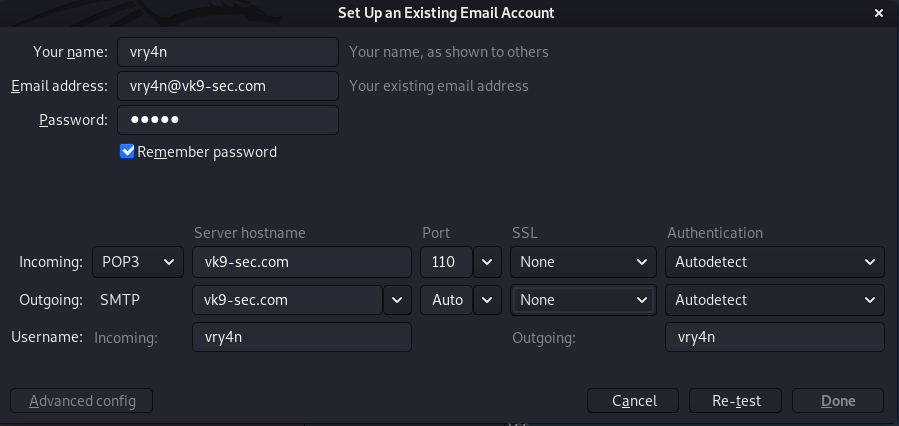
7. Test connectivity
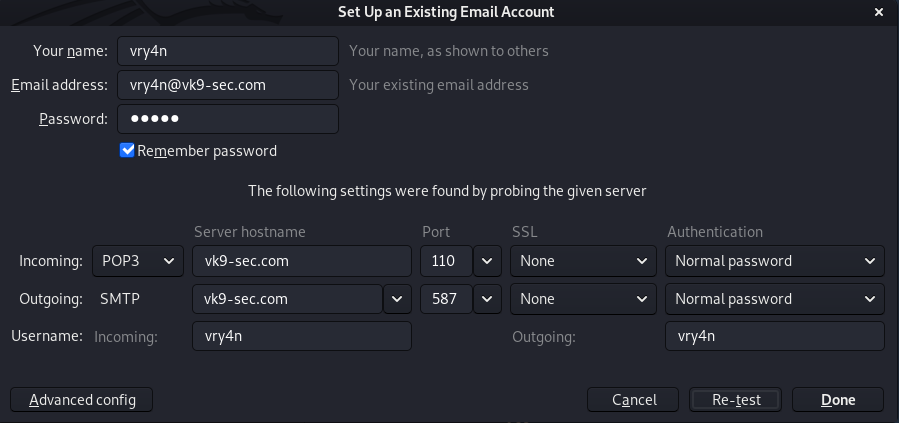
Doin gthis auto adjusts the settings, now it’s time to click on “Done”
8. Accept the risk, since, we are not using encryption.
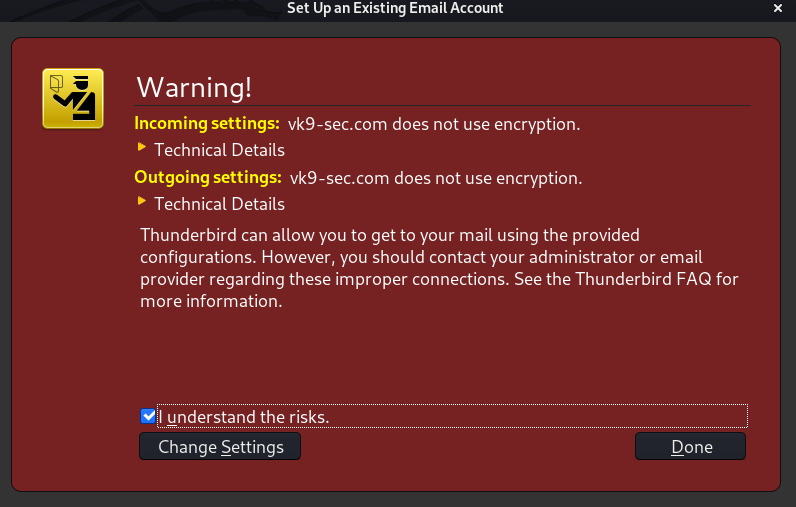
9. The account know shows up in the main page.
Now, we do the same for the other account. John
- File -> New -> Existing mailing account
- john
- john@vk9-sec.com
- pass1
10. Send an email as a test

by Vry4n_ | Mar 8, 2020 | Windows Management
This Guide provides a high view of Windows local management of groups and users
Users in windows
a user account is a collection of settings used by Windows to understand your preferences. It’s also used to control the files and folders you access, the tasks you are allowed to perform, the devices and resources you are allowed to use, User accounts are also the only way of authenticating and receiving the authorization to use your Windows device
Any user account has the following characteristics:
- the username or account name
- a unique identifier
- the password
- a user account picture
- the user type
- the user group
For each user account, Windows also generates a unique Security Identifier (SID) that’s not displayed in the user interface but is used internally for storing your settings. The SID has a unique value of variable length, and it looks like this: S-1-5-21-1180699209-877415012-3182924384-500.

SID meanings
S-1-5-32-544
In this example, the SID has the following components. The constants in parentheses are well-known identifier authority and RID values defined in Winnt.h:
- A revision level of 1
- An identifier-authority value of 5 (SECURITY_NT_AUTHORITY)
- A first subauthority value of 32 (SECURITY_BUILTIN_DOMAIN_RID)
- A second subauthority value of 544 (DOMAIN_ALIAS_RID_ADMINS)
https://docs.microsoft.com/es-es/windows/win32/secauthz/well-known-sids
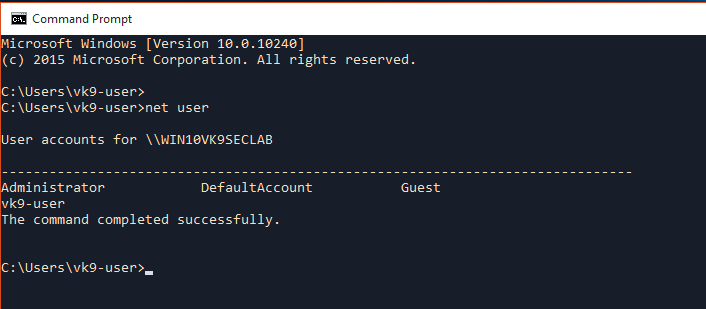
net user
1. Listing User accounts
net user = Net User is a command line tool that allows system administrators to manage user accounts on Windows PCs. You can use the command to display account information or make changes to user accounts.
2. Displaying help
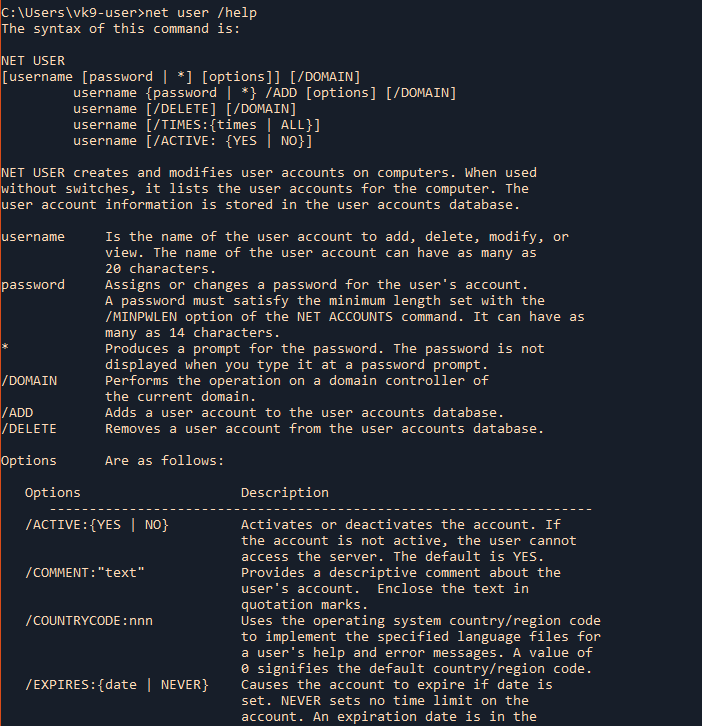
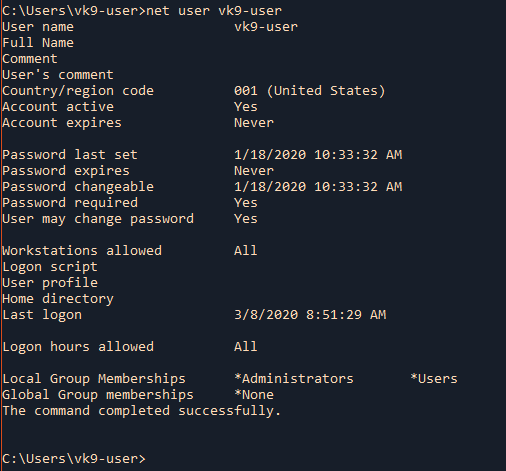
3. Display current user information, like, password settings, groups the user belongs, etc.
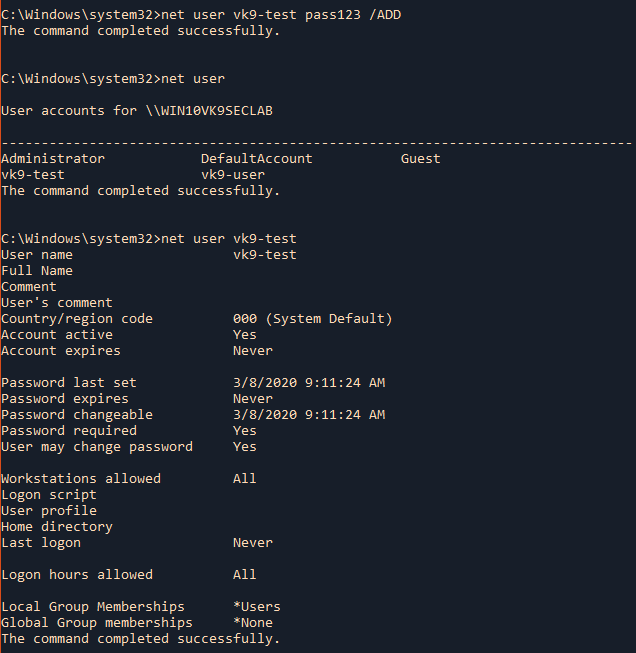
4. Add a new username, needs to run as administrator
username = Is the name of the user account to add, delete, modify, or view.
password = Assigns or changes a password for the user’s account.
/ADD = Adds a user account to the user accounts database.
- net user vk9-test pass123 /ADD
- net user
- net user vk9-test
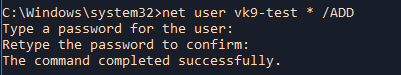
5. Create a user account hide the password when typing it
* = Produces a prompt for the password.
6. Add user & information
/COMMENT:”text” = Provides a descriptive comment about the user’s account.
/FULLNAME:”name” = Is a user’s full name (rather than a username). Enclose the name in quotation marks.
/USERCOMMENT:”text” Lets an administrator add or change the User Comment for the account.
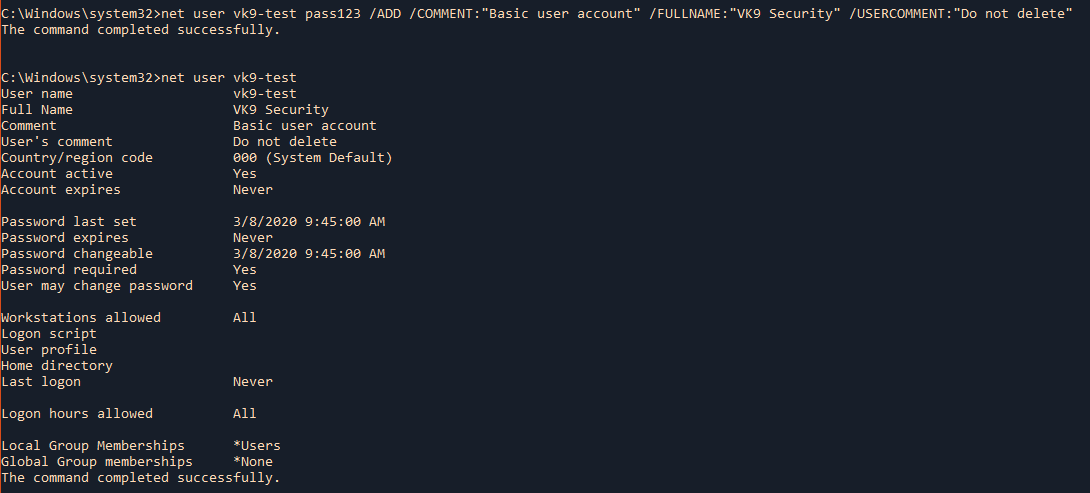
- net user vk9-test pass123 /ADD /COMMENT:”Basic user account” /FULLNAME:”VK9 Security” /USERCOMMENT:”Do not delete”
- net user vk9-test
7. Allow users to change or not their password
/PASSWORDCHG:{YES | NO} Specifies whether users can change their own password. The default is YES.
- net user vk9-test /PASSWORDCHG:NO
- net user vk9-test

8. Set a temporary account
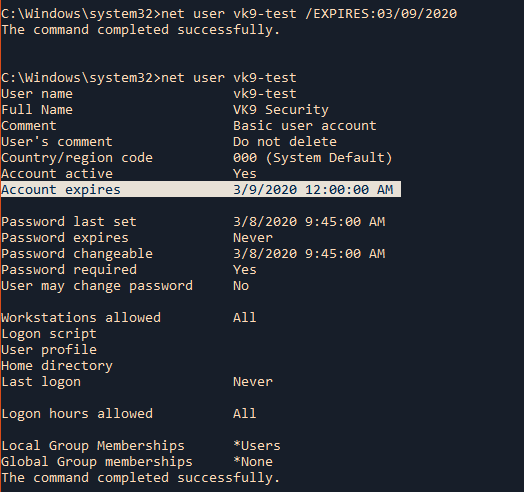
/EXPIRES:{date | NEVER} Causes the account to expire if date is set. NEVER sets no time limit on the account. An expiration date is in the form (mm/dd/yy).
- net user vk9-test /EXPIRES:03/09/2020
- net user vk9-test
9. Set user home directory
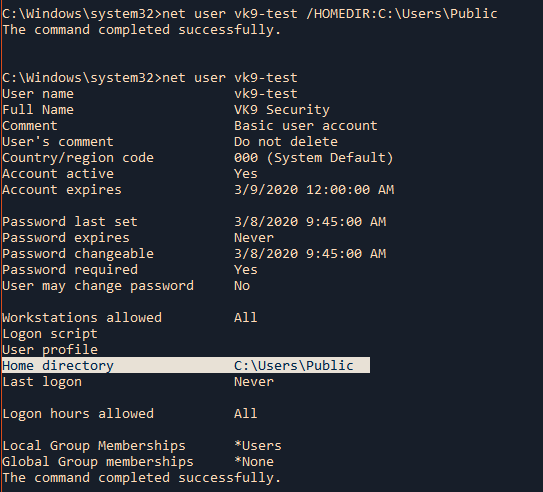
/HOMEDIR:pathname Sets the path for the user’s home directory. The path must exist.
- net user vk9-test /HOMEDIR:C:\Users\Public
Common errors
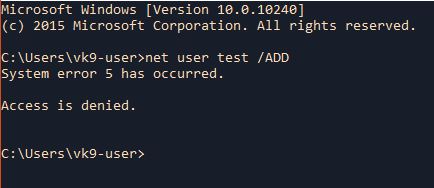
1. Lack of privileges. (Need to open CMD as admin)
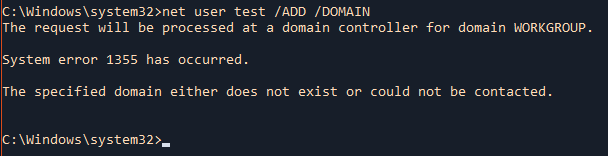
2. The computer not connected to the domain
Delete account
Local
Delete an existing user account
/DELETE Removes a user account from the user accounts database.
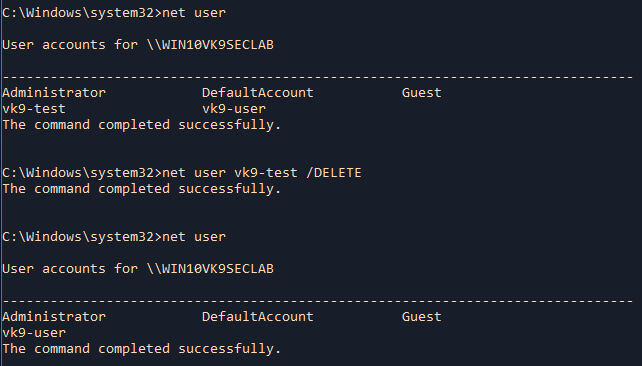
- net user
- net user vk9-test /DELETE
- net user
Domain
(when using /DOMAIN you have to be connected to Active Directory as an example)
- net user vk9-test /DELETE /DOMAIN
Groups in Windows
- Local groups – are the user groups that exist on your Windows computer or device. They are defined locally and can be managed from the “Local Users And Groups” tool. These are the user groups that home users work with and the ones that we’re going to talk about in this article.
- Security groups – have security descriptors associated with them. Security groups are used in Windows domains with Active Directory.
- Distribution groups – are useful for distributing e-mails for users that belong to domains with Active Directory.
You can add a regular user to Administrators group for having more rights on the computer.
net localgroup
Net localgroup command is used to manage local user groups on a computer. Administrators can add local/domain users to groups, delete users from groups, create new groups and delete existing groups.
1. Display help
/help = Displays help
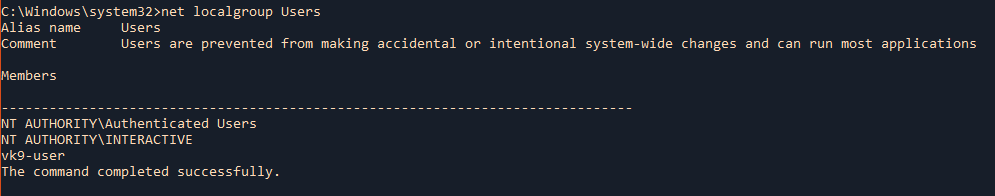
2. List existing groups

Show a specific group, its details and members
3. Create a new local group
/ADD = Adds a groupname or username to a local group.
- net localgroup vk9-group /ADD
- net localgroup vk9-group
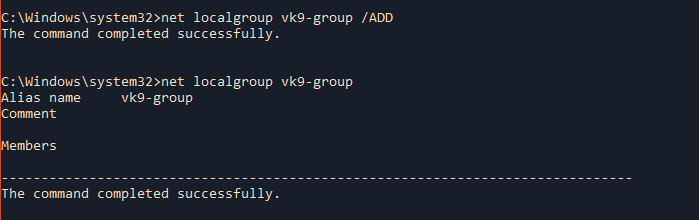
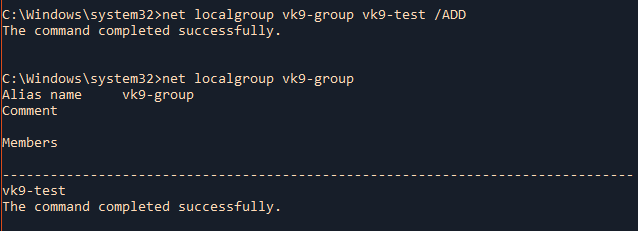
4. Add an existing user to a group
- net localgroup vk9-group vk9-test /ADD
- net localgroup vk9-group
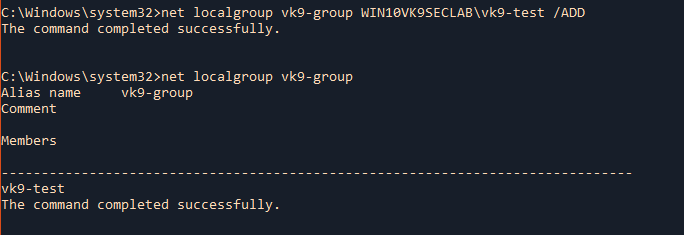
Extra
Add a domain group to a local group
- net localgroup <localgroup> <domaingroup> /ADD
- net localgroup vk9-group WIN10VK9SECLAB\vk9-test /ADD
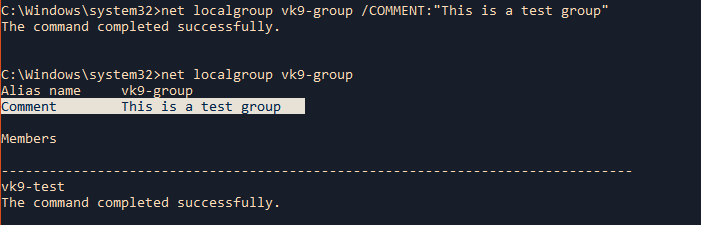
5. Add a comment to the group
/COMMENT:”text” = Adds a comment for a new or existing group.
- net localgroup vk9-group /COMMENT:”This is a test group”
- net localgroup vk9-group
Delete groups
1. To remove a user from existing group
/DELETE = Removes a groupname or username from a local group.
- net localgroup vk9-group
- net localgroup vk9-group vk9-test /DELETE
- net localgroup vk9-group
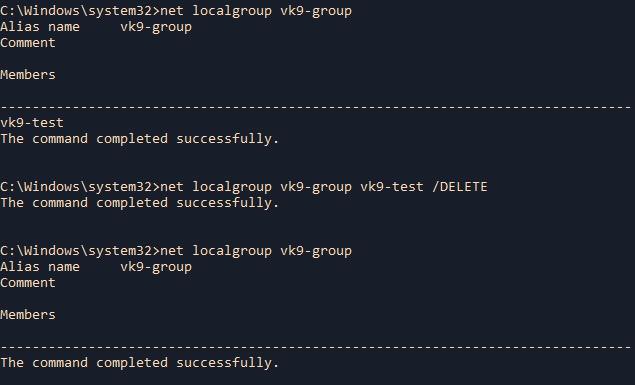
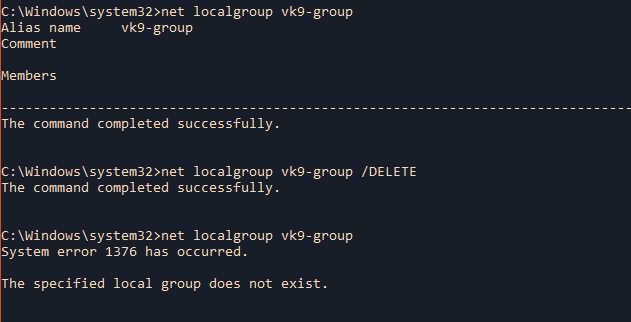
2. Delete an existing local group
- net localgroup vk9-group
- net localgroup vk9-group /DELETE
- net localgroup vk9-group
by Vry4n_ | Mar 8, 2020 | Linux Management
This is a guide written to help administering Users and Groups properly in Linux.
User Management
useradd
useradd is a low level utility for adding a new user or update default new user information
When we run ‘useradd‘ command in Linux terminal, it performs following major things:
- It edits /etc/passwd, /etc/shadow, /etc/group and /etc/gshadow files for the newly created User account.
- Creates and populate a home directory for the new user.
- Sets permissions and ownerships to home directory.
1. Basic add a new user
- sudo useradd vk9security
- id vk9security

We need to set a password to unlock the user account. As per the command below, ! in /etc/shadow means the account is locked, we use ‘passwd’ to change the user password.
- sudo cat /etc/shadow
- sudo passwd vk9security
- sudo cat /etc/shadow

Extra
To check if the account is locked. P means unlocked, L means Locked
- passwd -S vk9sec
- usermod -L vk9sec
- passwd -S vk9sec

Once, the password is set, we can confirm the creation of the user in /etc/passwd (users file)

Analyzing /etc/passwd 7 fields

- Username: User login name used to login into system. It should be between 1 to 32 characters long.
- Password: User password (or x character) stored in /etc/shadow file in encrypted format.
- User ID (UID): Every user must have a User ID (UID) User Identification Number. By default UID 0 is reserved for root, user and UID’s ranging from 1-99 are reserved for other predefined accounts. Further UID’s ranging from 100-999 are reserved for system accounts and groups.
- Group ID (GID): The primary Group ID (GID) Group Identification Number stored in /etc/group file.
- User Info: Description text
- Home Directory: The absolute location of user’s home directory.
- Shell: The absolute location of a user’s shell i.e. /bin/bash.
2. Create an user with different home directory
-d = The directory HOME_DIR does not have to exist but will not be created if it is missing.
- useradd -d /tmp/test vk9security
- cat /etc/passwd | grep vk9

3. Create a user with a defined UID
-u = The default is to use the smallest ID value greater than or equal to UID_MIN and greater than every other user.
- useradd -u 1999 vk9security
- id vk9security

4. Create a user and add it to an existing group
-g = The group name or number of the user’s initial login group. The group name must exist.
- useradd -g 60 vk9security
- id vk9security

5. Add a user to multiple groups
-G = A list of supplementary groups which the user is also a member of. Each group is separated from the next by a comma, with no intervening whitespace. (name or GID)
- useradd -G bluetooth,122,www-data vk9security
- id vk9security

6. Add a user without home directory
-M = Do not create the user’s home directory, even if the system wide setting from /etc/login.defs (CREATE_HOME) is set to yes.
- useradd -M vk9security
- cat /etc/passwd | grep vk9
- ls /home/vk9security

7. Create a temporary account
-e = The date on which the user account will be disabled. The date is specified in the format YYYY-MM-DD.
-f = The number of days after a password expires until the account is permanently disabled.
- useradd -e 2020-03-08 -f 5 vk9security
- chage -l vk9security

8. Create the account and leave a comment
-c = Any text string. It is generally a short description of the login
- useradd -c “This is a test account” vk9security
- cat /etc/passwd | grep vk9

9. Choose the login shell
-s = The name of the user’s login shell. The default is to leave this field blank, which causes the system to select the default login shell specified by the SHELL variable in /etc/default/useradd
/usr/sbin/nologin = add the account without user shell
- useradd -s /usr/sbin/nologin vk9security
- cat /etc/passwd | grep vk9

userdel
delete a user account and related files
1. Delete the user account and the user home directory
-r, –remove = Files in the user’s home directory will be removed along with the home directory itself and the user’s mail spool.

2. Force the removal
-f, –force = This option forces the removal of the user account, even if the user is still logged in.

usermod
After creating user accounts, in some scenarios where we need to change the attributes of an existing user such as, change user’s home directory, login name, login shell, password expiry date, etc, where in such case ‘usermod’ command is used.
When we execute ‘usermod‘ command in terminal, the following files are used and affected.
- /etc/passwd – User account information.
- /etc/shadow – Secure account information.
- /etc/group – Group account information.
- /etc/gshadow – Secure group account information.
- /etc/login.defs – Shadow password suite configuration..
Requirements
- existing user accounts to execute usermod command.
- Only superuser (root) is allowed to execute usermod command.
Command options
- -c = We can add comment field for the useraccount.
- -d = To modify the directory for any existing user account.
- -e = Using this option we can make the account expiry in specific period.
- -g = Change the primary group for a User.
- -G = To add a supplementary groups.
- -a = To add anyone of the group to a secondary group.
- -l = To change the login name from tecmint to tecmint_admin.
- -L = To lock the user account. This will lock the password so we can’t use the account.
- -m = moving the contents of the home directory from existing home dir to new dir.
- -p = To Use un-encrypted password for the new password. (NOT Secured).
- -s = Create a Specified shell for new accounts.
- -u = Used to Assigned UID for the user account between 0 to 999.
- -U = To unlock the user accounts. This will remove the password lock and allow us to use the user account.
1. Add a comment
-c, –comment = The new value of the user’s password file comment field.
- cat /etc/passwd | grep vk9
- usermod -c “This is a test acc” vk9security
- cat /etc/passwd | grep vk9

2. Change user home directory
-d, –home = The user’s new login directory.
- cat /etc/passwd | grep vk9
- usermod -d /tmp/test vk9security
- cat /etc/passwd | grep vk9

3. Set account expiration
-e, –expiredate = The date on which the user account will be disabled. The date is specified in the format YYYY-MM-DD.
- chage -l vk9security
- usermod -e 2020-03-09 vk9security
- chage -l vk9security

4. Change user primary group
-g, –gid = The group name or number of the user’s new initial login group. The group must exist.
- id vk9security
- usermod -g www-data vk9security
- id vk9security

5. Adding an existing user to other groups
-G, –groups = A list of supplementary groups which the user is also a member of. Each group is separated from the next by a comma, with no intervening whitespace.
- id vk9security
- usermod -G bluetooth,vk9security vk9security
- id vk9security

6. Change login name, or username
-l, –login = The name of the user will be changed from LOGIN to NEW_LOGIN. Nothing else is changed. In particular, the user’s home directory or mail spool should probably be renamed manually to reflect the new login name.
- id vk9security
- usermod -l vk9sec vk9security
- id vk9security

7. Lock user account
-L, –lock = Lock a user’s password. This puts a ‘!’ in front of the encrypted password, effectively disabling the password.
- cat /etc/shadow | grep vk9
- usermod -L vk9sec
- cat /etc/shadow | grep vk9

8. Unlock a user
-U, –unlock = Unlock a user’s password. This removes the ‘!’ in front of the encrypted password.
- cat /etc/shadow | grep vk9
- usermod -U vk9sec
- cat /etc/shadow | grep vk9

9. Move home directory to a new location
-m, –move-home = Move the content of the user’s home directory to the new location.
- usermod -d /home/vk9security -m vk9sec
10. Change user shell
-s, –shell = The name of the user’s new login shell.
- cat /etc/passwd | grep vk9
- usermod -s /bin/bash vk9sec
- cat /etc/passwd | grep vk9
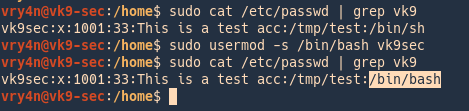
11. Change user UID
-u, –uid = The new numerical value of the user’s ID.
- id vk9sec
- usermod -u 1111 vk9sec
- id vk9sec

12. Change user GID
-g, –gid = The group name or number of the user’s new initial login group.
- id vk9sec
- usermod -g 129 vk9sec
- id vk9sec

Group Management
groupadd
The /etc/group file holds all of the group information, as well as the users belonging to each group. The structure is very similar to that of /etc/password.

1. Create a new group
- groupadd test_g
- cat /etc/group | grep test

2. Specify the GID
-g, –gid = The numerical value of the group’s ID. This value must be unique, unless the -o option is used.
- groupadd -g 1050 test_g
- cat /etc/group | grep test

3. Create a system group
-r, –system = Create a system group.
- groupadd -r sys_test
- cat /etc/group | grep sys_test

groupdel
delete a group
1. Delete an existing group
- cat /etc/group | grep sys_tes
- groupdel sys_test
- cat /etc/group | grep sys_tes

groupmod
modify a group definition on the system
1. Change group name
-n, –new-name = The name of the group will be changed from GROUP to NEW_GROUP name.
- groupmod -n test test_g
- cat /etc/group | grep test

2. Change GID
-g, –gid = The group ID of the given GROUP will be changed to GID.
- cat /etc/group | grep test
- groupmod -g 1100 test
- cat /etc/group | grep test

by Vry4n_ | Mar 8, 2020 | Linux Management
The Linux terminal has a number of useful commands that can display running processes, kill them, and change their priority level.
Parent and Child Processes
Each unix process has two ID numbers assigned to it: The Process ID (pid) and the Parent process ID (ppid). Each user process in the system has a parent process.
Starting a Process
When you start a process (run a command), there are two ways you can run it −
- Foreground Processes
- Background Processes
1. Foreground Processes
By default, every process that you start runs in the foreground. If the command is like “ls” it will print the output, and, exit the command, most likely when a persistent program runs it stays and the terminal actively shows that running, events are displayed in the screen, in other words, the terminal becomes exclusively part of the program.
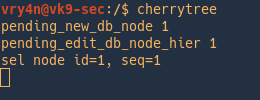
2. Background Processes
A background process runs without being connected to your keyboard. If the background process requires any keyboard input, it waits.
The advantage of running a process in the background is that you can run other commands; you do not have to wait until it completes to start another. Meaning the terminal is no longer exclusive to that newprocess.
& = send program to background
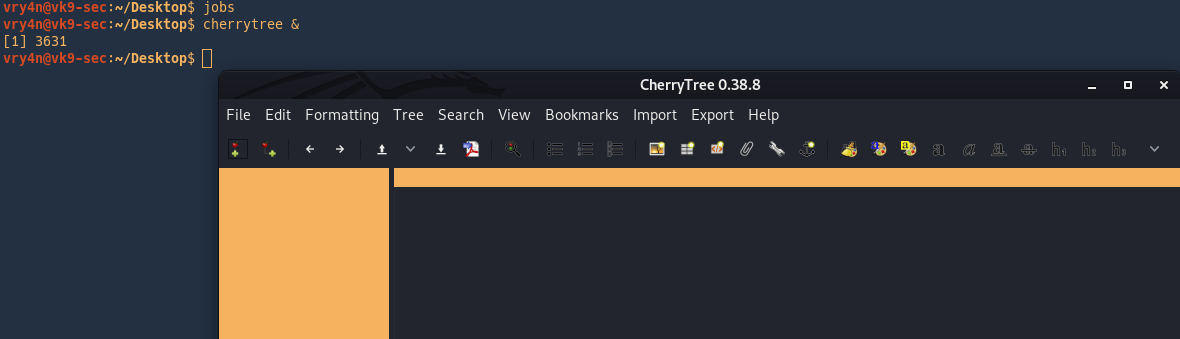
Sending a program to foreground or background
fg = send to foreground
bg = send to background
use jobs to list the programs running for that terminal.
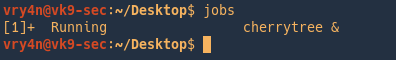
As we can see the program is running in the foreground
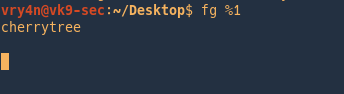
To send it to the background stop it (Ctrl + z) , and then run bg command
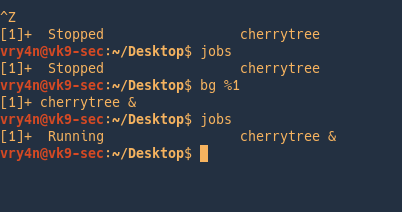
Listing Running processes
PS
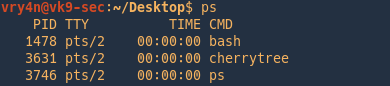
1. To show processes use ‘ps’, run in bash
-f = Do full-format listing.
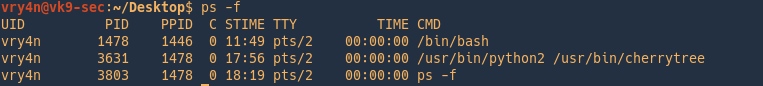
- UID = User ID that this process belongs to (the person running it)
- PID = Process ID
- PPID = Parent process ID (the ID of the process that started it)
- C = CPU utilization of process
- STIME = Process start time
- TTY = Terminal type associated with the process
- TIME = CPU time taken by the process
- CMD = The command that started this process
2. Show all information of all processes running
-e = Select all processes. Identical to -A
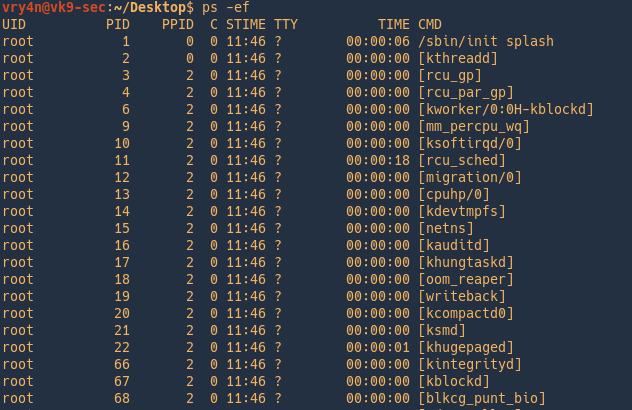
An alternative is
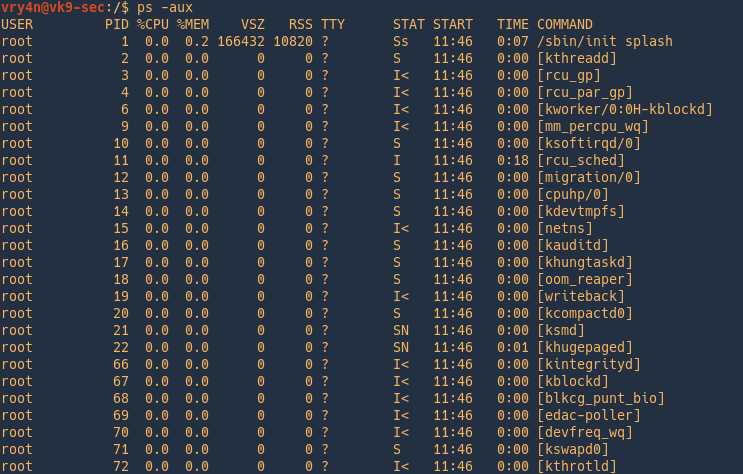
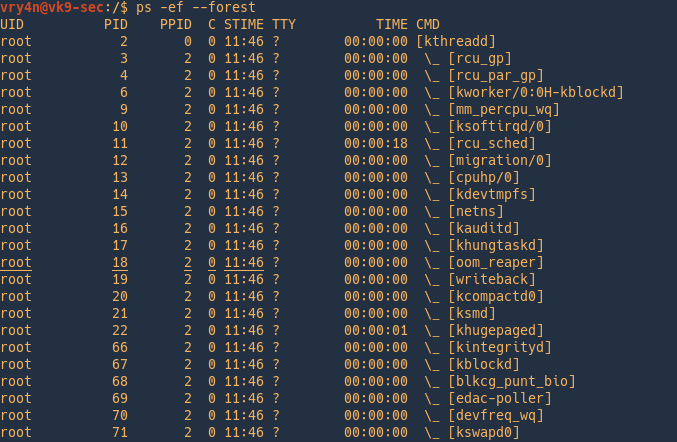
3. Display process tree
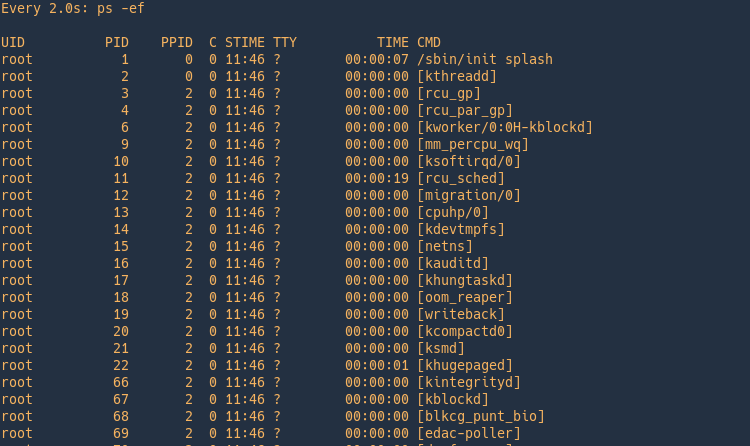
4. List processes dynamically
watch -n 2 = running the ps command every 2 seconds
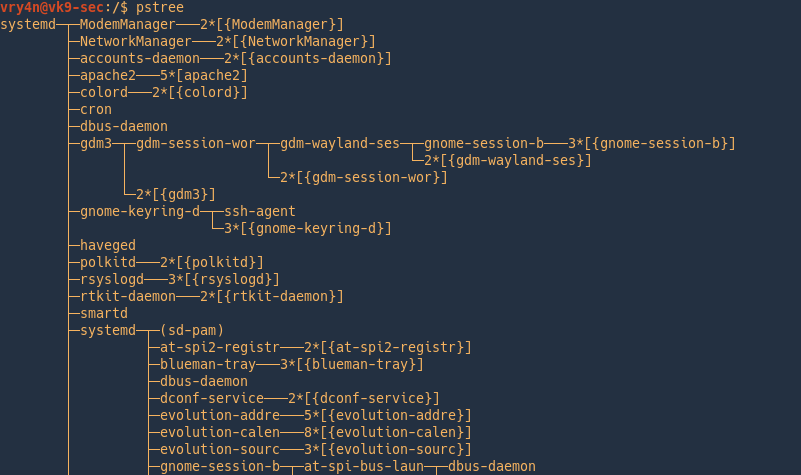
PSTREE
Display a tree of processes
Print the tree with PID
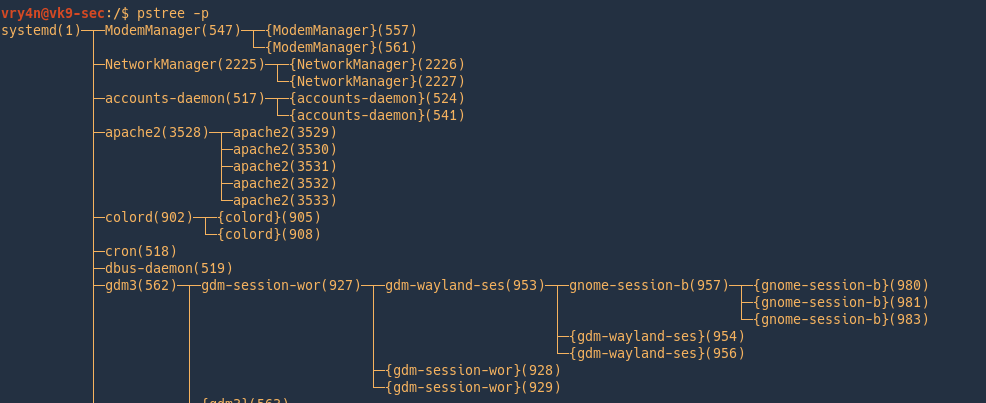
Sorting the output
-n = Sort processes with the same ancestor by PID instead of by name
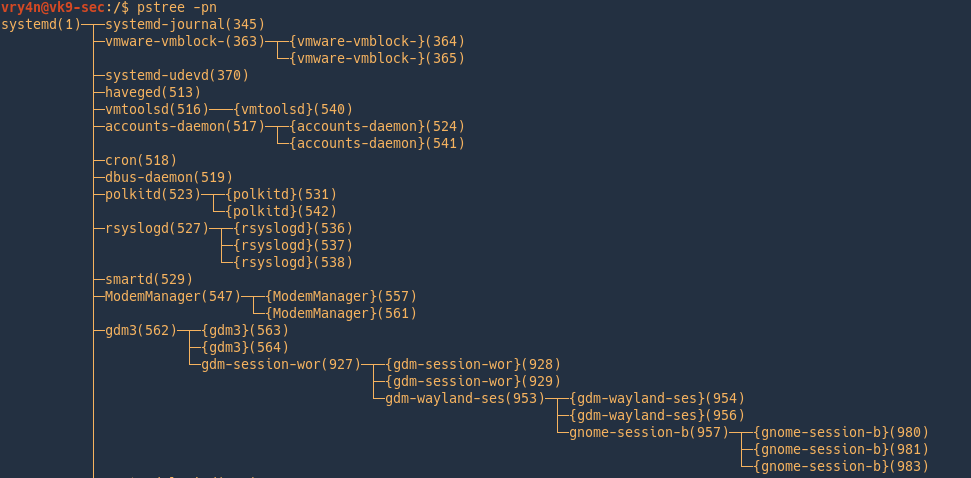
Filter by processes also
-s = Show parent processes of the specified process.
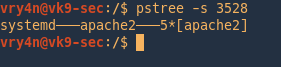
Filter process by users
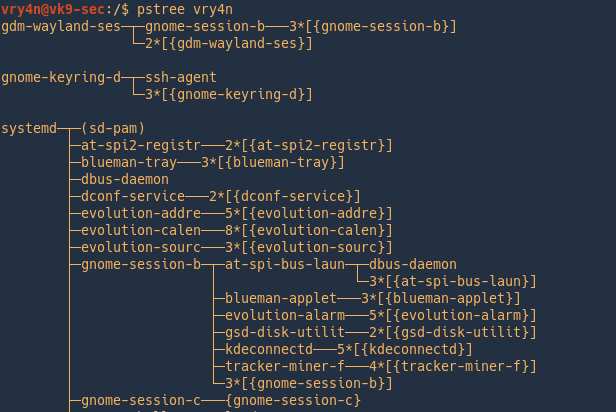
TOP
top command is used to show the Linux processes. It provides a dynamic real-time view of the running system.
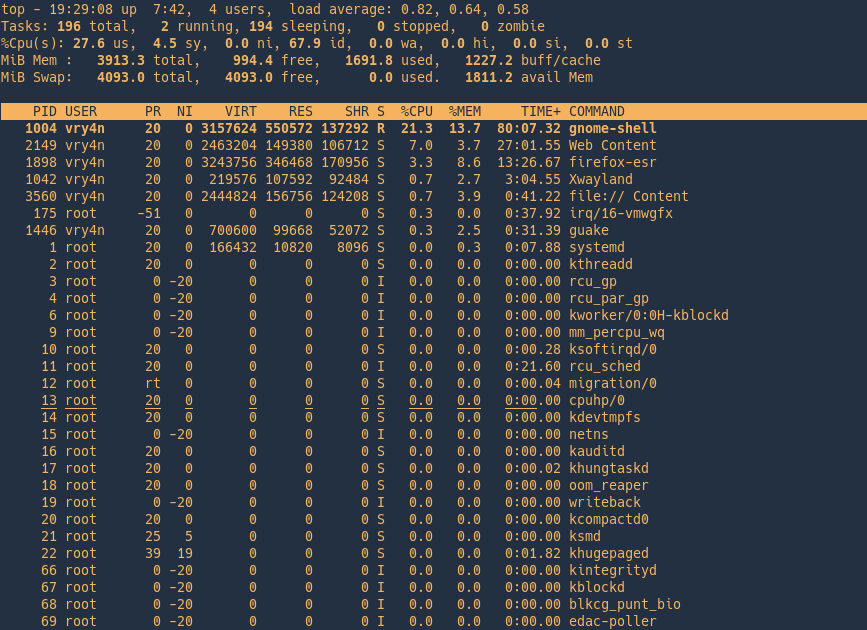
- PID: Shows task’s unique process id.
- USER: User name of owner of task.
- PR: Stands for priority of the task.
- NI: Represents a Nice Value of task. A Negative nice value implies higher priority, and positive Nice value means lower priority.
- VIRT: Total virtual memory used by the task.
- SHR: Represents the amount of shared memory used by a task.
- %CPU: Represents the CPU usage.
- %MEM: Shows the Memory usage of task.
- TIME+: CPU Time, the same as ‘TIME’, but reflecting more granularity through hundredths of a second.
- Command: Shows the command used to run the process
Display processes by user
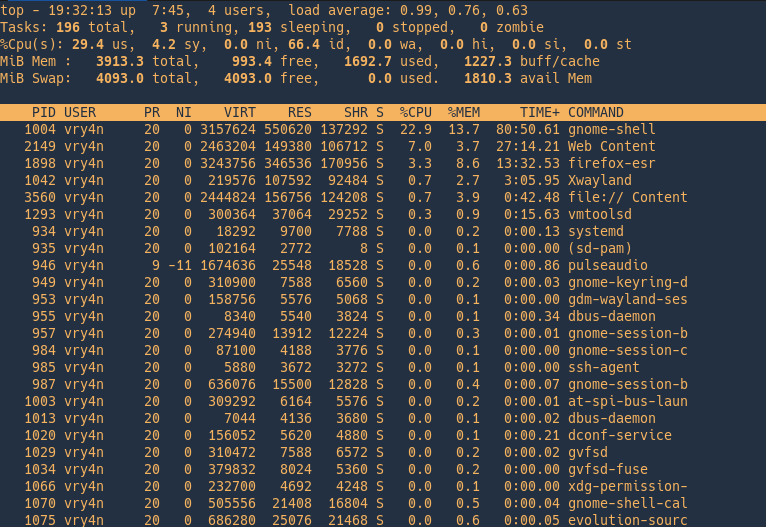
Show absolute path
Top commands
While running to you can run commands
Use ‘h’ to display help menu
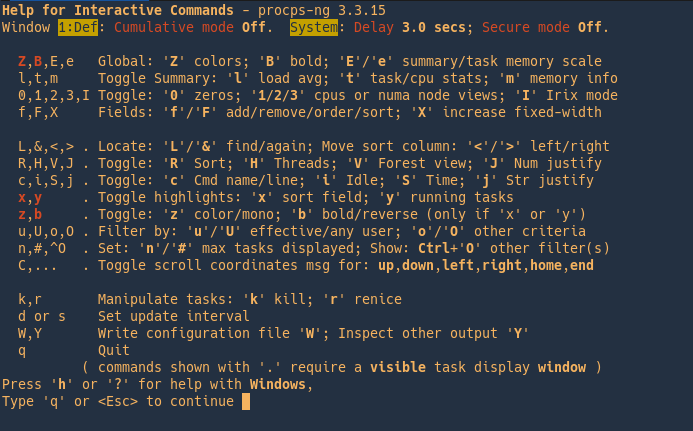
z = color output
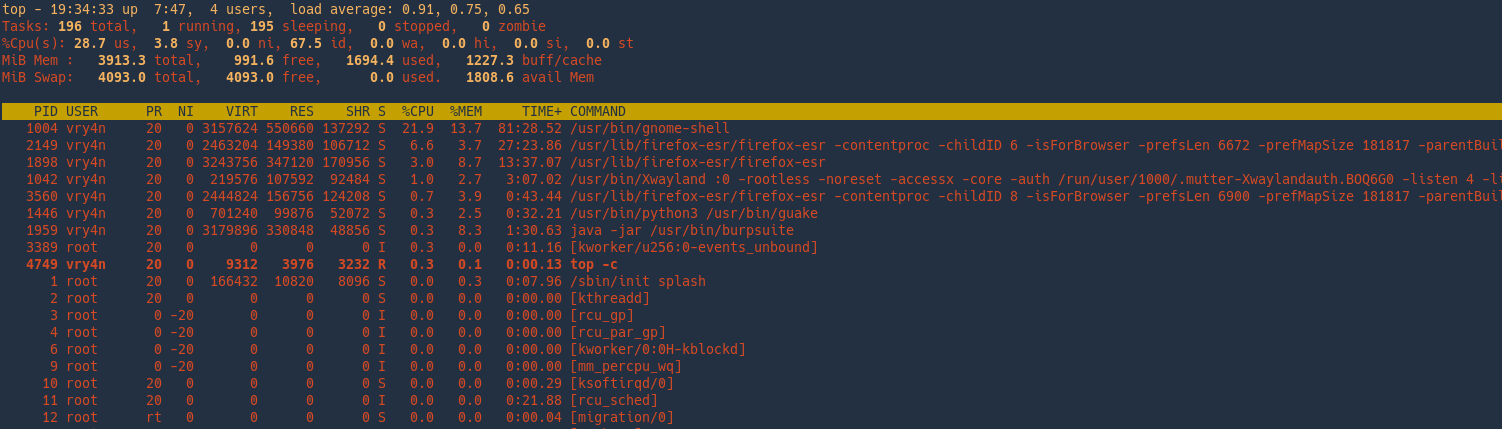
k = kill a process
In this example we will kill Firefox, PID 4758
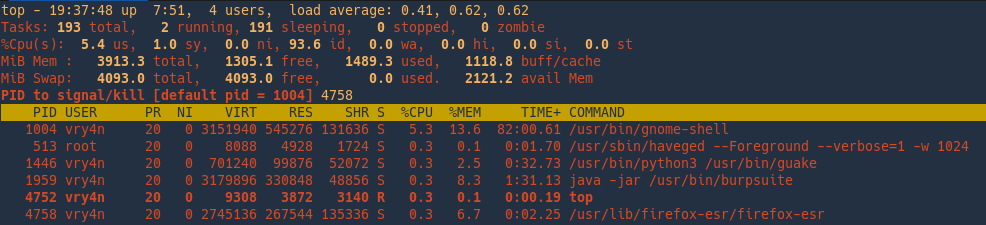
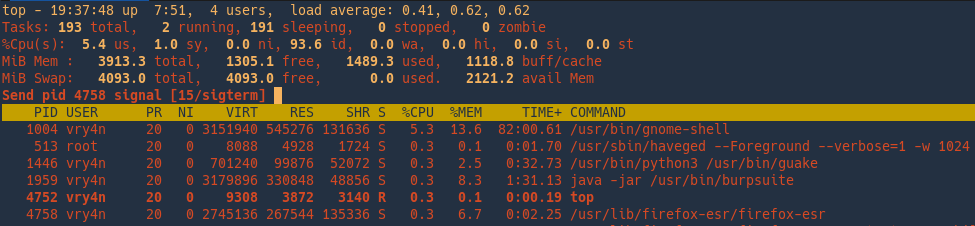
Choose the signal to send the kill
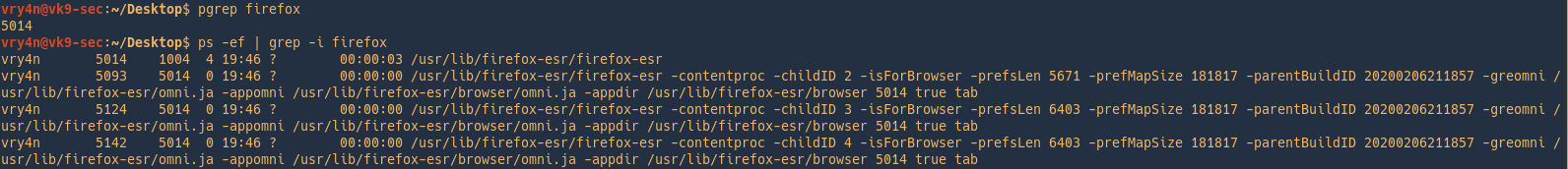
pgrep
pgrep returns the process IDs that match it.
- pgrep firefox
- ps -ef | grep -i firefox
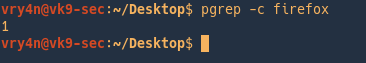
Count matches
-c = Suppress normal output; instead print a count of matching processes.
Print full PID and child PID
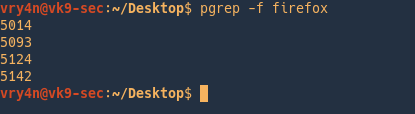
-f = The pattern is normally only matched against the process name. When -f is set, the full command line is used.
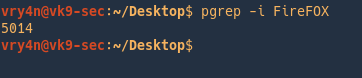
Ignore case
-i = Match processes case-insensitively.
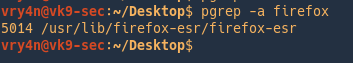
Print command line and PID
-a = List the full command line as well as the process ID.
Change process priority
Nice is a command in Unix and Linux operating systems that allows for the adjustment of the “Niceness” value of processes. Adjusting the “niceness” value of processes allows for setting an advised CPU priority that the kernel’s scheduler will use to determine which processes get more or less CPU time.
Different OS distributions can have different default values for new processes. The simplest method to determine the default value is to simply run the nice command with no arguments.
Nice value is a user-space and priority PR is the process’s actual priority that use by Linux kernel
System priorities are 0 to 139 in which 0 to 99 for real time and 100 to 139 for users
Nice value range is -20 to +19 where -20 is highest, 0 default and +19 is lowest.
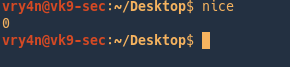
Checking current nice value of a running process
- ps -ef | grep firefox
- ps -lp 5014
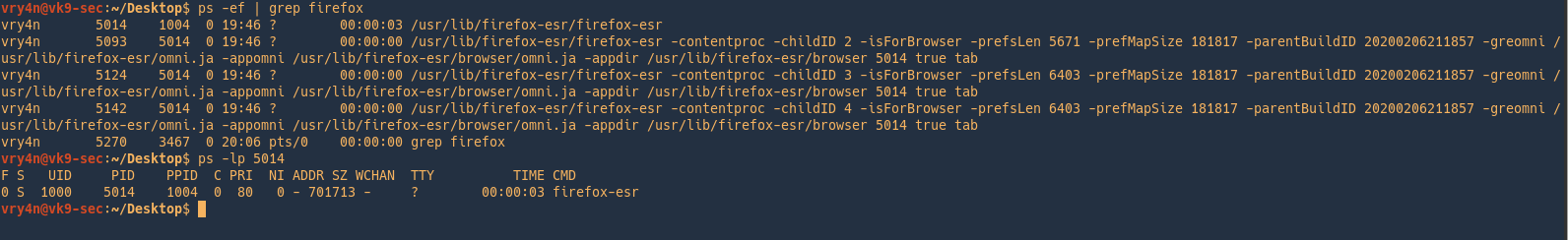
Changing the nice value of a new process
The nice command itself will run the supplied command with the desired niceness value. This time the value is one, overwriting the default 0
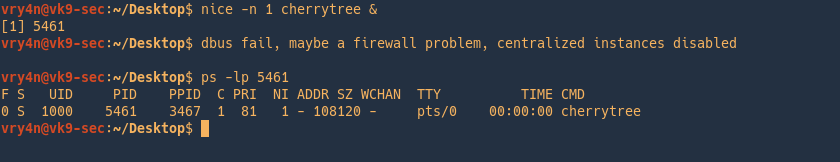
Changing the nice value of a running process
To change the niceness value of a running process we will utilize the renice command.
Killing a process
Zombie and Orphan Processes
Normally, when a child process is killed, the parent process is updated via a SIGCHLD signal. Then the parent can do some other task or restart a new child as needed.
Daemon Processes
Daemons are system-related background processes that often run with the permissions of root and services requests from other processes.
A daemon has no controlling terminal. It cannot open /dev/tty. If you do a “ps -ef” and look at the tty field, all daemons will have a ? for the tty.
kill
Send a signal to a process. The default signal for kill is TERM. Use -l or -L to list available signals. Particularly useful signals include HUP, INT, KILL, STOP, CONT, and 0. Alternate signals may be specified in three ways: -9, -SIGKILL or -KILL.
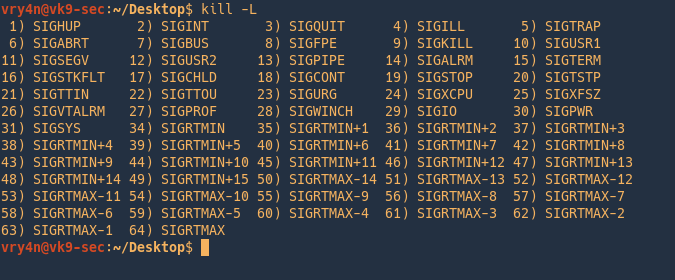
Kill a process
- pgrep cherrytree
- kill 5461
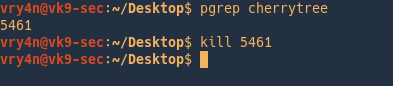
Send SIGKILL (powerful)
- pgrep firefox
- kill -9 5014
- pgrep firefox
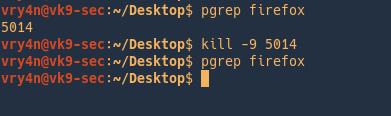
Killing a job
- firefox &
- jobs
- kill %1
- jobs
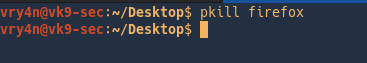
pkill
pkill kills processes based on name and other attributes
killall
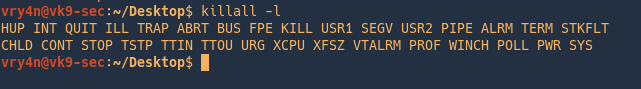
kill processes by name
List the signal
Kill a process by name
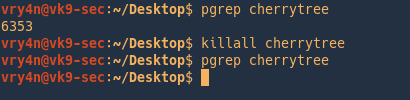
- pgrep cherrytree
- killall cherrytree
- pgrep cherrytree
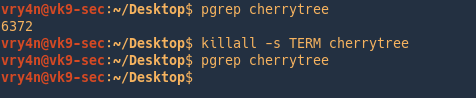
Kill using a signal
- pgrep cherrytree
- killall -s TERM cherrytree
- pgrep cherrytree
Be verbose
- pgrep cherrytree
- killall -v -s TERM cherrytree
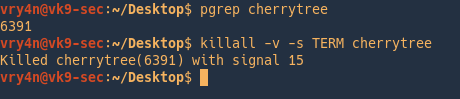
Kill processes by user
- sudo killall -v -s TERM –user www-data
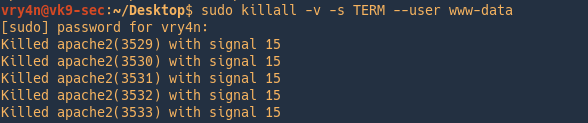
Keeping a process running
NOHUP
A process may not continue to run when you log out or close your terminal. This special case can be avoided by preceding the command you want to run with the nohup command.
/proc Linux folder
Proc file system (procfs) is virtual file system built at run time. It contains the useful information about the processes that are currently running, it is regarded as control and information centre for kernel.
The proc file system also provides communication medium between kernel space and user space.
Examining a process using /proc as an example
- pgrep cherrytree
- ps -ef | grep 6832
- ls -l 6832
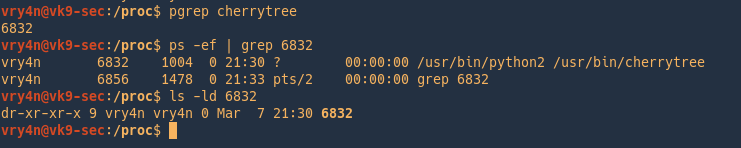
We now know that cherrytree has the pid of 6832, there is also a directory with that name within /proc.
Change to the pid folder
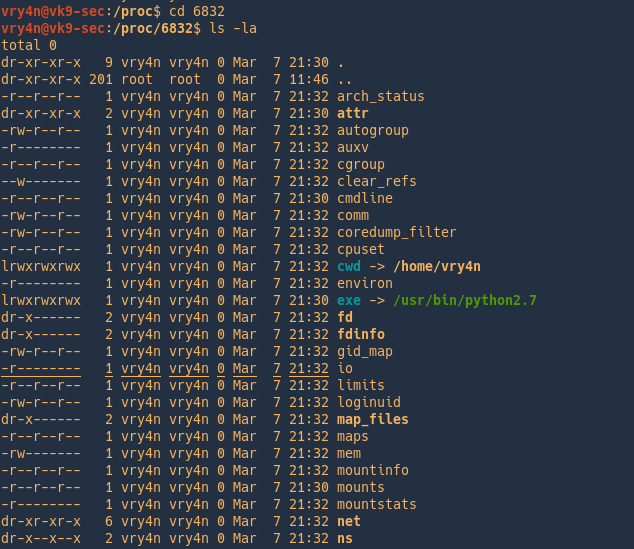
Below you have a summary of the most important files and directories within each process directory.
Directories
- /proc/PID/cmdline Command line arguments.
- /proc/PID/cpu Current and last cpu in which it was executed.
- /proc/PID/cwd Link to the current working directory.
- /proc/PID/environ Values of environment variables.
- /proc/PID/exe Link to the executable of this process.
- /proc/PID/fd Directory, which contains all file descriptors.
- /proc/PID/maps Memory maps to executables and library files.
- /proc/PID/mem Memory held by this process.
- /proc/PID/root Link to the root directory of this process.
- /proc/PID/stat Process status.
- /proc/PID/statm Process memory status information.
- /proc/PID/status Process status in human readable form.
Files
- /proc/crypto list of available cryptographic modules
- /proc/diskstats information (including device numbers) for each of the logical disk devices
- /proc/filesystems list of the file systems supported by the kernel at the time of listing
- /proc/kmsg holding messages output by the kernel
- /proc/meminfo summary of how the kernel is managing its memory.
- /proc/scsi information about any devices connected via a SCSI or RAID controller
- /proc/tty information about the current terminals
- /proc/version containing the Linux kernel version, distribution number, gcc version number (used to build the kernel) and any other pertinent information relating to the version of the kernel currently running
Important files with /proc besides the process specific directories
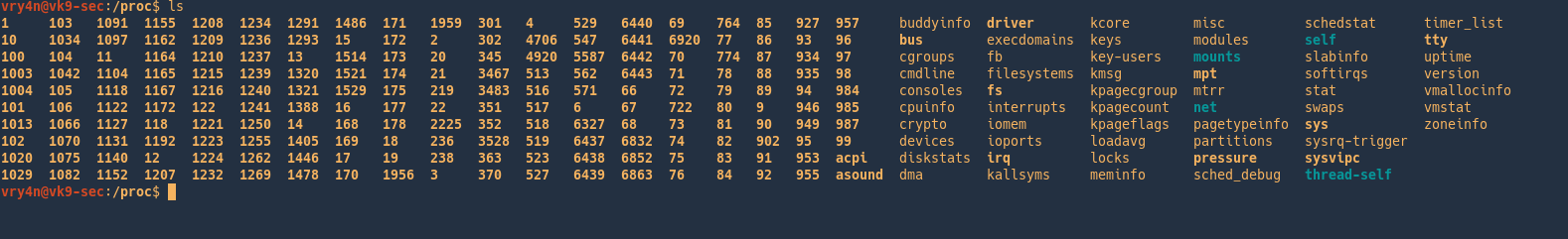
- /proc/apm: Provides information on Advanced Power Management, if it’s installed.
- /proc/acpi: A similar directory that offers plenty of data on the more modern Advanced Configuration and Power Interface.
- /proc/cmdline: Shows the parameters that were passed to the kernel at boot time.
- /proc/cpuinfo: Provides data on the processor of your box.
- /proc/loadavg: A related file that shows the average load on the processor; its information includes CPU usage in the last minute, last five minutes, and last 10 minutes, as well as the number of currently running processes.
- /proc/stat: Also gives statistics, but goes back to the last boot.
- /proc/uptime: A short file that has only two numbers: how many seconds your box has been up, and how many seconds it has been idle.
- /proc/devices: Displays all currently configured and loaded character and block devices.
- /proc/ide and /proc/scsi: Provide data on IDE and SCSI devices.
- /proc/ioports: Shows you information about the regions used for I/O communication with those devices.
- /proc/dma: Shows the Direct Memory Access channels in use.
- /proc/filesystems: Shows which filesystem types are supported by your kernel.
- /proc/mounts: Shows all the mounts used by your machine (its output looks much like /etc/mtab). Similarly,
- /proc/partitions: show all partitions
- /proc/swaps: show all swap space.
- /proc/fs: If you’re exporting filesystems with NFS, this directory has among its many subdirectories and files /proc/fs/nfsd/exports, which shows the file system that are being shared and their permissions.
- /proc/net: it includes /dev (each network device), several iptables (firewall) related files, net and socket statistics, wireless information, and more.
- /proc/meminfo: RAM-related files. I’ve already mentioned but you’ve also got
- /proc/iomem, which shows you how RAM memory is used in your box
- /proc/kcore, which represents the physical RAM of your box.
- /proc/kcore shows a size that’s equal to your RAM plus a small overhead. (Don’t try to cat this file, because its contents are binary and will mess up your screen.)
- Hardware-related files and directories, such as /proc/interrupts and /proc/irq, /proc/pci (all PCI devices), /proc/bus, and so on, but they include very specific information, which most users won’t need.
Within /proc/sys
- debug: Has debugging information. This is good if you’re into kernel development.
- dev: Provides parameters for specific devices on your system; for example, check the /dev/cdrom directory.
- fs: Offers data on every possible aspect of the filesystem.
- kernel: Lets you affect the kernel configuration and operation directly.
- net: Lets you control network-related matters. Be careful, because messing with this can make you lose connectivity!
- vm: Deals with the VM subsystem.
by Vry4n_ | Mar 6, 2020 | Linux Misc
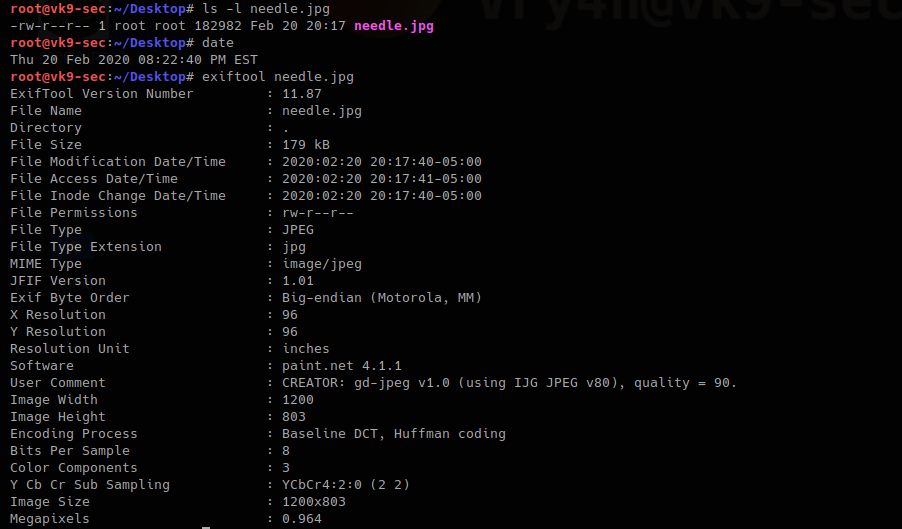
A picture metadata can change, example dates, if you download a picture directly from a browser. I recommend downloading the content using wget.
Download from browser
1. In this case we can see a recent date (File modification date/time)
- ls -l needle.jpg
- date
- exiftool needle.jpg
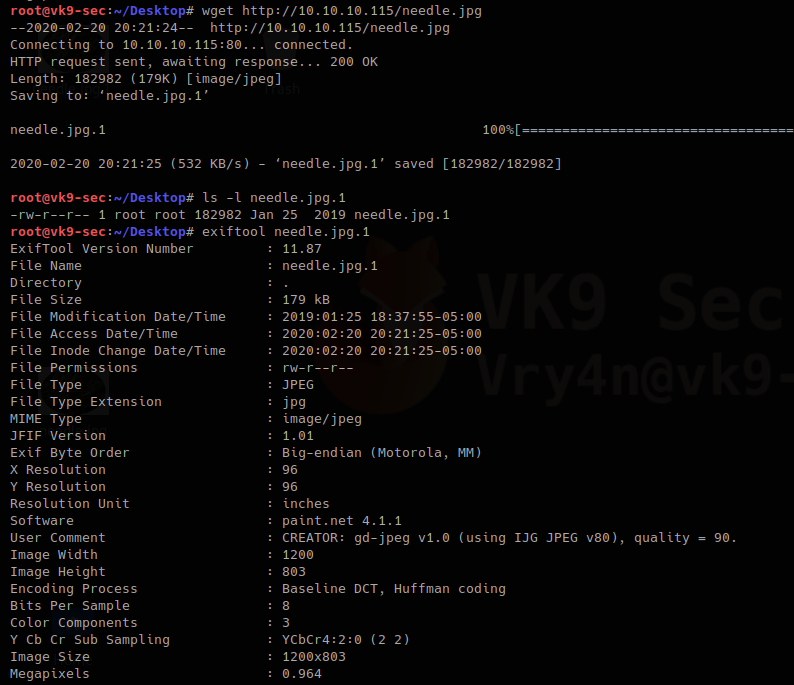
Download using wget
1. In this other scenario, the last modification time will show as the original. An older date.
- wget http://10.10.10.115/needle.jpg
- ls -l needle.jpg.1
- exiftool needle.jpg.1